PingAccess Agent for IIS
The PingAccess agent for IIS is a Microsoft Internet Information Services module that intercepts requests to the web server’s protected resources and evaluates applicable access control policies. These policies are evaluated by either accessing a locally cached policy decision or by querying the PingAccess engine node.
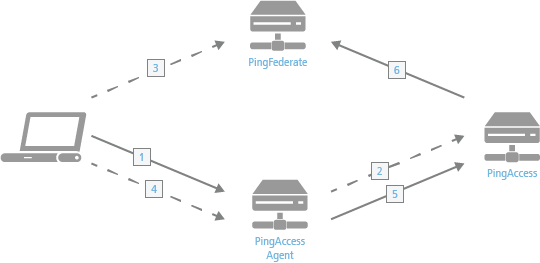
Processing steps
-
The client accesses a resource. If the user is already authenticated, this process continues with step 5.
-
The agent asks PingAccess for instructions. PingAccess checks the URL policy and determines that it is a protected resource. PingAccess then redirects the client to PingFederate to establish a session.
-
The user logs in, and PingFederate creates the session.
-
The client is then redirected back to the resource.
-
The agent asks PingAccess for instructions. PingAccess checks the URL policy and determines that it is a protected resource. PingAccess then checks the session token and determines that it is valid.
-
If session revocation is enabled, PingAccess checks and updates the central session revocation list. If the session is valid, the agent is instructed to set identity HTTP headers.
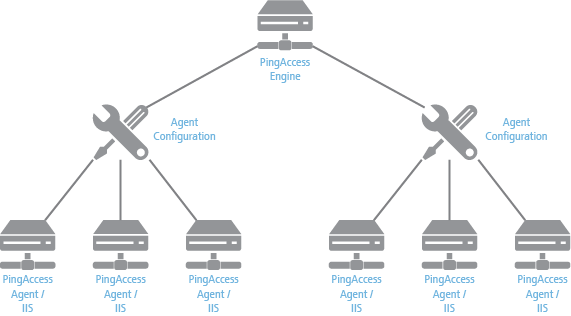
Within the PingAccess administrative console, agent nodes are configured with information that allows a PingAccess agent to connect to the engine node to retrieve information about access control policies for resources within that agent’s control. An agent configuration has a one-to-many relationship with PingAccess agents, allowing a single agent configuration bootstrap file to be used on multiple web servers within a server farm.
|
An agent node is a shared configuration used by one or more agents, rather than a specific agent instance. |
|
A problem with the PingAccess IIS agent configuration might cause all applications in an IIS application pool to become unreachable. To maximize availability of unprotected resources, place applications protected by the PingAccess agent in a separate pool. |
The features documented here are affected by the settings in the configuration file. See the Configuration file reference for more information.