Release Notes
New features and improvements in PingAuthorize. Updated March 6, 2026.
PingAuthorize 9.3.0.7 (November 2024)
Fixed an issue with deployment package store requests
Fixed PAZ-16140
We fixed an issue that caused logs and monitors to make requests to deployment package stores more frequently than the configured polling interval, creating performance issues.
Fixed a Policy Editor sign-off issue
Fixed PAZ-16253
We fixed an issue that could prevent complete sign-off from the Policy Editor when using the Authorization Code with PKCE grant type.
PingAuthorize 9.3.0.6 (August 2024)
Added support for a new signature algorithm
New
We added support for Elliptic Curve Digital Signature Algorithm (ECDSA)-encoded signatures for JWT tokens when using the Has Valid Signature For JWKS and Has Invalid Signature For JWKS attribute comparators. Learn more in Conditions.
Fixed a Policy Editor UI issue
Fixed PAZ-12736
We fixed an issue where, in some cases, when selecting a scenario in entity testing or in the Test Suite with a large number of scenarios already defined, the Policy Editor UI would repeatedly flicker.
Fixed a PingAuthorize Server performance issue
Fixed PAZ-13013
We fixed an issue where, when using PingAuthorize Server’s API security gateway in embedded PDP mode, policy decision logging could cause a memory leak and negatively impact the performance of long-running server instances.
Fixed an issue with PIP keystore service calls
Fixed PAZ-12014
We fixed an issue where, when making a service call with a policy information provider key store for MTLS configured and the Server (TLS) option set to None or Default, the service would incorrectly return a Client TLS certificate is required error.
Fixed an issue with HTTP service log messages
Fixed PAZ-12454
We fixed an issue where the status field of an HTTP service log message would include a status message, such as OK, rather than a status code.
PingAuthorize 9.3.0.5 (March 2024)
Fixed a NullPointerException caused by an unconfigured alert handler
Fixed DS-47455
Fixed an issue where a NullPointerException was thrown when an alert or alarm was raised and one or more of the alert handlers weren’t configured. This most commonly happened when the server was being stopped.
Now, instead of throwing a NullPointerException, the server logs this message: Alert notification '<notification>' will not be processed by alert handler '<alert_handler>' since that alert handler does not have configuration.
PingAuthorize 9.3.0.2 (October 2023)
Fixed handling of empty array values for SCIM patch operations
Fixed PAZ-9435
SCIM replace operations with a value of [] now unassign the corresponding attribute. SCIM add operations with a value of [] are now ignored and no longer return an error.
PingAuthorize 9.3.0.0 (June 2023)
Exercise fine-grained control over Policy Editor changes using self-governance
New
Build self-governance policies to manage access to your Policy Editor entities and operations. This allows you to protect against unauthorized or accidental application policy changes. For more information, see Self-governance.
Simpler OAuth token handling for PIPs using HTTP services
New
To reduce configuration complexity and time to production when connecting to HTTP services that require OAuth authentication, configure the Client Credentials flow to handle tokens directly from a token endpoint. For more information, see HTTP services.
Copy Policy Editor entities for faster configuration
New
To build your authorization logic more quickly and accurately, you can make editable copies of many of your Policy Editor entities, including items in the Trust Framework, Policy Manager, and Library. For more information, see Copying Policy Editor entities.
New authorization comparators for IP subnet ranges
New
With the new In CIDR Block and Not In CIDR Block comparators, you can check whether a user’s IP address is in, or not in, a defined subnet range. These comparators make it easier to add network information checks to your zero trust policies. IPv4 and IPv6 addresses are supported. For more information, see Conditions.
Added a property that lets you control servlet information
New
Added the include-servlet-information-in-error-pages configuration property to give you control over whether servlet information gets printed on HTTP error pages or remains hidden (by default).
Apache Camel services have been removed
Info
To enhance overall security for PingAuthorize, Camel services have been removed from the default configuration. If your policies depend upon Camel, see Apache Camel availability for more information.
Validate token signatures and claims in policy
Improved
You can now validate JWT signatures and claims in the authorization layer, adding defense in depth and allowing you to build policy and rule logic around genuine tokens. Enhances support for PDP API use cases. For more information, see Conditions.
Better control over statements in decision outcomes
Improved
You now have more control over whether statements are included in decision outcomes and the way statements propagate through decision evaluations. This makes it easier to provide information in decision responses, such as reasons for both permit and deny decisions and risk evaluation feedback. For more information, see Statements.
Add parent resolvers to attributes more quickly
Improved
To reduce the number of clicks needed to add a parent resolver to a Trust Framework attribute, we added the Add Parent Resolver button.
Better targeting for regex-replace-attributes
Improved
We added the ability to target individual attributes using the regex-replace-attributes statement for a more precise modification of the payload. For more information, see Regex Replace Attributes.
Clarified WARN logs by migrating slow methods
Improved
We made WARN logging easier to interpret by changing the logging level for slow methods from WARN to DEBUG.
More resilient audit logging in the Policy Editor
Improved
We updated the default configuration for the decision-audit log to make audit logging more resilient.
Timeouts improved for replication enable and remove defunct server operations
Improved
Improved various timeouts for replication enable and remove defunct server operations to scale with the size of the topology. Smaller sized topologies should not be impacted by these changes.
Improved how a backup of the config backend is handled
Improved
If during a backup of the config backend, a file is deleted from the config/archived-configs directory, that deleted file will now be ignored instead of causing the backup to fail.
Added a missing field value in Policy Editor audit logging
Fixed PAZ-7026
We fixed an audit logging issue where ADMIN_POINT_AUDIT was not logging the operation field.
Fixed the Add Statement list display
Fixed PAZ-801
We fixed a display issue where the Add Statement drop-down list was running off of the page and couldn’t be fully accessed.
PingAuthorize 9.2.0.5 (March 2024)
Fixed SCIM case-sensitivity error
Fixed PAZ-8473
We fixed an issue where requests to create SCIM entries were not always observing the case-exact=false property, leading to incorrect case-sensitivity errors. Now, requests featuring this property will not be case-sensitive.
Fixed a NullPointerException caused by an unconfigured alert handler
Fixed DS-47455
We fixed an issue where a NullPointerException was thrown when an alert or alarm was raised, and one or more of the alert handlers were not configured. This most commonly happened when the server was being stopped.
Now, instead of throwing a NullPointerException, the server logs this message: Alert notification '<notification>' will not be processed by alert handler '<alert handler>' since that alert handler does not have configuration.
PingAuthorize 9.2.0.0 (December 2022)
Added the ability to define external Trust Framework attribute caches for development and production
New
Added support and configuration controls for Redis external caching of Trust Framework attribute values. See Configuring Trust Framework attribute caching for production and Configuring Trust Framework attribute caching for development.
Added the ability to configure custom OIDC scopes for the Policy Editor
New
You can now use the --scope option during Policy Editor setup to persistently override the default OpenID Connect (OIDC) scopes. For a one-time override, use the PING_SCOPE environment variable during Policy Editor startup. See the OIDC mode (custom scope) tab of Installing the PingAuthorize Policy Editor non-interactively for more details.
Added an HTTP servlet extension to support Prometheus monitoring
New
Added an HTTP servlet extension that allows the values of numeric monitor attributes to be published as metrics in a form that can be consumed by a Prometheus monitoring server. Learn more in Monitoring server metrics with Prometheus.
Docker support update for PingAuthorize PAP using PostgreSQL
Info
PingAuthorize policy administration point (PAP) Docker images based on product version 9.2.0.0 EA do not support PostgreSQL as a policy database backend due to schema changes. We have reintroduced PostgreSQL support for images based on version 9.2.0.0 GA or later. See Deploying PingAuthorize Policy Editor using Docker.
Updated Groovy version support
Info
Updated Groovy support from version 2.x to 3.x. This change might introduce some minor incompatibilities in Groovy script support. For example, import statements can no longer be split into multiple lines. Deployments making use of Groovy-scripted extensions should carefully test these extensions in a temporary standalone instance to verify compatibility and make any necessary changes before updating an existing instance.
Deprecated the OIDC implicit flow for the Policy Editor
Info
The OIDC Implicit flow implementation in the Policy Editor has been deprecated, because the OAuth Working Group no longer recommends its use. Implicit flow will be removed from a future version of PingAuthorize. You should transition to the Authorization Code with PKCE flow.
Qualified the Apigee OAuth flow
Info
You can use OAuth standard authentication as part of your Apigee integration with PingAuthorize. See Configuring Apigee for PingAuthorize integration for more information.
Deprecated the Swagger documentation for the Policy Editor REST APIs
Info
The Swagger pages documenting the REST APIs that manage the Policy Editor have been deprecated and will be removed from the product in a future release. We plan to re-implement the REST API documentation outside of the Policy Editor and make it available at a future date.
Introduced a character limit for Policy Editor entities
Info
Set a limit of 255 characters for the following names: branches, deployment packages, Trust Framework entities, and Policy Manager entities.
Improved the performance of the Policy Editor and PDP APIs
Improved
You should see performance improvements when using the Policy Editor or the various PingAuthorize PDP modes and APIs.
Made the JWKS endpoint response cacheable in the Policy Editor
Improved
You can now use the Authentication.oidcJwksCacheExpirySeconds setting in the options.yml file to control whether the server caches the JWKS endpoint response and for how long when using the Policy Editor in OIDC mode. See Configuring the JWKS endpoint cache.
Made the Policy Editor user data configurable
Improved
You can now change the claim that controls the user data displayed in the upper right of the Policy Editor. See Changing the default JWT claim for the OIDC user ID for more information.
Added support for generating digital signatures
Improved
Added support for generating digital signatures with a key obtained from an encryption settings definition. By default, the server’s preferred encryption settings definition is used to obtain the signing key, but you can use the signing-encryption-settings property in the crypto manager configuration to choose an alternative definition.
Previously, signatures were generated using a legacy key shared among servers in the topology, which could make it difficult to validate signatures outside of the topology. The legacy key will continue to be used in environments without any encryption settings definitions.
The replace-certificate tool re-prompts you for the path to a valid file containing certificates
Improved
Previously in an interactive PingAuthorize Server setup, when replace-certificate prompted you for the path to a file containing one or more certificates to be imported, it would exit with an error if the provided path represented a file that did not contain valid certificate information. It now re-prompts you for the path to a valid file after displaying the error message.
Fixed an issue with batch JSON PDP API requests
Fixed PAZ-5366
You should now be able to make batch JSON PDP API requests that contain only one decision request.
Fixed an issue with SpEL allow lists
Fixed PAZ-5424
Fixed an issue where SpEL allow lists in the configuration file were being ignored.
Fixed an issue with policy database value migration during an upgrade
Fixed PAZ-6154
Fixed a database upgrade issue where attributes with default values of null were not migrating and test assertion values became empty. This issue only affected customers that were running a pre-9.2-EA Policy Editor and upgraded to 9.2-EA.
Fixed an issue that prevented the Policy Editor from starting after upgrading the policy database schema
Fixed PAZ-6122
Fixed a rare issue where the tools missed applying some upgrade operations for the policy database, preventing the Policy Editor from starting. The setup and policy-db tools now validate the system time when performing schema element upgrades.
Fixed an issue with the Policy Editor UI when trying to drag multiple components onto a rule condition
Fixed PAZ-899
The Policy Editor UI no longer prevents you from dragging more than one Trust Framework component onto a policy rule when creating conditions.
Fixed an issue with missing Policy Editor entity changes
Fixed PAZ-5186
Fixed an issue where the Policy Editor could drop entity changes when performed concurrently with commits on the same branch.
Fixed an issue with policy creation using Applies To targets
Fixed PAZ-5344
Fixed an issue that stopped you from creating policies or policy sets with targets in the Applies To section.
Fixed an issue with replacing deleted deployment packages
Fixed PAZ-5574
Fixed an issue where the Deployment Manager wouldn’t let you replace the deployment package after deleting that deployment package from the Policy Editor.
Fixed an issue with Policy Editor logging
Fixed PAZ-6494
Fixed a regression from 9.2-EA where the lowered log level of HTTP PIP service call failures prevented them from appearing when using the default Policy Editor logging configuration.
Fixed a pagination issue with Test Suite entities in the Policy Editor
Fixed PAZ-6640
Fixed an issue where a large number of saved Test Suite entities were not being paged correctly by the Policy Editor backend, resulting in an HTTP 400 response.
Fixed an issue with portability of the configuration.yml file for the Policy Editor
Fixed PAZ-4448
Fixed an issue with the Policy Editor setup tool using an absolute file reference to the default H2 policy database when writing configuration.yml, which caused issues if the server instance root was moved to a different file system location. Now, the setup tool generates a file reference relative to the server instance root. You can still provide your own value through --dbConnectionString, or by modifying configuration.yml after it is generated.
Fixed a Policy Editor OIDC sign-on error
Fixed PAZ-5452
Fixed the following error in the OIDC implicit grant flow: Unable to complete background login with reason: invalid state parameter.
Fixed a Policy Editor issue with propagating the OIDC base URL to the configuration file
Fixed PAZ-6051
Fixed a Policy Editor issue for the bin/setup oidc command with the --oidcBaseUrl argument. Previously, when you provided a path without an ending forward slash, the command didn’t propagate your path value to configuration.yml.
Updated the dsconfig tool for applying authentication settings to a server group
Fixed DS-46313
Updated the dsconfig tool to ensure that it uses the correct authentication type when applying changes to all servers in a server group. Previously, it would always attempt to use simple authentication, even if the connection to the initial server was authenticated using a different mechanism.
Fixed a Kong-related issue when using set-headers with an array of strings
Fixed PAZ-5847
Fixed an issue where, when using the ping-auth plugin with Kong Gateway, sending the set-headers statement with an array of strings in the payload produced an error.
Fixed a Kong-related issue where using exclude-attributes or regex-replace-attributes produced invalid JSON
Fixed PAZ-5848
Fixed an issue where, when using the ping-auth plugin with Kong Gateway, sending either the exclude-attributes or regex-replace-attributes statements returned invalid JSON in the response.
Fixed a Kong-related issue where using set-attributes produced an upstream server timeout error
Fixed PAZ-5849
Fixed an issue where, when using the ping-auth plugin with Kong Gateway, sending the set-attributes statement returned the following message: An invalid response was received from the upstream server. The Kong error log also listed an upstream timed out error for the same response.
Fixed Kong-related modify-query statement failures
Fixed PAZ-5846
Fixed an issue where, when using the ping-auth plugin with Kong Gateway, sending the modify-query statement with a query in the payload but no set query parameters returned the following response: An unexpected error occurred. The Kong error log also listed a thread aborted runtime error.
PingAuthorize 9.1.0.5 (May 2024)
Fixed SCIM case-sensitivity error
Fixed PAZ-8473
We fixed an issue where requests to create SCIM entries were not always observing the case-exact=false property, leading to incorrect case-sensitivity errors. Now, requests featuring this property will not be case-sensitive.
Fixed a NullPointerException caused by an unconfigured alert handler
Fixed DS-47455
We fixed an issue where a NullPointerException was thrown when an alert or alarm was raised, and one or more of the alert handlers were not configured. This most commonly happened when the server was being stopped.
Now, instead of throwing a NullPointerException, the server logs this message: Alert notification '<notification>' will not be processed by alert handler '<alert handler>' since that alert handler does not have configuration.
PingAuthorize 9.1.0.0 (June 2022)
Updated commons-codec to address a security issue
Security DS-45898
Updated the commons-codec library to version 1.13 to address a security issue.
Updated Jackson Databind to address a security vulnerability
Security DS-45806
Updated Jackson Databind to 2.13.3 to address the CVE-2020-36518 security vulnerability.
Updated Google Guava to address a security vulnerability
Security DS-45903
Updated the Google Guava dependency in common libraries to address the CVE-2020-8908 security vulnerability.
Added conditional effects for policy rules
New
Rules now include conditional effects, allowing policy builders to write one rule with two possible effects. The effect produced depends on whether the effect condition evaluates to true or false.
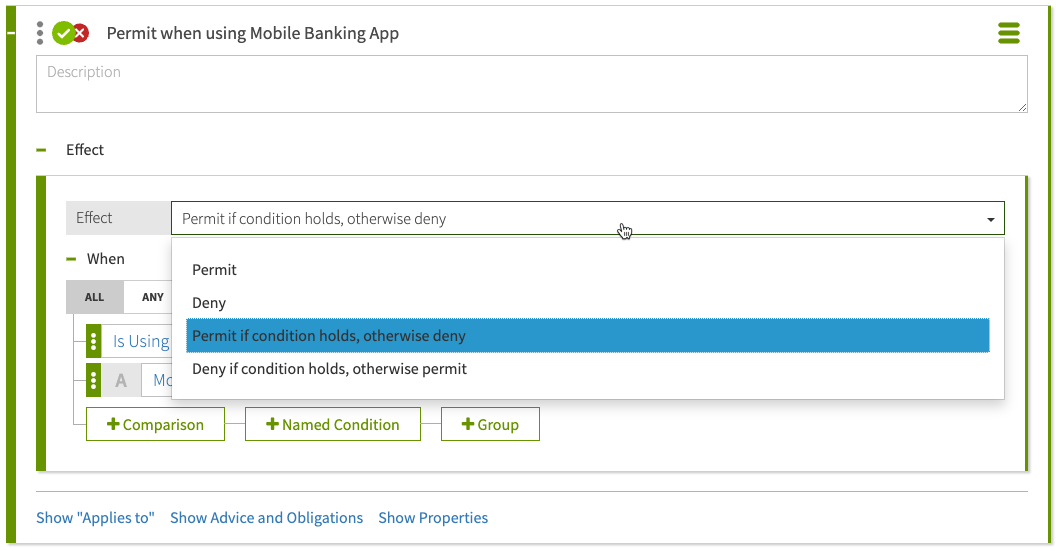
|
Previous rule conditions are now set as targeting conditions in the Applies To section. |
Added the ability to configure attribute logging for the Policy Decision Service
New
Added the option to configure logging for Trust Framework attributes. The Policy Decision Service logs the designated attributes when they are evaluated as part of a request. This option is only available in embedded mode.
Added the ability to sanitize error logging to protect sensitive data
New
Added the ability to sanitize error log messages as they are generated. This can help prevent sensitive information from being leaked through log messages, although the resulting log messages can potentially be less useful for troubleshooting purposes. Learn more in Log Sanitization.
Updated the administrative console browser support
Info
The administrative console now supports Microsoft Edge. Administrative console support for Microsoft Internet Explorer 11 has been deprecated.
Deprecated Apache Camel for PIP connections
Info
Using Apache Camel to connect policy information points (PIPs) to PingAuthorize has been deprecated, and the feature will be removed in a future release of the product. We recommend using HTTP services instead, where applicable.
Made it easier to present a custom SSL certificate to the Policy Editor
Improved
We added a new environment variable named KEYSTORE_PIN_FILE to the Policy Editor setup and start-server tools. This variable takes precedence over PING_KEYSTORE_PASSWORD when validating and presenting the server certificate.
Improved UI performance in the Policy Editor
Improved
The Policy Editor now supports API HTTP caching, which is enabled by default to improve UI performance. Disable this feature and restore the legacy behavior by providing the --disableApiHttpCache option to the setup tool. Alternatively, set the environment variable PING_ENABLE_API_HTTP_CACHE to false when running start-server to disable it for a particular server runtime instance.
Added a command-line configuration tool for PingAuthorize Docker containers
Improved
Added a docker-pre-start-config command-line tool for PingAuthorize Docker containers. Use the tool before the server is started to make configuration changes to the server that depend on the running container’s environment.
Added and updated PingAuthorize Server profile command-line tools
Improved
Added a --skipValidation argument for the manage-profile replace-profile command. This argument allows skipping the final server validation step when running on an offline server.
Added an --excludeSetupArguments argument for the manage-profile generate-profile command. This argument allows generating a server profile that does not include a setup-arguments.txt file.
Updated the setup and replace-profile subcommands to fail when a server profile includes an encryption-settings-db file in the profile’s server-root/pre-setup/ directory.
Enhanced advice logging
Improved
During advice processing, the File Based Error Log Publisher publishes additional helpful messages to the configured output file.
Removed the OIDC offline_access scope requirement for the Policy Editor
Fixed PAZ-3061
The Policy Editor no longer requires the offline_access scope when configured in OpenID Connect mode using the Authorization Code with PKCE grant type.
Fixed the Policy Editor issue rejecting bearer tokens with array-type aud claims
Fixed PAZ-1088
Fixed an issue that prevented the Policy Editor REST APIs from accepting a bearer token when the aud claim was an array of strings.
Enabled the Policy Editor to decode JWTs with underscores
Fixed PAZ-4325
The Policy Editor is now able to decode JWTs that contain underscore characters.
Enhanced HTTP performance
Fixed PAZ-3238, PAZ-2291
This release includes general HTTP performance improvements and bug fixes.
Fixed alert consistency for cleared alarms
Fixed DS-45578
Fixed issues where gauges could raise an alarm and create an alert, but not create an alert when that same alarm was later cleared, making it unclear when the reported condition had abated.
Updated the API gateway behavior for handling trailing zeros
Fixed PAZ-2705
When operating as an API gateway, PingAuthorize will no longer remove trailing zeros from numbers in non-SCIM response bodies and advice payloads.
Fixed the Policy Editor UI tab switching error
Fixed PAZ-2110
Fixed an issue where the Policy Editor threw an error when rapidly switching between Trust Framework tabs under slow network conditions.
Fixed the Policy Editor error that occurs when updating entities concurrently
Fixed PAZ-3667
Fixed an issue where concurrent updates to the same entities in the Policy Editor could sometimes produce an error.
Fixed an issue resolving JSONPath expressions that contain the keys() function
Fixed PAZ-4501
Fixed an issue where calling keys() in a JSONPath expression did not return the object’s keys.
Fixed the PIN retrieval issues with third-party passphrase providers
Fixed DS-45336
Fixed issues that prevented obtaining key and trust store PINs with the Amazon Secrets Manager, CyberArk Conjur, and HashiCorp Vault passphrase providers.
Fixed erroneous certificate expiration warnings
Fixed DS-41468
Fixed an issue that prevented the server from refreshing the monitor data used to detect and warn about an upcoming certificate expiration. This could cause the server to continue to warn about an expiring certificate even after that certificate had been replaced.
Fixed the PingAuthorize name and version in collect-support-data
Fixed DS-45280
The collect-support-data (CSD) tool now correctly displays the name and version of PingAuthorize.
Updated the incorrect version information for collect-support-data
Fixed DS-44481
The status tool now shows the current collect-support-data version.
Updated to LDAP SDK version 6.0.5
Fixed DS-45746
Updated to LDAP SDK for Java version 6.0.5 for bug fixes and new functionality.
Recovering from a failed setup on Windows
Issue DS-45941
The setup command might fail on Windows operating systems due to the presence of Bouncy Castle JAR files that begin with bc in the lib directory. The JAR files are mentioned in an error message similar to the following:
An unexpected error occurred while attempting to copy the non-FIPS Bouncy Castle jar file into the server's classpath: FileSystemException: lib\bcprov-jdk15to18-1.71.jar: The process cannot access the file because it is being used by another process.
A temporary workaround is to delete the JAR files that begin with bc from the lib directory before attempting to run setup again.
PingAuthorize 9.0.0.4 (January 2023)
Fixed erroneous certificate expiration warnings
Fixed DS-41468
Fixed an issue that prevented the server from refreshing the monitor data used to detect and warn about an upcoming certificate expiration. This could cause the server to continue to warn about an expiring certificate even after that certificate had been replaced.
PingAuthorize 9.0.0.2 (July 2022)
Updated to LDAP SDK version 6.0.5
Fixed DS-45746
Updated to LDAP SDK for Java version 6.0.5 for bug fixes and new functionality.
Fixed an incorrect SCIM POST error response
Fixed DS-45647
Fixed an issue where SCIM POST requests that violated a unique attribute constraint received an internal error instead of the expected SCIM error response.
PingAuthorize 9.0.0.0 (December 2021)
Added support for policy deployment from Microsoft Azure blob storage
New
The PingAuthorize Server can now consume deployment packages published to Microsoft Azure blob storage. This enables policy writers to deploy new policies to a central Azure deployment package store read by the PingAuthorize Server running in embedded mode. For more information, see Adding an Azure deployment package store, Configuring the Policy Editor to publish to a deployment package store, and Using the Deployment Manager.
Enabled configuration of the SpEL allow list in PDP mode
New
Now you can configure the SpEL allow list when the Policy Decision Service is running in embedded policy decision point (PDP) mode. An out-of-the-box PingAuthorize installation adds the following classes to the default allow list: String, Date, Random, UUID, Integer, Long, Double, Byte, Math, Boolean, LocalDate, DayOfWeek, Instant, ChronoUnit, and SimpleDateFormat. When configuring a policy deployment package containing SpEL expressions that reference additional Java classes, administrators must use dsconfig or the administrative console to add spel-allowlisted-class attributes to the Policy Decision Service. The class must also be available on the server classpath at server start. For non-standard Java classes, place the .jar file in the server lib folder.
Expanded Policy Editor database support to include PostgreSQL
New
The PingAuthorize Policy Editor can now persist its policies, Trust Framework, and versioning data in a PostgreSQL policy database instead of the default H2 file-based database. To initialize the database, use the instructions at https://github.com/pingidentity/pingauthorize-contrib/tree/main/sql/postgresql. To configure the Policy Editor for PostgreSQL, use the following setup options:
-
--dbConnectionString-
The JDBC connection string (for example,
"jdbc:postgresql://localhost:5432/policy_db")
-
-
--dbAppUsername-
The PostgreSQL user
-
-
--dbAppPassword-
The user’s password
-
Added support for the MuleSoft API Gateway in a sideband architecture
New
Now you can deploy PingAuthorize in a sideband configuration with the MuleSoft API Gateway. With a sideband deployment, your organization can quickly set up an environment for fine-grained, dynamic authorization that integrates with existing identity management infrastructure and requires minimal changes to your network configuration. For more information about our custom MuleSoft policy, see MuleSoft API gateway integration.
OpenID Connect (OIDC) Authorization Code with Proof Key for Code Exchange (PKCE)
New
Policy Editor setup in OpenID Connect (OIDC) authentication mode now uses the Authorization Code with Proof Key for Code Exchange (PKCE) grant type by default, instead of the implicit grant type. For information about configuring the Policy Editor in OIDC authentication mode, see Installing the PingAuthorize Policy Editor non-interactively.
Upgrading from early access to general availability
Info
If you are upgrading from PingAuthorize 9.0.0.0 Early Access to 9.0.0.0 General Availability, you must upgrade both the PingAuthorize Server and the Policy Editor before you use the Policy Decision Service in external mode. Upgrading only one component results in this error: Please upgrade to PingAuthorize Policy Editor version '9.0.0.0'.
Server profiles replace peer setup
Info
Peer server setup and clustered configuration have been removed from setup. To manage server configuration, use server profiles instead of peer setup. Server profiles support deployment best practices such as automation and Infrastructure-as-Code (IaC). For more information about server profiles, see Deployment automation and server profiles.
Upgrading from earlier versions of PingAuthorize
Info
For more considerations, see Upgrade considerations.
Added support for password storage schemes
Improved
Added support for password storage schemes that allow users to authenticate with passwords stored in the Amazon AWS Secrets Manager service, the Microsoft Azure Key Vault service, a CyberArk Conjur instance, or a HashiCorp Vault instance.
Added redaction capability for dsconfig
Improved
Added a global configuration property that can be used to indicate that the values of sensitive configuration properties should be redacted when constructing the dsconfig representation for a configuration change, given that these values might be included in the server’s configuration audit log or administrative alerts whenever a configuration change is applied. By default, the values of configuration properties that are defined as sensitive get obscured rather than redacted, which allows the change to be replayed without revealing the actual value of the property. However, it is now possible to redact such values rather than obscuring them, which provides stronger protection against exposing those values but might interfere with the ability to replay the configuration audit log if it contains changes involving sensitive properties.
Mirrored configuration change logging
Improved
Updated the server to record the original requester’s DN and IP address in access log and configuration audit log messages for mirrored configuration changes.
Added support for obtaining secrets from CyberArk Conjur
Improved
The Conjur cipher stream provider can use a retrieved secret to generate the encryption key used to protect the contents of the encryption settings database. The Conjur passphrase provider can be used in other cases where the server might need a clear-text secret, including PINs for accessing certificate key stores or credentials for authenticating to external services. The server can authenticate to Conjur with a username and password or an API key.
Added support for obtaining secrets from Azure Key Vault
Improved
The Azure Key Vault cipher stream provider can use a retrieved secret to generate the encryption key used to protect the contents of the encryption settings database. The Azure Key Vault passphrase provider can be used in other cases where the server might need a clear-text secret, including PINs for accessing certificate key stores or credentials for authenticating to external services.
Added a PKCS #11 cipher stream provider
Improved
Added a PKCS #11 cipher stream provider that can require access to a certificate in a PKCS #11 token to unlock the server’s encryption settings database. Only certificates with RSA key pairs can be used because JVMs do not currently provide adequate key wrapping support for elliptic curve key pairs.
Runtime server problem-status handling
Improved
When the Policy Decision Service is unable to handle requests due to misconfiguration or problems with the runtime environment, the PingAuthorize Server status is now DEGRADED instead of UNAVAILABLE. Orchestration systems like Kubernetes now remove such servers from pools instead of restarting them, allowing server administrators to investigate and correct the issue.
Added administrative console PIN support
Improved
The administrative console can now be configured to supply PINs to its trust stores through the oidc-trust-store-pin-passphrase-provider and trust-store-pin-passphrase-provider settings. This means trust store types that require passphrases (for example, PKCS12 or BCFKS) are now properly supported.
Administrative console file retrieval with SSO
Improved
The administrative console can now retrieve files created from collect-support-data or server-profile tasks when using single sign-on (SSO) to authenticate with the managed server.
Added file servlet support for OIDC and OAuth 2.0
Improved
Updated the file servlet to add support for token-based authentication using an OAuth 2.0 access token or an OpenID Connect ID token. The servlet previously only supported basic authentication.
manage-profile generate-profile argument validation
Improved
Improved includePath argument validation performed by the manage-profile generate-profile tool. The tool will only use relative paths that exist below the server root, and it previously silently ignored absolute paths or relative paths that referenced files outside of the server root. It will now exit with an error if the includePath argument is used to provide an absolute path or a path outside the server root. It will accept—but warn about—paths that reference files that do not exist.
Expanded ldap-diff capabilities
Improved
Made several improvements to the ldap-diff tool:
-
Added the ability to perform a byte-for-byte comparison of attribute values rather than using schema-based logical equivalence.
-
Added the ability to use a properties file to obtain default values for command-line arguments.
-
Improved the ability to use different TLS-related settings for the source and target servers.
-
Improved support for SASL authentication.
Added TLS protocol configuration to the crypto manager
Improved
Updated the crypto manager configuration to add properties for controlling the set of TLS protocols and cipher suites that will be used for outbound connections, as well as properties for controlling whether to enable TLS cipher suites that rely on the SHA-1 digest algorithm or the RSA key exchange algorithm.
Added JDK support
Improved
Added support for the use of JDKs obtained through Eclipse Foundation and BellSoft.
Added certificate management support
Improved
Added support for new extended operations that can be used to help manage the server’s listener and inter-server certificates. Updated the replace-certificate tool to add support for replacing and purging certificates in a remote instance, and to allow skipping validation for the new certificate chain.
Secret key loss when removing a server from the topology
Fixed DS-44591
Fixed an issue introduced in version 7.0.0.0 where secret keys under cn=Topology,cn=config could be lost when removing a server from the topology. When a server is removed via the dsreplication disable or remove-defunct-server tools, its secret keys will now be distributed among the remaining members of the topology. The keys from the rest of the topology will also be copied to the server being removed.
The cipher secret keys in the topology that are affected by this change are used by reversible password storage schemes (except for AES256, which uses the encryption settings database). If you are using a reversible password storage scheme other than AES256, prior to this fix, you could lose access to keys that had been used for reversible password encryption when removing servers from the topology.
|
Since this change only applies to the most recent version of |
Shutting down PingAuthorize Server with an invalid package store
Fixed DS-44770
An invalid deployment package store no longer prevents the PingAuthorize Server from shutting down.
remove-defunct-server attribute removal
Fixed DS-44793
Fixed an issue in which remove-defunct-server would remove attributes from config.ldif if they were identical apart from case.
Policy Editor batch scripts refer to non-existent Java files
Fixed DS-45105
The PingAuthorize Policy Editor start-server.bat and stop-server.bat scripts no longer output messages referring to non-existent java.properties or dsjavaproperties files.
JVM segmentation faults during start-server
Fixed DS-45124
Removed -XX:RefDiscoveryPolicy=1 from the default start-server Java arguments. In rare cases, this argument was related to segmentation faults in the Java virtual machine, especially when used with the G1 garbage collector.
Configuration keys and values in the Policy Editor Test Suite
Fixed PAZ-1481
The Policy Editor now uses policy configuration keys and values correctly in Test Suite tests. For details about configuring policy configuration keys, see Environment-specific Trust Framework attributes.
OIDC authentication to the Policy Editor for PingOne users with TLS 1.3 might limit functionality
Issue PAZ-5312
When PingOne users authenticate with OIDC to the Policy Editor, environments using OpenJDK versions older than 11.0.3 might run into an intermittent TLS 1.3 issue preventing them from loading test scenarios. The issue appears in the logs as com.symphonicsoft.authentication.OidcAuthenticator: Could not retrieve jwks information from '<ping-one-url>/as/jwks' and includes the following message: javax.net.ssl.SSLException: No PSK available. Unable to resume. This is an OpenJDK bug that has been fixed in version 11.0.3. To circumvent this issue, you can upgrade to OpenJDK 11.0.3 or newer. Disabling TLS 1.3 also prevents this issue.
Deployment package store detection
Issue DS-44549
If the configured deployment package store is not available when the PingAuthorize Server starts, it will not be able to detect when the store becomes available again. To ensure that the PingAuthorize Server begins using the deployment package store when the store is available again, you must restart the server or change the Policy Decision Service configuration.
Can’t use an existing persistent database with Docker volumes
Issue DS-44206
The pingdatagovernancepap and pingauthorizepap Docker images now run as unprivileged (non-root) users by default. If you have existing pingdatagovernancepap policy databases, configure the containers to run as root. For more information, see Deploying PingAuthorize Policy Editor using Docker.
Can’t persist the database in /opt/db with Docker volumes
Issue DS-44206
To persist a policy database in a Docker volume, create a new Docker volume with a mount target of /opt/out instead of /opt/db. For more information, see Deploying PingAuthorize Policy Editor using Docker.
Reconfiguring the Policy Editor in a Docker volume
Issue DS-44207
When you use the Policy Editor in a Docker volume, changing the configuration using an options.yml file also requires that you create an empty file such as /opt/out/instance/delete-after-setup before you restart pingauthorizepap. Consider this example:
-
You start the container with a command like the following:
$ docker run --network=<network_name> --name pap -p 8443:1443 \ --env-file ~/.pingidentity/config \ --volume /home/developer/pap/server-profile:/opt/in/ \ --env PING_OPTIONS_FILE=custom-options.yml \ --volume /home/developer/pap/Symphonic.mv.db:/opt/out/Symphonic.mv.db \ --env PING_H2_FILE=/opt/out/Symphonic \ pingidentity/pingauthorizepap:<TAG>This example command bind mounts a customized
options.ymlfile namedcustom-options.ymlto the server root using the server profile capability. The host systemserver-profilefolder must containinstance/custom-options.ymlfor this example to work correctly. The Docker image<TAG>is only a placeholder. See https://devops.pingidentity.com/reference/config/. -
You decide to change the configuration, so you edit the
custom-options.ymlfile. -
You create the empty file with a command like this:
docker exec -it pap /bin/sh -c "touch /opt/out/instance/delete-after-setup" -
With that file in place, you can now restart the Policy Editor with the following commands:
$ docker stop pap $ docker start --attach pap
Upgrading multi-server topologies from earlier versions
Issue DS-44165
Upgrading multi-server topologies that contain PingDataGovernance 6.x or 7.x to PingAuthorize is not supported.
Using the Periodic Stats Logger
Issue DS-43622
Published throughput and latency stats for SCIM, sideband, and gateway requests for the Periodic Stats Logger are not recorded until the requests are made and the logger is reset.
Policy Editor snapshot import error
Issue DS-41741
The Policy Editor produces an error when a user attempts to import an exported snapshot that contains references to named value processors.
Using the administrative console with Tomcat 9.0.31
Issue DS-41836
Several known issues can occur when you use the administrative console with Tomcat 9.0.31. You can resolve these issues by upgrading to Tomcat 9.0.33 or later.
Harmless failure message when stopping the PingAuthorize service
Issue DS-42365
If you use the create-systemd-script tool to create a forking systemd service, the service is stopped by the systemctl stop ping-authorize.service command. At that time, you can see the status using the systemctl status ping-authorize.service command. That status might contain an indication of failure: Active: failed (Result: exit-code). This error has to do with the way the service exits. It is harmless.