SSO—Browser-Artifact
In this scenario, the identity provider (IdP) sends a SAML artifact to the service provider (SP) through either HTTP POST or a redirect. The SP uses the artifact to obtain the associated SAML response from the IdP.
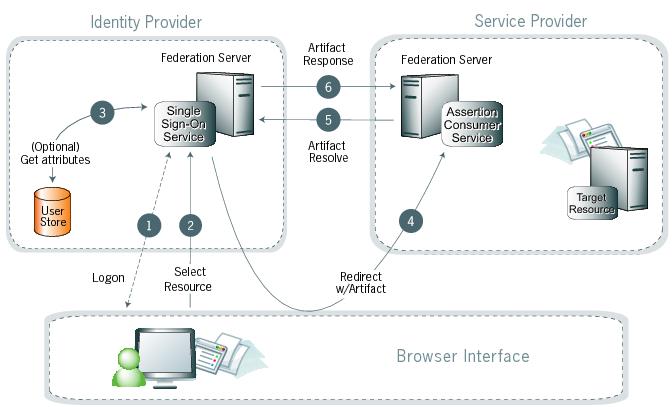
Processing steps
-
A user logs on to the IdP.
If a user is not logged on for some reason, the IdP challenges them to do so at step 2.
-
The user clicks a link or otherwise requests access to a protected SP resource.
-
Optionally, the IdP retrieves attributes from the user datastore.
-
The IdP federation server generates an assertion, creates an artifact, and sends an HTTP redirect containing the artifact through the browser to the SP’s Assertion Consumer Service (ACS).
-
The ACS extracts the Source ID from the SAML artifact and sends an artifact-resolve message to the identity federation server’s Artifact Resolution Service (ARS).
-
The ARS sends a SAML artifact response message containing the previously-generated assertion.
-
(Not shown) If the IdP returns a valid SAML assertion to the SP, a session is established on the SP and the browser is redirected to the target resource.