Agent deployment
The following diagram shows hows users are authenticated, and how access policies and identity mappings are applied to requests to access applications or APIs with an agent deployment.
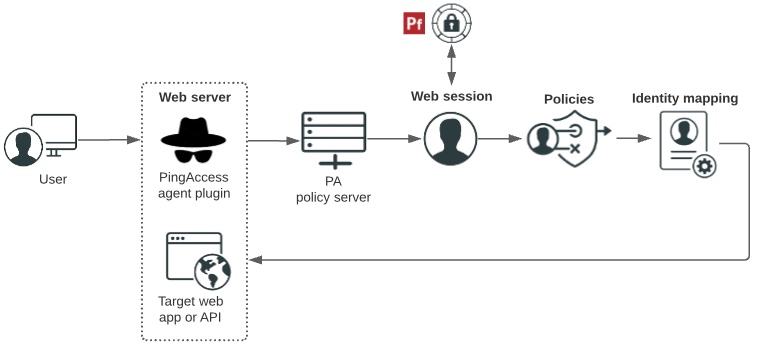
-
Users enter a URL to request access to a resource and their requests.
-
The PingAccess agent plugin intercepts the request. Agents use names and shared secrets to authenticate with the policy server. These names and secrets do not need to be unique. Any number of agents can have the same name and secret, and they are all treated equally by the policy server.
-
If the agent does not have previously cached policies for the resource, it contacts the PingAccess policy server for instructions.
-
The PingAccess policy server receives claims from the token provider, which provides instructions for handling the request.
-
Policies are applied to the request and PingAccess makes policy-based decisions to grant or deny access to the requested resource.
-
Identity mapping is applied to the request if the target application expects user information to be included to further authenticate the user.
-
The user accesses the target web application or API.