Policy Editor configuration with runtime environment variables
You do not have to hard-code values for policy configuration keys in an options file in the Policy Editor configuration. You can specify values for policy configuration keys at runtime using environment variables.
To use environment variables, specify a policy configuration key value in the options file using the ${variableName} notation, and then define the environment variable before starting the Policy Editor.
Example: Set policy information provider URI using an environment variable
This example takes the scenario in Define policy configuration keys in a development environment and modifies it to specify the Consent API base URI at runtime using an environment variable.
To specify the base URI using an environment variable:
-
Make a copy of the default options file.
$ cp config/options.yml my-options.yml -
Edit the new options file and define a policy configuration key in the core section called
ConsentBaseUri. Instead of hard-coding its value, specify a variable calledCONSENT_BASEURI.core: ConsentBaseUri: ${CONSENT_BASEURI} # Other options omitted for brevity... -
Stop the GUI server.
$ bin/stop-server -
Run
setupusing the--optionsFileargument. Customize all other options as appropriate for your needs.$ bin/setup demo \ --adminUsername admin \ --generateSelfSignedCertificate \ --decisionPointSharedSecret pingauthorize \ --hostname <pap-hostname> \ --port <pap-port> \ --adminPort <admin-port> \ --licenseKeyFile <path-to-license> \ --optionsFile my-options.yml -
Set the value of the
CONSENT_BASEURIenvironment variable and then start the server.$ export CONSENT_BASEURI=https://consent-us-east.example.com/consent/v1; bin/start-server
To set a different host name, redefine the CONSENT_BASEURI environment variable and restart the server.
$ bin/stop-server
$ export CONSENT_BASEURI=https://consent-us-west.example.com/consent/v1; bin/start-serverExample: Set trust store details using an environment variable
This example takes the scenario in Example: Configure a trust store for a policy information provider and modifies it to specify the trust store password at runtime using an environment variable.
Given a Java KeyStore (JKS) trust store named my-ca-truststore.jks with the password password123 and a trusted root certificate with the alias my-ca, create an options file with details about the trust store. Instead of hard-coding the trust store password, specify it as an environment variable.
To specify the password as an environment variable:
-
Make a copy of the default options file.
$ cp config/options.yml my-options.yml -
To edit the new options file and define the key store details, add an item in the
truststoressection. Specify the password value using the${ENVIRONMENT_VARIABLE}notation. Also, assign the password to a policy configuration key so it can be used in the Trust Framework.core: TrustStorePassword: ${TRUST_STORE_PASSWORD} truststores: - name: MyCATrustStore resource: /path/to/my-ca-truststore.jks # TRUST_STORE_PASSWORD is an environment variable password: ${TRUST_STORE_PASSWORD} # Other options omitted for brevity... -
Stop the Policy Editor.
$ bin/stop-server -
Run
setupusing the--optionsFileargument. Customize all other options as appropriate for your needs.$ bin/setup demo \ --adminUsername admin \ --generateSelfSignedCertificate \ --decisionPointSharedSecret pingauthorize \ --hostname <pap-hostname> \ --port <pap-port> \ --adminPort <admin-port> \ --licenseKeyFile <path-to-license> \ --optionsFile my-options.yml -
Set the value of the
TRUST_STORE_PASSWORDenvironment variable and start the server.$ export TRUST_STORE_PASSWORD=password123; bin/start-server
The policy configuration key that you defined can be used in the Trust Framework. You must first create an attribute to hold the policy configuration key value. Add an attribute with the following settings.
| Property | Value |
|---|---|
Name |
TrustStorePassword |
Resolver Type |
Configuration Key |
Resolver Value |
TrustStorePassword |
The following image shows the attribute in the Policy Editor.
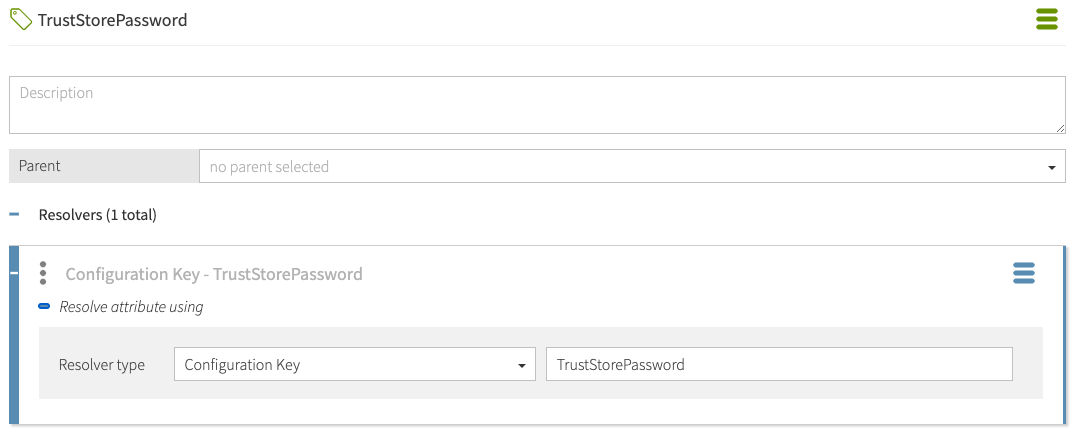
After you define the policy information provider in the Trust Framework, you can refer to the trust store password using the TrustStorePassword attribute.
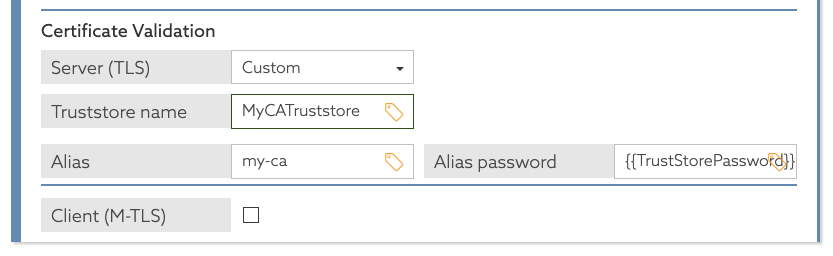
If you later use a trust store with a different password, you can redefine the TRUST_STORE_PASSWORD environment variable and restart the server.
$ bin/stop-server
$ export TRUST_STORE_PASSWORD=new-password; bin/start-server