Prepare policies for production
If you configured any of the following features during policy development and testing using the Policy Editor as your decision point, you need to reconfigure these features before putting your policies into a production environment using PingAuthorize Server as your decision point:
Example: Define a policy information provider key store for MTLS
The policy engine supports the use of PIPs to dynamically retrieve data from external services at runtime. In these cases, the policy engine can use a client certificate contained in a Java KeyStore (JKS) or PKCS12 key store.
When using embedded PDP mode, the key store containing the client certificate is represented in the PingAuthorize Server configuration as a Key Manager Provider, which is then assigned to the Policy Decision Service.
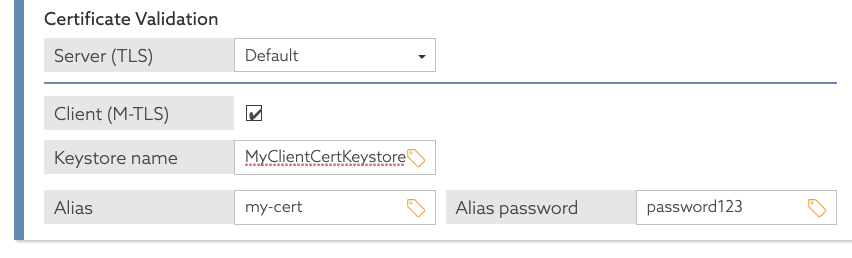
The following example creates a Key Manager Provider named MyClientCertKeystore and makes it available to the policy engine.
dsconfig create-key-manager-provider \ --provider-name MyClientCertKeystore \ --type file-based \ --set enabled:true \ --set key-store-file:<full path to a key store> \ --set key-store-type:JKS \ --set key-store-pin:<key store password> dsconfig set-policy-decision-service-prop \ --set service-key-store:MyClientCertKeystore
When you define the PIP in the Trust Framework, you can refer to the key store that you configured, using the name MyClientCertKeystore.
Example: Define a policy information provider trust store
For a policy information provider (PIP), you can use the Java Runtime Environment (JRE)'s default trust store or you can provide a custom Java KeyStore (JKS) or PKCS12 trust store.
The policy engine supports the use of PIPs to dynamically retrieve data from external services at runtime. By default, the policy engine determines whether it should accept a PIP’s server certificate using the Java Runtime Environment (JRE)'s default trust store, which contains public root certificates for common certificate authorities. However, if your PIP uses a server certificate issued by some other certificate authority, for example, a private certificate authority operated by your organization, then you can provide a custom Java KeyStore (JKS) or PKCS12 trust store.
When using embedded PDP mode, the trust store containing the client certificate is represented in the PingAuthorize Server configuration as a Trust Manager Provider, which is then assigned to the Policy Decision Service.
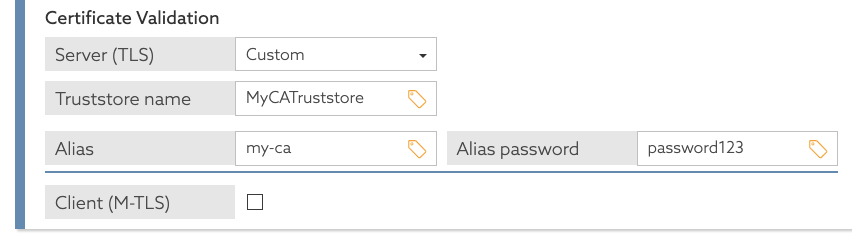
The following example creates a Trust Manager Provider named MyCATruststore and makes it available to the policy engine.
dsconfig create-trust-manager-provider \ --provider-name MyCATruststore \ --type file-based \ --set enabled:true \ --set trust-store-file:<full path to a trust store> \ --set trust-store-type:JKS dsconfig set-policy-decision-service-prop \ --set service-trust-store:MyCATruststore
When you define the policy information provider in the Trust Framework, you can refer to the trust store that you configured using the name MyCATruststore.
Example: Add SpEL Java classes to the allowed list
When you develop policies, you can use SpEL expressions in your deployment packages. Configure the Java classes used during SpEL expression evaluation by adding classes to the allowed list.
When using embedded PDP mode, the policy engine allows use of the following classes by default.
java.lang.String java.util.Date java.util.UUID java.lang.Integer java.lang.Long java.lang.Double java.lang.Byte java.lang.Math java.lang.Boolean java.time.LocalDate java.time.LocalTime java.time.LocalDateTime java.time.ZonedDateTime java.time.DayOfWeek java.time.Instant java.time.temporal.ChronoUnit java.text.SimpleDateFormat java.util.Collections
Use dsconfig or the administrative console to add non-standard classes to the allowed list. In the administrative console, you can find SpEL allowed classes in the Policy Decision Service configuration.
Example
The following example shows how to add the java.time.format.DateTimeFormatter and java.util.Base64 classes to the allowed list. Run dsconfig with the set-policy-decision-service-prop option.
dsconfig set-policy-decision-service-prop \ --set spel-allowed-class:java.time.format.DateTimeFormatter \ --set spel-allowed-class:java.util.Base64
|
After you add non-standard classes to the allowed list, you must make them available on the server classpath at server start. |
The following example shows how to add .jar files containing the classes to the lib folder and restart the server.
cd <paz-instance-root> cp <jar-file-dir>/addl-spel-classes.jar lib bin/stop-server -R