Conditions
Use conditions in PingAuthorize attributes, rules, and policies to define authorization logic by comparing one thing to another. Conditions evaluate to either true or false.
You can compare requests, attributes, constant values, and regular expressions in conditions. Conditions can also serve as targets that define when a policy or rule applies to a decision request. For example, you can target a rule so that it applies when a payment amount is greater than or equal to a payment limit.
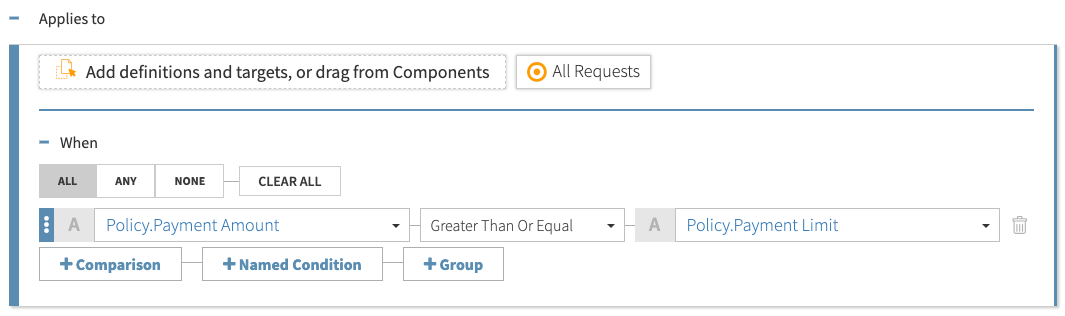
When you define a condition, on the left side, select an attribute or request type that represents unknown or variable information to be validated. On the right side, enter known or predefined criteria in the form of an attribute, request, or constant value. This keeps logical statements consistent regardless of what’s being compared. You can drag collapsed conditions to change their order, as needed.
You can add conditions directly to resolvers and rules or define them on the Components tab of the Library as reusable named conditions.
Condition comparators
You can use the following comparators in condition comparisons.
|
For simplicity, the table groups logical comparator pairs together, but you can only use one comparator at a time in a condition. |
| Comparator | Supported data types | Description | ||
|---|---|---|---|---|
Contains Does Not Contain |
Collection, String |
Checks whether a string or collection contains, or doesn’t contain, another string. Use this comparator when you know part of a value that you want to check.
|
||
Contains Claim Pair Does Not Contain Claim Pair |
String |
Add defense in depth by validating token claims as part of the authorization layer. Checks whether a JSON Web Token (JWT) contains a given claim pair. Encrypted tokens are not supported. To create a comparison:
To check a multivalued claim, create a comparator for each value you want to check. Multivalued |
||
Ends With Does Not End With |
String |
Checks whether a string ends with, or doesn’t end with, another string. |
||
Equals Does Not Equal |
Boolean, Collection, Date, Date Time, Duration, JSON, Number, Period, String, Time, XML, Zoned Date Time |
Checks whether two values are equal or not equal. |
||
Greater Than Less Than |
Boolean, Date, Date Time, Duration, Number, String, Time, Zoned Date Time |
Checks whether a value is greater than, or less than, another value. |
||
Greater Than Or Equal Less Than Or Equal |
Boolean, Date, Date Time, Duration, Number, String, Time, Zoned Date Time |
Checks whether a value is greater than or equal to, or less than or equal to, another value. |
||
Has Valid Signature For JWKS Has Invalid Signature For JWKS |
String, JSON |
Add defense in depth by validating tokens as part of the authorization layer. Checks the following for a JWT:
A valid token must have a verified signature and not be expired.
To create a comparison:
|
||
In CIDR Block Not In CIDR Block |
String |
Simplify adding network checks to support your zero trust policies. Verifies whether a user’s IP address is in, or not in, an IP subnet range. IPv4 and IPv6 addresses are supported. To create a comparison:
You must express the IP address range in Classless Inter-Domain Routing (CIDR) notation (the bitmask indicates the size of the routing prefix): IP address/bitmask For example, consider a condition that checks for IP addresses between 192.0.2.0 - 192.0.2.15. CIDR notation for this range is
|
||
Is In Is Not In |
Collection, String |
Checks whether a string or a collection is in, or not in, another collection. |
||
Regular Expression |
String |
Checks whether a string matches a regular expression. |
||
Starts With Does Not Start With |
String |
Checks whether a value starts with, or doesn’t start with, another value. |
| Comparator | Description | ||
|---|---|---|---|
Matches Does Not Match |
Checks whether the inbound request name starts with, or does not start with, the conditional request name.
|
||
Equals Does Not Equal |
Checks whether the inbound request equals, or does not equal, the conditional request. |