Introduction to PingCentral
Use PingCentral to add user authentication and authorization support to your applications, promote them to the appropriate development environments for testing, and monitor them throughout their life cycles.
PingCentral:
-
Makes it possible for you to apply security configurations to your applications without assistance from an administrator.
-
Allows you to promote these applications yourself, when you are ready, rather than submitting a request and waiting for someone else to promote them for you.
-
Provides a central monitoring location for greater visibility into applications across deployment life cycles.
-
Minimizes the risk of promoting applications with vulnerable security policies within your organization.
Using PingCentral does not require extensive training. However, for the best possible experience, become familiar with how the platform works before getting started.
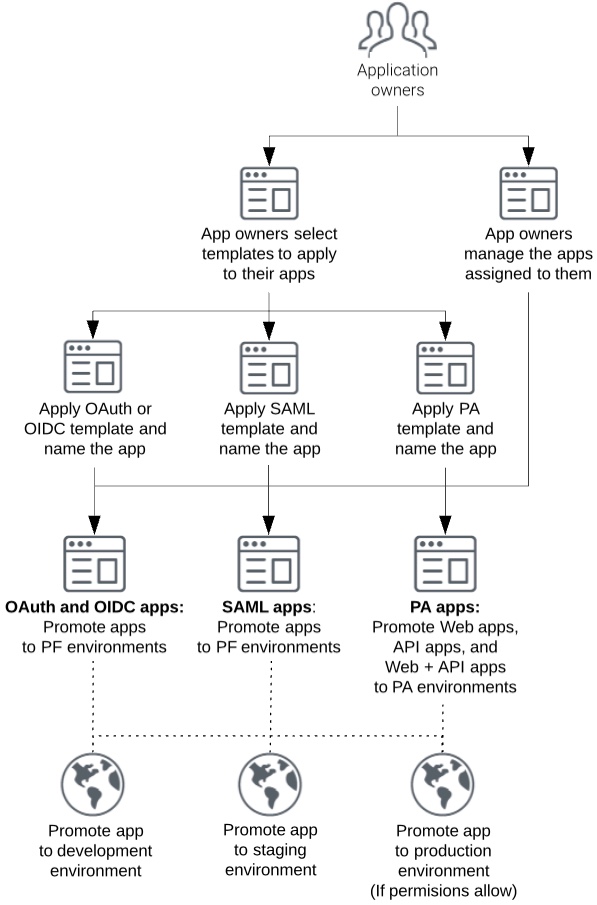
How PingCentral works
-
IAM Administrators create OAuth, OpenID Connect (OIDC), SAML, and PingAccess templates based on clients, connections, and application security configurations they think are worth replicating.
-
Administrators can also add clients, connections, and applications directly to PingCentral and assign owners to them.
-
You use SAML, OAuth, OIDC, and PingAccess templates to apply security configurations to your applications. A wizard guides you through the process of providing a name and description for each application you add to PingCentral. Another wizard guides you through the process of promoting your application to the target environment.
-
When you’re ready, promote applications to the appropriate development environments to test them and promote them directly to production environments if your permissions allow.