Autonomous Identity API
This chapter is targeted to developers who want to access Autonomous Identity using the REST Application Programming Interface (API).
ForgeRock® Autonomous Identity is an entitlements and roles analytics system that lets you fully manage your company’s access to your data.
An entitlement refers to the rights or privileges assigned to a user or thing for access to specific resources. A company can have millions of entitlements without a clear picture of what they are, what they do, and who they are assigned to. Autonomous Identity solves this problem by using advanced artificial intelligence (AI) and automation technology to determine the full entitlements landscape for your company. The system also detects potential risks arising from incorrect or over-provisioned entitlements that lead to policy violations. Autonomous Identity eliminates the manual re-certification of entitlements and provides a centralized, transparent, and contextual view of all access points within your company.
About the Autonomous Identity API
Autonomous Identity provides a RESTful application programming interface (API) that lets you use HTTP request methods (GET, PUT, and POST) to interact with the system and its components. The API lets a developer make requests to send or receive data to an Autonomous Identity endpoint, a point where the API communicates with the system. The data that is sent or returned is in JavaScript Object Notation (JSON) format.
| With the release of version 2021.8.4, Autonomous Identity no longer provides a Swagger client that you can access on the console. The Swagger UI was removed to tighten security within Autonomous Identity. However, you can download the Autonomous Identity API and import it into Postman. |
| You cannot import the Autonomous Identity API into Swagger as there is an existing CORS issue that breaks functionality. |
Using Postman
-
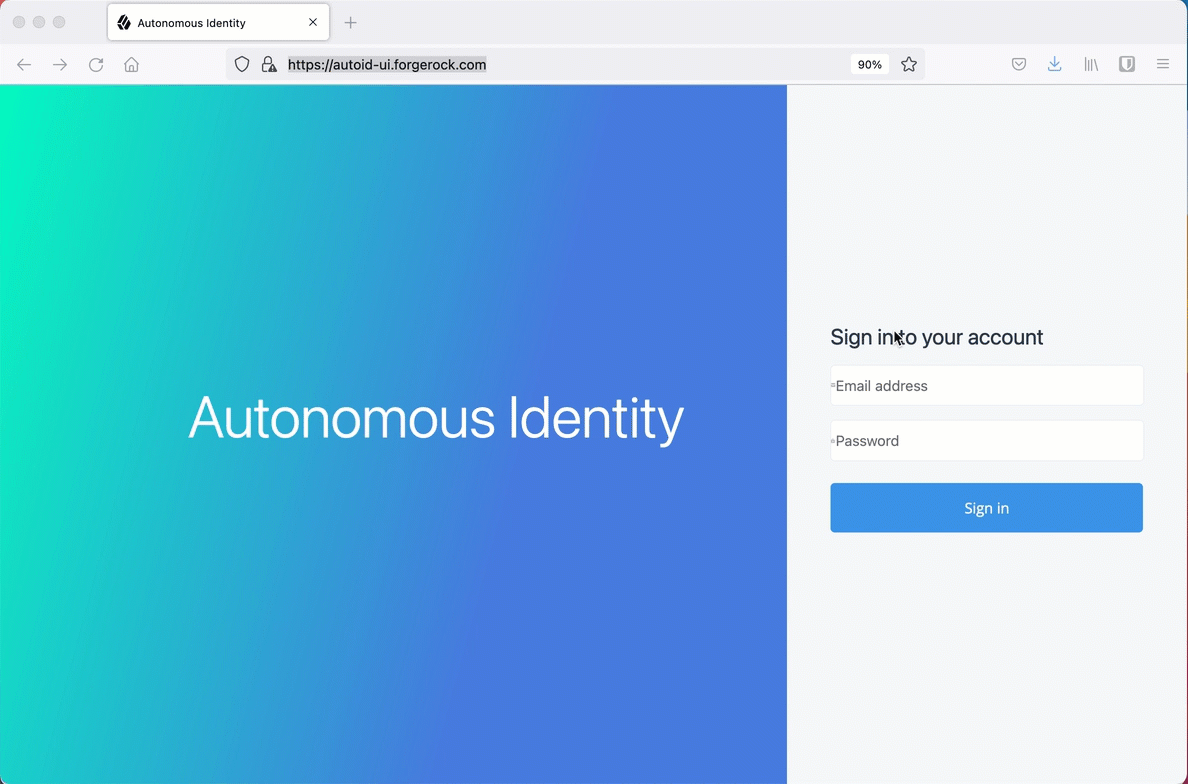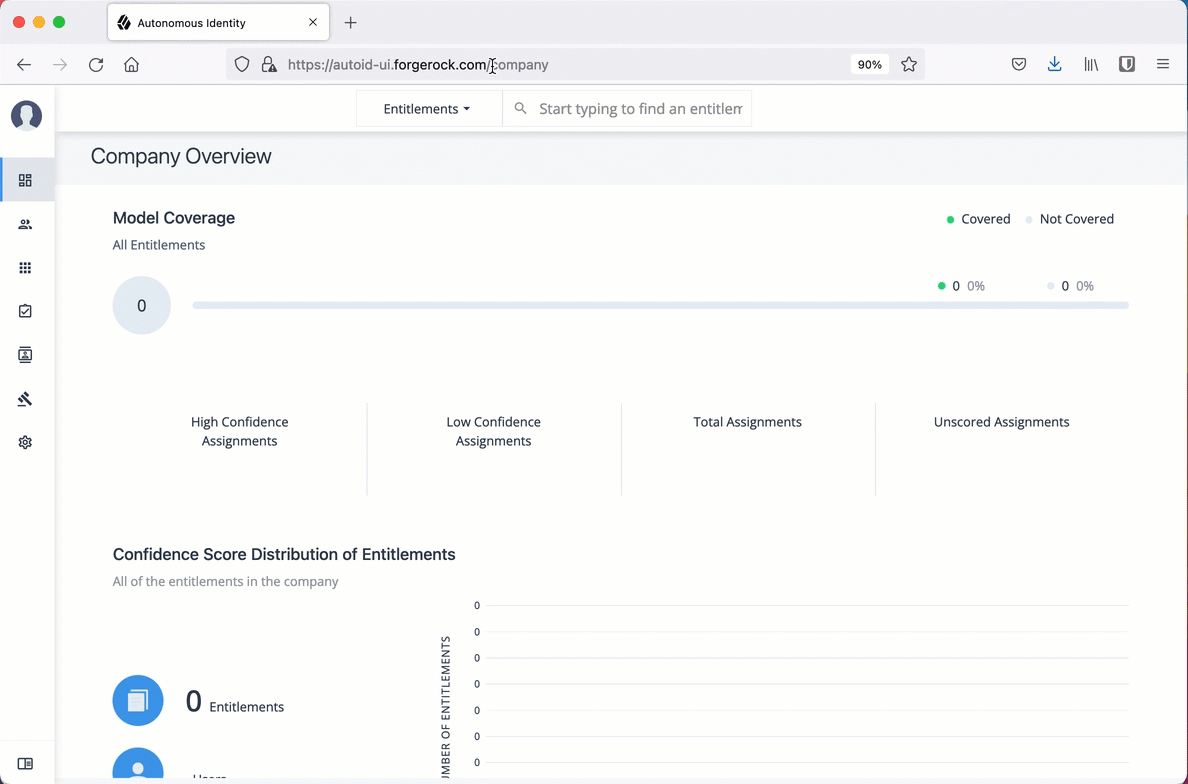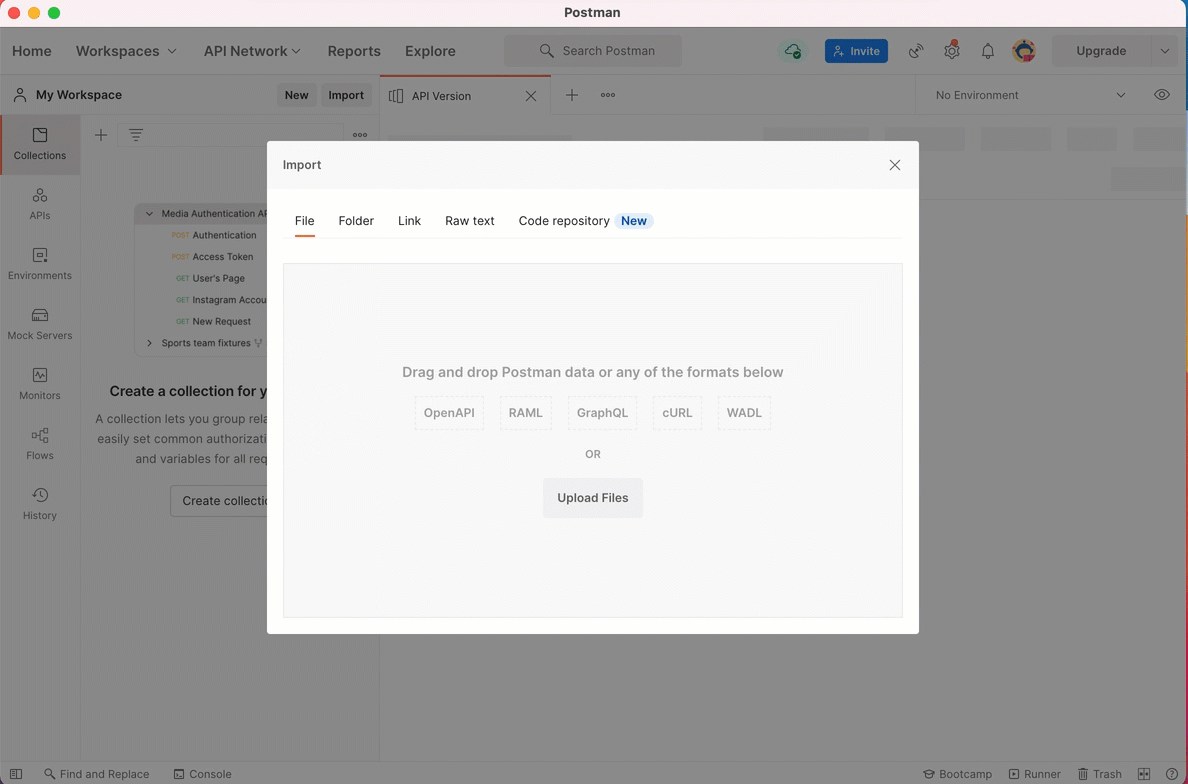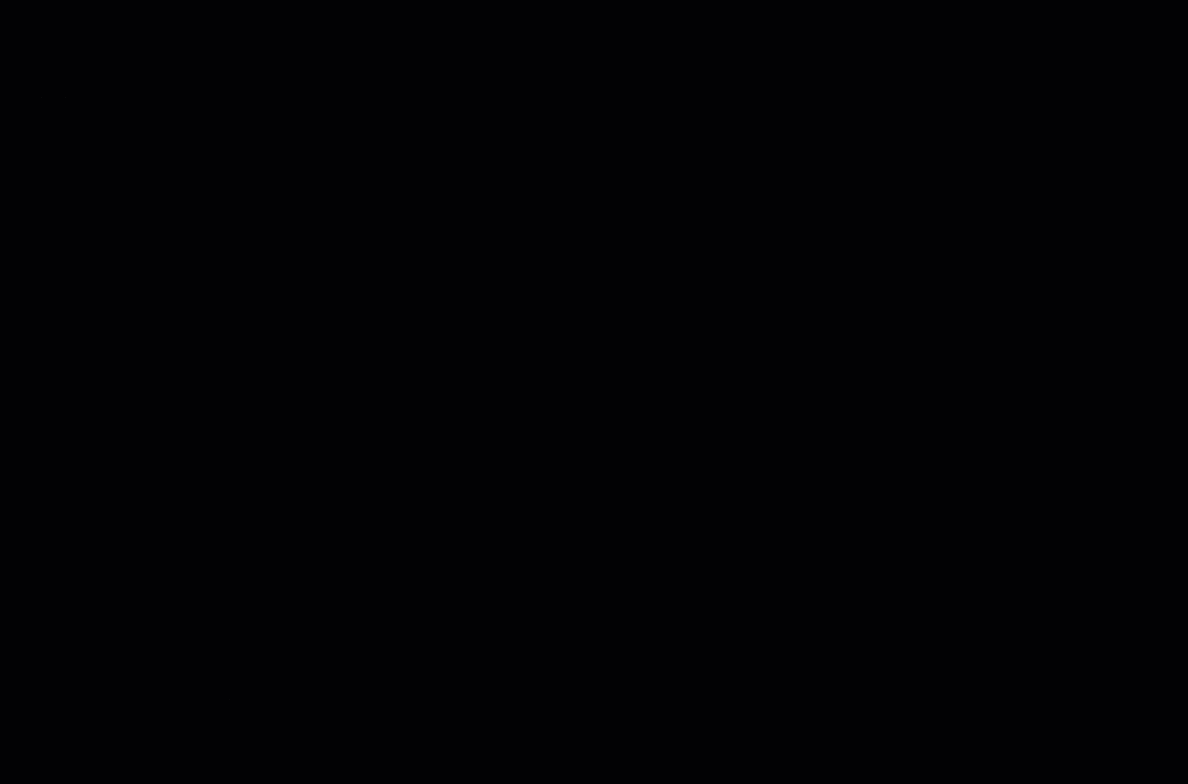
On an upgraded Autonomous Identity instance, open a browser, and log in using your account at
https://autoid-ui.forgerock.com/. -
Point your browser to
https://autoid-ui.forgerock.com/api/swagger.An Opening Swagger dialog appears. -
Save the file as
api.ymlorconf.ymlto your local server or laptop. -
Open Postman, and click Import. The file is imported into Postman.
-
Click Zoran-API-Service.
Click an example
You now can access the Autonomous Identity API in Postman.
Generate an API key
Autonomous Identity gives an administrator the ability to generate API keys for those who want to access certain endpoints using REST. Administrators can create an API from the Self-Service page of the Autonomous Identity UI.
| As of this release, only the Ingest endpoints use the API key. |
|
To use an API token, you need both the tenant ID that the API key belongs to, and the API token itself. |
Obtain the tenant ID
In Autonomous Identity 2021.8.0 and later, the tenant ID is set as an environment variable that you can easily access.
-
On the target node, get the tenant ID.
$ env | grep TENANT_ID TENANT_ID=8700f5cb-eaca-461e-8c2e-245a25f2399d
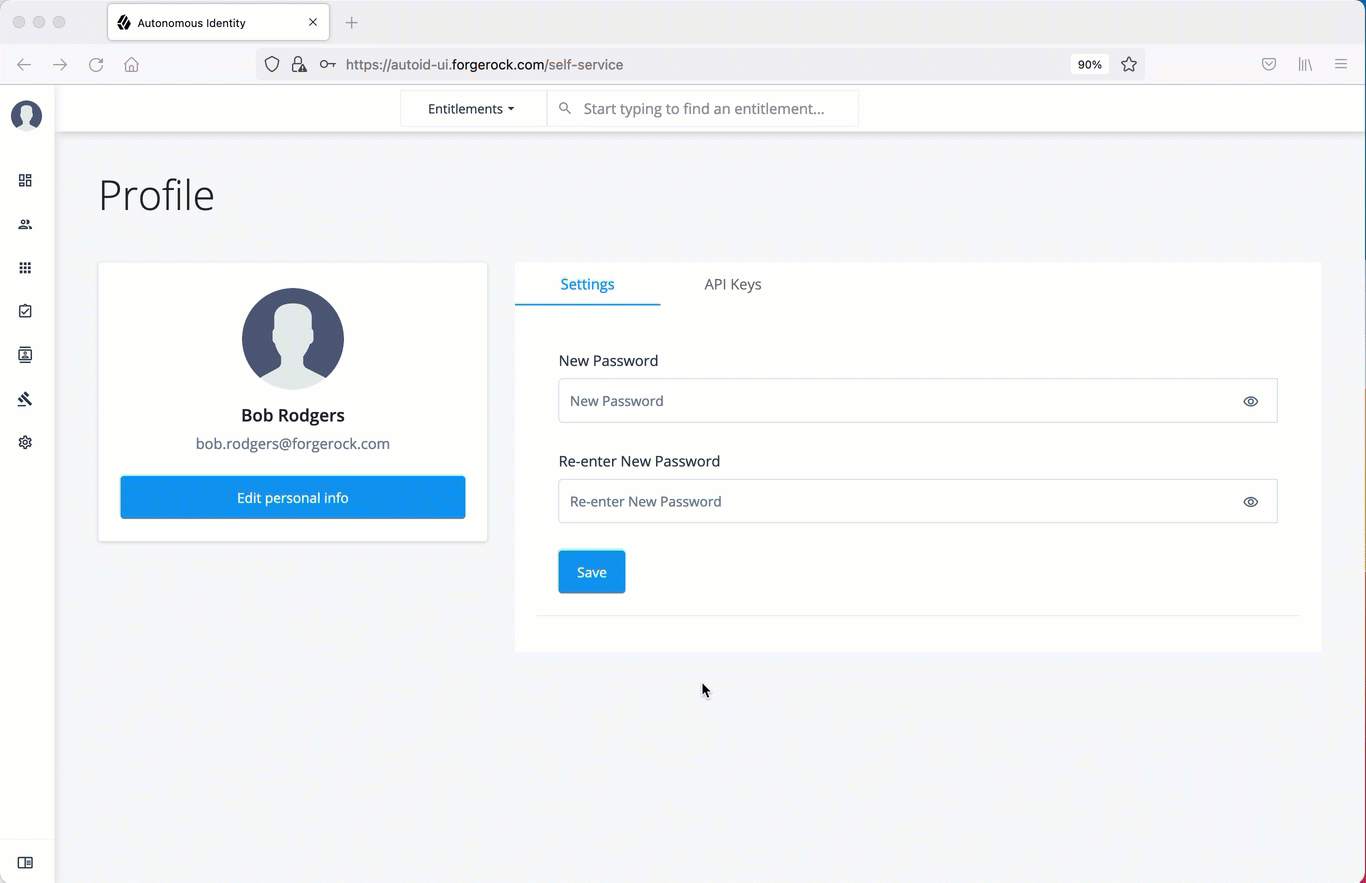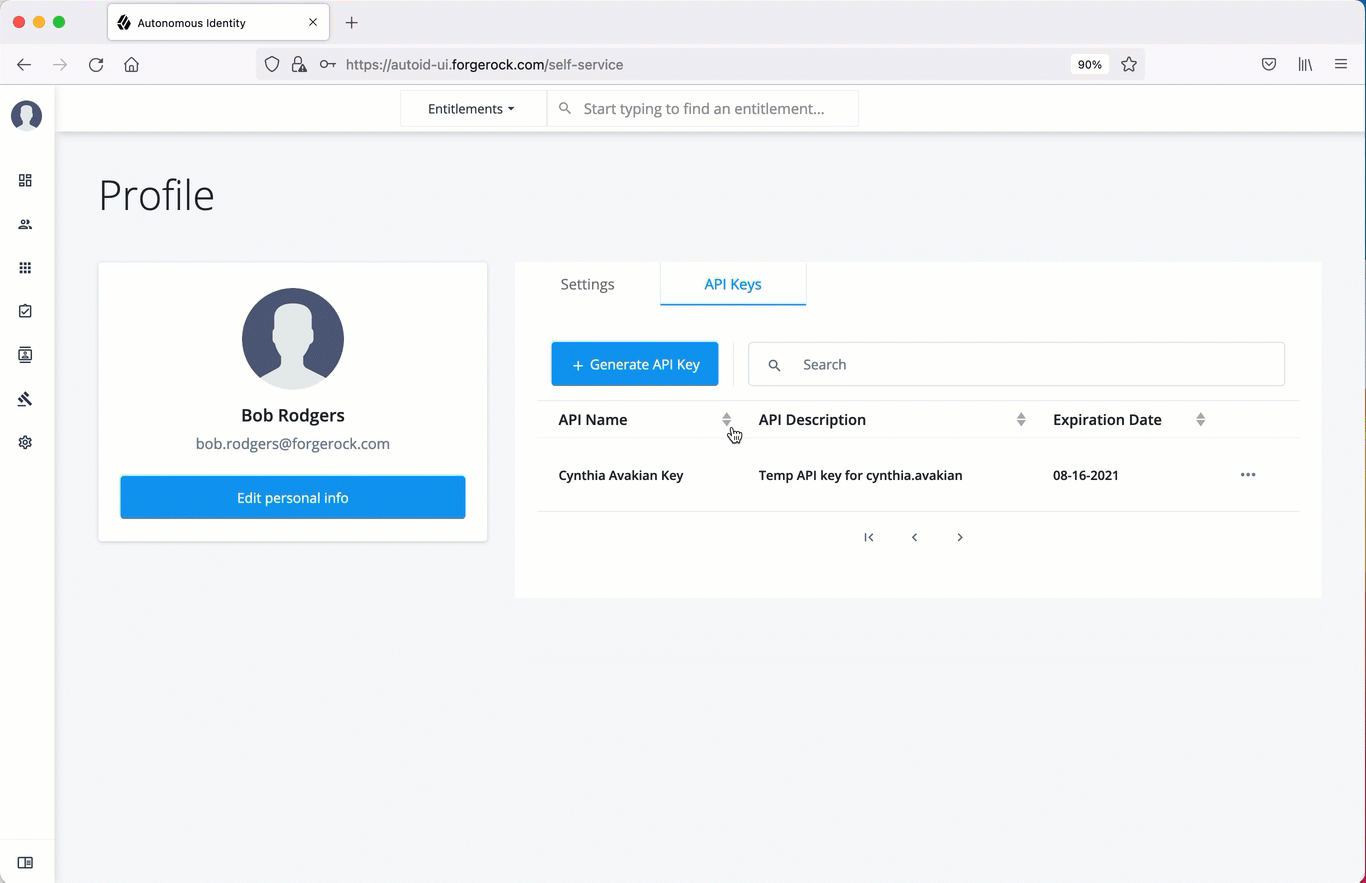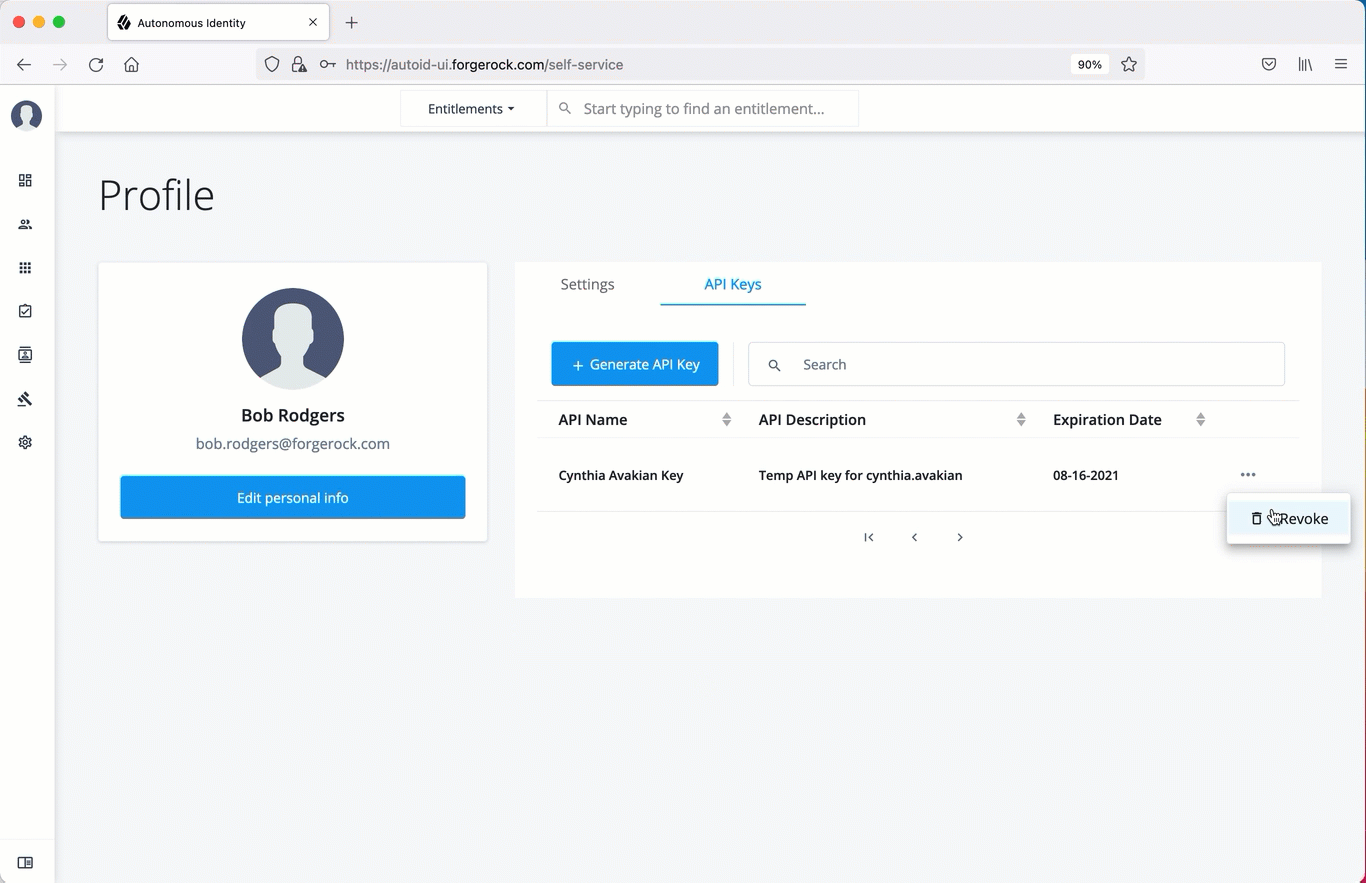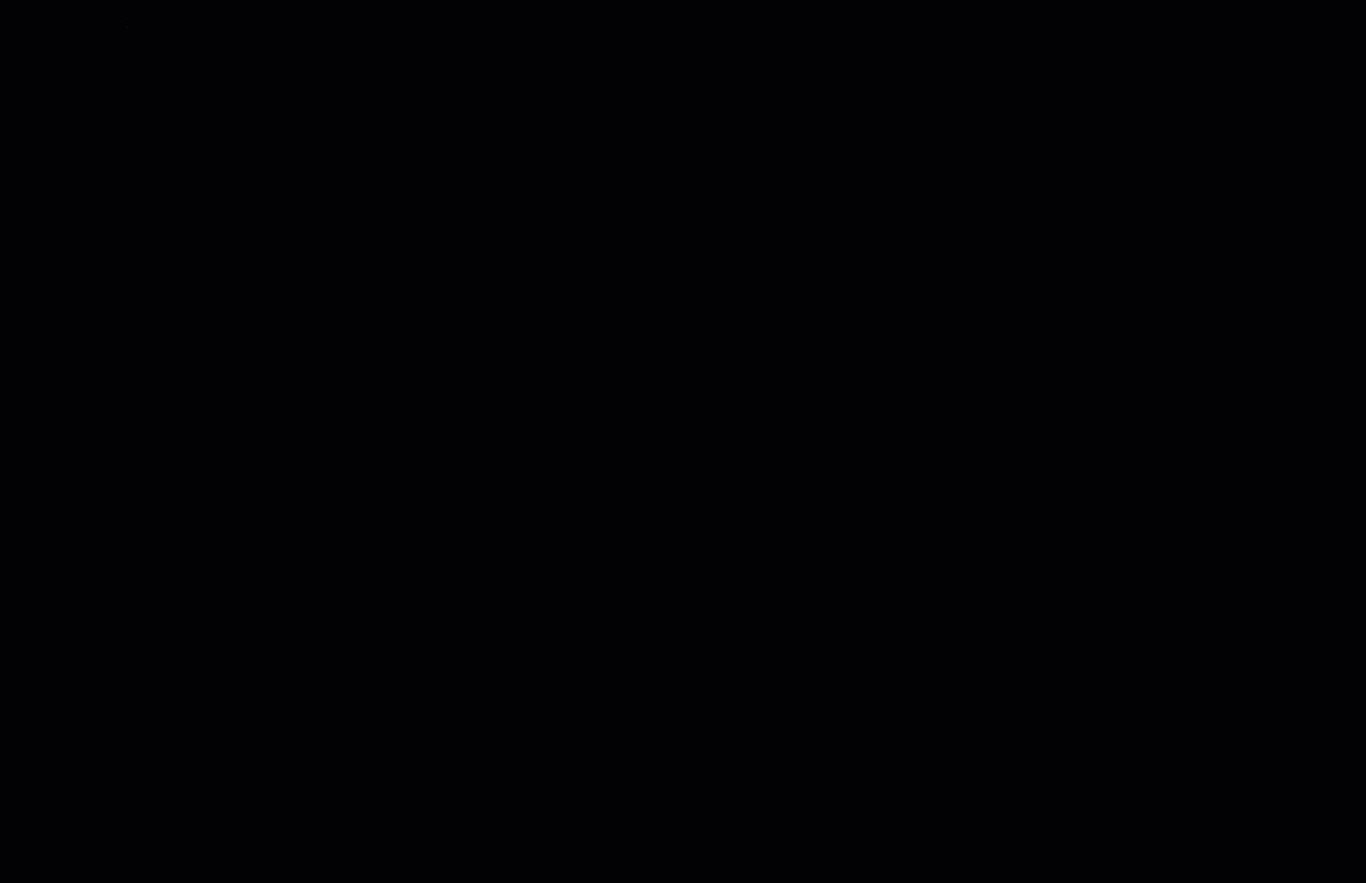
Create an API key using the UI
Administrators can create API keys on the Self-Service page of the Autonomous Identity UI.
-
On the Autonomous Identity UI, click the admin drop-down on the top-left of the page.
-
Click Self Service.
-
Click the API Keys tab.
-
Click Generate API Key.
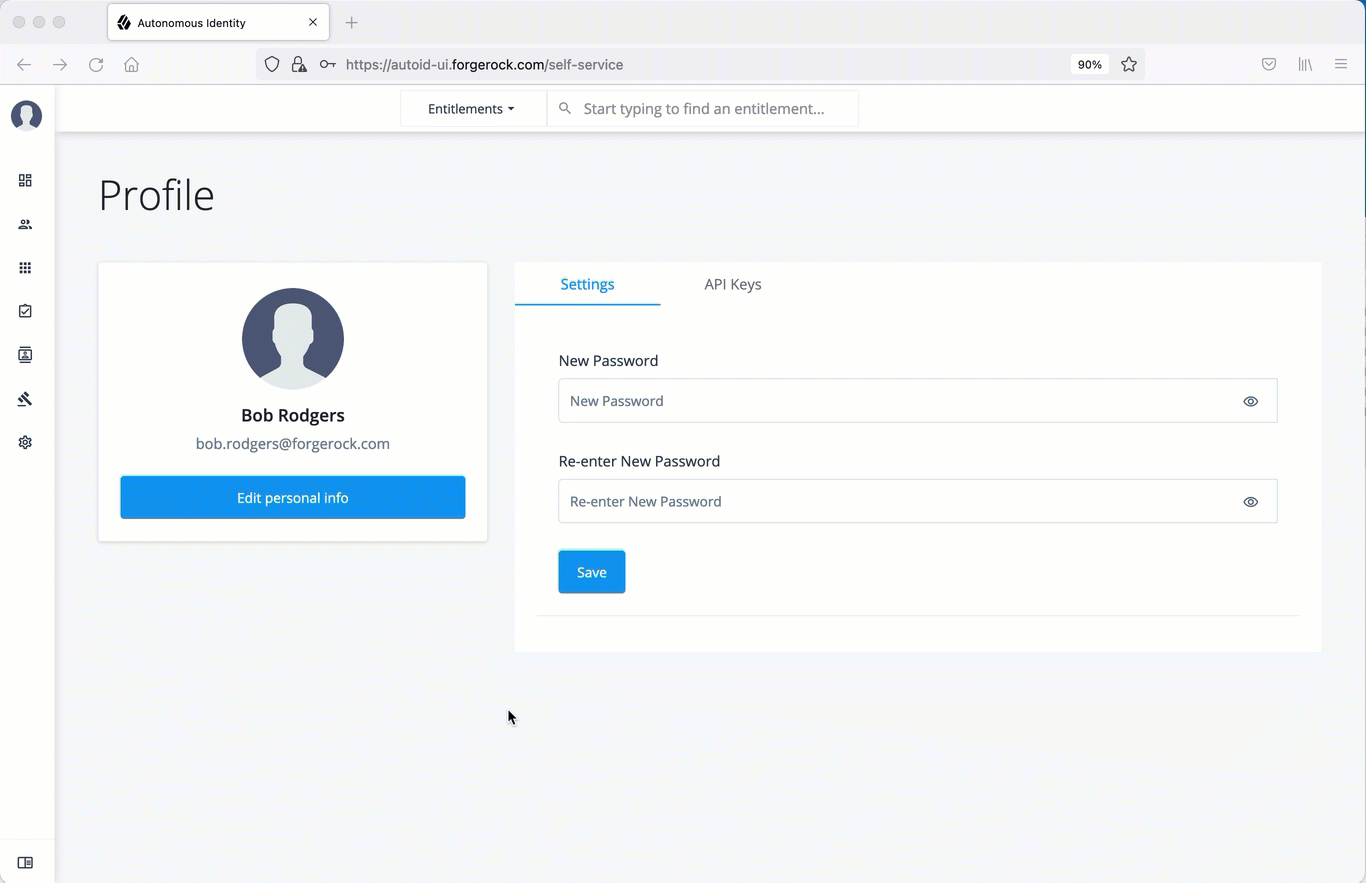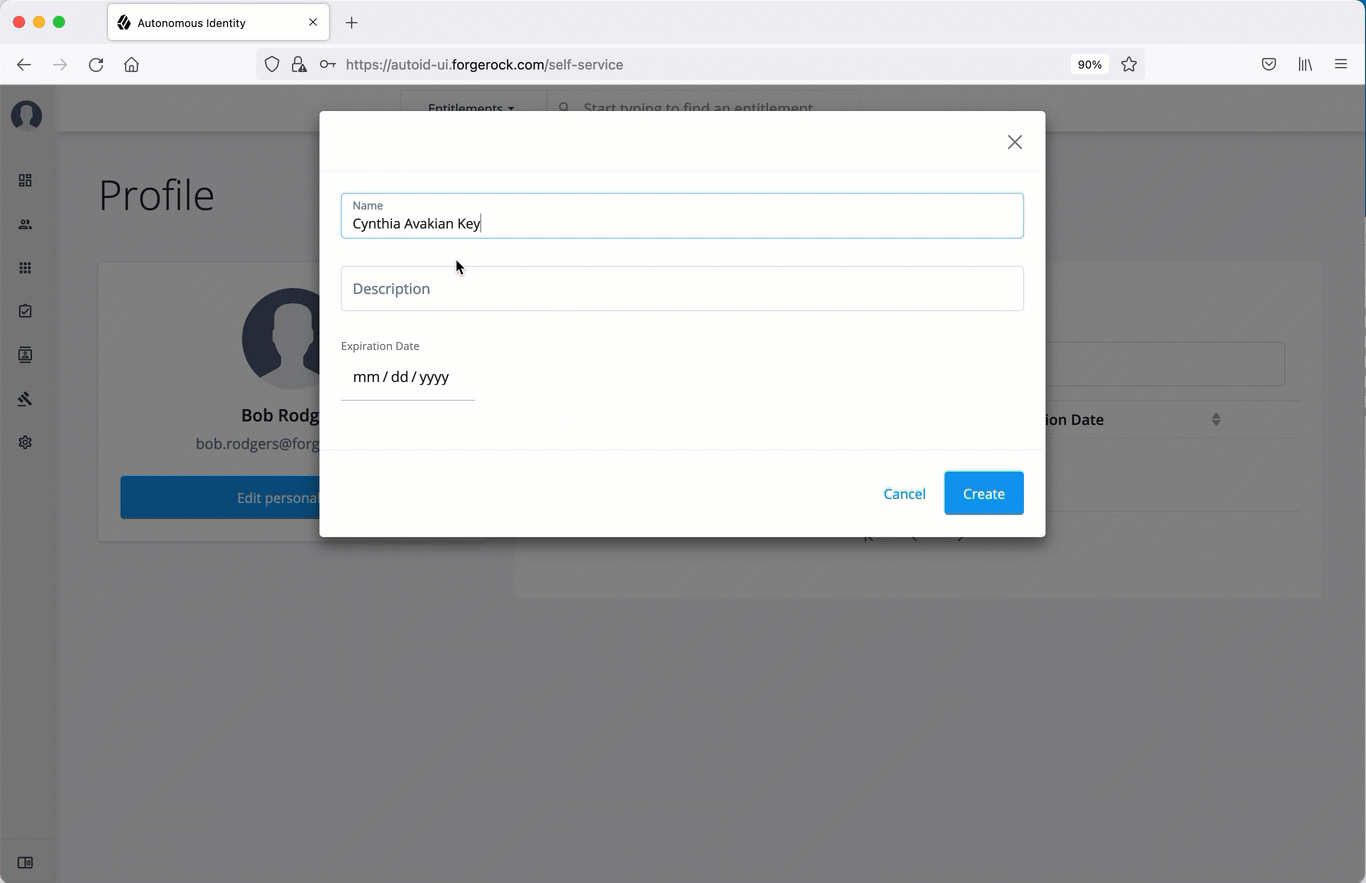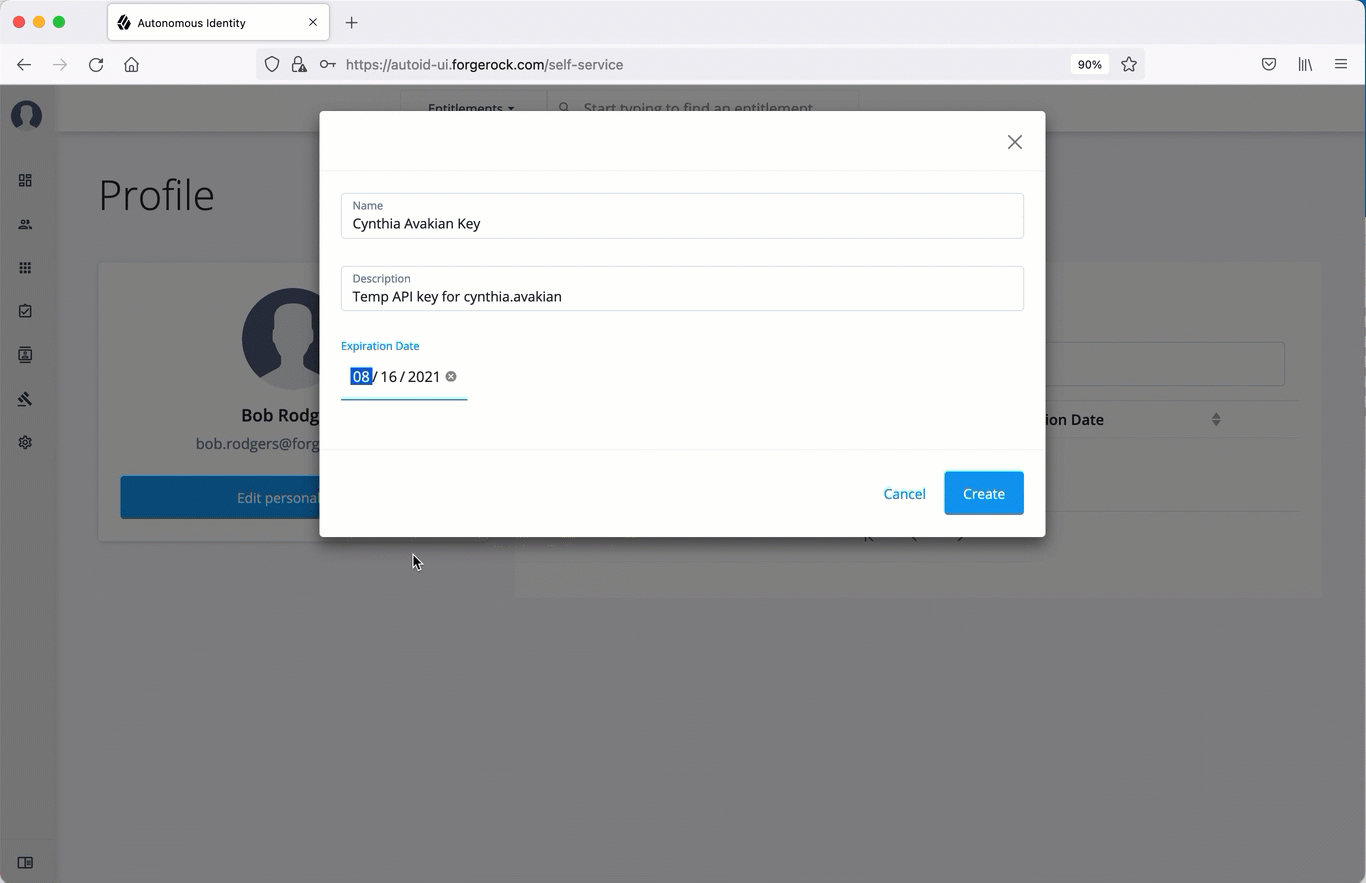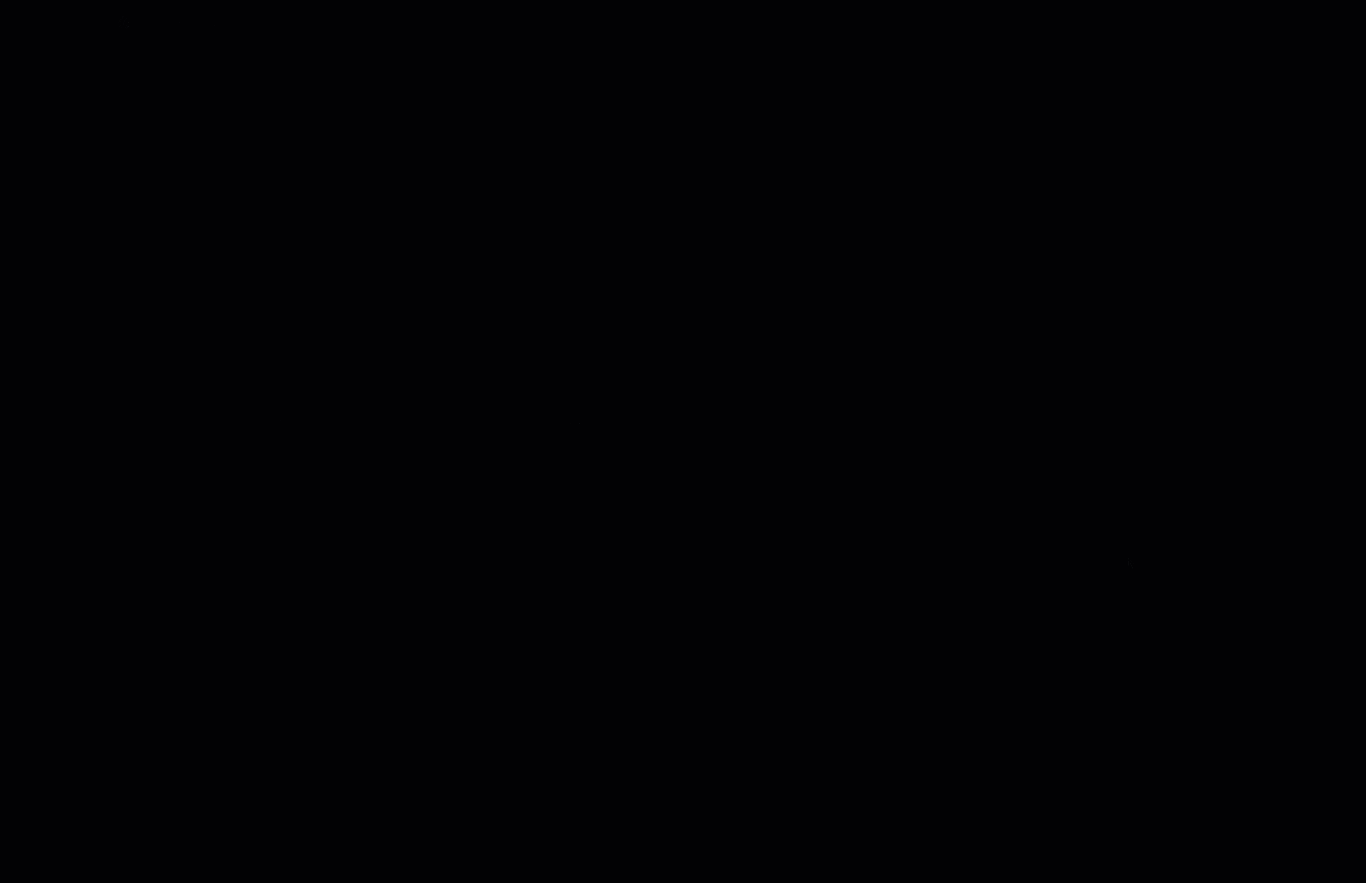
-
Set the name, description, and expiration date for API key, and then click Create.
-
Make sure to make a copy of the key in the box as it cannot be retrieved once the dialog box is closed. The new API key appears in the list of keys on the API Keys page.
Click an example
Deactivate API keys using the UI
Administrators can revoke or delete API keys. Use the following procedure to revoke an API key.
-
On the Autonomous Identity UI, click the admin drop-down on the top-left of the page.
-
Click Self Service.
-
Click the API Keys tab.
-
In the Search field, enter the API key.
-
In the list of API keys, click the three dots, and select Revoke. This action deletes the API key for use.
Click an example
Create an API key using curl
Administrators can create API keys on the command line using curl commands.
-
Open a terminal, and create an authentication bearer token for an admin user:
curl -k -X POST \ https://autoid-ui.forgerock.com/api/authentication/login \ -H 'Content-Type: application/json' \ -d '{ "username": "bob.rodgers@forgerock.com", "password": "Welcome123" }'
The response is:
{ "user": { "dn": "cn=bob.rodgers@forgerock.com,ou=People,dc=zoran,dc=com", "controls": [], "displayName": "Bob Rodgers", "gidNumber": "999", "uid": "bob.rodgers", "_groups": [ "Zoran User", "Zoran Admin" ] }, "token": "token_value” } -
Set the
TOKENenvironment variable:export TOKEN=token_value
-
Generate a new API key:
curl -k -X POST \ https://autoid-ui.forgerock.com/api/admin/createApiToken \ -H "Authorization: Bearer $TOKEN" \ -H 'Content-Type: application/json' \ -d ' { "name": "Ingest Key", "description": "API key for ingestion endpoints", "expiration": "2022-01-02" }'
The response is:
{ "token": "19412ace-1d99-44b2-88e0-16136fc5c77a" }
API key examples
The following curl example illustrates how to use the API key to get a datasource ID for an ingestion job:
-
Obtain an API key from an administrator. See Create API Keys.
-
Obtain the tenant ID using the environment variable.
$ env | grep TENANT_ID TENANT_ID=8700f5cb-eaca-461e-8c2e-245a25f2399d
-
Query Autonomous Identity’s Java API Service (JAS) to obtain a data source ID using the API Key (for example, '1b7789f0-6c2f-4afa-a84b-a65a28f5c1a1'):
curl 'https://autoid-ui.forgerock.com/jas/datasource/search' \ -H 'authority: autoid-ui.forgerock.com' \ -H 'sec-ch-ua: "Chromium";v="92", " Not A;Brand";v="99", "Google Chrome";v="92"' \ -H 'accept: application/json, text/plain, /' \ -H 'x-tenant-id: 8700f5cb-eaca-461e-8c2e-245a25f2399d' \ -H 'authorization: 1b7789f0-6c2f-4afa-a84b-a65a28f5c1a1' \ -H 'sec-ch-ua-mobile: ?0' \ -H 'user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36' \ -H 'content-type: application/json' \ -H 'origin: https://autoid-ui.forgerock.com' \ -H 'sec-fetch-site: same-origin' \ -H 'sec-fetch-mode: cors' \ -H 'sec-fetch-dest: empty' \ -H 'referer: https://autoid-ui.forgerock.com/data-sources' \ -H 'accept-language: en-US,en;q=0.9' \ --data-raw '{ "query": { "sort": [ { "datasource_id.keyword": { "order": "desc" } } ], "size": 10, "track_total_hits": true, "query": { "match_all": {} } } }' \ --compressed \ --insecure
The response includes the datasource ID:
{ "took": 8, "timed_out": false, "_shards": { "total": 3, "successful": 3, "skipped": 0, "failed": 0 }, "hits": { "total": { "value": 1, "relation": "eq" }, "max_score": null, "hits": [ { "_index": "autonomous-iam_common_datasources_latest", "_type": "_doc", "_id": "259b80c7693e92c4c29bd64deac4cd99826d427027645c9413afdb3f083b891d8d34cefaebd5fcf098c066dc1a4da2879d8732d59bfd2e239a285184f8e7a35b", "_score": null, "_source": { "datasource_id": "2d7a6a76-469c-4035-b312-fb1daf104e98", "name": "Showcase-CSV-DS", "sync_type": "full", "icon": "apps", "isActive": true, "entityTypes": { "/autoid/system/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98/applications": { "uri": { "file": "file:/data/input/applications.csv" } }, "/autoid/system/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98/assignments": { "uri": { "file": "file:/data/input/assignments.csv" } }, "/autoid/system/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98/entitlements": { "uri": { "file": "file:/data/input/entitlements.csv" } }, "/autoid/system/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98/identities": { "uri": { "file": "file:/data/input/identities.csv" } } }, "connectionSettings": { "csv": {} }, "metadata": { "contextId": "scripts", "entityType": "/common/datasources", "primaryKey": "2d7a6a76-469c-4035-b312-fb1daf104e98", "entityPath": "/common/datasources/2d7a6a76-469c-4035-b312-fb1daf104e98", "entityDefinition": "datasources", "namespace": "/common", "branch": "actual", "created": "2021-08-25T03:53:33.634Z", "tenantId": "autonomous-iam" } }, "sort": [ "2d7a6a76-469c-4035-b312-fb1daf104e98" ] } ] } } -
Make sure your client that accesses the JAS configuration has something similar to the following:
public static final String CONFIG_JAS_API_TOKEN = "JAS_API_KEY"; public static final String CONFIG_JAS_TENANT_ID = "TENANT_ID";
API service
The following are Autonomous Identity API Service endpoints:
GET /health-check
- GET /health-check
-
Check that the Autonomous Identity API service is running. Get uptime statistics. [All]
Endpoint
/health-check
Headers
Content-Type application/json
Body
Example Request
curl --request GET "<instance-IP>/health-check" \ --header "Content-Type: application/json"
Example Response
{ "status": "zoran-api: OK", "uptime": 5412.465875997, "uptimeFormatted": "1:30:12" }
Authentication
The following are Autonomous Identity authentication endpoints:
POST /api/authentication/login
- POST /api/authentication/login
-
Log in to the system. The endpoint accepts the
usernameandpasswordin the body of the request. The token provided has an expiry date that can be obtained by decoding the returned JWT and using theexpdata inside the token. [All]Endpoint
/api/authentication/login
Headers
Content-Type application/json
Body
{ "username": "admin@test.com", "password": "test" }Example Request
curl --location --request POST 'https://autoid-api.forgerock.com/api/authentication/login' \ --header 'Content-Type: application/json' \ --data-raw '{ "username": "admin@test.com", "password": "test" }'Example Response
{ "user": { "dn": "cn=test.user@test.com,dc=example,dc=org", "controls": [], "gidNumber": "7777", "uid": "test.user", "displayName": "Test User", "_groups": [ "Admin" ] }, "token": "123456" }
GET /api/authentication/verify
- GET /api/authentication/verify
-
Verify the authenticity of a bearer token.
Endpoint
/api/authentication/verify
Authorization
Token <token>
Headers
Content-Type application/json
Body
''
Example Request
curl --location --request GET 'https://autoid-api.forgerock.com/api/authentication/verify' \ --header 'Content-Type: application/json'
Example Response
{ "user": { "controls": [], "displayName": "Bob Rodgers", "email": "bob.rodgers@forgerock.com", "dn": "cn=bob.rodgers@forgerock.com,ou=People,dc=zoran,dc=com", "gidNumber": "999", "uid": "bob.rodgers", "_groups": [ "Zoran Admin" ], "iat": 1628893019, "exp": 1628936219, "aud": "http://my.service", "sub": "6711197" } }
POST /api/authentication/renewToken
- POST /api/authentication/renewToken
-
Renew a token for the system. The endpoint accepts the JWT in the header
Authorization: Bearer JWT. The expiry time of the token is reset and return in the new token. [All]Endpoint
/api/authentication/renewToken
Authorization
Token <token>
Headers
Content-Type application/json
Body
''
Example Request
curl --location --request POST 'https://autoid-api.forgerock.com/api/authentication/renewToken' \ --header 'Content-Type: application/json' \ --data-raw ''
Example Response
{ "user": { "dn": "cn=test.user@test.com,dc=example,dc=org", "controls": [], "gidNumber": "7777", "uid": "test.user", "displayName": "Test User", "_groups": [ "Admin" ] }, "token": "123456" }
GET /api/authentication/actions
- GET /api/authentication/actions
-
Retrieve the permitted actions of the currently authenticated user. [All]
Endpoint
/api/authentication/action
Headers
Content-Type application/json
Example Request
curl --location --request GET 'https://autoid-api.forgerock.com/api/authentication/actions' \ --header 'Content-Type: application/json'
Example Response
{ "userActions": [ "*" ], "roleTitle": "Unknown", "homepage": "company" }
SSO
The following are Autonomous Identity SSO endpoints:
GET /api/sso/start
- GET /api/sso/start
-
Endpoint to initiate SSO. [All]
Endpoint
/api/sso/start
Authorization
Token <token>
Headers
Content-Type /
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/sso/start" \ --header "Content-Type: /"
Config
The following are Autonomous Identity config endpoint:
GET /api/config
- GET /api/config
-
Get the configuration. This endpoint is mainly used by the Autonomous Identity UI microservice to get values stored in Consul. [All]
Endpoint
/api/config
Headers
Content-Type application/json
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/config" \ --header "Content-Type: application/json"
Example Response
{ "thresholds": { "top": 1.01, "high": 0.75, "medium": 0.35, "low": 0, "autoAccess": 0.5 }, "volumeThresholds": { "high": 90, "low": 20 }, "mostAssignedStats": { "count": 100 }, "highVolumeStats": { "high": { "minScore": 0.9, "minUsersCount": 100 }, "low": { "maxScore": 0.2, "minUsersCount": 100 } }, "authorizers": { "ldap": true, "oidc": false } }
GET /api/admin/reloadUIConfig
- GET /api/admin/reloadUIConfig
-
Reload justification and filterable attributes configuration from JAS. [User, Supervisor, Ent Owner, App Owner, Admin]
Endpoint
/api/admin/reloadUIConfig
Headers
Content-Type /
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/admin/reloadUIConfig" \ -H "accept: /"
POST /api/admin/updateUser
- POST /api/admin/updateUser
-
Update credentials for a user.
Endpoint
/api/admin/updateUser
Authorization
<Bearer Token JWT-value>
Body
{ email: “john.doe@forgerock.com”, password: “password”, groups: [“Zoran Supervisor”, “Zoran Role Engineer”] }Example Request
curl --location --request POST 'https://autoid-api.forgerock.com/api/admin/updateUser' \ --header 'Content-Type: application/json' \ --header 'Authorization: Bearer <token>' \ --data-raw '{ “email”: “john.doe@forgerock.com”, “password”: “password”, “groups”: [“Zoran Supervisor”, “Zoran Role Engineer”] }'Example Response
{ message: 'success' }
POST /api/admin/updateSelf
- POST /api/admin/updateSelf
-
Update credentials for a user.
Endpoint
/api/admin/updateSelf
Authorization
<Bearer Token JWT-value>
Body
{ email: “john.doe@forgerock.com”, password: “password”, groups: [“Zoran Supervisor”, “Zoran Role Engineer”] }Example Request
curl --location --request POST 'https://autoid-api.forgerock.com/api/admin/updateSelf' \ --header 'Content-Type: application/json' \ --header 'Authorization: Bearer <token>' \ --data-raw '{ “email”: “john.doe@forgerock.com”, “password”: “password”, “groups”: [“Zoran Supervisor”, “Zoran Role Engineer”] }'Example Response
{ message: 'success' }
POST /api/admin/disableUser
- POST /api/admin/disableUser
-
Disable user account.
Endpoint
/api/admin/disableuser
Authorization
<Bearer Token JWT-value>
Body
{ email: “john.doe@forgerock.com“ }Example Request
curl --location --request POST 'https://autoid-api.forgerock.com/api/admin/disableUser' \ --header 'Content-type: application/json' \ --header 'Authorization: Bearer <token>' \ --data-raw '{ “email”: “john.doe@forgerock.com” }'Example Response
{ message: 'success' }
POST /api/admin/enableUser
- POST /api/admin/enableUser
-
Enable a user account.
Endpoint
/api/admin/enableUser
Authorization
<Bearer Token JWT-value>
Body
{ email: “john.doe@forgerock.com” }Example Request
curl --location --request POST "https://autoid-api.forgerock.com/api/admin/enableUser" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" \ --data-raw '{ “email”: “john.doe@forgerock.com” }'Example Response
{ message: 'success' }
POST /api/admin/createUser
- POST /api/admin/createUser
-
Create credentials for a user
Endpoint
/api/admin/createUser
Authorization
<Bearer Token JWT-value>
Body
{ dn: “cn=john.doe@forgerock.com,ou=People,dc=zoran,dc=com”,gidNumber: “321”, email: “john.doe@forgerock.com“, password: “password”, controls: [], displayName: “John Doe”, uid: “john.doe”, groups: [“Zoran Admin”] }Example Request
curl --request POST "https://autoid-api.forgerock.com/api/admin/createUser" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" \ --data-raw '{ dn: “cn=john.doe@forgerock.com,ou=People,dc=zoran,dc=com”,gidNumber: “321”, email: “john.doe@forgerock.com“, password: “password”, controls: [], displayName: “John Doe”, uid: “john.doe”, groups: [“Zoran Admin”] }'Example Response
{ message: 'success' }
POST /api/admin/createApiToken
- POST /api/admin/createApiToken
-
Create API credentials (token) for a user.
Endpoint
/api/admin/createApiToken
Authorization
<Bearer Token JWT-value>
Body
{ name: “John Doe“, description: “description”, expiration: “2021-08-12T12:00:00.000Z” }Example Request
curl --request POST "https://autoid-api.forgerock.com/api/admin/createApiToken" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" \ --data-raw '{ name: “John Doe“, description: “description”, expiration: “2021-08-12T12:00:00.000Z” }’Example Response
{ token: uuid }
POST /api/admin/revokeApiToken
- POST /api/admin/revokeApiToken
-
Revoke API credentials for a user.
Endpoint
/api/admin/revokeApiToken
Authorization
<Bearer Token JWT-value>
Body
{ token: “11b57769-d436-4357-bc1c-0e0b9c6a49b6“ }Example Request
curl --location --request POST "https://autoid-api.forgerock.com/api/admin/revokeApiToken" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" \ --data-raw '{ token: “11b57769-d436-4357-bc1c-0e0b9c6a49b6“ }’Example Response
{ message: 'User token disabled' }
GET /api/admin/verifyApiToken/{token}
- GET /api/admin/verifyApiToken/{token}
-
Verify that an API token is valid
Endpoint
/api/admin/verifyApiToke
Authorization
<Bearer Token JWT-value>
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/admin/verifyApiToken/da0b5228-1e11-4278-ad1c-f0938fccdf82" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>"
Example Response
{ "name": "John Doe", "description": "description", "expiration": "2021-08-17T12:00:00.000Z", "is_valid": true, "creator": "bob.rodgers@forgerock.com", "modifier": "bob.rodgers@forgerock.com" }
GET /api/admin/getTokens
- GET /api/admin/getTokens
-
Get a list of tokens.
Endpoint
/api/admin/getTokens
Authorization
<Bearer Token JWT-value>
Body
{ maxResults: 6, offset: 5 }Example Request
curl --request GET "https://autoid-api.forgerock.com/api/admin/getTokens" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" \ --data-raw '{ maxResults: 6, offset: 5 }’Example Response
[{ “token”: “da0b5228-1e11-4278-ad1c-f0938fccdf82”, "name": "John Doe", "description": "description", "expiration": "2021-08-17T12:00:00.000Z", "is_valid": true, "creator": "bob.rodgers@forgerock.com", "modifier": "bob.rodgers@forgerock.com" }]
GET /api/admin/getUsers
- GET /api/admin/getUsers
-
Get a list of users.
Endpoint
/api/admin/getUsers
Authorization
<Bearer Token JWT-value>
Body
{ maxResults: 6, offset: 5, sortBy: uid | displayName | gidNumber }Example Request
curl --location --request GET "https://autoid-api.forgerock.com/api/admin/getUsers" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" \ --data-raw '{ maxResults: 6, offset: 5, sortBy: uid }’Example Response
[{ "controls": [], "displayName": "David Elliott", "email": "david.elliott@forgerock.com", "dn": "cn=david.elliott@forgerock.com,ou=People,dc=zoran,dc=com", "gidNumber": "809", "uid": "david.elliott", "_groups": [ "Zoran Entitlement Owner" ], "enabled": true }]
Report
Autonomous Identity captures information in its log files that are useful when troubleshooting problems. You can access the reports using REST calls to the Report API endpoint.
POST /api/report
- POST /api/report
-
Get reporting data. [All]
Endpoint
/api/report
Authorization
<Bearer Token JWT-value>
Headers
Content-Type application/json
Params
fields
Body
{ "fields": [ "id", "type", "batch_id", "original", "update" ], "reportType": "EventBasedCertification" }Example Request
curl --request POST "https://autoid-api.forgerock.com/api/report" \ --header "Content-Type: application/json" \ --header 'Authorization: Bearer <token>' \ --data-raw '{ "fields": [ "id", "type", "batch_id", "original", "update" ], "reportType": "EventBasedCertification" }'
Company View
The following are Autonomous Identity company view endpoints:
GET /api/companyview
- GET /api/companyview
-
Get the data for company overview dashboard data. [Executive, Admin]
Endpoint
/api/companyview
Authorization
<Bearer Token JWT-value>
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/companyview" \ --header "Content-Type: application/json"
Example Response
{ "companyView": { "employeeTypes": [ { "type": "Employee", "high": 723, "low": 27, "medium": 1796, "null_conf": 0, "total": 2546 }, { "type": "Non-Employee", "high": 867, "low": 14, "medium": 1768, "null_conf": 0, "total": 2649 } ], "employees_wo_manager": 0, "employees_w_manager": 5200, "entitlements_without_roleowners": 0, "entitlements_with_roleowners": 2456, "total_employees": 5200, "coverage": { "total": 2456, "covered": 2456, "not_covered": 0 }, "entitlementsDistribution": { "no_users": 0, "one_user": 0, "zero_to_five_users": 1, "five_to_ten_users": 1064, "ten_to_hundred_users": 1549, "hundred_to_onek_user": 35, "onek_to_tenk_users": 0, "tenk_users": 0, "hundredk_users": 0 } } }
GET /api/companyview/allEntitlementsAvgGroups
- GET /api/companyview/allEntitlementsAvgGroups
-
Get the average confidence score list for the company view chart. [Executive, Admin]
Endpoint
/api/companyview/allEntitlementAvgGroups
Authorization
<Bearer Token JWT-value>
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/companyview/allEntitlementAvgGroups" \ --header "Content-Type: application/json"
Example Response
{ "entitlementList": [ { "start": 0, "end": 0.05, "entitlementCount": 2 }, { "start": 0.06, "end": 0.1, "entitlementCount": 14 } ] }
GET /api/companyview/mostCriticalEntitlements
- GET /api/companyview/mostCriticalEntitlements
-
Get the most critical entitlements list. [Executive, Admin]
Endpoint
/api/companyview/mostCriticalEntitlements
Authorization
<Bearer Token JWT-value>
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/companyview/mostCriticalEntitlements" \ --header "Content-Type: application/json"
Example Response
[ { "org": "organization", "entt_id": "ent1", "avg_conf_score": 0.04, "entt_name": "Ent 1", "high": 0, "low": 1, "medium": 0, "seq": 0, "total_employees": 6 }, { "org": "organization", "entt_id": "ent2", "avg_conf_score": 0.04571, "entt_name": "Ent 2", "high": 0, "low": 1, "medium": 0, "seq": 1, "total_employees": 7 } ]
GET /api/companyview/assignmentStats
- GET /api/companyview/assignmentStats
-
Get the total assignments, low/high confidence, high volume and low/high confidence, most assigned [Executive, Admin]
Endpoint
/api/companyview/assignmentsStats
Authorization
<Bearer Token JWT-value>
Params
assignmentLimit 1 highVolumeHighMinScore 0.9 highVolumentHighMinUsersCount 100 highVolumenLowMaxScore 0.2 highVolumeLowMinUsersCount 100
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/companyview/assignmentsStats?assignmentsLimit=5" \ --header "Content-Type: application/json"
Example Response
{ "total": 47670, "high": 13145, "low": 4992, "unscored": 4986, "mostAssigned": [ { "count": 344, "entitlement": "ent1" } ], "mostAssignedCount": 35, "highVolume": { "high": 23, "low": 17 } }
GET /api/companyview/assignmentHistConfSummary/{year}/{month}
- GET /api/companyview/assignmentHistConfSummary/{year}/{month}
-
Get the number of high, medium, and low confidence assignments for the past 12-month period ending in a given year and month. [Executive, admin]
Endpoint
/api/companyview/assignmentsHistConfSummary/2020/01
Authorization
<Bearer Token JWT-value>
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/companyview/assignmentsHistConfSummary/2020/1" \ --header "Content-Type: application/json"
Example Response
[ { "year": 0, "month": 0, "highConf": 0, "medConf": 0, "lowConf": 0, "total": 0 } ]
User Details
The following are Autonomous Identity user details endpoints:
POST /api/userDetails
- POST /api/userDetails
-
Obtain the employee details for Identities views. [User, Supervisor, Ent Owner, App Owner, Admin] NOTE: This is a POST due to the endpoint receiving a JSON body query.
Endpoint
/api/userDetails
Authorization
<Bearer Token JWT-value>
Headers
Content-Type application/json
Body
{ "employeeId": "john.doe", "sortDir": "asc, desc", "lastEntitlementId": "Web_NAS_Share_Case Management_7HQ", "lastRecommendedEnttId": "string" }Example Request
curl --request POST "https://autoid-api.forgerock.com/api/userDetails" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" \ --data-raw '{ "employeeId": "john.doe", "sortDir": "asc, desc", "lastEntitlementId": "Web_NAS_Share_Case Management_7HQ", "lastRecommendedEnttId": "string" }'Example Response
{ "recommendedEntt": { "predictions": [ { "usr_key": "john.doe", "ent": "ent1", "conf": "0.88", "freq": "10.0", "frequnion": "9", "rule": [ { "title": "Chief", "value": "Yes" }, { "title": "Employee Type", "value": "Employee" } ], "entt": { "entitlement": "Ent 1", "app_id": "app1", "role": "role.owner", "app_name": "App 1", "entitlement_name": "Ent 1", "high_risk": "High", "roleOwnerDisplayName": "Role Owner", "requestorCanAccess": false } }, { "usr_key": "john.doe", "ent": "ent2", "conf": "1.00", "freq": "4.0", "frequnion": "4", "rule": [ { "title": "Job Code Name", "value": "Business Representitive" }, { "title": "Line of Business", "value": "Portfolio Management" }, { "title": "Department", "value": " South" }, { "title": "Employee Type", "value": "Employee" } ], "entt": { "entitlement": "ent2", "app_id": "app1", "role": "role.owner", "app_name": "App 1", "entitlement_name": "Ent 2", "high_risk": "High", "roleOwnerDisplayName": "Role Owner", "requestorCanAccess": true } } ], "entitlementsCount": 14, "entitlementsRemainingCount": 9, "lastEntitlementId": "ent2" }, "userEntt": [ { "user": "john.doe", "entitlement": "ent3", "app_id": "app1", "app_name": "App 1", "entitlement_name": "Ent 3", "freq": "10.0", "frequnion": "9", "high_risk": "High", "justification": [ { "title": "Chief", "value": "Yes" }, { "title": "Employee Type", "value": "Employee" } ], "score": 0.88, "user_name": "John Doe", "lastAccessed": "2020-01-01 00:00:00", "requestorCanAccess": false, "rawJustification": [ "CHIEF_YES_NO_Yes", "USR_EMP_TYPE_Employee" ] }, { "user": "john.doe", "entitlement": "ent4", "app_id": "app1", "app_name": "App 1", "entitlement_name": "Ent 4", "freq": "4.0", "frequnion": "4", "high_risk": "High", "justification": [ { "title": "Job Code Name", "value": "Business Representitive" }, { "title": "Line of Business", "value": "Portfolio Management" }, { "title": "Department", "value": " South" }, { "title": "Employee Type", "value": "Employee" } ], "score": 1, "user_name": "John Doe", "lastAccessed": "2020-01-01 00:00:00", "requestorCanAccess": false, "rawJustification": [ "JOBCODE_NAME_Business Representitive", "LINE_OF_BUSINESS_Portfolio Management", "USR_DEPARTMENT_NAME_Customer Operations_ South", "USR_EMP_TYPE_Employee" ] } ], "user": { "displayName": "John Doe", "hrData": [ { "title": "Job Code Name", "id": "JOBCODENAME", "value": "Business Representitive" }, { "title": "Line of Business", "id": "LINEOFBUSINESS", "value": "Portfolio Management" }, { "title": "Department", "id": "DEPARTMENT", "value": " South" }, { "title": "Employee Type", "id": "EMPTYPE", "value": "Employee" } ] }, "entitlementsCount": 2, "entitlementsRemainingCount": 9, "lastEntitlementId": "ent4" }
GET /api/userDetails/decisions
- GET /api/userDetails/decisions
-
Get the current entitlement decisions for the user [Supervisor, Ent Owner, App Owner, Admin].
Endpoint
/api/userDetails/decisions
Authorization
<Bearer Token JWT-value> OR <API-KEY>
Query Parameters Parameter Type Description user
string
User ID (required)
filter
object
Filter to add (single property shown below)
Filter Query Object Properties Parameter Type Description datasinkStatus
string
Datasink status filter ('ack' or 'nack')
timestampThresholds
timestampThresholds object
Timestamp threshold object (available properties below)
timestampThresholds Object Properties Parameter Type Description gt
string
Greater than timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with gte.
gte
string
Greater than or equal timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with gt.
lt
string
Less than timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with lte.
lte
string
Less than or equal timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with le.
Example Request (DatasinkStatus Filter)
curl -k -X GET \ 'datasinkStatus=nack' \ -H 'Authorization: Bearer <token value>' \ <or> -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json'
Example Response (DatasinkStatus Filter)
{ "decisions": [ { "user": "john.doe", "entitlement": "ent_1", "is_certified": false, "is_revoked": false, "is_processed": false, "is_archived": false, "author": "jane.smith", "author_name": "Jane Smith", "author_type": "Zoran Admin", "reason": null, "last_updated": "2022-01-11T19:48:17.195Z", "datasink_status": "nack", "usr_name": "John Doe", "ent_name": "Entitlement 1", "app_id": "Gateway", "app_name": "Gateway", "usr_manager_id": "john.smith", "conf": 0.75, "freq": 4, "freqUnion": 3 } ] }
POST /api/userDetails/decisions
- POST /api/userDetails/decisions
-
Update entitlement decisions for users. [Supervisor, Ent Owner, App Owner, Admin]
Endpoint
/api/userDetails/decisions
Authorization
<Bearer Token JWT-value>
Request Body Parameters Parameter Type Description assignments
array of assignment objects
List of assignments affected by the decision (available properties listed below)(required)
is_certified
boolean
Certification decision
is_revoked
boolean
Revoke decision
is_requested
boolean
Decision is processed
reason
string
Reason for decision
datasink_status
string
Datasink status ('ack' or 'nack')
Assignments Object Properties Parameter Type Description user
string
User ID (required)
entitlements
string array
List of entitlement ID’s (required)
Body
{ "assignments": [ { "user": "string", "entitlements": [ "string" ] } ], "is_certified": true, "is_revoked": true, "is_requested": true, "is_processed": true, "reason": "string", "datasink_status": "nack" }Example Request
curl -k -X POST \ "https://autoid-api.forgerock.com/api/userDetails/decisions" \ -H 'Authorization: Bearer <token-value>' \ -H "accept: /" -H "Content-Type: application/json" \ --data-raw '{ "assignments": [ { "user": "john.doe", "entitlements": [ "ABC", "DEFFF" ] } ], "is_certified": true, "is_revoked": false, "is_requested": false, "is_processed": false, "reason": "string", "datasink_status": "nack" }'Example Response
{ "status": 200 }
POST /api/userDetails/hrData
- POST /api/userDetails/hrData
-
Get a user’s HR data. [User, Supervisor, Ent Owner, App Owner, Admin]
Endpoint
/api/userDetails/hrData
Authorization
<Bearer Token JWT-value>
Headers
Content-Type application/json
Body
{ "employeeId": "john.doe" }Example Request
curl --request POST "https://autoid-api.forgerock.com/api/userDetails/hrData" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" \ --data-raw '{ "employeeId": "john.doe" }'Example Response
{ "user": [ { "id": "USER_NAME", "title": "User Name", "value": "john.doe" }, { "id": "CHIEF", "title": "Chief", "value": "Yes" }, { "id": "CITY", "title": "City", "value": "Toledo" }, { "id": "USER_DISPLAY_NAME", "title": "User Display Name", "value": "John Doe" }, { "id": "EMPLOYEE_TYPE", "title": "Employee Type", "value": "Employee" }, { "id": "MANAGER", "title": "Manager", "value": "the.manager" } ], "displayName": "John Doe" }
POST /api/userDetails/search
- POST /api/userDetails/search
-
Search for users by name and with applied filters. [Executive, Supervisor, App Owner, Admin]
Endpoint
/api/userDetails/search
Authorization
<Bearer Token JWT-value>
Headers
Content-Type application/json
Body
{ "username": "john.doe" }Example Request
curl --request POST "https://autoid-api.forgerock.com/api/userDetails/search" \ --header "Content-Type: application/json" --data-raw '{ "username": "john.doe" }'Example Response
{ "values": [ { "user": "john.doe", "isapplicationowner": "false", "isentitlementowner": "false", "issupervisor": "false", "userdisplayname": "John Doe" } ] }
POST /api/userDetails/ent/autoprovision
- POST /api/userDetails/ent/autoprovision
-
Get user’s entitlements for autoprovisioning. [Admin]
Endpoint
/api/userDetails/ent/autoprovision
Authorization
<Bearer Token JWT-value>
Headers
Content-Type application/json
Body
{ "user": "john.doe" }Example Request
curl --request POST "https://autoid-api.forgerock.com/api/userDetails/ent/autoprovision" \ --header "Content-Type: application/json" \ --header 'Authorization: Bearer <token>' \ --data-raw '{ "user": "john.doe" }'Example Response
{ "usr_id": "string", "usr_name": "string", "ents": [ { "ent_id": "string", "ent_name": "string", "ent_attribute": "string", "ent_risk_level": "string", "score": 0, "freq": 0, "frequnion": 0, "justification": [ { "title": "string", "value": "string" } ], "app_id": "string", "app_name": "string" } ], "cursor": "string" } No links
POST /api/userDetails/autoAction
- POST /api/userDetails/autoAction
-
Get the list of entitlements for a user or list of users for an entitlement to provision, revoke, or certify. [Admin]
Endpoint
/api/userDetails/autoAction
Authorization
<Bearer Token JWT-value>
Headers
Content-Type application/json
Body
{ "action": "addAccess", "usrId": "john.doe", "entId": "entitlement_1", "thresholds": { "gte": 0, "gt": 0, "lte": 0, "lt": 0 }, "cursor": "string" }Example Request
curl --request POST "https://autoid-api.forgerock.com/api/userDetails/autoAction" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" \ --data-raw '{ "action": "addAccess", "usrId": "john.doe", "entId": "entitlement_1", "thresholds": { "gte": 0, "gt": 0, "lte": 0, "lt": 0 }, "cursor": "string" }'
POST /api/userDetails/drivingFactor
- POST /api/userDetails/drivingFactor
-
Get the driving factor data. [User, Supervisor, Ent Owner, App Owner, Admin]
Endpoint
/api/userDetails/drivingFactor
Authorization
<Bearer Token JWT-value>
Headers
Content-Type application/json
Params
{ "entitlement": "entitlement1" }Example Request
curl --request POST "https://autoid-api.forgerock.com/api/userDetails/drivingFactor" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" \ --data-raw '{ "entitlement": "entitlement1" }'Example Request
[ { "ent": "ent1", "attribute": { "title": "Chief", "value": "No" }, "count": 3, "rawAttribute": "CHIEF_YES_NO_No" }, { "ent": "ent1", "attribute": { "title": "City", "value": "Tacoma" }, "count": 5, "rawAttribute": "CITY_Tacoma" } ]
POST /api/userDetails/distinct
- POST /api/userDetails/distinct
-
Get a list of all users.
Endpoint
/api/userDetails/distinct
Authorization
<Bearer Token JWT-value>
Headers
Content-Type application/json
Params
pageSize number (optional) Specify the number of assignments to return per page cursor (optional) String (Indicator on where to start a 2+ page list) <searchable-attribute> Any searchable attribute specified in the Identities Entity Definitions page
Body
{ "pageSize": 2, "cursor": "eyJ1c3JfaWQiOiJtYXJ5LmRvbm92YW4ifQ==", "cost_center": "OP" }Example Request
curl --request POST "https://autoid-api.forgerock.com/api/userDetails/distinct" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" --data-raw { "pageSize": 2, "cursor": "eyJ1c3JfaWQiOiJtYXJ5LmRvbm92YW4ifQ==", "cost_center": "OP" }Example Response
[ { "usr_id": "john.doe", "usr_name": "John Doe", "usr_manager_id": "jane.smith", "cost_center": "OP_TT4" } ]
Single view with application
| This endpoint has been deprecated in this release and will be removed in a future release. |
| This endpoint has been updated in this release to accept only string values for all fields. |
The following is an Autonomous Identity single view with applications endpoint:
POST employees
- POST employees
-
Endpoint
/api/singleViewWithApp/employees
Authorization
<Bearer Token JWT-value>
Body
{ "employeeId": "elizabeth.saiz", "includeLastAccessed": "true", "pageSize": "5" }Example Request
curl --location --request POST '/api/singleViewWithApp/employees' \ --header 'Content-Type: application/json' \ --data-raw '{ "employeeId": "elizabeth.saiz", "includeLastAccessed": "true", "pageSize": "5" }'Example Response
{ "high": 0, "medium": 1, "low": 1, "avg_score": 0.25, "app_name": "", "app_id": "", "entitlement_name": "", "high_risk": null, "userEntt": [ { "user": "elizabeth.saiz", "entitlement": "192aed21-a7d1-40c3-87a3-9dfa4a3d21f5", "app_id": "null", "app_name": "test3", "entitlement_name": "null", "freq": null, "frequnion": null, "high_risk": "null", "justification": [], "score": 0.1, "user_name": "alpha" }, { "user": "elizabeth.saiz", "entitlement": "36bad416-d42c-47c2-991e-623aa3833028", "app_id": "null", "app_name": "test6", "entitlement_name": "null", "freq": null, "frequnion": null, "high_risk": "null", "justification": [], "score": 0.4, "user_name": "vce" } ], "user": "elizabeth.saiz", "entitlementsCount": 14, "entitlementsRemainingCount": 10, "lastEntitlementId": "36bad416-d42c-47c2-991e-623aa3833028" }
Access Control
The following are Autonomous Identity access control endpoints:
GET /api/userDetails/decisions
- GET /api/userDetails/decisions
-
Get the current entitlement decisions for the user. [Supervisor, Ent Owner, App Owner, Admin]
Endpoint
/api/userDetails/decisions
Authorization
<Bearer Token JWT-value> OR <API-KEY>
Param
user=john.doe
Query Parameters Parameter Type Description user
string
User ID (required)
filter
object
Filter to add (single property shown below)
Filter Query Object Properties Parameter Type Description datasinkStatus
string
Datasink status filter ('ack' or 'nack')
timestampThresholds
Timestamp threshold object
timestampThresholds Object Properties Parameter Type Description gt
string
Greater than timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with gte.
gte
string
Greater than or equal timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with gt.
lt
string
Less than timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with lte.
lte
string
Less than or equal timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with le.
Example Request (DatasinkStatus Filter)
curl -k -X GET \ 'datasinkStatus=nack' \ -H 'Authorization: Bearer <token value>' \ <or> -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json'
Example Response (DatasinkStatus Filter)
{ "decisions": [ { "user": "john.doe", "entitlement": "ent_1", "is_certified": false, "is_revoked": false, "is_processed": false, "is_archived": false, "author": "jane.smith", "author_name": "Jane Smith", "author_type": "Zoran Admin", "reason": null, "last_updated": "2022-01-11T19:48:17.195Z", "datasink_status": "nack", "usr_name": "John Doe", "ent_name": "Entitlement 1", "app_id": "Gateway", "app_name": "Gateway", "usr_manager_id": "john.smith", "conf": 0.75, "freq": 4, "freqUnion": 3 } ] }
POST /api/userDetails/decisions
- POST /api/userDetails/decisions
-
Update entitlement decisions for users. [Supervisor, Ent Owner, App Owner, Admin]
Endpoint
/api/userDetails/decisions
Authorization
<Bearer Token JWT-value> OR <API-KEY>
Request Body Parameters Parameter Type Description assignments
array of assignment objects
List of assignments affected by the decision (available properties listed below)(required)
is_certified
boolean
Certification decision
is_revoked
boolean
Revoke decision
is_requested
boolean
Decision is processed
reason
string
Reason for decision
datasink_status
string
Datasink status ('ack' or 'nack')
Assignments Object Properties Parameter Type Description user
string
User ID (required)
entitlements
string array
List of entitlement ID’s (required)
Body
{ "assignments": [ { "user": "string", "entitlements": [ "string" ] } ], "is_certified": true, "is_revoked": true, "is_requested": true, "is_processed": true, "reason": "string", "datasink_status": "nack" }Example Request
curl --request POST "https://autoid-api.forgerock.com/api/userDetails/decisions" \ -H "accept: /" -H "Content-Type: application/json" \ --data-raw '{ "assignments": [ { "user": "string", "entitlements": [ "string" ] } ], "is_certified": true, "is_revoked": true, "is_requested": true, "is_processed": true, "reason": "string", "datasink_status": "nack" }'Example Response
{ "status": 200 }
POST /api/rules/decision
- POST /api/rules/decision
-
Update rule decisions. [Supervisor, Ent Owner, App Owner, Admin]
Endpoint
/api/rules/decision
Authorization
<Bearer Token JWT-value>
Request Body Parameters Parameter Type Description rules
array of rules objects
List of rules affected by the decision (available properties listed below)(required)
is_autocertify
boolean
Auto-Certification decision (required)
is_autorequest
boolean
Auto-Request decision (required)
autocertify_reason
boolean
Auto-Certification reason (required)
autorequest_reason
boolean
Auto-Request reason (required)
datasink_status
string
Datasink status ('ack' or 'nack')
Rule Object Properties Parameter Type Description entitlement
string
Entitlement ID (required)
justification
string array
List of raw justifications (required)
Body
{ "rules": [ { "entitlement": "string", "justification": [ "string" ] } ], "is_autocertify": true, "is_autorequest": true, "autocertify_reason": "string", "autorequest_reason": "string" }Example Request
curl -k -X POST \ "https://autoid-api.forgerock.com/api/rules/decision" \ -H 'Authorization: Bearer <token-value>' \ -H "accept: /" -H "Content-Type: application/json" \ --data-raw '{ "rules": [ { "entitlement": "Ent_1", "justification": [ "0C_CHIEF_YES_NO_Yes", "0C_JOBCODE_NAME_Service Representitive II", "0C_MANAGER_NAME_John_Doe", "0C_USR_EMP_TYPE_Non-Employee" ] } ], "is_autocertify": true, "is_autorequest": false, "autocertify_reason": "Goodbye, world.", "autorequest_reason": "Hello, world." }'Example Response
Status 204: No Content
Applications
The following are Autonomous Identity applications view endpoints:
GET /api/applications
- GET /api/applications
-
Get a list of applications and stats for an Application Owner. [App Owner, Admin]
Endpoint
/api/applications
Authorization
<Bearer Token JWT-value>
Params
ownerId (optional) derick.hui cursor (optional) string (Indicator on where to start a 2+ page list)
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/applications?ownerId=derick.hui" \ --header "Content-Type: application/json"
Example Response
{ "cursor": "string", "total_applications": 0, "total_entitlements": 0, "total_assignments": 0, "applications": [ { "app_id": "string", "app_name": "string", "high": 0, "medium": 0, "low": 0, "avg": 0 } ] }
POST /api/applications/{appId}
- POST /api/applications/{appId}
-
Get a list of entitlements and stats for a selected application. [App Owner, Admin]
Endpoint
/api/applications/{appId}Authorization
<Bearer Token JWT-value>
Params
appId (required) app_1 cursor (optional) string (Indicator on where to start a 2+ page list)
Body
{ "filters": [ { "type": "user", "attribute": "city", "value": ["Seattle", "Denver"] }, { "type": "user", "attribute": "line_of_business", "value": ["Distribution Operations"] } ] }Example Request
curl --request POST "https://autoid-api.forgerock.com/api/applications/app_1" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" \ --data-raw '{ "filters": [ { "type": "user", "attribute": "city", "value": ["Seattle", "Denver"] }, { "type": "user", "attribute": "line_of_business", "value": ["Distribution Operations"] } ] }'Example Response
{ "cursor": "string", "total_entitlements": 0, "total_users": 0, "total_rules": 0, "entitlements": [ { "ent": "string", "ent_name": "string", "high": 0, "medium": 0, "low": 0, "avg": 0 } ] }
POST /api/applications/{appId}/assignments
- POST /api/applications/{appId}/assignments
-
Get filterable user-entitlement assignment and decision data for a specific application. [App Owner, Admin]
Endpoint
api/applications/{appId}/assignmentsAuthorization
<Bearer Token JWT-value>
Params
appId (required) app_1 user string cursor (optional) string (Indicator on where to start a 2+ page list) sortBy string sortDir string
Body
{ "filters": [ { "type": "user", "attribute": "city", "value": [ "Seattle", "Denver" ] }, { "type": "user", "attribute": "line_of_business", "value": [ "Distribution Operations" ] } ] }Example Request
curl --request POST "https://autoid-api.forgerock.com/api/applications/app_1/assignments" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" \ --data-raw '{ "filters": [ { "type": "user", "attribute": "city", "value": [ "Seattle", "Denver" ] }, { "type": "user", "attribute": "line_of_business", "value": [ "Distribution Operations" ] } ] }'Example Response
{ "cursor": "string", "total_users": 0, "total_entitlements": 0, "total_assignments": 0, "assignments": [ { "ent": "string", "ent_name": "string", "confidence": 0, "user_id": "string", "user_name": "string", "isCertified": true, "dateCertified": "2021-04-14T19:10:39.178Z", "isRevoked": true, "dateRevoked": "2021-04-14T19:10:39.178Z", "isRequested": true, "dateRequested": "2021-04-14T19:10:39.178Z", "isProcessed": true, "approvalAuthor": { "id": "string", "name": "string" } } ] }
GET /api/applications/search
- GET /api/applications/search
-
Search all applications. [App Owner, Admin]
Endpoint
/api/applications/search
Authorization
<Bearer Token JWT-value>
Params
by appOwner or enttOwner user user ID q Search query string
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/applications/search" \ --header "Content-Type: application/json"
Example Response
{ "values": [ { "app_id": "string", "app_name": "string" } ] }
Entitlements
The following are Autonomous Identity filtering by entitlements endpoints:
GET /api/entitlements/search
- GET /api/entitlements/search
-
Search for entitlements by name and with applied filters. [Ent Owner, App Owner, Admin]
Endpoint
/api/entitlements/search?q=QueryString
Authorization
<Bearer Token JWT-value>
Params
by appOwner or enttOwner user user ID q Search query string (required) appId Application ID to use as a filter
Example Request
curl --location --request GET 'https://autoid-api.forgerock.com/api/entitlements/search?by=enttOwner&user=john.doe&q=WEB&appId=Salesforce' \ --header 'Content-Type: application/json'
Example Response
{ "values": [ { "id": "string", "app_id": "string", "app_name": "string", "entt_name": "string" } ] }
POST /api/entitlements/stats
- POST /api/entitlements/stats
-
Get data for entitlements view. [Supervisor, Ent Owner, Admin]
Endpoint
/api/entitlements/stats?by=supervisor/entitlementOwner/admin
Authorization
<Bearer Token JWT-value>
Params
by supervisor, roleOwner
Body
{ "ownerId": "timothy.slack", "isHighRiskOnly": true, "isMediumLowRiskOnly": false, "isUserEntitlementsIncluded": true, "filters": [{ "type": "app_id", "group": "criticality", "value": "Essential" }] }Example Request
curl --location --request POST 'https://autoid-api.forgerock.com/api/entitlements/stats?by=supervisor' \ --header 'content-type: application/json' \ --data-raw '{ "ownerId": "timothy.slack", "isHighRiskOnly": true, "isMediumLowRiskOnly": false, "isUserEntitlementsIncluded": true, "filters": [{ "type": "app_id", "group": "criticality", "value": "Essential" }] }'Example Response
{ "total_entitlements": 0, "total_subordinates": 0, "unscoredEntitlements": 0, "scoredEntitlements": 0, "usersWithNoEntitlement": 0, "usersWithNoScoredEntitlement": 0, "distinct_apps": [ { "app_id": "string", "app_name": "string", "low": 0, "medium": 0, "high": 0 } ], "users": [ { "user": "string", "user_name": "string", "high": 0, "medium": 0, "low": 0, "avg": "string" } ], "entitlements": [ { "entitlement": "string", "entitlement_name": "string", "app_id": "string", "high_risk": "string", "high": 0, "medium": 0, "low": 0, "avg": "string" } ] }
GET /api/entitlements/id/{id}
- GET /api/entitlements/id/{id}
-
Get entitlement details. [User, Supervisor, Ent Owner, App Owner, Admin]
Endpoint
/api/entitlements/id/{id+}Authorization
<Bearer Token JWT-value>
Params
by entitlement ID
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/entitlements/id/1234" \ --header "Content-Type: application/json"
Example Response
{ "entitlement_name": "string", "scores": { "avg": 0, "high": 0, "medium": 0, "low": 0 }, "drivingFactors": [ { "attribute": { "id": "string", "title": "string", "value": "string" }, "count": 0 } ], "userScores": [ { "score": 0, "count": 0 } ], "users": [ { "user": "string", "user_name": "string", "app_id": "string", "freq": 0, "frequnion": 0, "justification": [ { "title": "string", "value": "string" } ], "rawJustification": [ "string" ], "score": 0 } ] }
GET /api/entitlements/unscored
- GET /api/entitlements/unscored
-
Get unscored entitlements and users for a given Supervisor or Entitlement Owner ID. [Supervisor, Ent Owner, Admin]
Endpoint
/api/entitlements/unscored
Authorization
<Bearer Token JWT-value>
Params
by supervisor, entitlement owner user supervisor or entitlement owner user ID
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/entitlements/unscored?by=supervisor&user=1234" \ --header "Content-Type: application/json"
GET /api/entitlements/distinct
- GET /api/entitlements/distinct
-
Get a list of all entitlements.
Endpoint
/api/entitlements/distinct
Authorization
<Bearer Token JWT-value>
Example Request
curl --location --request GET 'https://autoid-api.forgerock.com/api/entitlements/distinct' \ --header 'Content-Type: application/json' \ --header 'Authorization: Bearer <token>'
Example Response
[ { "ent_id": "AccessType : XMLP_ADMIN", "ent_name": "AccessType : XMLP_ADMIN", "ent_owner_id": "julie.yee", "app_id": "Salesforce", "ent_criticality": "Non-Essential", "ent_risk_level": "Medium" } ]
GET /api/entitlements/recommendations
- GET /api/entitlements/recommendations
-
Get a list of entitlement recommendations for a given set of user attributes.
Endpoint
/api/entitlements/recommendations
Authorization
<Bearer Token JWT-value>
Body
{ "confidenceThreshold": 0.1, "maxResults": 1000, "offset": 200, "userAttributes": [ "0E_USR_MANAGER_ID_gregory.suhr", "13_USR_DEPARTMENT_NAME_Facilities Area A", "0C_CHIEF_YES_NO_No", "0C_MANAGER_NAME_Gregory Suhr", "0C_USR_EMP_TYPE_Employee", "13_USR_DEPARTMENT_NAME_Wireless Operations" ] }Example Request
curl --request GET "https://autoid-api.forgerock.com/api/entitlements/recommendations" \ --header "Content-Type: application/json" \ --header "Authorization: Bearer <token>" \ --data-raw '{ "confidenceThreshold": 0.1, "maxResults": 1000, "offset": 200, "userAttributes": [ "0E_USR_MANAGER_ID_gregory.suhr", "13_USR_DEPARTMENT_NAME_Facilities Area A", "0C_CHIEF_YES_NO_No", "0C_MANAGER_NAME_Gregory Suhr", "0C_USR_EMP_TYPE_Employee", "13_USR_DEPARTMENT_NAME_Wireless Operations" ] }'Example Response
[ { "attributes": [ "0C_CHIEF_YES_NO_No", "0E_USR_MANAGER_ID_gregory.suhr" ], "entitlement": "06_ENT_ID_WEB_user_WEB RCQ Flare NonIT Distribution_II", "confidence": 0.14, "frequency": 22 }, { "attributes": [ "0C_MANAGER_NAME_Gregory Suhr", "13_USR_DEPARTMENT_NAME_Facilities Area A" ], "entitlement": "06_ENT_ID_Web_tildeNon-security plus", "confidence": 0.14, "frequency": 28 }, ]
Assignments
The following endpoint has been added to support the extraction of assignments. New APIs introduced in this release are marked with .
POST /api/assignments
- POST /api/assignments
-
Get a list of all assignments or filtered assignments when the following optional filtering is sent as a JSON request body.
The endpoint requires a valid API key passed in a
X-API-KEYheader for authorization (refer to Generate an API key) or an authorized admin-level bearer token.Endpoint
+
/api/assignments
Headers
+
Content-Type application/json
Body Parameters
Parameter Type Description cursor
string
Cursor to send for the next page of assignments (the response returns null if there are no more pages)
pageSize
integer
Number of assignments to return per page
ent_id
string
Entitlement ID to filter by
usr_id
string
User ID to filter by
app_id
string
Application ID to filter by
Example Request
+
curl -k -X POST \ https://autoid-ui.forgerock.com/api/assignments \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d '{ "pageSize": 20, "cursor": "WyJhYXJvbi5maXNjaGVyIiwiV0VCX3VzZXJfU2hhcmVkX0VkaXRfQURNSU5fSUkiXQ==" }'
Example Response
+
{ "cursor": "WyJhYXJvbi5mb2x0eiIsIldlYl9TZXJ2aWNlQW5hbHl0aWNzIDogS1BJIEFnZW50IGFuZCBQb3dlciBBY2Nlc3NfSUkiXQ==", "assignments": [ { "ent_id": "WEB_user_Web_Local Access 32 All_II_Europe", "usr_id": "aaron.fischer", "score": null, "justification": [] }, { "ent_id": "WEB_user_Web_Shared_Edit_ADMIN_Europe", "usr_id": "aaron.fischer", "score": null, "justification": [] }, { "ent_id": "WEB_user_Web_WEB RCQ Flare NonIT Distribution_Europe", "usr_id": "aaron.fischer", "score": 0.98, "justification": [ { "id": "CHIEF_YES_NO", "title": "chief_yes_no", "value": "Yes" }, { "id": "USR_DEPARTMENT_NAME", "title": "USR_DEPARTMENT_NAME", "value": "Information Systems 1" } ] }, { "ent_id": "Web_Flare NonIT Distribution", "usr_id": "aaron.fischer", "score": 0.6, "justification": [ { "id": "CITY", "title": "city", "value": "Jacksonville" }, { "id": "USR_EMP_TYPE", "title": "usr_emp_type", "value": "Employee" }, { "id": "LINE_OF_BUSINESS", "title": "line_of_business", "value": "Strategy and Policy" } ] } ] }
Rules
The following are Autonomous Identity rules endpoints:
GET /api/rules/info
- GET /api/rules/info
-
List information and statistics regarding available rules. [Ent Owner, App Owner, Admin]
Endpoint
/api/rules/info
Authorization
<Bearer Token JWT-value>
Params
by enttowner, appOwner user patrick.murphy
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/rules/info?by=appOwner&user=patrick.murphy" \ --header "Content-Type: application/json"
Example Response
{ "countRules": 0, "countAssignments": 0, "countApplications": 0, "applications": [ { "app_id": "string", "app_name": "string", "countAssignments": 0, "low": 0, "medium": 0, "high": 0 } ] }
GET /api/rules
- GET /api/rules
-
List the available rules for a user [Ent Owner, App Owner, Admin]. You can filter by time period by using greater than and/or less than date-times.
Endpoint
/api/rules/
Authorization
<Bearer Token JWT-value> OR <API-KEY>
Query Parameters Parameter Type Description by
string
User type to apply when searching rules:
enttOwner,appOwneruser
string
User ID when applying by filters (required if using "by")
cursor
string
Position to start a 2+ page list.
pageSize
number
Number of records per page to retrieve.
filter
filter object
Additional filters to apply (refer to properties below).
Filter Query Object Properties Parameter Type Description lowConfidence
boolean
Low confidence scores only.
medConfidence
boolean
Medium confidence scores only.
highConfidence
boolean
High confidence scores only.
app_id
string array
Array of application IDs.
autoCertify
boolean
Auto-certified only.
autoRequest
boolean
Auto-requested only.
entitlement
string
Entitlement ID
datasinkStatus
string
Datasink status filter ('ack' or 'nack')
timestampThresholds
object
Timestamp threshold object (available properties below)
timestampThresholds Object Properties Parameter Type Description gt
string
Greater than timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with gte.
gte
string
Greater than or equal timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with gt.
lt
string
Less than timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with lte.
lte
string
Less than or equal timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with le.
Example Request (Datasink status filter)
curl -k -X GET \ 'datasinkStatus=ack' \ -H 'Authorization: Bearer <token value>' <OR> -H 'X-API-KEY: <api-key-value>' \ -H 'Content-Type: application/json'
Example Response (Datasink status filter)
{ "cursor": null, "totalRulesCount": 1, "rules": [ { "entitlement": { "ent_id": "Cognos EDI Reporting", "ent_owner_id": "david.elliott", "ent_criticality": "Essential", "ent_risk_level": "High", "ent_name": "Cognos EDI Reporting", "app_id": "SAP" }, "app": { "app_criticality": "Essential", "app_name": "SAP", "app_owner_id": "derick.hui", "app_risk_level": "High", "app_id": "SAP" }, "justification": [ { "id": "CHIEF_YES_NO", "title": "Chief?", "value": "No" }, { "id": "MANAGER_NAME", "title": "Manager_Name", "value": "Patrick Gardner" }, { "id": "USR_EMP_TYPE", "title": "Employee Type", "value": "Employee" }, { "id": "USR_DEPARTMENT_NAME", "title": "User department Name", "value": "General Office" } ], "rawJustification": [ "0C_CHIEF_YES_NO_No", "0C_MANAGER_NAME_Patrick Gardner", "0C_USR_EMP_TYPE_Employee", "13_USR_DEPARTMENT_NAME_General Office" ], "assignees": [ { "id": "gordon.choy", "name": "Gordon Choy" }, { "id": "jennifer.kanenaga", "name": "Jennifer Kanenaga" }, { "id": "lawrence.nicholls", "name": "Lawrence Nicholls" }, { "id": "roel.dilag", "name": "Roel Dilag" }, { "id": "salvatore.taormina", "name": "Salvatore Taormina" } ], "confidence": 1, "countUnassigned": 0, "countAssigned": 5, "isAutoCertify": true, "autoCertifyDate": "2021-10-01T19:01:31.567Z", "isAutoRequest": true, "autoRequestDate": "2021-10-01T19:01:31.567Z", "approvalAuthor": { "id": "bob.rodgers", "name": "Bob Rodgers" }, "requestApprovalReason": "Test", "certifyApprovalReason": "Test", "datasink_status": "ack" } ] }
POST /api/rules/decision
- POST /api/rules/decision
-
Update rule decisions. [Supervisor, Ent Owner, App Owner, Admin]
Endpoint
/api/rules/decision
Authorization
<Bearer Token JWT-value>
Request Body Parameters Parameter Type Description rules
array of rules objects
List of rules affected by the decision (available properties listed below)(required)
is_autocertify
boolean
Auto-Certification decision (required)
is_autorequest
boolean
Auto-Request decision (required)
autocertify_reason
boolean
Auto-Certification reason (required)
autorequest_reason
boolean
Auto-Request reason (required)
datasink_status
string
Datasink status ('ack' or 'nack')
Rule Object Properties Parameter Type Description entitlement
string
Entitlement ID (required)
justification
string array
List of raw justifications (required)
Body
{ "rules": [ { "entitlement": "string", "justification": [ "string" ] } ], "is_autocertify": true, "is_autorequest": true, "autocertify_reason": "string", "autorequest_reason": "string" }Example Request
curl -k -X POST \ 'https://autoid-ui.forgerock.com/api/rules/decisions' \ -H 'Authorization: Bearer <token value>' \ -H 'Content-Type: application/json' \ -d '{ "rules": [ { "entitlement": "Ent_1", "justification": [ "0C_CHIEF_YES_NO_Yes", "0C_JOBCODE_NAME_Service Representitive II", "0C_MANAGER_NAME_John_Doe", "0C_USR_EMP_TYPE_Non-Employee" ] } ], "is_autocertify": true, "is_autorequest": false, "autocertify_reason": "Goodbye, world.", "autorequest_reason": "Hello, world." }'Example Response
Status 204: No Content
Filters
The following are Autonomous Identity Filters endpoints:
GET /api/filters/owner
- GET /api/filters/owner
-
Get filterable attributes and values. [Supervisor, Ent Owner, Admin]
Endpoint
/api/filters/owner?by=supervisor&user=albert.pardini
Authorization
<Bearer Token JWT-value>
Query Parameters
by supervisor, enttOwner user albert.pardini
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/filters/owner?by=supervisor&user=albert.pardini" \ --header "Content-Type: application/json"
Example Response
{ "items": [ { "title": "string", "field": "string", "filters": { "field": "string", "title": "string", "options": [ { "text": "string", "value": "string", "count": 0 } ] } } ] }
GET /api/filters/app
- GET /api/filters/app
-
Get filterable attributes and values. [App Owner, Admin]
Endpoint
/api/filters/app
Authorization
<Bearer Token JWT-value>
Query Parameters
id: application ID
Example Request
curl --request GET "https://autoid-api.forgerock.com/api/filters/app?id=app_1" \ --header "Content-Type: application/json"
Example Response
{ "items": [ { "title": "string", "field": "string", "filters": { "field": "string", "title": "string", "options": [ { "text": "string", "value": "string", "count": 0 } ] } } ] }
Roles
The following are Autonomous Identity filtering by roles endpoints:
POST /api/roles
- POST /api/roles
-
Create draft roles and make updates to roles.
Endpoint
/api/roles
Authorization
<Bearer Token JWT-value> OR <API-KEY>
Request Body Parameters Parameter Type Description action
string
Action to perform ('create', 'save', 'publish', 'unpublish') (required)
updateAllMetadata
boolean
Update metadata for all related roles regardless of statuus
role
role object
Role object (properties below) (required)
Role Object Properties Parameter Type Description role_id
string
Role ID in uuid format (required)
status
string
Status of role ('draft', 'candidate', or 'active') (required)
custom_role
boolean
Role is a custom role
member_count
number
Number of users the roles applies to
assignment_count
number
Number of assignments the role applies to
entitlements
string array
List of entitlement IDs that are part of the role
justifications
string array
List of raw justifications
datasink_status
string
Datasink status ('ack' or 'nack')
role_metadata
role metadata object
Role metadata (properties below)
entitlements_metadata
array of entitlement metadata objects
List of entitlement metadata for each entitlement (object properties below)
Role Metadata Object Properties Parameter Type Description role_name
string
Display name of role
description
string
Role description
role_owner_id
string
Role owner ID
role_owner_display_name
string
Role owner display name
Entitlement Metadata Object Properties Parameter Type Description ent_id
string
Entitlement ID (required)
ent_name
string
Entitlement name (required)
application
application object
Application metadata (object properties below)
entitlement_owner
owner object
Entitlement owner data (object properties below)
Application Object Properties Parameter Type Description app_id
string
Application ID
app_name
string
Application name
application_owner
owner object
Application owner data (object properties below)
Owner Object Properties Parameter Type Description usr_id
string
User ID (required)
usr_name
string
User name (required)
usr_manager_id
string
User manager ID (required)
Example Request
curl --location --request POST 'https://autoid-api.forgerock.com/api/roles' \ --header 'Content-Type: application/json' \ --header 'Authorization: Bearer <token>' \ --data-raw '{ "action": "save", "updateAllMetadata": false, "role": { "role_id": "3fa85f64-5717-4562-b3fc-2c963f66afa6", "status": "draft", "custom_role": false, "member_count": 0, "assignment_count": 0, "entitlements": [ "string" ], "entitlements_metadata": [ { "ent_id": "string", "ent_name": "string", "application": { "app_id": "string", "app_name": "string", "application_owner": { "usr_id": "string", "usr_name": "string", "usr_manager_id": "string" } }, "entitlement_owner": { "usr_id": "string", "usr_name": "string", "usr_manager_id": "string" } } ], "justifications": [ "string" ], "role_metadata": { "role_name": "string", "description": "string", "role_owner_display_name": "string", "role_owner_id": "string" } } }'Example Response
204 (No Content)
POST /api/roles/delete
- POST /api/roles/delete
-
Delete roles.
Endpoint
/api/roles/delete
Authorization
<Bearer Token JWT-value>
Body
{ "role_id": "3fa85f64-5717-4562-b3fc-2c963f66afa6", "status": "draft" | “active” }Example Request
curl --location --request POST 'https://autoid-api.forgerock.com/api/admin/updateSelf' \ --header 'Content-Type: application/json' \ --header 'Authorization: Bearer <token>' \ --data-raw '{ "role_id": "3fa85f64-5717-4562-b3fc-2c963f66afa6", "status": "draft" | “active” }'Example Response
204 (No content)
POST /api/roles/export
- POST /api/roles/export
-
Export role data to json.
Endpoint
/api/roles/export
Authorization
<Bearer Token JWT-value> OR <API-KEY>
Query Parameters Parameter Type Description usrId
string
Roles that apply for a particular user ID
entId
string
Roles that apply for a particular entitlement ID
status
string
Status of role ('draft', 'candidate', or 'active')
role_name
string
Role name
description
string
Role description
role_owner_id
string
Role owner ID
role_owner_display_name
string
Role owner name
datasinkStatus
string
Datasink status filter ('ack', 'nack')
timestampThresholds
object
Timestamp threshold object (available properties below)
timestampThresholds Object Properties Parameter Type Description gt
string
Greater than timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with gte.
gte
string
Greater than or equal timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with gt.
lt
string
Less than timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with lte.
lte
string
Less than or equal timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with le.
Body
{ "usrId": "john.doe", "datasinkStatus": "nack" }Example Request (Datasink Filter)
curl -k -X POST \ 'https://autoid-ui.forgerock.com/api/roles/export' \ --header 'Content-type: application/json' \ --header 'Authorization: Bearer <token>' <OR> -H 'X-API-KEY: <api-key-value>' \ --data-raw '{ "usrId": "john.doe", "datasinkStatus": "nack" }'Example Response (Datasink Filter)
{ "roles": [ { "temp_role_name": "Role J0-R21", "normalized_role_name": "role j0-r21", "member_count": 1, "assignment_count": 1, "entitlement_count": 1, "role_id": "4aaf81db-2f8c-42b4-b954-1018a71743de", "status": "candidate", "entitlements": [ "Ent_1" ], "entitlements_metadata": [ { "ent_criticality": "Essential", "ent_id": " Ent_1", "ent_name": " Ent_1", "ent_risk_level": "Low", "application": { "app_criticality": "Essential", "app_id": "Active Directory", "app_name": "Active Directory", "app_risk_level": "High", "application_owner": { "chief_yes_no": "Yes", "city": "Kansas City", "cost_center": "CON_SD9", "department": "Facilities Area A", "is_active": "Y", "job_description": "Facilities Area A", "jobcode_name": "Operating Clerk", "line_of_business": "Transmission Operations", "line_of_business_subgroup": "Real Estate", "manager_name": "Thomas Shawyer", "usr_department_name": "Facilities Area A", "usr_display_name": "Derick Hui", "usr_emp_type": "Non-Employee", "usr_id": "derick.hui", "usr_manager_id": "thomas.shawyer", "usr_name": "Derick Hui" } }, "entitlement_owner": { "chief_yes_no": "No", "city": "Saint Paul", "cost_center": "OP_TT4", "department": "InfoSYS Power Gen", "is_active": "Y", "job_description": "InfoSYS Power Gen", "jobcode_name": "Lineman", "line_of_business": "Ethics and Compliance", "line_of_business_subgroup": "System Operations", "manager_name": "James Bosch", "usr_department_name": "InfoSYS Power Gen", "usr_display_name": "Carolyn Latanafrancia", "usr_emp_type": "Non-Employee", "usr_id": "carolyn.latanafrancia", "usr_manager_id": "james.bosch", "usr_name": "Carolyn Latanafrancia" } } ], "justifications": [ "0B_COST_CENTER_SOL_ER2 19_LINE_OF_BUSINESS_SUBGROUP_Energy%20Solutions" ], "users": [ { "usr_id": "aaron.lozada", "usr_display_name": "Aaron Lozada", "attributes": [ "13_USR_DEPARTMENT_NAME_Operations%20SUP", "0F_JOB_DESCRIPTION_Operations_%20SUP", "0C_JOBCODE_NAME_Apprentice", "0C_MANAGER_NAME_Gary%20Amelio", "09_IS_ACTIVE_Y", "10_LINE_OF_BUSINESS_Distribution%20Operations", "10_USR_DISPLAY_NAME_Aaron%20Lozada", "0B_COST_CENTER_SOL_ER2", "08_USR_NAME_Aaron%20Lozada", "0C_CHIEF_YES_NO_No", "0C_USR_EMP_TYPE_Employee", "19_LINE_OF_BUSINESS_SUBGROUP_Energy%20Solutions", "04_CITY_Kansas%20City" ] } ] } ] }
Ingest
The following endpoints support the ingestion of base entities, such as applications, entitlements, identities, assignments, data sources, and mappings. New APIs introduced in this release are marked with .
To access these endpoints, you need a valid API key in the X-API-KEY header for authorization. To obtain an API key, see Generate an API key.
POST /api/ingest/applications
- POST /api/ingest/applications
-
Create, update, upsert, or delete application entities.
Endpoint
/api/ingest/applications
Authorization
<API Key-value>
Body Parameters Parameter Type Description action
string
Action to perform: create, update, upsert, delete (required)
apps
array
Array of application objects (properties below) (required)
Base Application Object Properties: Parameter Type Description app_id
string
Application ID (required)
app_name
string
Application Name
app_owner_id
string
Application owner user ID
Example Request
curl -k -X POST \ https://autoid-ui.forgerock.com/api/ingest/applications \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d '{ "action": "create", "apps": [ { "app_id": "app1", "app_name": "Test App", "app_owner_id": "bob.rodgers" } ] }'
Example Response
{ "message": "ok" }
POST /api/ingest/entitlements
- POST /api/ingest/entitlements
-
Create, update, upsert, or delete entitlement entities.
Endpoint
/api/ingest/entitlements
Authorization
<API Key-value>
Body
Body Parameters Parameter Type Description action
string
Action to perform: create, update, upsert, delete (required)
entitlements
array
Array of entitlements objects (properties below) (required)
Base Entitlements Object Properties Parameter Type Description ent_id
string
Entitlement ID (required)
ent_name
string
Entitlement Name
ent_owner_id
string
Entitlement owner user ID
app_id
string
Application ID
Example Request
curl -k -X POST \ https://autoid-ui.forgerock.com/api/ingest/entitlements \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d '{ "action": "upsert", "entitlements": [ { "ent_id": "ent1", "ent_name": "Test Ent", "ent_owner_id": "bob.rodgers", "app_id": "app1" } ] }'
Example Response
{ "message": "ok" }
POST /api/ingest/identities
- POST /api/ingest/identities
-
Create, update, upsert, or delete identity entities.
Endpoint
/api/ingest/identities
Authorization
<API Key-value>
Body Parameters Parameter Type Description action
string
Action to perform: create, update, upsert, delete (required)
entitlements
array
Array of identities objects (properties below) (required)
Base Entitlements Object Properties Parameter Type Description usr_id
string
User ID (required)
usr_name
string
User name
usr_manager_id
string
User’s manager ID
Example Request
curl -k -X POST \ https://autoid-ui.forgerock.com/api/ingest/identities \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d '{ "action": "upsert", "identities": [ { "usr_id": "john.doe", "usr_name": "John Doe", "usr_manager_id": "bob.rodgers" }, { "usr_id": "jane.smith", "usr_name": "Jane Smith", "usr_manager_id": "bob.rodgers" } ] }'
Example Response
{ "message": "ok" }
POST /api/ingest/assignments
- POST /api/ingest/assignments
-
Create, update, upsert, or delete assignment entities.
Endpoint
/api/ingest/assignments
Authorization
<API Key-value>
Body Parameters Parameter Type Description action
string
Action to perform: create, update, upsert, delete (required)
entitlements
array
Array of assignment objects (properties below) (required)
Base Entitlements Object Properties Parameter Type Description ent_id
string
Entitlementd ID (required)
usr_id
string
User ID (required)
Example Request
curl -k -X POST \ https://autoid-ui.forgerock.com/api/ingest/assignments \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d '{ "action": "upsert", "assignments": [ { "usr_id": "john.doe", "ent_id": "ent1" }, { "usr_id": "jane.smith", "ent_id": "ent1" } ] }'
Example Response
{ "message": "ok" }
POST /api/ingest/datasources
- POST /api/ingest/datasources
-
Get data sources. Optional filtering can be applied as a JSON request body outlined below:
Endpoint
/api/ingest/datasources
Authorization
<API Key-value>
Body Parameters Parameter Type Description datasourceId
string
Data source ID
name
string
Data source name
isActive
boolean
Data source activated
connectionTypes
string array
List of connection types to filter: jdbc, csv, generic
entityTypes
string array
List of entity types
Example Request
curl -k -X GET \ https://autoid-ui.forgerock.com/api/ingest/datasources \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d '{ "connectionTypes": ["csv"], "isActive": true }'
Example Response
[ { "datasource_id": "fdbfb998-7b3e-4ddc-9e4a-a4c46cace49e", "name": "Test data", "sync_type": "full", "icon": "apps", "isActive": true, "entityTypes": { "/autoid/system/datasources/fdbfb998-7b3e-4ddc-9e4a-a4c46cace49e/applications": { "uri": { "file": "file:/data/input/applications.csv" } }, "/autoid/system/datasources/fdbfb998-7b3e-4ddc-9e4a-a4c46cace49e/assignments": { "uri": { "file": "file:/data/input/assignments.csv" } }, "/autoid/system/datasources/fdbfb998-7b3e-4ddc-9e4a-a4c46cace49e/entitlements": { "uri": { "file": "file:/data/input/entitlements.csv" } }, "/autoid/system/datasources/fdbfb998-7b3e-4ddc-9e4a-a4c46cace49e/identities": { "uri": { "file": "file:/data/input/identities.csv" } } }, "connectionSettings": { "csv": {} } } ]
POST /api/ingest/mappings
- POST /api/ingest/mappings
-
Get mappings. Optional filtering can be applied as a JSON request body outlined below:
Endpoint
/api/ingest/mappings
Authorization
<API Key-value>
Body Parameters Parameter Type Description mappingId
string
Mapping ID
sourceEntity
string
Mapping source entity
targetEntity
string
Mapping target entity
sourceProperties
string array
List of source properties to filter on
targetProperties
string array
List of target properties to filter on
Example Request
curl -k -X GET \ https://autoid-ui.forgerock.com/api/ingest/mappings \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d '{ "targetProperties": ["app_id", "app_name"] }'
Example Response
[ { "mapping_id": "fb6896e5-8d0a-4bd7-b10d-5608c9a953a1", "source_entity": "/autoid/system/datasources/0474f92c-d530-43cc-a012-29fb6c8b3b8b/applications", "target_entity": "/autoid/base/applications", "properties": [ { "source": "APP_ID", "target": "app_id", "apply": true }, { "source": "APP_NAME", "target": "app_name", "apply": true }, { "source": "APP_OWNER_ID", "target": "app_owner_id", "apply": true } ] } ]
Jobs
You can define, run, and get the status of each job using REST API endpoints. When using REST calls, the available job types are the following:
-
ingest
-
train
-
mine
-
predict-as-is
-
recommend
-
load
-
create-assignment-index
-
create-assignment-index-report
-
anomaly
-
insight
-
audit
The following are Autonomous Identity jobs endpoints:
POST /api/job_definition
- POST /api/job_definition
-
Set up a job definition.
Endpoint
/api/job_definition
Authorization
Bearer <Token JWT-value> or <API Key-value>
Body
{ "branch": "actual", "contextId": "40c20f01-a9d8-4284-b290-c8b6ccdb8b77", "entityData": [ { "job_name": "ShowCaseCSVAnomaly", "job_type": "anomaly", "job_parameters": { "driverMemory": "2g", "driverCores": 3, "executorMemory": "3G", "executorCores": 6 } } ], "indexingRequired": true, "tags": {}, "indexInSync": true }contextIdis a unique identifier string. It can be anything you define.Example Request
curl 'https://autoid-ui.forgerock.com/jas/entity/persist/autoid/api/job_definition' \ -H 'authority: autoid-ui.forgerock.com' \ -H 'sec-ch-ua: "Chromium";v="92", " Not A;Brand";v="99", "Google Chrome";v="92"' \ -H 'accept: application/json, text/plain, /' \ -H 'x-tenant-id: 8700f5cb-eaca-461e-8c2e-245a25f2399d' \ -H 'authorization: 1b7789f0-6c2f-4afa-a84b-a65a28f5c1a1' \ -H 'sec-ch-ua-mobile: ?0' \ -H 'user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36' \ -H 'content-type: application/json' \ -H 'origin: https://autoid-ui.forgerock.com' \ -H 'sec-fetch-site: same-origin' \ -H 'sec-fetch-mode: cors' \ -H 'sec-fetch-dest: empty' \ -H 'referer: https://autoid-ui.forgerock.com/jobs' \ -H 'accept-language: en-US,en;q=0.9' \ --data-raw '{ "branch": "actual", "contextId": "40c20f01-a9d8-4284-b290-c8b6ccdb8b77", "entityData": [ { "job_name": "ShowCaseCSVAnomaly", "job_type": "anomaly", "job_parameters": { "driverMemory": "2g", "driverCores": 3, "executorMemory": "3G", "executorCores": 6 } } ], "indexingRequired": true, "tags": {}, "indexInSync": true }' \ --compressed \ --insecure } }’
The Job definition for data ingestion requires a
datasourceId,which you can query. Refer to API key examples.Example Request (ingest)
curl 'https://autoid-ui.forgerock.com/jas/entity/persist/autoid/api/job_definition' \ -H 'authority: autoid-ui.forgerock.com' \ -H 'sec-ch-ua: "Chromium";v="92", " Not A;Brand";v="99", "Google Chrome";v="92"' \ -H 'accept: application/json, text/plain, /' \ -H 'x-tenant-id: 8700f5cb-eaca-461e-8c2e-245a25f2399d' \ -H 'authorization: 1b7789f0-6c2f-4afa-a84b-a65a28f5c1a1' \ -H 'sec-ch-ua-mobile: ?0' \ -H 'user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36' \ -H 'content-type: application/json' \ -H 'origin: https://autoid-ui.forgerock.com' \ -H 'sec-fetch-site: same-origin' \ -H 'sec-fetch-mode: cors' \ -H 'sec-fetch-dest: empty' \ -H 'referer: https://autoid-ui.forgerock.com/jobs' \ -H 'accept-language: en-US,en;q=0.9' \ --data-raw '{ "branch": "actual", "contextId": "ba9cefff-1e06-4cc3-b7d6-d15e2126351c", "entityData": [ { "job_name": "ShowCaseCSVIngest", "job_type": "ingest", "job_parameters": { "driverMemory": "2g", "driverCores": 3, "executorMemory": "3G", "executorCores": 6, "datasourceId": "2d7a6a76-469c-4035-b312-fb1daf104e98" } } ], "indexingRequired": true, "tags": {}, "indexInSync": true }' \ --compressed \ --insecure
POST /jas/job/run
- POST /jas/job/run
-
Run the job definition.
Endpoint
/jas/job/run
Authorization
Bearer <Token JWT-value> or <API Key-value>
Body
{ "jobType":"ingest", "jobDefinitionName":"ShowCaseCSVIngest" }Example Request
curl 'https://autoid-ui.forgerock.com/jas/job/run' \ -H 'authority: autoid-ui.forgerock.com' \ -H 'sec-ch-ua: "Chromium";v="92", " Not A;Brand";v="99", "Google Chrome";v="92"' \ -H 'accept: application/json, text/plain, /' \ -H 'x-tenant-id: 8700f5cb-eaca-461e-8c2e-245a25f2399d' \ -H 'authorization: 1b7789f0-6c2f-4afa-a84b-a65a28f5c1a1' \ -H 'sec-ch-ua-mobile: ?0' \ -H 'user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36' \ -H 'content-type: application/json' \ -H 'origin: https://autoid-ui.forgerock.com' \ -H 'sec-fetch-site: same-origin' \ -H 'sec-fetch-mode: cors' \ -H 'sec-fetch-dest: empty' \ -H 'referer: https://autoid-ui.forgerock.com/jobs' \ -H 'accept-language: en-US,en;q=0.9' \ --data-raw '{ "jobType":"ingest", "jobDefinitionName":"ShowCaseCSVIngest" }' \ --compressed \ --insecure
GET /jas/job/status
- GET /jas/job/status
-
Obtain the job’s status.
Endpoint
/jas/job/status
Authorization
Bearer <Token JWT-value> or <API Key-value>
Body
{ "jobType":"anomaly", "jobDefinitionName":"ShowCaseCSVAnomaly" }Example Request
curl 'https://autoid-ui.forgerock.com/jas/job/status' \ -H 'authority: autoid-ui.forgerock.com' \ -H 'sec-ch-ua: "Chromium";v="92", " Not A;Brand";v="99", "Google Chrome";v="92"' \ -H 'accept: application/json, text/plain, /' \ -H 'x-tenant-id: 8700f5cb-eaca-461e-8c2e-245a25f2399d' \ -H 'authorization: 1b7789f0-6c2f-4afa-a84b-a65a28f5c1a1' \ -H 'sec-ch-ua-mobile: ?0' \ -H 'user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36' \ -H 'content-type: application/json' \ -H 'origin: https://autoid-ui.forgerock.com' \ -H 'sec-fetch-site: same-origin' \ -H 'sec-fetch-mode: cors' \ -H 'sec-fetch-dest: empty' \ -H 'referer: https://autoid-ui.forgerock.com/jobs' \ -H 'accept-language: en-US,en;q=0.9' \ --data-raw '{ "jobType":"anomaly", "jobDefinitionName":"ShowCaseCSVAnomaly" }' \ --compressed \ --insecure
GET /jas/job/search
- GET /jas/job/search
-
Search for a job definition.
Endpoint
/jas/job/search
Authorization
Bearer <Token JWT-value> or <API Key-value>
Body
{ "query": { "sort": [ { "job_name.keyword": { "order": "asc" } }, { "metadata.primaryKey.keyword": { "order": "desc" } } ], "size": 10, "track_total_hits": true, "query": { "match_all": {} } } }Example Request
curl 'https://autoid-ui.forgerock.com/jas/entity/search/autoid/api/job_definition' \ -H 'authority: autoid-ui.forgerock.com' \ -H 'sec-ch-ua: "Chromium";v="92", " Not A;Brand";v="99", "Google Chrome";v="92"' \ -H 'accept: application/json, text/plain, /' \ -H 'x-tenant-id: 8700f5cb-eaca-461e-8c2e-245a25f2399d' \ -H 'authorization: 1b7789f0-6c2f-4afa-a84b-a65a28f5c1a1' \ -H 'sec-ch-ua-mobile: ?0' \ -H 'user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36' \ -H 'content-type: application/json' \ -H 'origin: https://autoid-ui.forgerock.com' \ -H 'sec-fetch-site: same-origin' \ -H 'sec-fetch-mode: cors' \ -H 'sec-fetch-dest: empty' \ -H 'referer: https://autoid-ui.forgerock.com/jobs' \ -H 'accept-language: en-US,en;q=0.9' \ --data-raw '{ "query": { "sort": [ { "job_name.keyword": { "order": "asc" } }, { "metadata.primaryKey.keyword": { "order": "desc" } } ], "size": 10, "track_total_hits": true, "query": { "match_all": {} } } }' \ --compressed \ --insecure
Data Sink
Data sink is the downstream consumer of data within Autonomous Identity for service connectors and is accessible through API endpoints.
See a conceptual image of Data Sink
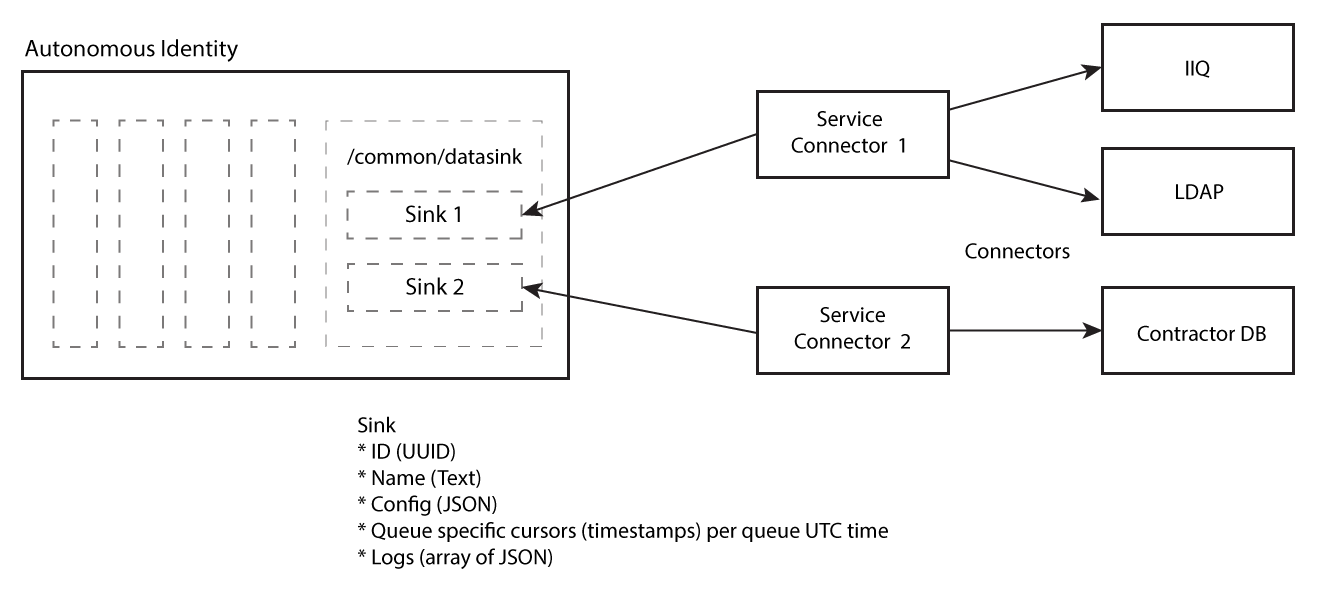
The following are Autonomous Identity datasink endpoints:
POST /api/datasink/create
- POST /api/datasink/create
-
Create a new /common/datasink entity.
Endpoint
/api/datasink/create
Authorization
<Bearer Token JWT-value>
JSON Body Parameters Parameter Type Description id
string
Data sink ID (format: UUID) (required)
name
string
Data sink name (required)
config
object
Free form client-defined connection object
autoCertifyTimestamp
string
Last auto-certification operation timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ)
autoRequestTimestamp
string
Last auto-request operation timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ)
certifyTimestamp
string
Last certification operation timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ)
revokeTimestamp
string
Last revoke operation timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ)
rolePublishTimestamp
string
Last role publish timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ)
logs
object
Free form client-defined log object
Example Request
curl -k -X POST https://autoid-ui.forgerock.com/api/datasink/create' \ -H 'Authorization: Bearer <token value>' \ -H 'Content-Type: application/json' \ -d '{ "id": "eaa19702-3806-4ee7-9466-91f0968699d9", "name": "Test", "config": { "something": 1234 } }'
Example Response (Success)
{ "message": "ok" }
POST /api/datasink/update
- POST /api/datasink/update
-
Update a /common/datasink entity.
Endpoint
/api/datasink/update
Authorization
<Bearer Token JWT-value>
JSON Body Parameters Parameter Type Description id
string
Data sink ID (format: UUID) (required)
name
string
Data sink name (required)
config
object
Free form client-defined connection object
autoCertifyTimestamp
string
Last auto-certification operation timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ)
autoRequestTimestamp
string
Last auto-request operation timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ)
certifyTimestamp
string
Last certification operation timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ)
revokeTimestamp
string
Last revoke operation timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ)
rolePublishTimestamp
string
Last role publish timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ)
logs
object
Free form client-defined log object
Example Request
curl -k -X POST https://autoid-ui.forgerock.com/api/datasink/update' \ -H 'Authorization: Bearer <token value>' \ -H 'Content-Type: application/json' \ -d '{ "id": "eaa19702-3806-4ee7-9466-91f0968699d9", "name": "Test3", "config": { "something": 5678 } }'
Example Response (Success)
{ "message": ok }
POST /api/datasink/delete
- POST /api/datasink/delete
-
Remove a /common/datasink entity.
Endpoint
/api/datasink/delete
Authorization
<Bearer Token JWT-value>
JSON Body Parameters Parameter Type Description id
string
Data sink ID (format: UUID) (required)
Example Request
curl -k -X POST https://autoid-ui.forgerock.com/api/datasink/delete' \ -H 'Authorization: Bearer <token value>' \ -H 'Content-Type: application/json' \ -d '{ "id": "eaa19702-3806-4ee7-9466-91f0968699d9" }'
Example Response (Success)
{ "message": ok }
POST /api/datasink/update/status/assignments
- POST /api/datasink/update/status/assignments
-
Update data sink status for assignment decisions. Decisions are stored in the /autoid/api/user_access_decisions JAS entity and entitlement-assignment Elasticsearch index.
Endpoint
/api/datasink/update/status/assignments
Authorization
<API Key>
JSON Body Parameters Parameter Type Description assignments
array
Array of assignment objects (properties below) (required)
Base Assignment Object Properties Parameter Type Description user
string
User ID (required)
entitlements
string array
Array of entitlement IDs (required)
datasink_status
string
Updated data sink status (required)
Example Request
curl -k -X POST \ https://autoid-ui.forgerock.com/api/datasink/update/status/assignments \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d '{ "assignments": [ { "user": "john.doe", "entitlements": [ "entitlement_1" ], "datasink_status": "ack" }, { "user": "jane.smith", "entitlements": [ "entitlement_1", "entitlement_2", ], "datasink_status": "nack" } ] }'
Example Response (Success)
{ "message": ok }
POST /api/datasink/update/status/rules
- POST /api/datasink/update/status/rules
-
Update data sink status for rule decisions. Decisions are stored in the /autoid/api/rule_access_decisions JAS entity and entitlement-assignment Elasticsearch index.
Endpoint
/api/datasink/update/status/rules
Authorization
<API Key>
JSON Body Parameters Parameter Type Description rules
array
Array of rule objects (properties below) (required)
Base Rules Object Properties Parameter Type Description entitlement
string
Entitlement ID (required)
justification
string array
Array of justifications (required)
datasink_status
string
Updated data sink status (required)
Example Request
curl -k -X POST \ https://autoid-ui.forgerock.com/api/datasink/update/status/rules \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d '{ "rules": [ { "entitlement": "entitlement_1", "justification": [ "0B_COST_CENTER_OP_TS5", "0C_USR_EMP_TYPE_Non-Employee", "10_LINE_OF_BUSINESS_Health and Safety", "13_USR_DEPARTMENT_NAME_Testing" ], "datasink_status": "nack" } ] }'
Example Response (Success)
{ "message": ok }
POST /api/datasink/update/status/roles
- POST /api/datasink/update/status/roles
-
Update data sink status for exported roles.
Endpoint
/api/datasink/update/status/roles
Authorization
<API Key>
JSON Body Parameters Parameter Type Description roles
array
Array of role objects (properties below) (required)
Base Roles Object Properties Parameter Type Description role_id
string
Role ID (required)
status
string
Role status (draft, candidate, active) (required)
datasink_status
string
Updated data sink status (required)
Example Request
curl -k -X POST \ /https://autoid-ui.forgerock.com/api/datasink/update/status/roles \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d '{ "roles": [ { "role_id": "027d9a1d-9a2f-488a-8ab2-adf404e0aecb", "status": "draft", "datasink_status": "nack" } ] }'Example Response (Success)
{ "message": ok }
POST /api/datasink/query
- POST /api/datasink/query
-
Query data sink entities. Optional filtering can be applied as a JSON request body outlined below.
Endpoint
/api/datasink/query
Authorization
<API Key>
JSON Body Parameters Parameter Type Description id
string
Data sink ID (format: UUID)
name
string
Data sink name
autoCertifyTimestamp
object
Last auto-certify operation timestamp filter object (available properties below)
autoRequestTimestamp
object
Last auto-request operation timestamp filter object (available properties below)
certifyTimestamp
object
Last certify operation timestamp filter object (available properties below)
revokeTimestamp
object
Last revoke operation timestamp filter object (available properties below)
rolePublishTimestamp
object
Last role publish timestamp filter object (available properties below)
timestampThresholds Object Properties Parameter Type Description gt
string
Greater than timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with gte.
gte
string
Greater than or equal timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with gt.
lt
string
Less than timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with lte.
lte
string
Less than or equal timestamp (format: yyyy-mm-ddThh:mm:ss.SSSZ). Cannot be present with le.
Example Request
curl -k -X POST \ https://autoid-ui.forgerock.com/api/datasink/query \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d '{ "name": "IIQ", "certifyTimestamp": { "gt": "2021-11-19T10:01:19.937Z", "lte": "2021-11-20T10:01:19.937Z" } }'
Example Response (Success)
[ { "id": "b72c15b7-7dcb-44ac-b1d3-162565e360b4", "name": "IIQ", "certifyTimestamp": "2021-11-19T11:01:19.937Z", "auto_request_timestamp": "2021-10-01T10:01:19.937Z" }, { "id": "9501810e-1480-4f41-80d4-bc97154fddeb", "name": "IIQ", "certifyTimestamp": "2021-11-20T09:01:19.937Z", "auto_request_timestamp": "2021-10-01T10:01:19.937Z" } ]
POST /api/datasink/update/timestamp
- POST /api/datasink/update/timestamp
-
Update timestamps for a data sink entity.
Endpoint
/api/datasink/update/timestamp
Authorization
<API Key>
JSON Body Parameters Parameter Type Description id
string
Data sink ID (format: UUID)
autoCertifyTimestamp
object
Last auto-certify operation timestamp filter object (format: yyyy-mm-ddThh:mm:ss.SSSZ)
autoRequestTimestamp
object
Last auto-request operation timestamp filter object (format: yyyy-mm-ddThh:mm:ss.SSSZ)
certifyTimestamp
object
Last certify operation timestamp filter object (format: yyyy-mm-ddThh:mm:ss.SSSZ)
revokeTimestamp
object
Last revoke operation timestamp filter object (format: yyyy-mm-ddThh:mm:ss.SSSZ)
rolePublishTimestamp
object
Last role publish timestamp filter object (format: yyyy-mm-ddThh:mm:ss.SSSZ)
Example Request
curl -k -X POST \ https://autoid-ui.forgerock.com/api/datasink/update/timestamp \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d ' { "id": "87e341c0-c1aa-4b0e-9ae5-1384bb6de8fc", "certifyTimestamp": "2021-11-19T10:01:19.937Z", "revokeTimestamp": "2021-11-19T10:01:19.937Z" }'
Example Response (Success)
{ "message": "ok" }
POST /api/datasink/query/logs
- POST /api/datasink/query/logs
-
Query data sink logs. Optional filtering can be applied as a JSON request body outlined below.
Endpoint
/api/datasink/query/logs
Authorization
<API Key>
JSON Body Parameters Parameter Type Description id
string
Data sink ID (format: UUID)
name
string
Data sink name
Example Request
curl -k -X POST \ https://autoid-ui.forgerock.com/api/datasink/query/logs \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d '{ "name": "IIQ" }'
Example Response (Success)
[ { "id": "5f8c48c5-8f70-43a0-a9a6-61d1b017dac7", "name": "IIQ", "certify_timestamp": "2021-10-01T10:01:19.937Z", "revokeTimestamp": "2021-10-23T10:01:19.937Z", "logs": [ { "message": "log 1" }, { "message": "log 2" } ] }, { "id": "9c68c658-2d7d-487c-a0ce-6d9cdcc7eaf7", "name": "IIQ", "certify_timestamp": "2021-10-01T10:01:19.937Z", "revokeTimestamp": "2021-10-01T10:01:19.937Z", "logs": [ { "message": "log 1" }, { "message": "log 2" } ] } ]
POST /api/datasink/update/logs
- POST /api/datasink/update/logs
-
Update data sink logs.
Endpoint
/api/datasink/update/logs
Authorization
<API Key>
JSON Body Parameters Parameter Type Description id
string
Data sink ID (format: UUID) (required)
logs
object
JSON logs object (required)
Example Request
curl -k -X POST \ https://autoid-ui.forgerock.com/api/datasink/update/logs \ -H 'X-API-KEY: <api key value>' \ -H 'Content-Type: application/json' \ -d '{ "id": "87e341c0-c1aa-4b0e-9ae5-1384bb6de8fc", "logs": { "logs": [ { "created": "2021-11-19T09:01:19.937Z", "type": "INFO", "message": "transaction started" }, { "created": "2021-11-19T10:01:19.937Z", "type": "INFO", "message": "transaction successful" } ] } }'
Example Response (Success)
{ "message": "ok" }