Creating the OIDC policy
Steps
-
Go to Applications → OAuth → OpenID Connect Policy Management.
-
Click Add Policy.
-
On the Manage Policy tab:
-
In the Policy ID field, enter the policy identifier.
-
In the Name field, enter the policy name.
-
In the Access Token Manager menu, select your JWT access token manager.
-
Click Next.
-
-
On the Attribute Contract tab, add the
admin_role,iss, andmemberOfattribute contracts.-
In the Extend the Contract field, enter
admin_role, and click Add. -
Repeat step a. to add the
issandmemberOfattributes. -
Click the Edit action for
admin_role. Select the Override Default Delivery and ID Token check boxes, then click the Update action. -
Repeat step c for
iss, selecting the ID Token check box, and formemberOf, selecting the UserInfo check box.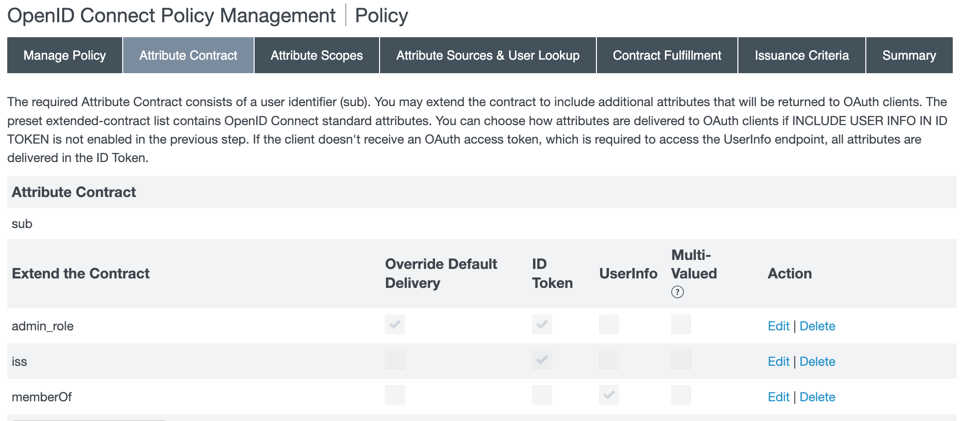
-
Click Next.
-
-
On the Attribute Scopes tab, add the
admin_roleandissattributes to the openid scope and thememberOfattribute to the profile scope.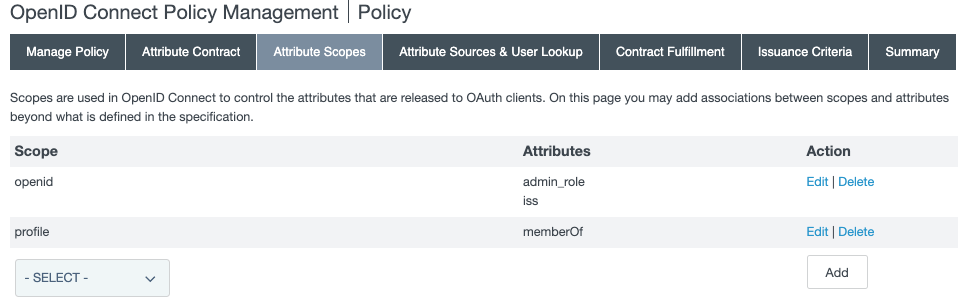
-
In the Scope menu, select openid. Select the
admin_roleattribute’s check box, and click Add. Theissattribute should already be selected. -
In the Scope menu, select profile. Select the
memberOfattribute’s check box, and click Add. -
Click Next.
-
-
On the Attribute Sources & User Lookup tab, click Next.
-
On the Contract Fulfillment tab, select a Source and a Value to map into the
admin_role,iss,memberOf, andsubitems in the Attribute Contract list.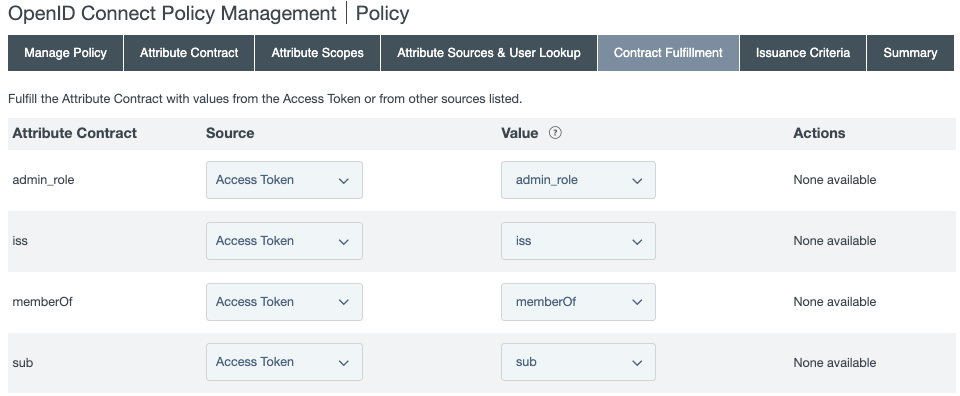
-
For the
admin_roleattribute contract, select Access Token in the Source menu and admin_role in the Value menu. -
For the
issattribute contract, select Access Token in the Source menu and iss in the Value menu. -
For the
memberOfattribute contract, select Access Token in the Source menu and memberOf in the Value menu. -
For the
subattribute contract, select Access Token in the Source menu and sub in the Value menu. -
Click Next.
-
-
On the Issuance Criteria tab, click Next.
-
On the Summary tab, review your configuration. Click Save.