Adding a policy for the Create Game endpoint
Now that we have confirmed that PingAuthorize Server is correctly configured to act as a reverse proxy to the Meme Game API, we can define a policy to try out its access control capabilities. This policy will accept or deny a request to create a game based on the identity making the request.
About this task
First, we define a service in the Trust Framework. Services have various uses, but at their most basic level, you use them to define a specific API that can be governed by your policies. By defining different services in your Trust Framework, you can target each policy specifically to their applicable APIs.
Then, we define a policy. This policy will reject any requests to start a new meme game if the user’s identifier ends with @example.com. We will identify users using the subject of the request’s access token.
Steps
-
Define the service.
-
Sign on to the Policy Editor using the URL and credentials from Accessing the GUIs.
-
Go to Trust Framework and click Services.
-
From the menu, select Add new Service.
-
For the name, replace Untitled with
Meme Game - Games.The service name must match the endpoint name. To understand why, see For further consideration: The PingAuthorize API security gateway, part 2.
-
Verify that in the Parent field, no parent is selected.
To remove a parent, click the delete icon to the right of the Parent field.
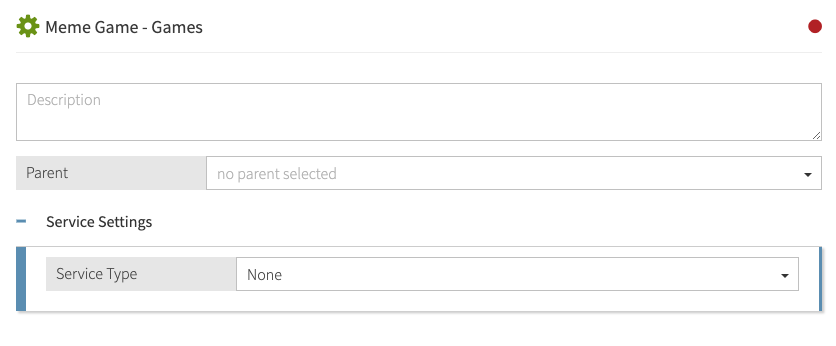
-
Click Save changes.
-
-
Define the policy.
-
In the Policy Editor, go to Policies in the left pane and then click Policies along the top.
-
Select Global Decision Point.
-
From the menu, select Add Policy.
-
For the name, replace Untitled with
Users starting a new game. -
Click next to Applies to.
-
In the upper-right corner of the left pane, click Components. This reveals a tree of items to target the policy and restrict the types of requests to which the policy applies.
-
From the Actions list, drag inbound-POST to the Add definitions and targets, or drag from Components box.
-
From the Services list, drag Meme Games - Games to the Add definitions and targets, or drag from Components box.
Using these components restricts the policy to incoming POST requests and the Meme Games - Games service.
-
Set the Combining Algorithm to Unless one decision is deny, the decision will be permit.
-
Click Add Rule. This reveals an interface to define a condition. Define the rule as follows.
-
For the name, replace Untitled with
Deny if token subject ends with @example.com. -
For Effect, select Deny.
-
Specify the condition.
-
Click Comparison.
-
From the Select an Attribute list, select HttpRequest.AccessToken.subject.
-
In the second field, select Ends With.
-
In the third field, type
@example.com.The following screen shows the rule.
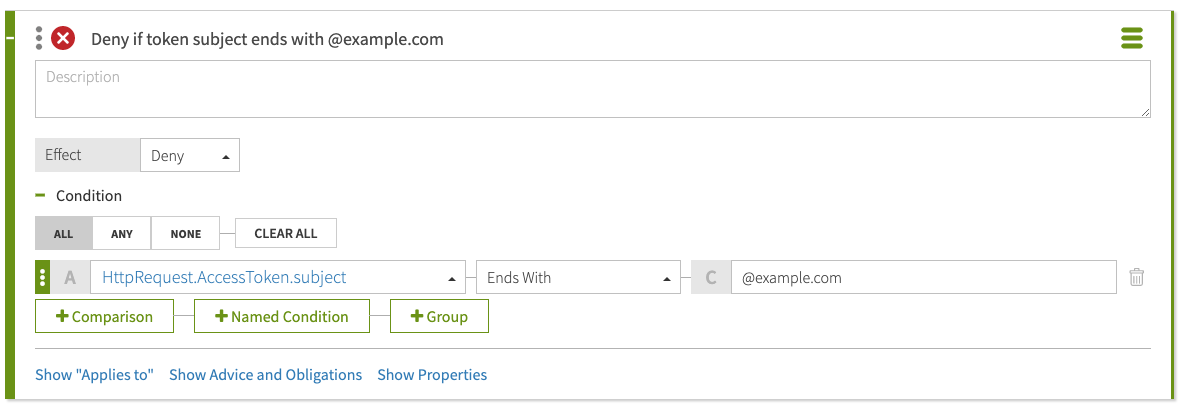
-
-
-
Click Save changes.
For more information about API security gateway processing, see For further consideration: The PingAuthorize API security gateway, part 2.
-