PingAuthorize 9.1.0.0 (June 2022)
Updated commons-codec to address a security issue
Security DS-45898
Updated the commons-codec library to version 1.13 to address a security issue.
Updated Jackson Databind to address a security vulnerability
Security DS-45806
Updated Jackson Databind to 2.13.3 to address the CVE-2020-36518 security vulnerability.
Updated Google Guava to address a security vulnerability
Security DS-45903
Updated the Google Guava dependency in common libraries to address the CVE-2020-8908 security vulnerability.
Added conditional effects for policy rules
New
Rules now include conditional effects, allowing policy builders to write one rule with two possible effects. The effect produced depends on whether the effect condition evaluates to true or false.
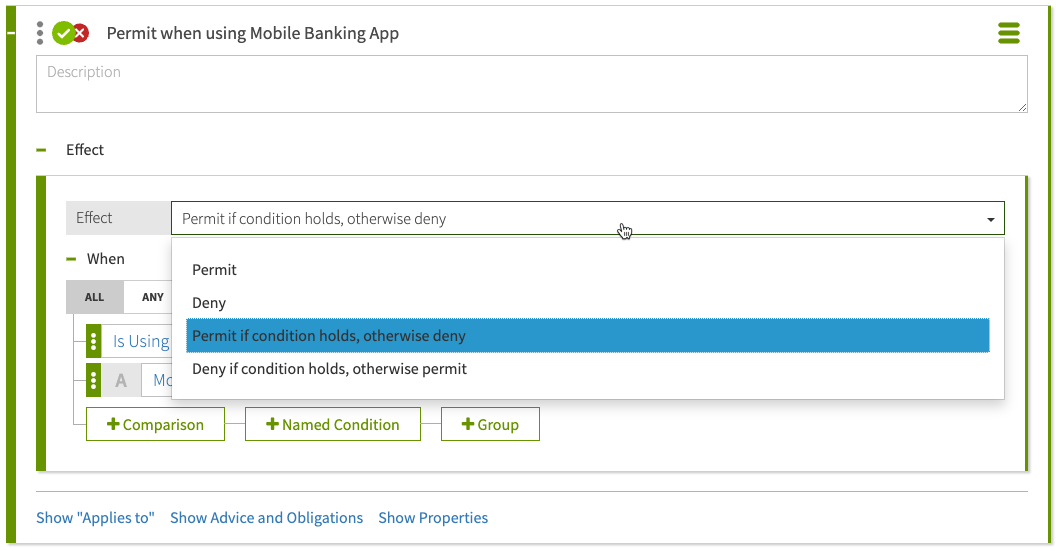
|
Previous rule conditions are now set as targeting conditions in the Applies To section. |
Added the ability to configure attribute logging for the Policy Decision Service
New
Added the option to configure logging for Trust Framework attributes. The Policy Decision Service logs the designated attributes when they are evaluated as part of a request. This option is only available in embedded mode.
Added the ability to sanitize error logging to protect sensitive data
New
Added the ability to sanitize error log messages as they are generated. This can help prevent sensitive information from being leaked through log messages, although the resulting log messages can potentially be less useful for troubleshooting purposes. Learn more in Log Sanitization.
Updated the administrative console browser support
Info
The administrative console now supports Microsoft Edge. Administrative console support for Microsoft Internet Explorer 11 has been deprecated.
Deprecated Apache Camel for PIP connections
Info
Using Apache Camel to connect policy information points (PIPs) to PingAuthorize has been deprecated, and the feature will be removed in a future release of the product. We recommend using HTTP services instead, where applicable.
Made it easier to present a custom SSL certificate to the Policy Editor
Improved
We added a new environment variable named KEYSTORE_PIN_FILE to the Policy Editor setup and start-server tools. This variable takes precedence over PING_KEYSTORE_PASSWORD when validating and presenting the server certificate.
Improved UI performance in the Policy Editor
Improved
The Policy Editor now supports API HTTP caching, which is enabled by default to improve UI performance. Disable this feature and restore the legacy behavior by providing the --disableApiHttpCache option to the setup tool. Alternatively, set the environment variable PING_ENABLE_API_HTTP_CACHE to false when running start-server to disable it for a particular server runtime instance.
Added a command-line configuration tool for PingAuthorize Docker containers
Improved
Added a docker-pre-start-config command-line tool for PingAuthorize Docker containers. Use the tool before the server is started to make configuration changes to the server that depend on the running container’s environment.
Added and updated PingAuthorize Server profile command-line tools
Improved
Added a --skipValidation argument for the manage-profile replace-profile command. This argument allows skipping the final server validation step when running on an offline server.
Added an --excludeSetupArguments argument for the manage-profile generate-profile command. This argument allows generating a server profile that does not include a setup-arguments.txt file.
Updated the setup and replace-profile subcommands to fail when a server profile includes an encryption-settings-db file in the profile’s server-root/pre-setup/ directory.
Enhanced advice logging
Improved
During advice processing, the File Based Error Log Publisher publishes additional helpful messages to the configured output file.
Removed the OIDC offline_access scope requirement for the Policy Editor
Fixed PAZ-3061
The Policy Editor no longer requires the offline_access scope when configured in OpenID Connect mode using the Authorization Code with PKCE grant type.
Fixed the Policy Editor issue rejecting bearer tokens with array-type aud claims
Fixed PAZ-1088
Fixed an issue that prevented the Policy Editor REST APIs from accepting a bearer token when the aud claim was an array of strings.
Enabled the Policy Editor to decode JWTs with underscores
Fixed PAZ-4325
The Policy Editor is now able to decode JWTs that contain underscore characters.
Enhanced HTTP performance
Fixed PAZ-3238, PAZ-2291
This release includes general HTTP performance improvements and bug fixes.
Fixed alert consistency for cleared alarms
Fixed DS-45578
Fixed issues where gauges could raise an alarm and create an alert, but not create an alert when that same alarm was later cleared, making it unclear when the reported condition had abated.
Updated the API gateway behavior for handling trailing zeros
Fixed PAZ-2705
When operating as an API gateway, PingAuthorize will no longer remove trailing zeros from numbers in non-SCIM response bodies and advice payloads.
Fixed the Policy Editor UI tab switching error
Fixed PAZ-2110
Fixed an issue where the Policy Editor threw an error when rapidly switching between Trust Framework tabs under slow network conditions.
Fixed the Policy Editor error that occurs when updating entities concurrently
Fixed PAZ-3667
Fixed an issue where concurrent updates to the same entities in the Policy Editor could sometimes produce an error.
Fixed an issue resolving JSONPath expressions that contain the keys() function
Fixed PAZ-4501
Fixed an issue where calling keys() in a JSONPath expression did not return the object’s keys.
Fixed the PIN retrieval issues with third-party passphrase providers
Fixed DS-45336
Fixed issues that prevented obtaining key and trust store PINs with the Amazon Secrets Manager, CyberArk Conjur, and HashiCorp Vault passphrase providers.
Fixed erroneous certificate expiration warnings
Fixed DS-41468
Fixed an issue that prevented the server from refreshing the monitor data used to detect and warn about an upcoming certificate expiration. This could cause the server to continue to warn about an expiring certificate even after that certificate had been replaced.
Fixed the PingAuthorize name and version in collect-support-data
Fixed DS-45280
The collect-support-data (CSD) tool now correctly displays the name and version of PingAuthorize.
Updated the incorrect version information for collect-support-data
Fixed DS-44481
The status tool now shows the current collect-support-data version.
Updated to LDAP SDK version 6.0.5
Fixed DS-45746
Updated to LDAP SDK for Java version 6.0.5 for bug fixes and new functionality.
Recovering from a failed setup on Windows
Issue DS-45941
The setup command might fail on Windows operating systems due to the presence of Bouncy Castle JAR files that begin with bc in the lib directory. The JAR files are mentioned in an error message similar to the following:
An unexpected error occurred while attempting to copy the non-FIPS Bouncy Castle jar file into the server's classpath: FileSystemException: lib\bcprov-jdk15to18-1.71.jar: The process cannot access the file because it is being used by another process.
A temporary workaround is to delete the JAR files that begin with bc from the lib directory before attempting to run setup again.