Validate the Token
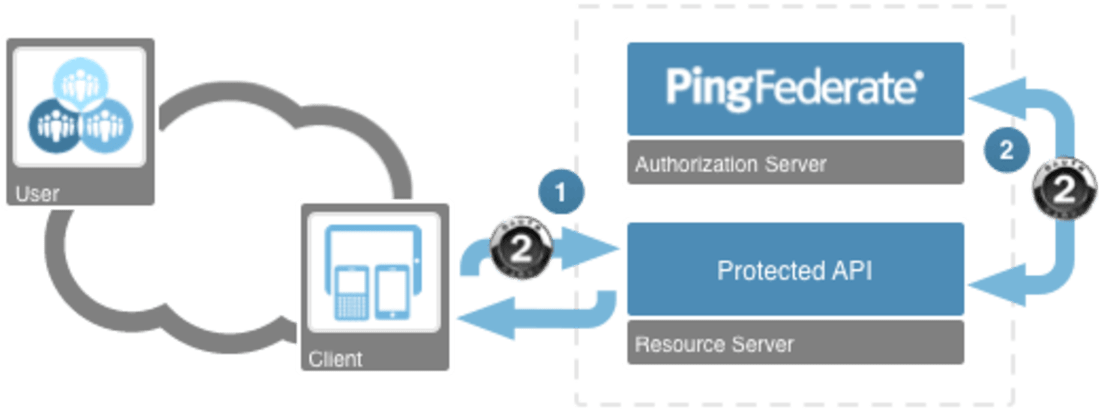
For an API developer to integrate with OAuth 2.0, the resource must accept and validate the OAuth 2.0 access token (step 1 below). Once the token has been received, the resource can then validate the access token against the PingFederate authorization server (step 2). The response from the access token validation will include attributes that the resource can use for authorization decisions.
|
Sample Client Configuration
For the access token validation example below, the following client information will be used:
| Admin Label | OAuth2 Parameter | Example Value |
|---|---|---|
Redirect URIs |
redirect_uri |
sample://oauth2/code/cb |
Scope Settings |
scope |
edit |
Refresh Token |
refresh_token |
123…789 |
Client ID |
client_id |
rs_client |
Client Authentication |
client_secret |
2Federate |
Allowed Grant Types |
grant_type |
Access Token Validation (Client is a Resource Server)
|
Validating the Token
The API first needs to receive the access token from the client as it was provided per the "Use a Token" section of this guide.
A request from a client would look similar to the following:
GET https://api.company.com/user HTTP/1.1 Authorization: Bearer AAA...ZZZ
In order to fulfill the request, the API first extracts the access token from the authorization header, then queries the token endpoint of the PingFederate AS to validate the token:
POST https://localhost:9031/as/token.oauth2 HTTP/1.1 Content-Type: application/x-www-form-urlencoded Authorization: Basic cnNfY2xpZW50OjJGZWRlcmF0ZQ== grant_type=urn:pingidentity.com:oauth2:grant_type:validate_bearer&token=AAA...ZZZ
A successful response to this message will result in a 200 OK HTTP response and a JSON structure in the body of the response similar to the following:
HTTP/1.1 200 OK
Content-Type: application/json;charset=UTF-8
{
"access_token": { "role":"all_access" },
"token_type":"Bearer",
"expires_in":14400,
"scope":"edit",
"client_id":"ac_client"
}
The resource server can then use this information to make an authorization decision and allow or deny the web request.