Tutorial: Creating the policy tree
This tutorial describes how to create a tree structure and ensure that your policies apply only to SCIM requests.
About this task
The default policies include the policy named Token Validation. In the PingAuthorize Policy Editor, you can find this policy under Global Decision Point. This policy denies any request using an access token if the token’s active flag is set to false. This policy is augmented with a set of scope-based access control policies.
Steps
-
To create the tree structure, perform the following steps:
-
Sign on to the PingAuthorize Policy Editor using the URL and credentials from Accessing the GUIs.
-
Click Policies.
-
Select Global Decision Point.
-
From the menu, select Add Policy Set.
-
For the name, replace Untitled with
SCIM Policy Set. -
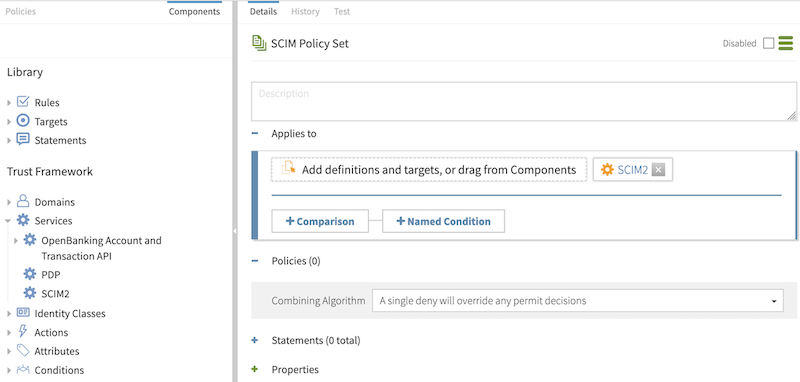
In the Policies section, set the Combining algorithm to A single deny will override any permit decisions.
A combining algorithm determines the manner in which the policy set resolves potentially contending decisions from child policies.
-
Click Applies to.
-
Click Components.
-
From the Services list, drag SCIM2 to the Add definitions and targets, or drag from Components box.
This step ensures that policies in the SCIM policy set apply only to SCIM requests.
-
Click Save changes.
Result:
You should have a screen like the following.
-
-
To add a branch under the SCIM policy set to hold SCIM-specific access token policies, go from Components to Policies and perform the following steps:
-
Select SCIM Policy Set.
-
From the menu, select Add Policy Set.
-
For the name, replace Untitled with
Token Policies. -
In the Policies section, set the Combining algorithm to A single deny will override any permit decisions.
-
Click Save changes.
-
-
To add another branch that holds a policy specific to access token scopes, perform the following steps:
-
Select Token Policies.
-
From the menu, select Add Policy Set.
-
For the name, replace Untitled with
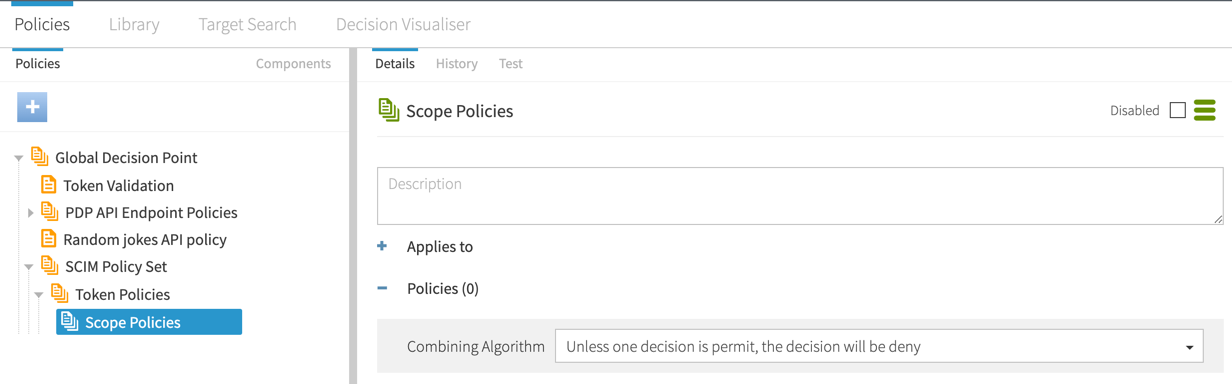
Scope Policies. -
In the Policies section, set the Combining algorithm to Unless one decision is permit, the decision will be deny.
-
Click Save changes.
Result:
After creating the new branches, they should look like the following.
-