Synchronize with a SCIM sync destination overview
The System for Cross-domain Identity Management (SCIM) 1.1 protocol is designed to make managing user identity in cloud-based applications and services easier. SCIM enables provisioning identities, groups, and passwords to, from, and between clouds. PingDataSync can be configured to synchronize with SCIM service providers.
|
Both the PingDirectory server and the PingDirectoryProxy server can be configured to be SCIM servers using the SCIM HTTP Servlet Extension. |
PingDataSync is LDAP-centric and operates on Lightweight Directory Access Protocol (LDAP) attributes. The SCIM sync destination server component acts as a translation layer between a SCIM service provider’s schema and an LDAP representation of the entries. While PingDataSync is LDAP-centric and typically at least one endpoint is an LDAP Directory server, this is not a strict requirement. For example, a Java database connectivity (JDBC) to SCIM sync pipe can be configured.
PingDataSync contains sync classes that define how source and destination entries are correlated. The SCIM sync destination contains its own mapping layer, based on scimresources.xml that maps an LDAP schema to and from SCIM.
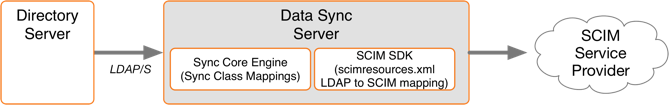
|
PingDataSync can use SCIM only as a sync destination. There is no mechanism in the SCIM protocol for detecting changes, so it cannot be used as a Sync Source. |
SCIM destination configuration objects
The SCIMSyncDestination object defines a SCIM 1.1 service provider Sync Pipe destination that is accessible over HTTP through the SCIM protocol. It is configured with the following properties:
-
server– Specifies the names of the SCIM External Servers that are used as the destination of synchronization. -
resource-mapping-file– Specifies the path to thescim-resources.xmlfile, a configuration file that defines the SCIM schema and maps it to the LDAP schema. This file is located in<server_root>/config/scim-resources.xmlby default, and it can be customized to define and expose deployment-specific resources. -
rename-policy– Specifies how to handle the rename of a SCIM resource.
The SCIM Sync Destination object is based on the SCIM SDK. Before configuring a SCIM destination, review the following documents on the Simple Cloud web site:
-
SCIM Core Schema
-
SCIM REST API
Considerations for synchronizing to a SCIM destination
When configuring an LDAP to SCIM Sync Pipe, consider the following:
- Use
scim-resources.xmlfor attribute and DN mappings -
There are two layers of mapping: once at the Sync Class level and again at the SCIM Sync Destination level in the
scim-resources.xmlfile. To reduce complexity, do all possible mappings in thescim-resources.xmlfile. - Avoid groups unless the SCIM ID is DN based
-
Group synchronization is supported if the SCIM ID is based on the distinguished name (DN). If the SCIM ID is not the DN itself, it must be one of the components of the RDN, meaning that the DNs of group members must contain the necessary attribute.
- SCIM modifies entries using PUT
-
The SCIM Sync Destination modifies entries using the full HTTP PUT method. For every modify, SCIM replaces the entire resource with the updated resource. For information about the implications of this on password updates, see Password considerations with SCIM.
Rename a SCIM resource
The SCIM 1.1 protocol does not support changes that require the SCIM resource to be renamed, such as a MODDN operation. Instead, when a change is detected to an attribute value that is used as part of the SCIM ID attribute, PingDataSync handles it in one of the following ways:
-
Deletes the specified SCIM resource and then adds the new resource with the new SCIM ID.
-
Adds the new resource with the new SCIM ID and then deletes the old resource.
-
Skips the rename portion of the change. If renames are expected on the source endpoint, a careful set of destination-correlation attributes should be chosen so that the destination can still be found after it is renamed on the source.
Configure this by setting the rename-policy property of the SCIM sync destination.
Password considerations with SCIM
Because the SCIM sync destination modifies entries using a full PUT method, special considerations need to be made for password attributes.
A Ping Identity SCIM server allows password attributes to be omitted from a change when they have not been modified by an operation. This prevents passwords from inadvertently being overwritten during the PUT operation, which does not include the password attribute. Ideally, other SCIM service providers will not wipe a password because a PUT request does not contain it. Check with the SCIM vendor to confirm this behavior before starting a SCIM sync pipe.