Configuring PingAuthorize Policy Editor to use PingFederate
Configure the PingAuthorize Policy Editor to use PingFederate for authentication.
Before you begin
Configure PingFederate to handle OpenID Connect requests as described in Configuring PingFederate for PingAuthorize.
About this task
Reconfigure a manually installed PingAuthorize Policy Editor to use PingFederate for authentication.
Steps
-
Add the certificate to the Java Trust Store.
If the certificate chain added to PingFederate uses an intermediate certificate authority that is not trusted by the default Java trust store, you must add the certificate. Use the following command (root permissions are usually required).
$JAVA_HOMEmust be defined as the installation location of the JVM on which the Policy Editor will run.keytool -import \ -file /path/to/IntermediateCA.cer \ -keystore $JAVA_HOME/jre/lib/security/cacerts \ -storepass changeit
-
Reconfigure PingAuthorize to point unauthenticated users to PingFederate.
-
Stop the application.
$ bin/stop-server The server was successfully stopped.shell -
Re-run
bin/setupto reconfigure the application. -
Select OpenID Connect to configure the Policy Editor.
[/opt/{pingauthorize}-PAP]$ bin/setup There is an existing configuration file at /config/configuration.yml. Overwrite? (yes / no) [no]: yes Detected valid license file in server root {pingauthorize}.lic {pingauthorize} Policy Editor ============================================ How would you like to configure the Policy Editor? 1) Quickstart (DEMO PURPOSES ONLY): This option configures the server with a form based authentication and generates a self-signed server certificate 2) OpenID Connect: This option configures the server to use an OpenID Connect provider such as PingFederate 3) Cancel the setup Enter option [1]:2On which port should the Policy Editor listen for HTTPS communications? [9443]: Enter the fully qualified host name or IP address that users' browsers will use to connect to this GUI [pap.example.com]: pap.example.com -
Ensure that the PingFederate discovery endpoint uses the public DNS name of the PingFederate server. In this example, the Policy Editor uses a self-signed SSL certificate.
Enter the port of the OpenID Connect provider [9031]: Enter the fully qualified host name or IP address of the OpenID Connect provider [pap.example.com]:
pf.example.comCertificate server options: 1) Generate self-signed certificate (recommended for testing purposes only) 2) Use an existing certificate located on a Java Keystore (JKS) 3) Use an existing certificate located on a PKCS12 keystore Enter option [1]: There already exists a keystore at /config/keystore.p12. Do you want to delete it? (yes / no) [no]:yes -
Follow the remaining prompts.
Setup Summary ======================================= Host Name: pap.example.com Server Port: 9443 Secure Access: Self-signed certificate Admin Port: 9444 Periodic Backups: Enabled Backup Schedule: 0 0 0 * * ? Command-line arguments that would set up this server non-interactively: setup oidc --pkcs12KeyStorePath config/keystore.p12 --licenseKeyFile {pingauthorize}.lic \ --oidcHostname pf.example.com --oidcPort 9031 --certNickname server-cert --backupSchedule '0 0 0 * * ?' \ --hostname pap.example.com --port 9443 --generateSelfSignedCertificate --adminPort 9444 What would you like to do? 1) Set up the server with the parameters above 2) Provide the setup parameters again 3) Cancel the setup Enter option [1]: Setup completed successfully Please configure the following values ============================================================================================= {pingauthorize} Server - Policy External Server Base URL: https://pap.example.com:9443 Shared Secret: 2222142a754f4838ad1e3dccb6e93940 Trust Manager Provider: Blind Trust PingFederate - OAuth Client Config Client ID: pingauthorizepolicyeditor CORS Allowed Origin: https://pap.example.com:9443 Redirect URL: https://pap.example.com:9443/idp-callback Please start the server by running bin/start-server -
Restart the application by running
bin/start-server.
-
-
Verify that you can log into the Policy Editor using OpenID Connect provided by PingFederate.
-
Go to the Policy Editor, for example, https://pap.example.com:9443. Your browser should be redirected into the OAuth flow.
-
Click Click to Sign In.
-
Sign on with your user name and password.
The sample configuration in this document creates an identity with the user name
user.20and passwordpassword. -
Once authenticated, PingFederate will prompt the user with the scopes associated with the OAuth client. Check all of them to continue.
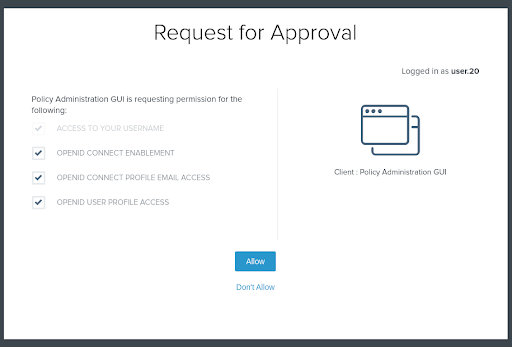
Result:
You are now authenticated and authorized to view the Policy Editor.
-