Configuring PingFederate group access for PingAuthorize
Configure PingFederate so that only members of a specific LDAP group are authorized to access the application.
About this task
Configuring PingFederate for PingAuthorize and Configuring PingAuthorize Policy Editor to use PingFederate explain how to configure the PingAuthorize Policy Editor and PingFederate so that any authenticated user can access the PingAuthorize Policy Editor. This task describes how to configure PingFederate to limit access to a specific LDAP group.
Steps
-
Create an LDAP group in PingDirectory and add the desired user (
user.20) to the group.-
Create a file named
create-policy-writer-group.ldifand add the following.dn: ou=groups,dc=example,dc=com objectclass: top objectclass: organizationalunit ou: groups dn: cn=PolicyWriter,ou=groups,dc=example,dc=com objectclass: top objectclass: groupOfUniqueNames cn: PolicyWriter ou: groups uniquemember: uid=user.20,ou=People,dc=example,dc=com
-
Use the PingDirectory
ldapmodifytool to load the newly createdldiffile./opt/PingDirectory/bin/ldapmodify -a -f create-policy-writer-group.ldif
-
-
Add the group membership claim requirement in PingFederate.
-
In PingFederate, go to Applications > OAuth > Access Token Mappings.
-
Select the PingDirectory mapping from the list, and then on the Attribute Sources & User Lookup tab, select the PingDirectory source.
-
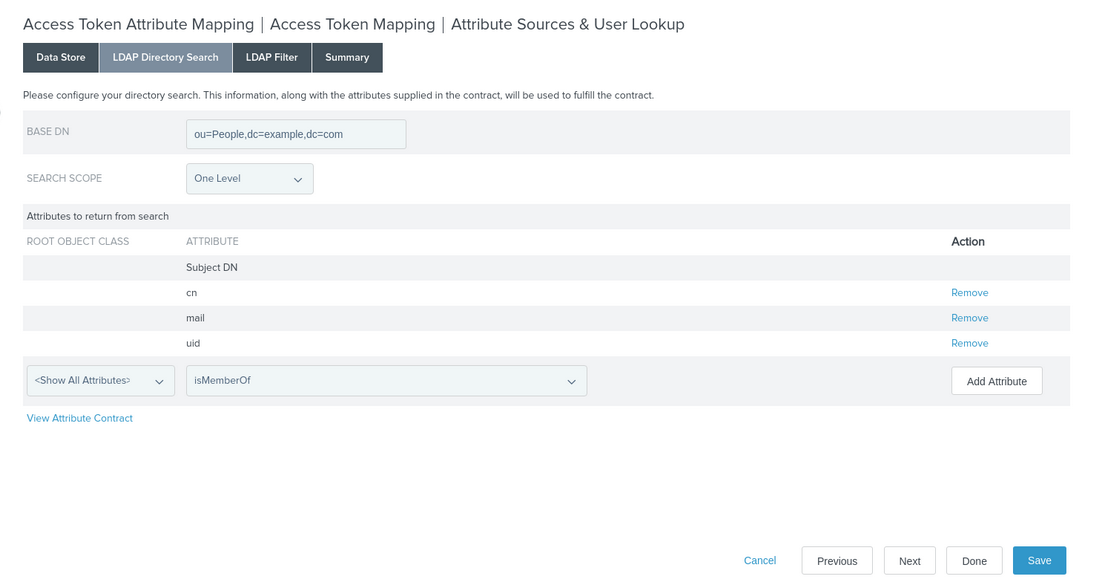
Click the LDAP Directory Search tab, and in the Root Object Class list, select Show All Attributes.
-
Add the isMemberOf attribute, and then click Done to return to Access Token Attribute Mapping.
-
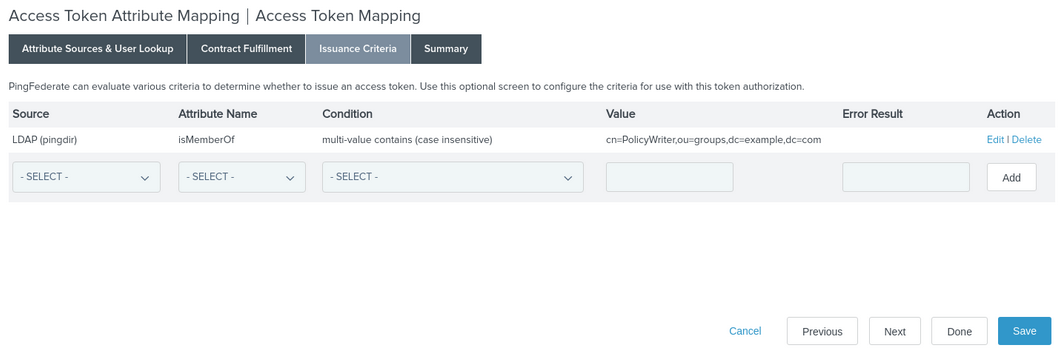
Go to the Issuance Criteria tab and add a new row with the following values:
Column Value Source
LDAP (pingdir)
Attribute Name
isMemberOf
Condition
multi-value contains (case sensitive)
Value
cn=PolicyWriter,ou=groups,dc=example,dc=com
-
Click Save.
Result:
Only
user.20can access the PingAuthorize Policy Editor.
-
-
Verify that only specified users can access the PingAuthorize Policy Editor.
Clear any active SSO sessions before you sign on as each user.
-
Sign on as
user.0.Result:
Access is denied.
-
Sign on as
user.20.Result:
Access is granted.
-