Troubleshooting the Apigee integration
Troubleshoot the most common issues with the Apigee gateway integration with PingAuthorize.
Troubleshooting API client HTTP 5xx errors
About this task
Apigee might return HTTP 502 when there is misconfiguration or miscommunication between the PingAuth Shared Flow for Apigee and PingAuthorize Server.
To address 5xx errors, make adjustments to the Load KVM Config policy assigned to PingAuth in Apigee X or the key value map that you created for the PingAuth Shared Flow in Apigee Edge or Apigee Private Cloud.
The PingAuth Shared Flow for Apigee logs warning messages to the Apigee error log when it encounters problems communicating with PingAuthorize. For more information, see Enable logging in Apigee.
Steps
-
Check the PingAuth Shared Flow
service_host_portvalue.If the Apigee
service_host_portvalue does not match your PingAuthorize server environment, the Apigee error log message might indicate that the plugin received an invalid response from the server.-
Confirm that the value entered for
service_host_portmatches the host name of your PingAuthorize server and the port of the HTTPS connection handler.You can find this port number on the Configuration page of the PingAuthorize administration console by going to System → Connection Handlers.
-
If necessary, update the
service_host_portvalue to match your PingAuthorize server.
-
-
Check the PingAuth Shared Flow shared secret.
If the shared secret doesn’t match the API gateway credential in PingAuthorize, the Apigee error log message might indicate that the plugin received an
HTTP 401error from PingAuthorize, which gets translated to a 5xx error and then sent to the API client.-
Confirm that the value of the shared_secret key that you created in Apigee matches the shared secret value that you created for PingAuthorize.
-
If necessary, on the Configuration page of the PingAuthorize administration console, go to Web Services and Applications → HTTP Servlet Extensions → Sideband API and update the value of the shared secret.
-
Copy the new value of the shared secret and update the value of the Apigee shared_secret key.
-
Troubleshooting API client HTTP 4xx errors
The Apigee API gateway might return a 4xx error to the API client if the API client’s request can’t be authenticated by the PingAuthorize sideband API endpoint.
To troubleshoot 4xx errors caused by authentication issues against the PingAuthorize sideband API, see Diagnostic and decision data.
Setting up error response handling in the target server
About this task
You should have an Apigee policy that handles errors returned by the target server.
If you don’t configure error handling using a policy, the API proxy goes into an error state in the <TargetEndpoint> response, and the normal API proxy flow won’t continue to the <ProxyEndpoint>.
Steps
-
Go to API Proxies → httpbin_bad_response → Develop and create a new ReturnGenericError policy of type AssignMessage. Configure the policy as desired.
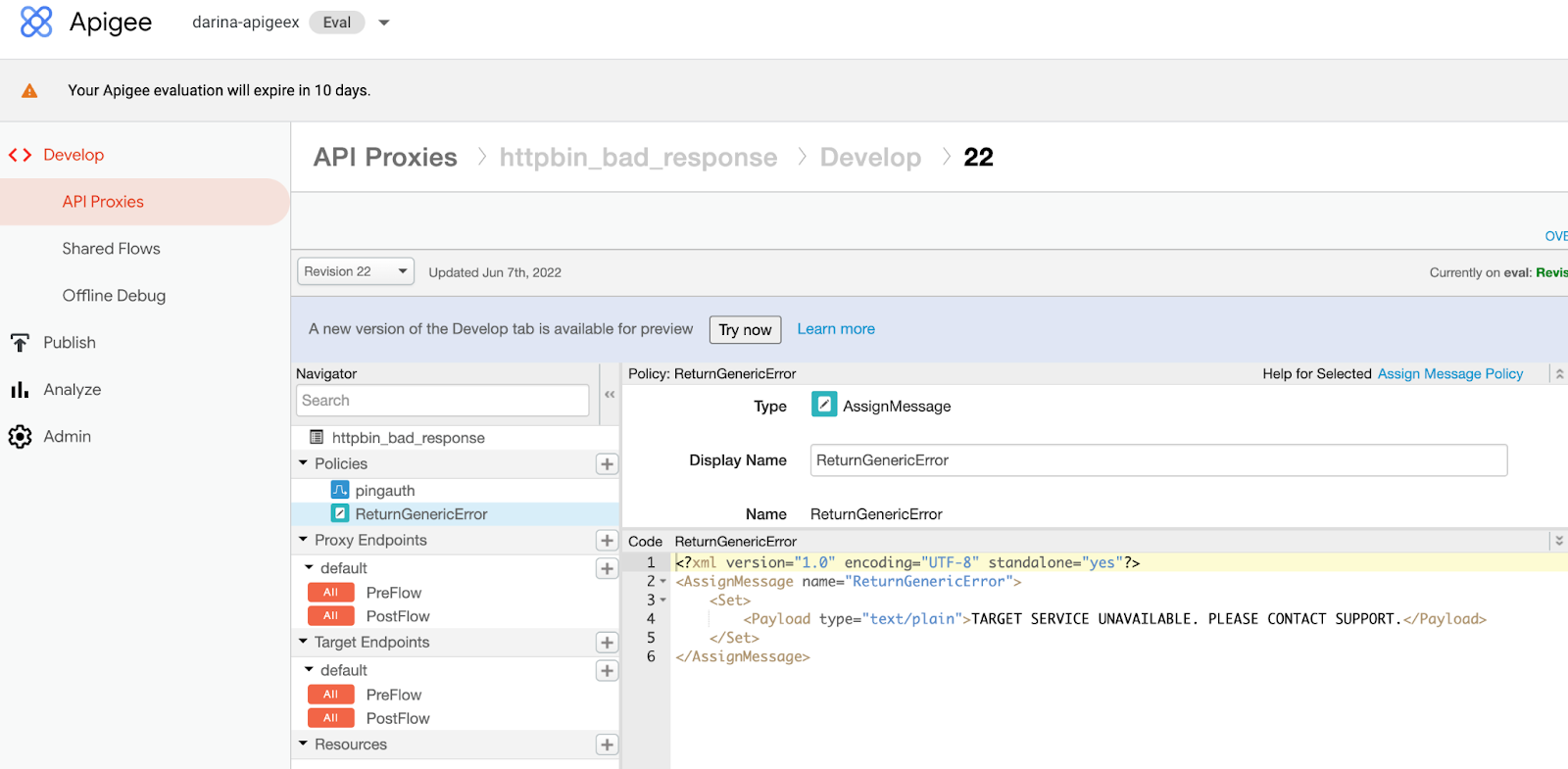
-
Select the PreFlow option in the Target Endpoints for your API proxy. Add the error policy you just created as a
<Step>in the<DefaultFaultRule>.There are multiple methods for adding the error handling policy.
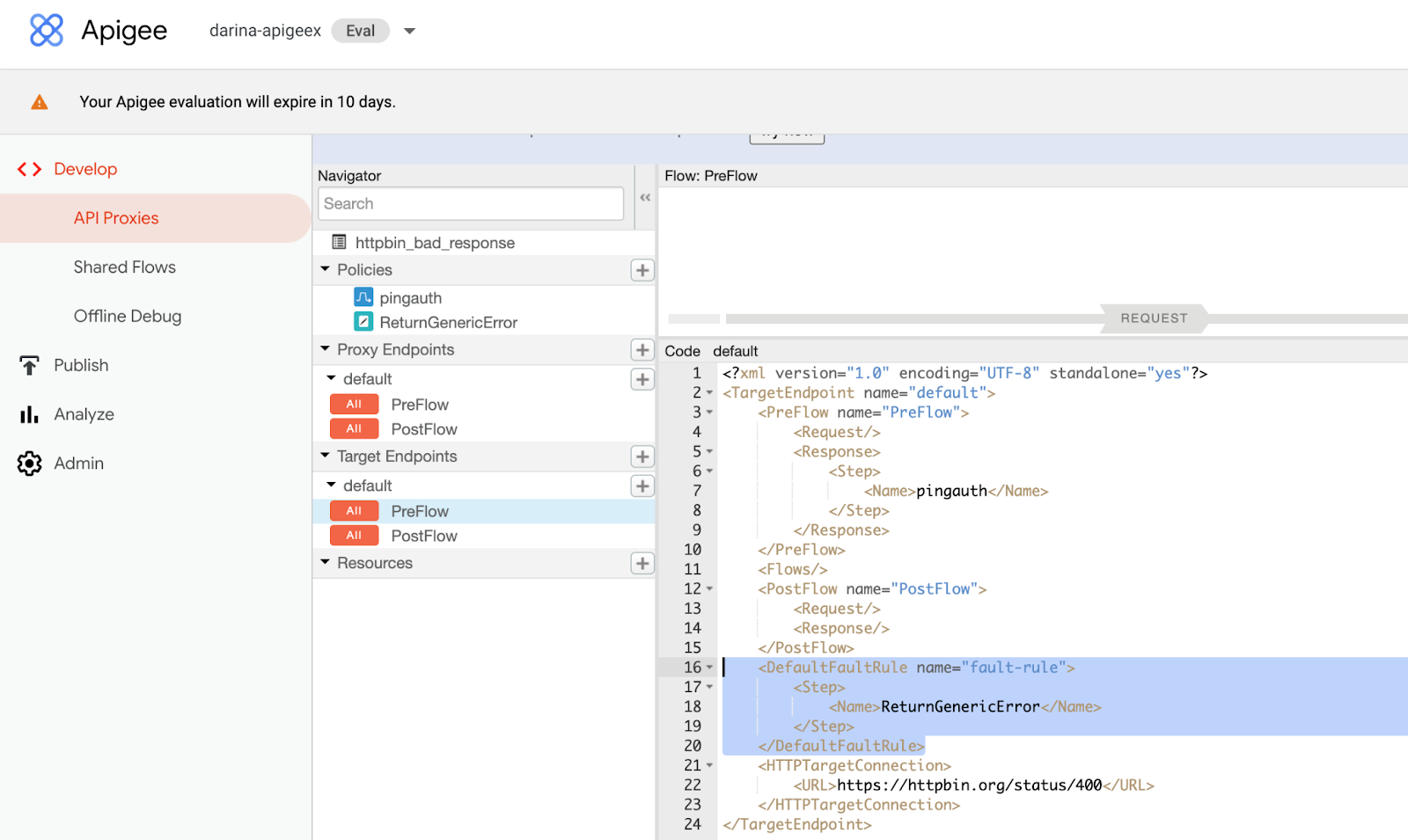
Enable logging in Apigee
To view error log messages, configure Apigee error logging. For more information, see the Apigee Trace documentation.
Apigee also provides debug logging for further troubleshooting. For more information, see Enabling debug logging in the Apigee documentation.