Creating a policy to check consent and then permit or deny access
Using the Trust Framework attributes and services we created, we now create a policy for the meme game API to get a user’s answers. The policy permits access if consent exists and the consent status is accepted.
Steps
-
In the Policy Editor, go to Policies in the left pane and then click Policies along the top.
The following steps create a policy under an existing policy called meme-game policies. This existing policy is for all requests to the meme game.
-
Select the existing meme-game policies policy.
-
From the menu, select Add Policy.
-
For the name, replace Untitled with
Requests for a user’s answers. -
Click the next to Applies to.
-
Click Add definitions and targets, or drag from Components and add the meme-game.user_answers service, which we set up in Getting a path component from the request URL. Also add the inbound-GET action.
-
Set Combining Algorithm to Unless one decision is permit, the decision will be deny.
-
Add a rule so that a user can access their own answers.
-
Click Add Rule.
-
For the name, replace Untitled with
Permit a user to request their own answers. -
Click Comparison.
-
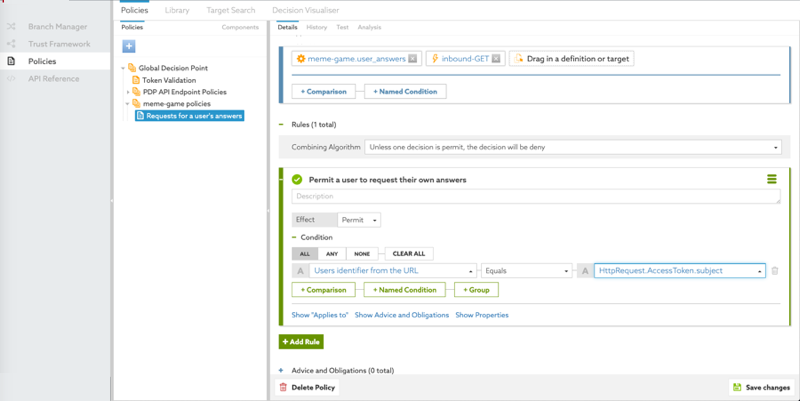
From the Select an Attribute list, select Users identifier from the URL, which we also set up in Getting a path component from the request URL.
-
In the second field, select Equals.
-
In the third field, click the C to toggle to an A (for attribute) so that you can select the HttpRequest.AccessToken.subject attribute.
The following image shows this configuration.
-
Click Save changes.
-
-
Test the rule.
The following image shows a test with Postman making a request to the user.0 answers as user.0. The response shows the rule works.
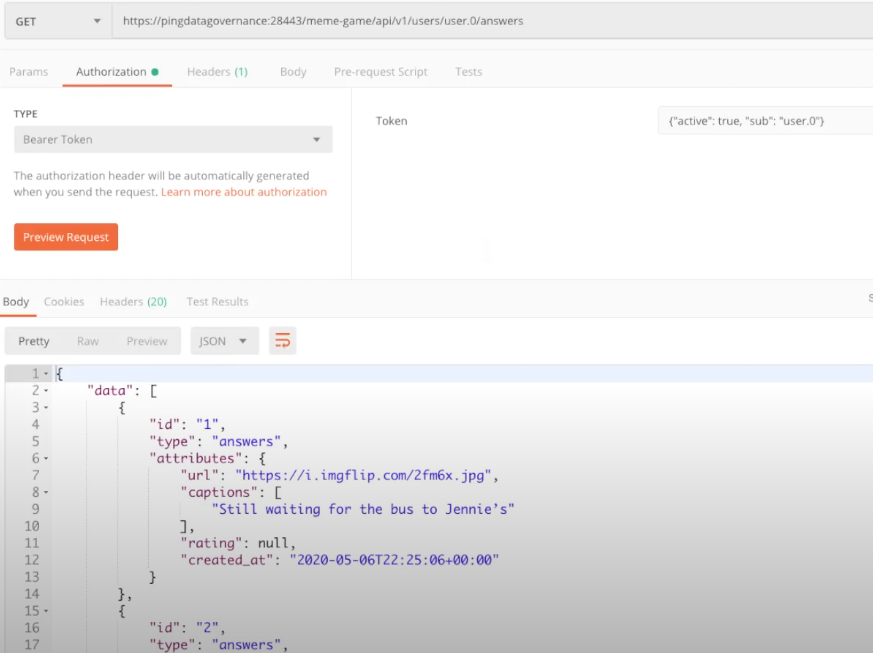
If we try again with user.1, the request is denied. Even though user.1 does have a consent record in our consent store, the policy does not do anything with that consent record. We need another rule to look at the consent record and get the status from that record.
-
Add a rule to get status from a consent record.
-
Click Add Rule.
-
For the name, replace Untitled with
Permit if resource owner gave consent to share answers. -
Click Comparison.
-
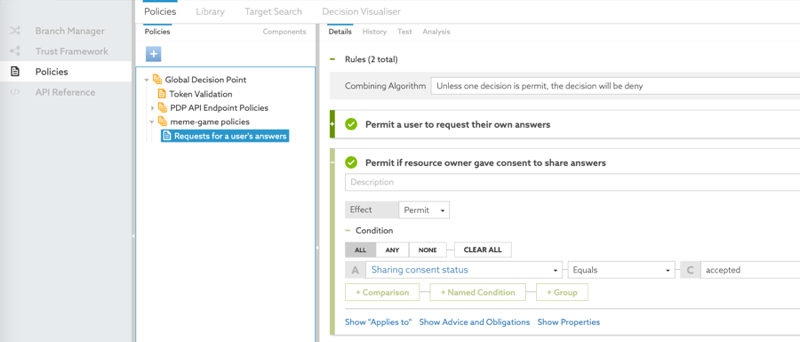
From the Select an Attribute list, select Sharing consent status, which we set up in Getting consent status from the consent record.
-
In the second field, select Equals.
-
In the third field, type
accepted.This value is the status to check against.
The following image shows this rule.
-
Click Save changes.
-
-
Test the policy with both rules in place now.
A request to the user.0 answers as user.1 should now work.
However, a request to the user.0 answers as a user without a consent record, say user.2, is denied.
The user.2 request is denied because of the combining algorithm, Unless one decision is permit, the decision will be deny. When the policy engine evaluates the policy rules, the Permit a user to request their own answers rule does not produce a permit because user.2 is not requesting their own answers. The Permit if resource owner gave consent to share answers rule uses the
Sharing consent statusattribute. user.0 does not have a consent record for user.2. With no consent record to get status from, the policy engine cannot evaluate the rule. So this rule also does not produce a permit. Thus, the combining algorithm produces a deny for the user.2 request.If user.0 revokes the consent given to user.1, the status in the consent record becomes
revoked. The rule no longer applies, so user.1 requests are then denied.