Restricting proxied authorization for specific users
Use the following example scenario with proxied users to restrict proxied authorization.
About this task
To illustrate how the proxied authorization operational attributes work, set up a simple example where two LDAP clients, uid=clientApp1 and uid=clientApp2, can freely proxy two administrator accounts, uid=admin1 and uid=admin2. Add the ds-auth-may-proxy-as-* and ds-auth-is-proxyable-* attributes to these entries to restrict how each account can use proxied authorization.
For example, the two client applications can continue to proxy the uid=admin1 account but the uid=admin2 account are no longer able to be used as a proxied entry.
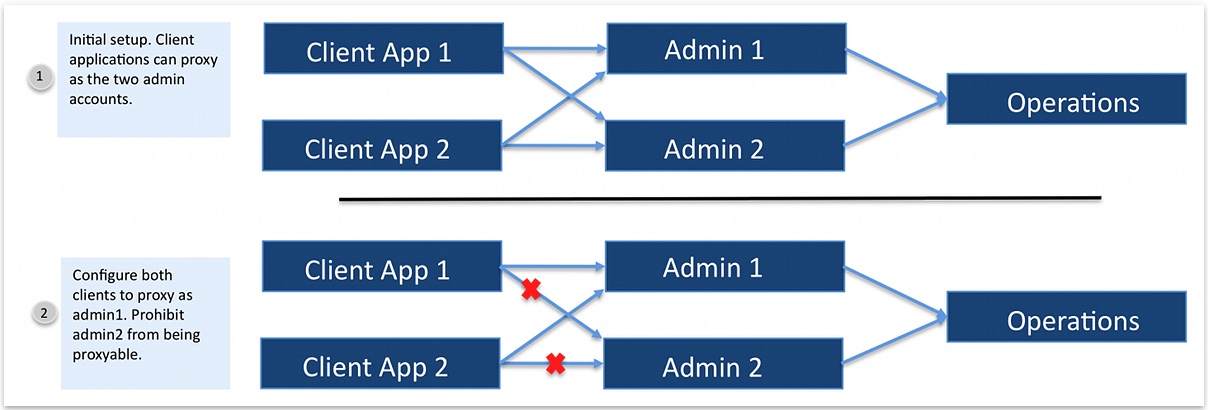
Steps
-
Set up two user entries,
uid=clientApp1anduid=clientApp2, with theproxied-authprivilege assigned to them.The user entries will proxy as the
uid=admin1anduid=admin2accounts to access theou=People,dc=example,dc=comsubtree.-
Open a text editor and create an LDIF file.
-
Add the file using the
ldapmodifytool.Example:
In this example,
…indicates that other attributes present in the entry are not included for readability purposes.dn: uid=clientApp1,ou=Applications,dc=example,dc=com objectClass: top ... ds-privilege-name: proxied-auth dn: uid=clientApp2,ou=Applications,dc=example,dc=com objectClass: top ... ds-privilege-name: proxied-auth
-
-
Assign the access control instruction (ACI) for each client application to the subtree,
ou=People,dc=example,dc=com.ACIs should be on one line of text. The following example displays ACIs over multiple lines for readability.
Example:
dn: ou=People,dc=example,dc=com aci: (version 3.0; acl "People Proxy Access"; allow(proxy) userdn="ldap:///uid=clientApp1,ou=Applications,dc=example,dc=com";) aci: (version 3.0; acl "People Proxy Access"; allow(proxy) userdn="ldap:///uid=clientApp2,ou=Applications,dc=example,dc=com";) -
Run a search for each entry.
Example:
In this example, assume that there are two admin accounts,
admin1andadmin2, that have full access rights to user attributes. You should be able to proxy as theuid=admin1anduid=admin2entries to access the subtree for both clients.$ bin/ldapsearch --port 1389 \ --bindDN "uid=clientApp1,ou=Applications,dc=example,dc=com" \ --bindPassword password \ --proxyAs "dn:uid=admin1,dc=example,dc=com" \ --baseDN ou=People,dc=example,dc=com \ "(objectclass=*)" $ bin/ldapsearch --port 1389 \ --bindDN "uid=clientApp2,ou=Applications,dc=example,dc=com" \ --bindPassword password \ --proxyAs "dn:uid=admin2,dc=example,dc=com" \ --baseDN ou=People,dc=example,dc=com \ "(objectclass=*)" -
Limit the proxied authorization capabilities for each client application.
In the following example, the
ds-auth-may-proxy-asattribute specifies thatuid=clientApp1can proxy as theuid=admin1entry.-
Open a text editor and create the following LDIF file.
-
Update the
uid=clientApp1entry to add theds-auth-may-proxy-asattribute.ds-auth-may-proxy-asis multi-valued. -
Save the file and add it using
ldapmodify.Example:
dn: uid=clientApp1,ou=Applications,dc=example,dc=com changetype: modify add: ds-auth-may-proxy-as ds-auth-may-proxy-as: uid=admin1,dc=example,dc=com
-
-
Repeat the previous step for the
uid=clientApp2entry, but specify theds-auth-may-proxy-as-urlattribute.The client entry can proxy as any distinguished name (DN) that matches the LDAP URL.
Example:
dn: uid=clientApp2,ou=Applications,dc=example,dc=com changetype: modify add: ds-auth-may-proxy-as-url ds-auth-may-proxy-as-url: ldap:///dc=example,dc=com??sub?(uid=admin*)
-
To illustrate the
ds-auth-proxyable-by-groupattribute, create a group of client applications that hasuid=clientApp1anduid=clientApp2as itsuniquemembers.Example:
This example sets up a static group using the
groupOfUniqueNamesobject class.dn: ou=Groups,dc=example,dc=com objectClass: top objectClass: organizationalunit ou: groups dn: cn=Client Applications,ou=Groups,dc=example,dc=com objectClass: top objectClass: groupOfUniqueNames cn: Client Applications ou: groups uniquemember: uid=clientApp1,ou=Applications,dc=example,dc=com uniquemember: uid=clientApp2,ou=Applications,dc=example,dc=com
-
Update the
uid=admin1entry to provide the DN that it can be proxied as.-
Open a text editor and create the following LDIF file.
-
Use the
ds-auth-is-proxyableto make theuid=admin1a required proxyable entry, meaning that it can only be accessed by some form of proxied authorization. -
Use the
ds-auth-is-proxyable-byattribute to specify each DN that can proxy asuid=admin1. -
Save the LDIF file and add it using
ldapmodify.Example:
dn: uid=admin1,dc=example,dc=com changetype: modify add: ds-auth-is-proxyable ds-auth-is-proxyable: required - add: ds-auth-is-proxyable-by ds-auth-is-proxyable-by: ou=clientApp1,ou=Applications,dc=example,dc=com ds-auth-is-proxyable-by: ou=clientApp2,ou=Applications,dc=example,dc=com - add: ds-auth-is-proxyable-by-group ds-auth-is-proxyable-by-group: cn=Client Applications,ou=Groups,dc=example,dc=com - add: ds-auth-is-proxyable-by-url ds-auth-is-proxyable-by-url: ldap:///ou=Applications,dc=example,dc=com??sub?(uid=clientApp*)
The example includes all three types of
ds-auth-is-proxable-by-*attributes as an illustration, but only one type of attribute is necessary if they all target the same entries.
-
-
Prohibit proxying for the
uid=admin2entry.-
Open a text editor and create the following LDIF file.
-
Set the
ds-auth-is-proxyableattribute toprohibited. -
Save the LDIF file and add it using
ldapmodify.Example:
dn: uid=admin2,dc=example,dc=com changetype: modify add: ds-auth-is-proxyable ds-auth-is-proxyable: prohibited
-
-
Run a search using the proxied account.
-
To return a successful operation, run a search with
uid=clientApp1oruid=clientApp2that proxies asuid=admin1. -
To return an unsuccessful operation, run a search for
uid=clientApp1that proxies asuid=admin2.Example:
$ bin/ldapsearch --port 1389 \ --bindDN "uid=clientApp1,ou=Applications,dc=example,dc=com" \ --bindPassword password \ --proxyAs "dn:uid=admin2,dc=example,dc=com" \ --baseDN ou=People,dc=example,dc=com \ "(objectclass=*)"Result:
The operation is unsuccessful because
uid=admin2does not match the list of potential entries that can be proxied. Theds-auth-may-proxy-as-*attributes specify that the client can only proxy asuid=admin1.One of the operational attributes (ds-auth-may-proxy-as, ds-auth-may-proxy-as-group, ds-auth-may-proxy-as-url) in user entry 'uid=clientApp1,ou=Applications,dc=example,dc=com' does not allow that user to be proxied as user 'uid=admin2,dc=example,dc=com' Result Code: 123 (Authorization Denied) Diagnostic Message: One of the operational attributes (ds-auth-may-proxy-as, ds-auth-may-proxy-as-group, ds-auth-may-proxy-as-url) in user entry 'uid=clientApp1,ou=Applications,dc=example,dc=com' does not allow that user to be proxied as user 'uid=admin2,dc=example,dc=com'
-
-
Run another search using
uid=clientApp2, which attempts to proxy asuid=admin2.Example:
$ bin/ldapsearch --port 1389 \ --bindDN "uid=clientApp2,ou=Applications,dc=example,dc=com" \ --bindPassword password \ --proxyAs "dn:uid=admin2,dc=example,dc=com" \ --baseDN ou=People,dc=example,dc=com \ "(objectclass=*)"Result:
The operation is unsuccessful because the
ds-auth-is-proxyable:prohibitedoperational attribute states thatuid=admin2is not available for proxied authorization.The 'ds-auth-is-proxyable' operational attribute in user entry 'uid=admin2,dc=example,dc=com' indicates that user may not be accessed via proxied authorization Result Code: 123 (Authorization Denied) Diagnostic Message: The 'ds-auth-is-proxyable' operational attribute in user entry 'uid=admin2,dc=example,dc=com' indicates that user may not be accessed via proxied authorization