Gateway deployment
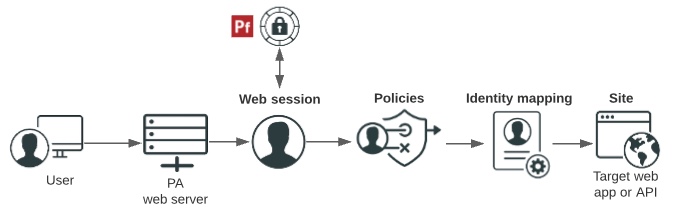
This diagram shows how users are authenticated, and how access policies and identity mappings are applied to requests to access applications or APIs with a gateway deployment.
-
Users enter a URL that consists of a unique virtual host and context root.
-
Virtual host: The public-facing host name and host port. For example,
den.ping.com:8443.A wildcard (
*) can be used either to define either any host (*:8443, for example) or any host within a domain (*.ping.com, for example). If a request matches more than one virtual host, the most specific match is used. -
Context root: The common root of all resources, specifies where in the URL path the application begins, and starts with a slash. In the example URL,
den-ping.com:8443/mygreatapp/home,/mygreatapp/is the context root.PingCentral prompts you for the context root when you add the application, and for the virtual hosts when you promote it.
-
-
The PingAccess web server determines whether a PingAccess session cookie (Web) or an OAuth token (API) exists for the user. If it does not, a web session starts. Web sessions define the policy for web application session creation, lifetime, timeouts, and their scope.
If you promote Web + API applications in PingCentral, you are required to select a Web session from a drop-down list. This information is not required to promote Web or API applications.
-
You can configure API and Web + API applications to use access token validators to locally verify signed and encrypted access tokens. If you are promoting an API or Web + API application in PingCentral, you can specify the access validation method, whether it be a token provider or a token validator, if appropriate.
-
Users are authenticated through the web session.
-
Policies are applied to the request. Policies are rules, or sets of rules, that are applied to application resources. PingAccess makes policy-based decisions to grant or deny access to the requested resource.
You can customize application and resource policies when you use templates to add applications to PingCentral.
-
Identity mapping is applied to the request if the target application expects user information to be included to further authenticate the user.
PingCentral prompts you for the name of the Web and/or API Identity mapping, as appropriate, when you promote it.
-
The user accesses the target web application or API.