Enterprise deployment features
PingFederate’s enterprise-deployment architecture provides one location to manage your environment, eliminating the need to maintain redundant copies of these configurations and trust relationships.
One-time configuration, available everywhere
PingFederate houses all protocol definitions, public key infrastructure (PKI) keys, policies, and profiles in a single location. You can add new protocols, profiles, or use cases, and then make them available to your entire organization.
Improved security
PingFederate improves security by creating a single “doorway” through which all your identity information is exchanged. The same doorway is used regardless of who the users are or in which direction information is shared, such as internal users accessing external applications and external users accessing internal systems.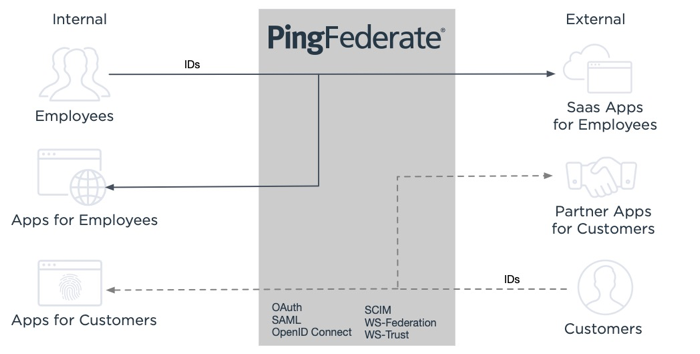
Load balancers and reverse proxies
To enhance performance and security, you can deploy PingFederate behind an application load balancer (ALB), a network load balancer (NLB), a reverse proxy, or a similar network traffic management solution on-premise or in the cloud.
|
PingFederate can benefit from knowing the originating IP addresses of incoming requests. Before you deploy PingFederate in the cloud or behind a load balancer, to avoid unexpected behaviors, work with your network team and configure PingFederate’s Incoming Proxy Settings accordingly. For more information, see Configuring incoming proxy settings. |