Identifying inbound provisioning attributes for LDAP
When configuring System for Cross-domain Identity Management (SCIM) inbound provisioning, you must identity the attributes you want to provision.
About this task
You can select the datastore attributes you want to provision on the Attributes tab.
|
This tab appears only if you are configuring an LDAP user store for provisioning. |
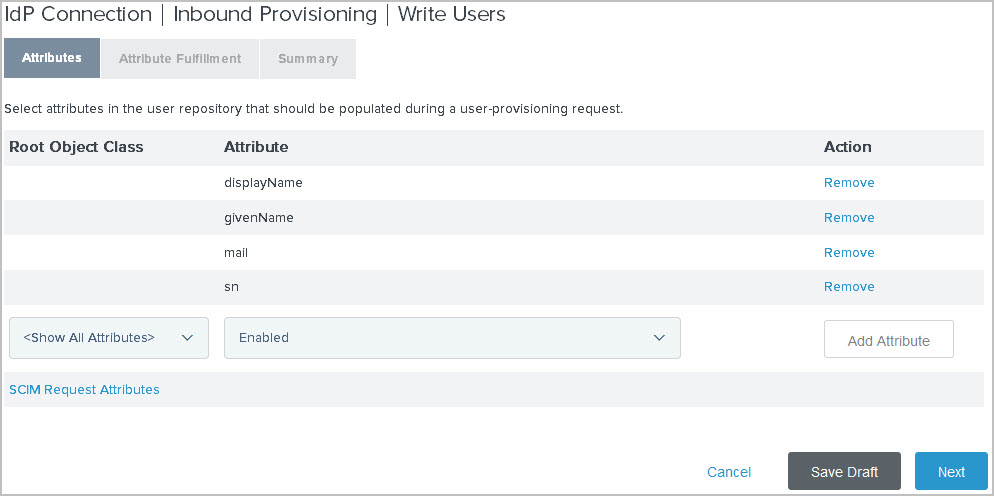
The following attributes are managed internally by PingFederate and do not require mapping:
-
objectClass -
unicodePwd -
objectGUID -
userAccountControl
You can override the internal management of objectClass and unicodePwd by selecting these attributes and mapping them to SCIM attributes on the Attribute Fulfillment tab. In this case, the values you supply are used. The objectGUID and userAccountControl attributes cannot be overridden and are ignored if selected.
Steps
-
Select a root object class and an attribute from the lists, then click Add Attribute.
Do not add
cnas one of the attributes.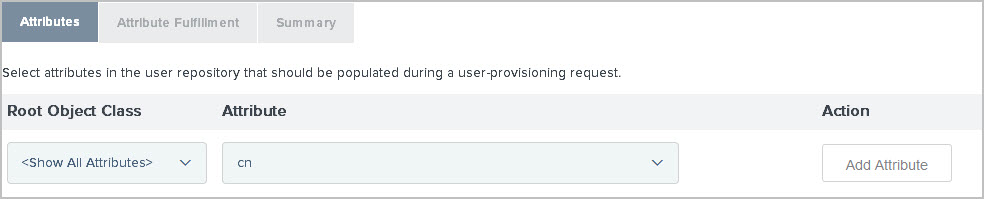
-
Repeat the previous step for each attribute requiring provisioning.