User profile availability in policies
In a policy, you might need to make a decision based on something about the requesting identity, meaning the access token subject or token owner. PingAuthorize can automatically look up the token owner’s attributes and provide them in the policy request using a token resource lookup method.
Token resource lookup methods
PingAuthorize provides built-in support for retrieving token owner data using paz_token_resource_lookup.adoc#section_jbj_xnk_1mb. Using a SCIM token resource lookup method requires a SCIM resource type to be configured, along with its prerequisite configuration objects. For information about SCIM configuration, such as SCIM resource types, store adapters, load-balancing algorithms, and LDAP external servers, see SCIM configuration basics.
For examples that show how to set up a token resource lookup method, see:
User profile data from access tokens
When processing an incoming HTTP request, PingAuthorize Server invokes any applicable access token validators to parse the request’s access token. If an access token validator successfully validates the access token, it then invokes any related token resource lookup methods. If a token resource lookup method succeeds in retrieving the attributes for the token owner, then PingAuthorize Server includes a TokenOwner attribute with the policy request. The contents of the TokenOwner attribute are a JSON object containing the user profile.
The exact structure of the TokenOwner attribute varies from deployment to deployment. When using a SCIM token resource lookup method, the contents of the TokenOwner attribute are a SCIM resource using the schema of the SCIM resource type configured for the token resource lookup method, exactly as if the resource had been retrieved via an HTTP GET without policy restrictions. For example, for a pass-through SCIM resource type for the LDAP inetOrgPerson object class, a TokenOwner value might look like the following.
{
"cn": [
"Mark E. Smith"
],
"employeeNumber": "1",
"entryDN": "uid=mark.e.smith,ou=people,dc=example,dc=com",
"entryUUID": "8ac3d8b5-4f17-33fa-a4b4-854599ed9a89",
"givenName": [
"Mark"
],
"id": "8ac3d8b5-4f17-33fa-a4b4-854599ed9a89",
"initials": [
"MES"
],
"l": [
"Manchester"
],
"mail": [
"mark.e.smith@example.com"
],
"meta": {
"location": "https://example.com/scim/v2/Users/8ac3d8b5-4f17-33fa-a4b4-854599ed9a89",
"resourceType": "Users"
},
"mobile": [
"+44 161 872 37676"
],
"modifyTimestamp": "2020-06-03T03:56:54.168Z",
"objectClass": [
"top",
"person",
"organizationalPerson",
"inetOrgPerson"
],
"schemas": [
"urn:pingidentity:schemas:store:2.0:UserStoreAdapter"
],
"sn": [
"Smith"
],
"uid": [
"mark.e.smith"
]
}The default Trust Framework includes a TokenOwner attribute as an empty JSON object. If you need to use a user profile attribute from a policy, add the attribute as a child of TokenOwner in the Trust Framework.
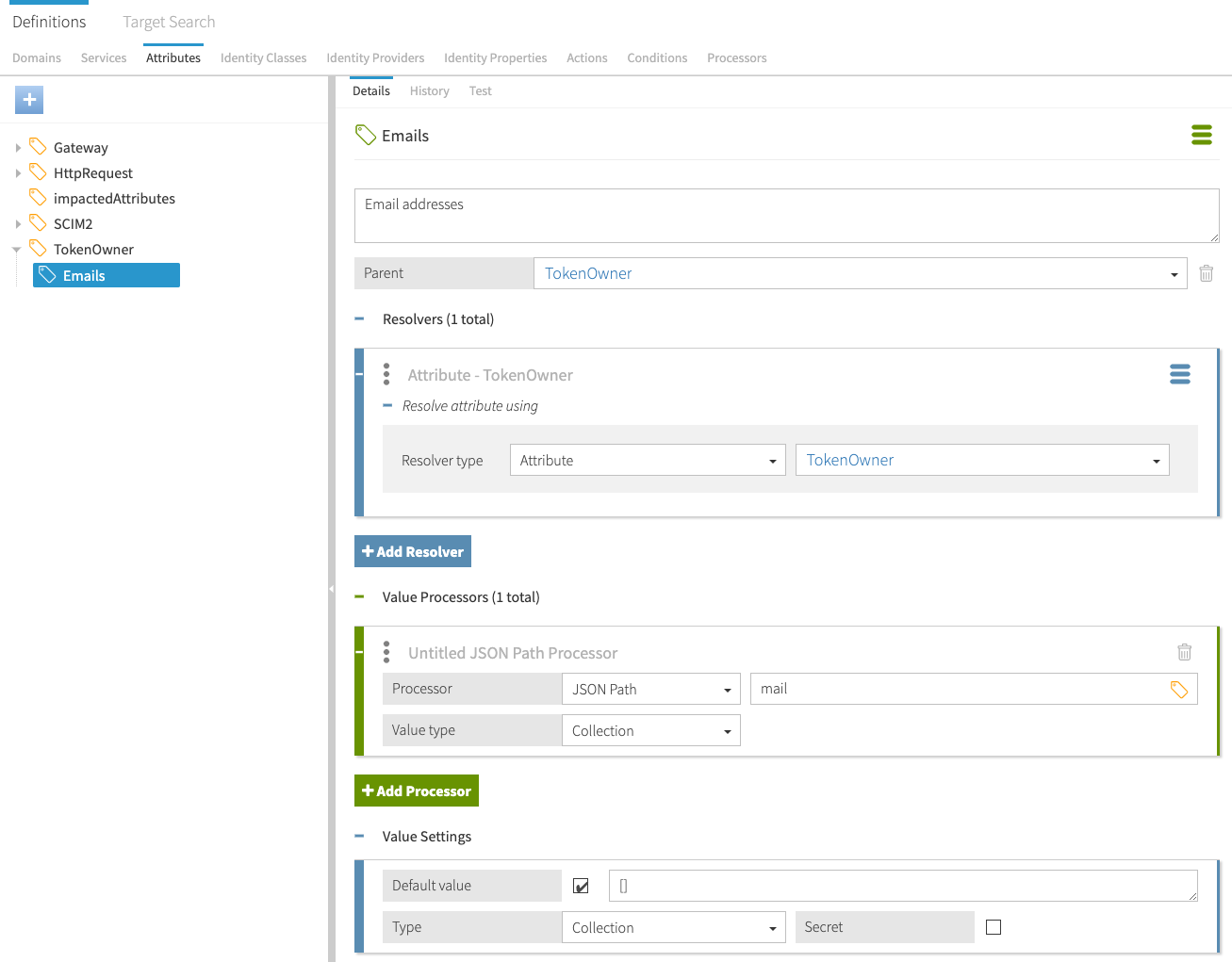
For example, the SCIM user profile shown above uses the mail attribute to store a user’s email addresses. To make policy decisions involving the token owner’s email address, you can add an Emails attribute under TokenOwner in the PingAuthorize Policy Editor, as shown in the following Trust Framework image.