Rules and policies
Rules let you specify who can access your applications and resources, how and when they can do so, and what modifications can be made to the requested content. There are two different types of rules: access control rules and processing rules. Access control rules determine whether users can access a resource, and processing rules determine how requests are processed.
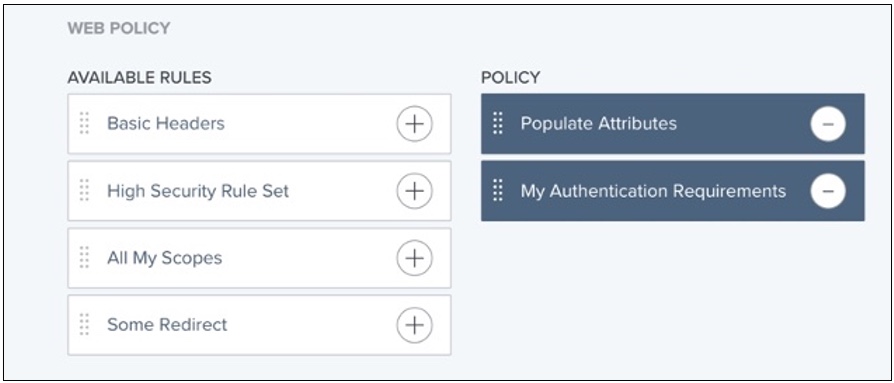
When you put rules together, they are called policies.
-
Application policies: Rules applied to the application as a whole. You can define Web rules and API rules for Web + API applications.
-
Resource policies: Rules applied to specific resources. Every application has at least one resource.
Rules can limit access based on information such as user attributes, client network range, time of day. You can combine rules to create rule sets, which are reusable and can be applied to many different resources and applications. Rule sets grant requests if any or all of the constituent rules are successful:
-
Any: An any rule set is evaluated from top to bottom and stops at the first rule that has its criteria met. If all rules fail, the request is denied.
-
All: An all rule set is evaluated from top to bottom and stops when it gets to the first rule that does not have its criteria met. If one rule fails, the request is denied.
Since rules within a rule set are evaluated from top to bottom, the order in which rules display in rule sets is important. In PingCentral, you can customize policies by dragging rules from the Available Rules list to the Policy list and changing the order to meet your needs.
For more information, see Rules in the PingAccess User Interface Reference Guide.