Provided statements
The PingAuthorize Policy Editor comes with preconfigured statement types that are also in PingAuthorize Server.
Policy writers can use the following provided statements out of the box, and PingAuthorize Server fulfills the statements as documented:
-
Add Filter
-
Combine SCIM Search Authorizations
-
Denied Reason
-
Exclude Attributes
-
Filter Response
-
Include Attributes
-
Modify Attributes
-
Modify Headers
-
Modify Query
-
Modify SCIM Patch
-
Regex Replace Attributes
To view the set of provided statement types within the Policy Editor, click Add Statement.
You can hover over a statement type to view its description.
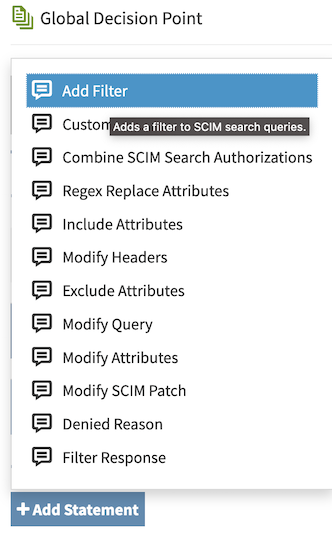
Selecting a statement type prepopulates the Description and Code fields and provides an example Payload value. Most users replace the example Payload value with one that is appropriate for their policy.
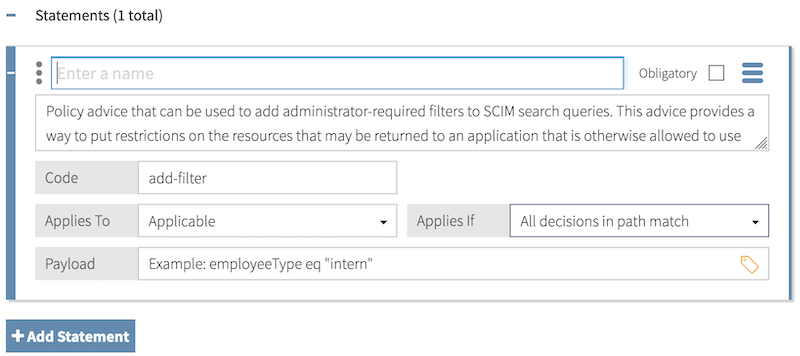
The following sections describe the statement types built into PingAuthorize Server.
Add Filter
Use add-filter to add administrator-required filters to System for Cross-domain Identity Management (SCIM) search queries.
| Description | Details |
|---|---|
Applicable to |
SCIM |
Additional information |
The Add Filter statement places restrictions on the resources returned to an application that can otherwise use SCIM search requests. The filters that the statement specifies are The payload for this statement is a string that represents a valid SCIM filter, which can contain multiple clauses separated by |
Combine SCIM Search Authorizations
Use combine-scim-search-authorizations to optimize policy processing for SCIM search responses.
| Description | Details |
|---|---|
Applicable to |
SCIM |
Additional information |
By default, SCIM search responses are authorized by generating multiple policy decision requests with the When you use this statement type, the current SCIM search result set is processed using an alternative authorization mode in which all search results are authorized by a single policy request that uses the This statement type does not use a payload. For more information about SCIM search handling, see About SCIM searches. |
Denied Reason
Use denied-reason to allow a policy writer to provide an error message that contains the reason for denying a request.
| Description | Details | ||
|---|---|---|---|
Applicable to |
DENY decisions
|
||
Additional information |
The payload for Denied Reason statements is a JSON object string with the following fields:
The following example shows a possible response for a request made with insufficient scope:
|
Exclude Attributes
Use exclude-attributes to specify the attributes to exclude from a JSON response.
| Description | Details |
|---|---|
Applicable to |
PERMIT decisions, although you cannot apply Exclude Attributes statements directly to a SCIM search. Also, do not use this statement type with SCIM modifies. Instead, use the Modify SCIM Patch statement type. |
Additional information |
The payload for this statement is a JSON array of strings. Each string is interpreted as a JSONPath into the response body of the request being authorized. Each JSONPath can select multiple attributes in the object. The portions of the response that a JSONPath selects are removed before sending the response to the client. The following example instructs PingAuthorize Server to remove the attributes
For more information about the processing of SCIM searches, see Filter Response. |
Filter Response
Use filter-response to direct PingAuthorize Server to invoke policy iteratively over each item of a JSON array contained within an API response.
| Description | Details | ||
|---|---|---|---|
Applicable to |
PERMIT decisions from the gateway, although you cannot apply Filter Response statements directly to a SCIM search. However, the SCIM service performs similar processing automatically when it handles a search result. For every candidate resource in a search result, the SCIM service makes a policy request for the resource with an |
||
Additional information |
When presented with a request to permit or deny a multivalued response body, Filter Response statements allow policies to require that a separate policy request be made to determine whether the client can access each individual resource that a JSON array returns. The following list identifies the fields of the JSON object that represents the payload for this statement.
On each policy request, if policy returns a For a response object that contains complex data, including arrays of arrays, this statement type can descend through the JSON content of the response.
|
Include Attributes
Use include-attributes to limit the attributes that a JSON response can return.
| Description | Details |
|---|---|
Applicable to |
PERMIT decisions, although you cannot apply Include Attributes statements directly to a SCIM search. Also, do not use this statement type with SCIM modifies. Instead, use the Modify SCIM Patch statement type. |
Additional information |
The payload for this statement is a JSON array of strings. Each string is interpreted as a JSONPath into the response body of the request being authorized. The response includes only the portions that one of the JSONPaths selects. When a single JSONPath represents multiple attributes, the response includes all of them. If the policy result returns multiple instances of Include Attributes statements, the response includes the union of all selected attributes. For more information about the processing of SCIM searches, see Filter Response. |
Modify Attributes
Use modify-attributes to modify the values of attributes in the JSON request or response.
| Description | Details |
|---|---|
Applicable to |
All, although you can’t apply the Modify Attributes statement directly to a SCIM search. Also, do not use this statement type for SCIM modify operations. Instead, use the Modify SCIM Patch statement type. |
Additional information |
The payload for this statement is a JSON object. Each key-value pair is interpreted as an attribute modification on the request or response body of the request being authorized. For each pair, the key is a JSONPath expression that selects the attribute to modify, and the value is the new value to use for the selected attribute. The value can be any valid JSON value, including a complex value such as an object or array. A Format: |
Modify Headers
Use modify-headers to modify the values of request headers before PingAuthorize sends them to the upstream server or to modify the values of response headers before PingAuthorize returns them to the client.
| Description | Details |
|---|---|
Applicable to |
All, although you cannot apply the Modify Headers statement directly to a SCIM search. |
Additional information |
The payload for this statement is a JSON object. The keys are the names of the headers to set, and the values are the new values of the headers. A value can be:
If the header already exists, PingAuthorize overwrites it. If the header does not exist, PingAuthorize adds it (unless the value is null). If a payload value is an array of strings:
|
Modify Query
Use modify-query to modify the query string of the request sent to the API server.
| Description | Details |
|---|---|
Applicable to |
All |
Additional information |
The payload for this statement is a JSON object. The keys are the names of the query parameters that must be modified, and the values are the new values of the parameters. A value can be one of the following options:
If the query parameter already exists on the request, it is overwritten. If the query parameter does not already exist, it is added. For example, consider the following request made to a proxied API: You can set a policy to limit certain groups of users to request only 20 users at a time. A payload of |
Modify SCIM Patch
Use modify-scim-patch to add operations to a SCIM patch in a modify request before it is submitted to the store adapter.
| Description | Details |
|---|---|
Applicable to |
SCIM requests with an action of modify |
Additional information |
The payload for this statement is either a JSON array or a JSON object. If the payload is an array, PingAuthorize treats it as a list of operations in the SCIM patch format to add to the end of the operations in the patch. For example, assume the modify has the following patch. Also, assume the statement payload is as follows. [
{"op": "add", "path": "name.first", "value": "John"},
{"op": "remove": "path": "name.last"}
]
Then the resulting request to the store adapter looks like this. If the payload is an object, PingAuthorize interprets it as a set of new replace operations to add to the end of the operations in the patch. In these replace operations, the keys from the object become the paths to modify, and the values from the object become the values for those paths. For example, assume the modify has the following patch. Also, assume the statement payload is as follows. Then the resulting request to the store adapter looks like this. |
Regex Replace Attributes
Use regex-replace-attributes to specify a regex to search for attributes in a request or response body and replace their values with a regex replacement string.
| Description | Details |
|---|---|
Applicable to |
All, although you cannot apply the Regex Replace Attributes statement directly to a SCIM search. |
Additional information |
The payload for this statement is either a JSON object or an array of JSON objects. Each object represents a single replacement operation and has up to four keys. The following list describes these keys:
PingAuthorize replaces any portion of the attribute value that matches the regular expression in the The regular expression and replacement string must be valid as described in the API documentation for the |
Example
For example, consider the following body.
{
"id":5,
"username":"jsmith",
"description":"Has a registered ID number of '123-45-6789'.",
"secrets":{
"description":"Has an SSN of '987-65-4321'."
}
}Also, consider the following payload.
{
"path":"$.secrets",
"regex":"\\\\d{3}-\\\\d{2}-(\\\\d{4})",
"replace":"XXX-XX-$1"
}Applying the statement produces the following body with a changed "secrets.description" value.
{
"id":5,
"username":"jsmith",
"description":"Has a registered ID number of '123-45-6789'.",
"secrets":{
"description":"Has an SSN of 'XXX-XX-4321'."
}
}