API discovery in your environment
PingIntelligence supports API discovery in sideband and inline mode as an automated method of building API definitions that provide the properties of the managed APIs.
These API definitions are then used to provide API visibility and detection of anomalous client behavior. You can configure API discovery through the Dashboard, which displays, manages, and renders the discovered APIs. The Dashboard also allows you to edit the discovered APIs and export their definition files.
To set up PingIntelligence for discovery, you must:
Configuring ASE with API discovery
About this task
|
Configure API discovery when API Security Enforcer (ASE) is deployed in sideband mode. To configure ASE for inline discovery, contact Ping Identity support. |
ASE requires a root definition that enables it to route all API traffic to the AI engine. The AI engine receives and monitors all API traffic that is not associated with a known API. It analyzes the traffic and builds API models for the unknown APIs, which are shown on the Discovery dashboard.
To add a root API in ASE:
Steps
-
Use the sample
rootAPI JSON shipped with ASE in the<ASE_Installation path>/pingidentity/ase/config/api/directory and configure the API JSON for therootAPI.For sideband environments, use the following settings:
Parameter Setting protocolhttpurl/hostname* -
To capture client identifiers such as token, cookies, API keys, IP addresses, and username, configure the
rootAPI JSON file with the following client identifiers.If the identifiers are not present in at least 50% of the traffic received for a discovered API, then the identifiers are not reported or used in Indicator of Attack (IoA) detection.
Client Identifier Description oauth2_access_tokenIf a bearer token is present, set to
true.cookieIf cookies are used as the primary client identifier, configure the cookie name.
apikey_qsorapikey_headerSet for the API key in query parameter or for the API key in header.
Example:
The following is a sample API JSON for the
rootAPI:{ "api_metadata": { "protocol": "http", "url": "/", "hostname": "*", "cookie": "", "oauth2_access_token": true, "apikey_qs": "", "apikey_header": "", "login_url": "", "enable_blocking": true, "api_memory_size": "1mb", "decoy_config": { "decoy_enabled": false, "response_code": 200, "response_def": "", "response_message": "", "decoy_subpaths": [] } } }IP addresses and usernames are captured separately.
-
After configuring an API JSON file for the
rootAPI, add it to ASE to initiate the API discovery process by running the following command:/<ASE_Installation path>/pingidentity/ase/bin/cli.sh –u admin -p admin add_api {file_path/api_name}
Configuring discovery settings in the Dashboard
About this task
To customize the discovery process, configure the discovery parameters on the Dashboard.
Steps
-
Go to Discovered APIs → Settings.
-
Click the Discovery Configuration tab and set the value for AI Engine Subpath Depth.
AI Engine Subpath Depth defines the number of subpaths used to uniquely discover the base path of a new API. The maximum allowed value is 6 when ASE is deployed in inline mode and 10 when ASE is deployed in sideband mode.
Example:
The following are examples of subpath values and what they mean:
-
1indicates/atmappis the base path for/atmapp/zipcode,/atmapp/update, and so on. -
3indicatesv1/cust1/atmappis the base path forv1/cust1/atmapp/zipcode, and so on.
-
-
Click Discovered APIs on the Dashboard and click Export to download the API definition in
.jsonformat .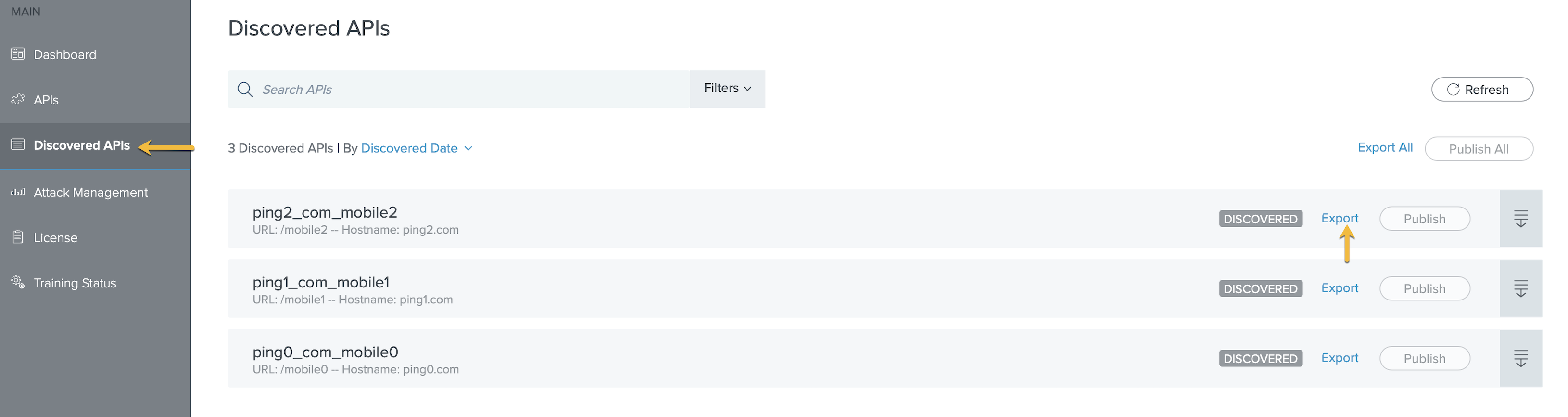
-
Add the downloaded API JSON definitions to ASE by running the following command:
# /<ASE_Installation path>/pingidentity/ase/bin/cli.sh –u admin -p admin add_api {file_path/api_name}