Connecting to a remote process
Use the remote process option to establish a connection when the PingAccess server is running as a Windows service, or if the com.pingidentity.pa.cli.Starter class is unavailable in the Local Process list.
About this task
Use these instructions to configure the remote process option to establish a connection. For demonstration purposes, the following task uses an Lightweight Directory Access Protocol (LDAP) configuration.
|
No direct configuration support is provided for enabling remote access Java Management Extensions (JMX) for the PingAccess server. To enable this level of access, use the built-in options that are available through the Java Virtual Machine (JVM). For more information, see Monitoring and Management Using JMX Technology in the Oracle Java Development Kit (JDK) documentation. |
Steps
-
In the
jvm-memory.optionsfile for the PingAccess server, add the following text at the end of the last memory settings:#Settings to enable remote access to JMX -Dcom.sun.management.jmxremote.port=5000" -Dcom.sun.management.jmxremote.login.config=ExampleCompanyConfig" #Configuration is assumed to be in the conf folder, relative path used -Djava.security.auth.login.config=conf/ldap.config" -Dcom.sun.management.jmxremote.ssl=false"
Each entry must reside on its own line. In this example, a relative path is used for the
ldap.configfile. Some deployments might require a full path.In a production environment, use Secure Sockets Layer (SSL), as shown in this example for initial testing and debugging. For information about setting up SSL, see Monitoring and Management Using JMX Technology in the Oracle JDK documentation.
-
Create the
ldap.configfile.ExampleCompanyConfig { com.sun.security.auth.module.LdapLoginModule REQUIRED userProvider="ldaps://ldap.server:port/OU=where,OU=users,OU=located" userFilter="(&(uid={USERNAME})(objectClass=inetOrgPerson))" authIdentity="uid={USERNAME},OU=where,OU=users,OU=located" authzIdentity=monitorRole useSSL=true; };Each entry must reside on its own line. In this example,
ldap.configis placed in the PingAccessconffolder. If your JVM setup trusts the certificates, you can use SSL. Because of theauthIdentityoption, the configuration binds as the user that you enter. Otherwise, an anonymous bind validates the user name but not the password. -
Place the
ldap.configfile that you created in step 2 in a location from which the PingAccess process can read it at start up. -
If you have a clustered PingAccess environment:
-
Perform steps 1 - 3 to each node in the cluster.
-
Restart each node.
-
-
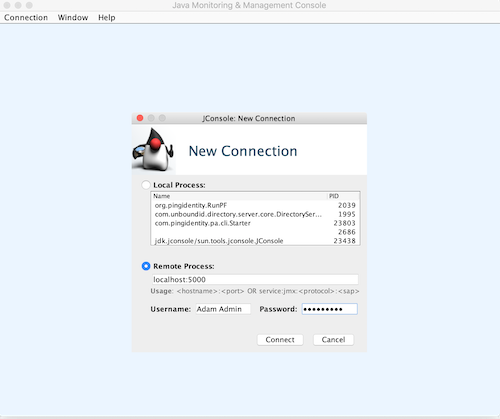
After you enable the JMX service, connect to the remote JMX service by specifying one of the following:
Choose from:
-
The name of the PingAccess server instance
-
The Internet Protocol (IP) address, port, and authentication credentials.
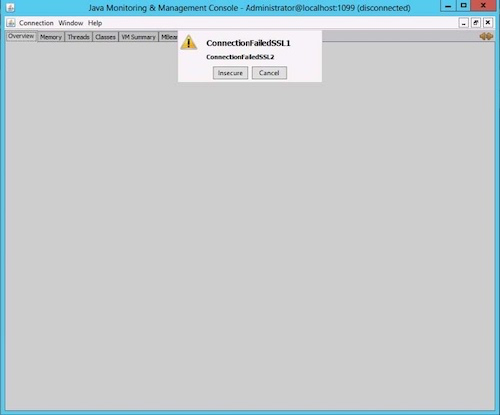
Because JMX uses SSL by default when communicating with a remote host, the client host must trust the SSL certificate that is presented during setup for JMX. If the JMX client does not trust the JMX certificate, it displays the following message:
ConnectionFailedSSL1
-
Troubleshooting:
-
If SSL is enabled, import the JMX SSL certificate to the client’s trusted certificates.
-
If SSL is disabled, click Insecure to connect.