Creating a policy to restrict the ability to delete based on resource type
For a given resource type, restrict the ability to delete. In particular, the policy focuses on the delete action and then denies the action when the resource type is Devices.
Steps
-
In the Policy Editor, go to Policies in the left pane and then click Policies along the top.
-
From the menu, select Add Policy.
-
For the name, replace Untitled with
User cannot delete a Device resource. -
Click the next to Applies to.
-
Click Add definitions and targets, or drag from Components and add the delete action.
-
Set Combining Algorithm to Unless one decision is deny, the decision will be permit.
You should have a screen similar to the following one for the policy so far.
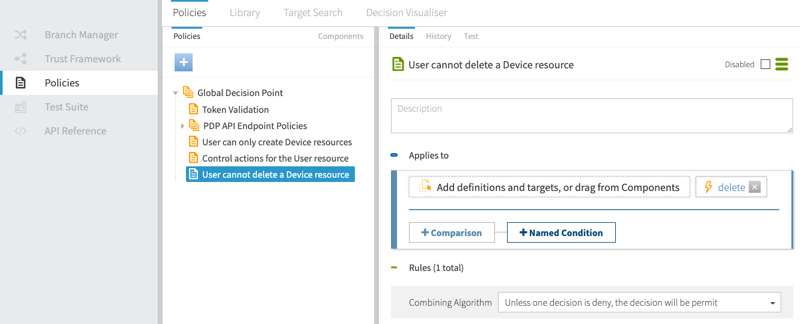
-
Add a rule to deny the deletion of Device resources.
-
Click Add Rule.
-
For the name, replace Untitled with
If the SCIM resource type is Device, then deny. -
Set Effect to Deny.
-
Click Comparison.
-
In the Select an Attribute list, select the
SCIM2.resource.meta.resourceTypeattribute. -
In the second field, select Equals.
-
In the third field, specify
Devicesas the constant. -
Add advice to provide a custom message.
-
Within the rule, click Show Advice and Obligations.
-
Click next to Advice and Obligations.
-
Click Add Advice → Denied Reason.
-
For the name, specify
denied-reason. -
Set Applies To to Deny.
-
In the Payload field:
-
Remove
Example: -
Change
Human-readable error messageto
System has restricted the ability to delete Device resources
-
-
-
Click Save changes.
Your rule should be similar to the following one.
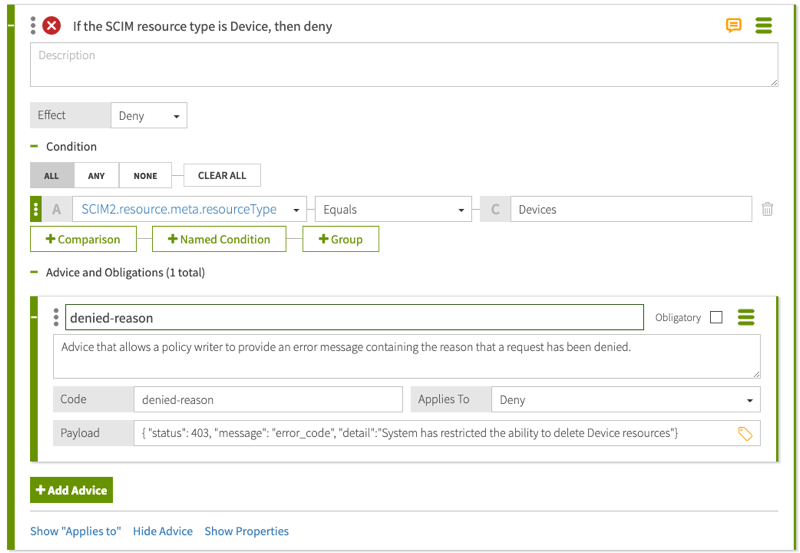
-
-
Send test requests to the SCIM service and verify data using the Policy Editor’s Decision Visualiser.