Key store configuration for policy information providers
The policy engine supports the use of policy information providers (PIPs) to dynamically retrieve data from external services at runtime. You can configure a key store for a PIP in PingAuthorize.
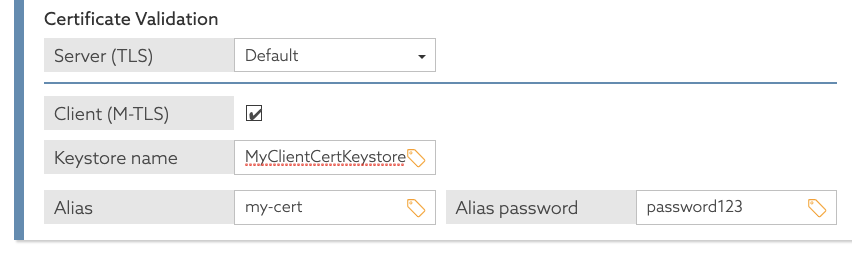
Some policy information providers might use MTLS, in which a client presents a client certificate to establish TLS communications with a server. In such cases, the policy engine can use a client certificate contained in a Java KeyStore (JKS) or PKCS12 key store. The key store details are then configured in an options file in the keystores section. A JKS key store file should use the extension .jks, while a PKCS12 key store file should use the extension .p12.
Example
Given a JKS key store named my-client-cert-keystore.jks with the password password123 and a client certificate with the alias my-cert, create an options file with details about the key store.
To set up this key store, complete the following steps.
-
Make a copy of the default options file.
$ cp config/options.yml my-options.yml -
Edit the new options file and define the key store details by adding an item under the
keystoressection.keystores: - name: MyClientCertKeystore resource: /path/to/my-client-cert-keystore.jks password: password123 # Other options omitted for brevity... -
Stop the Policy Editor.
$ bin/stop-server -
Run
setupusing the--optionsFileargument. Customize all other options as appropriate for your needs.$ bin/setup demo \ --adminUsername admin \ --generateSelfSignedCertificate \ --decisionPointSharedSecret pingauthorize \ --hostname <pap-hostname> \ --port <pap-port> \ --adminPort <admin-port> \ --licenseKeyFile <path-to-license> \ --optionsFile my-options.yml -
Start the Policy Editor.
$ bin/start-server
After you define the policy information provider in the Trust Framework, you can refer to the key store that you configured using the name MyClientCertKeystore.