Configuring authentication applications
You can let highly-trusted authentication applications employ the PingFederate Authentication API.
About this task
The following procedure describes how to use the Authentication Application window to integrate an authentication application with PingFederate.
Steps
-
Go to Authentication > Integration > Authentication API Applications.
Choose from:
-
To integrate a new application, click Add Authentication Application.
-
To modify an existing application’s settings, click the Application Name.
-
-
Provide information for each field.
For more information, see the following table.
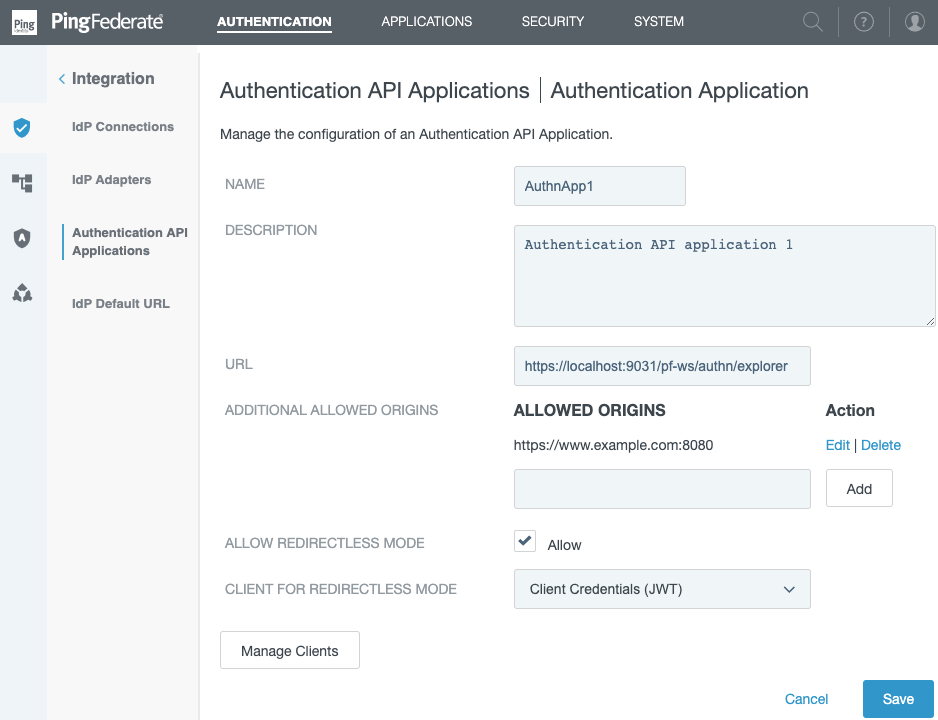
Field Description Name
The name of the authentication application.
Description
An optional description of the authentication application.
URL
The URL of the authentication application.
Additional Allowed Origins
Enter any number of trusted origins to enable cross-origin resource sharing (CORS) support for the authentication API endpoint.
Once configured, client-side web applications from the trusted origins are allowed to make requests to the PingFederate authentication API endpoint. For more information about CORS, see W3C’s recommendation on Cross-Origin Resource Sharing.
The following list includes example origin formats and their expected behaviors:
https://www.example.com-
CORS requests originating from https://www.example.com are allowed.
https://www.example.com:8080-
CORS requests originating from https://www.example.com:8080 are allowed.
https://www.example.com:-
CORS requests originating from https://www.example.com:<any port> are allowed.
Given this sample entry, a port number is required in the
Originrequest header.Although using the wildcard character provides the convenience of allowing multiple origins with one entry, we recommend adding individual origins to limit CORS requests to a list of trusted hosts.
Click Add to save an entered origin. Repeat to add multiple origins.
Allow Redirectless Mode
To allow the authentication application to use redirectless mode with a specified OAuth client, select this checkbox. Then select a Client for Redirectless Mode.
This checkbox is not selected by default. It is visible only if the Restrict Access to Redirectless Mode checkbox on the Authentication API Applications window is selected. For more information, see Managing authentication applications.
Client for Redirectless Mode
Select the OAuth client that will use this authentication application in redirectless mode. The client must allow authentication API redirectless mode. For more information, see Configuring OAuth clients.
This field is visible only if the Allow Redirectless Mode checkbox is selected.
-
To keep your configuration, click Save to or click Cancel to discard any changes made.