Supporting Web+API Applications
PingAccess simplifies adding OpenID Connect (OIDC) and OAuth to API-based web applications, such as single-page applications (SPAs).
About this task
In this configuration, PingAccess completely manages the OIDC authentication for the SPA, maintains a cookie-based web session with the browser, and replaces the cookie for an OAuth access token (or other identity mappings) before invoking the target API. You must perform additional steps to support this configuration.
Steps
-
Configure Apigee to intercept calls for PingAccess.
If you selected the Use context root as reserved resource base path checkbox on the PingAccess application you plan to use in conjunction with Apigee, skip ahead to step 2. When enabled, this feature provides reserved PingAccess resources from that application’s context root, which makes step 1 unnecessary.
-
In Apigee, go to Develop > API Proxies and click Create New.
-
On the Create Proxy page, click No Target.
-
In the Name field, enter
PingAccess. -
In the Base Path field, enter
/pa.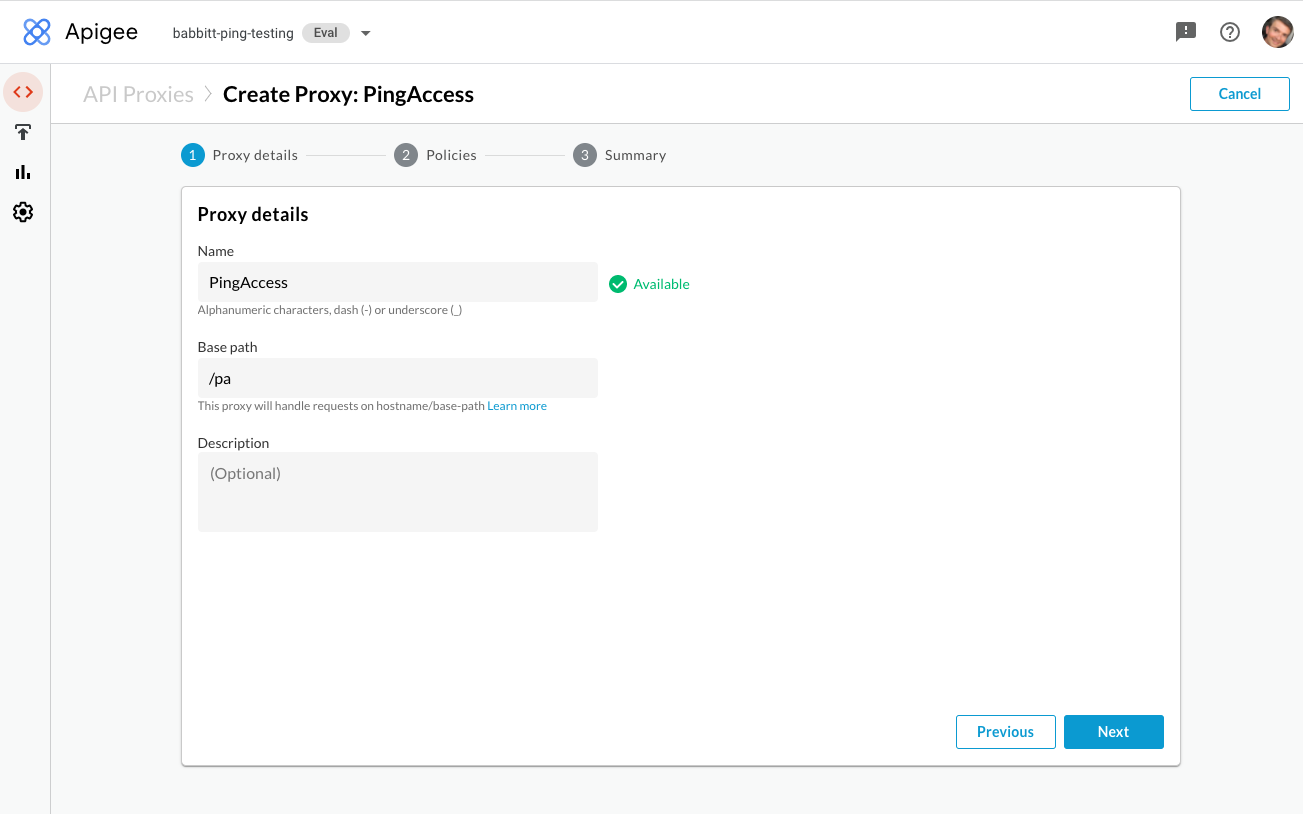
-
In the Policies section of the Navigator, click to add a policy.
-
Add a Flow Callout Policy, and in the Shared Flow list, select PingAuth.
-
Click Save.
-
In the Proxy Endpoints section of the navigator, select PreFlow, then add the flow callout policy as a Request Step.
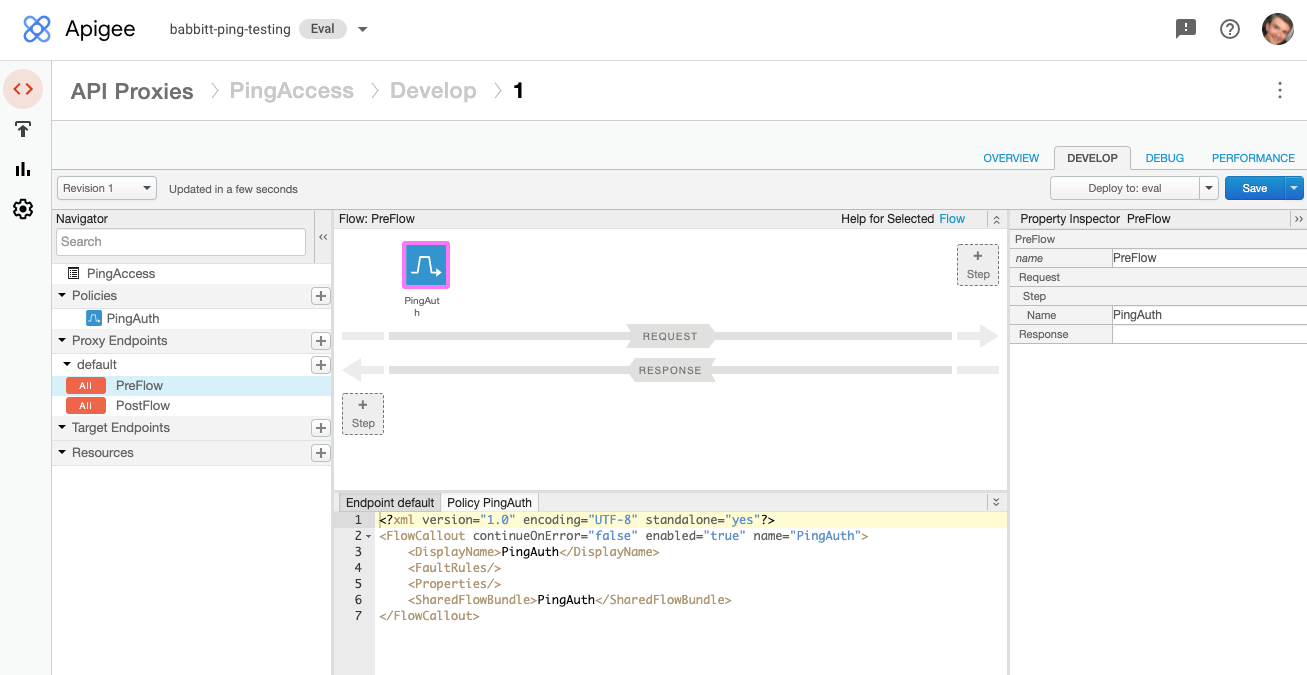
-
Save and deploy the new proxy.
-
-
Add a Web+API application in PingAccess:
-
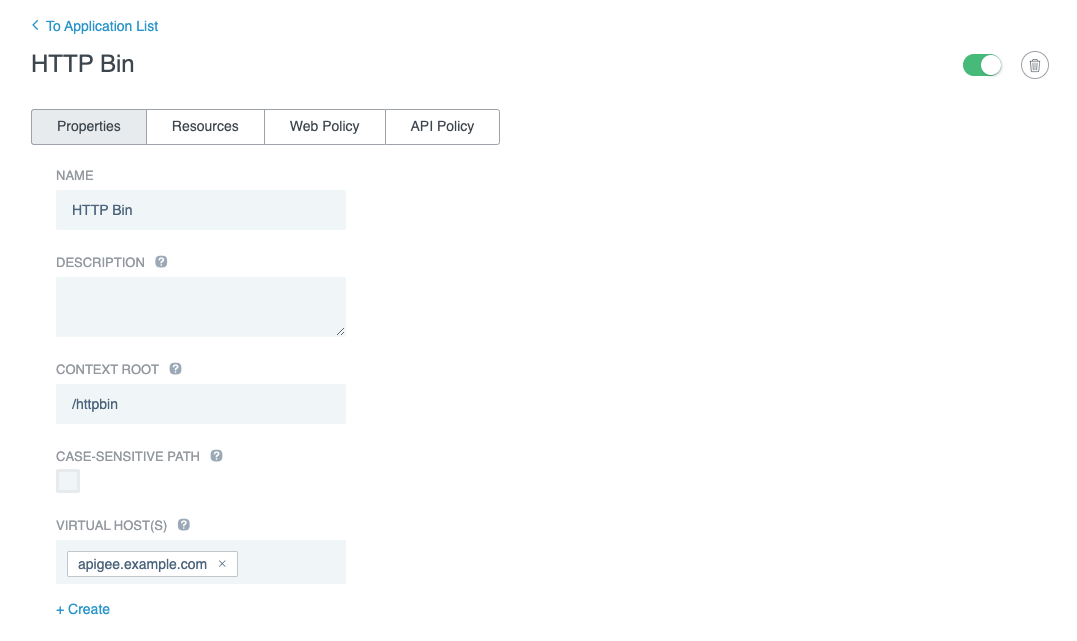
Go to Applications > Applications and click +Application.
-
Enter a Name, and then enter the Context Root and select or create Virtual Host(s) values to match how the application’s APIs are exposed from your Apigee environment.
To create a Virtual Host, click +Create below the field name.
-
-
Configure the web session:
-
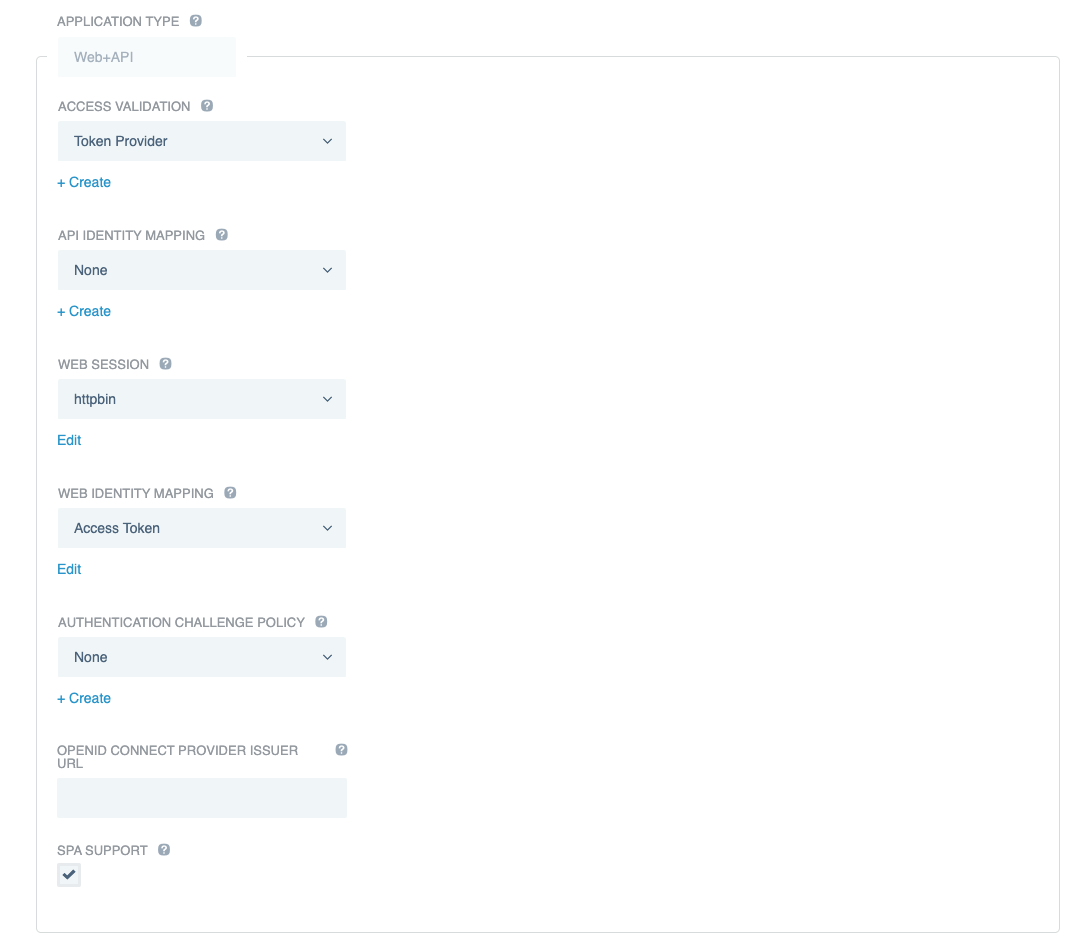
In the Application Type list, select Web+API.
-
Under Web Session, click +Create.
-
Enter the web session details, including the OIDC sign-on details configured in your OpenID Provider (OP).
PingAccess can only manage the OIDC authentication on behalf of the browser if PingAccess, through Apigee, is configured as the redirect URL in your OIDC provider.
For example,
https://apigee.example.com/pa/oidc/cb. -
Click Save to save the web session.
-
Under Web Identity Mapping, click +Create.
-
Name the identity mapping Access Token and select the type Web Session Access Token.
This configures PingAccess to forward the OAuth Access Token it obtains from the OIDC provider Authorization Server as the bearer token to the API behind Apigee.
-
Click Save.
-
-
In the Access Validation list, select the form of access validation that will be applied for non-web API clients, such as mobile applications.
-
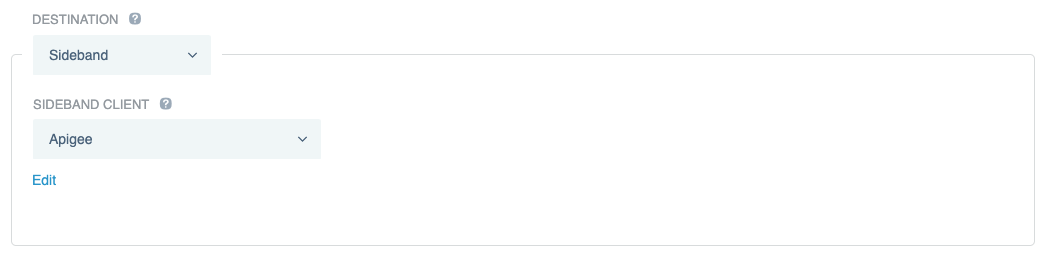
Configure Apigee as the application destination:
-
In the Destination list, select Sideband.
-
In the Sideband Client list, select the sideband client that you created earlier.
-
Click Save.
-