Configuring AWS session tags for PingOne OIDC connections
You can configure AWS session tag support for OpenID Connect (OIDC) connections in PingOne by changing the attribute mappings in your OIDC application.
Before you begin
-
Create an Amazon Web Services (AWS) console account and policy that uses session tags. For help, see AWS prerequisites in the PingAccess documentation.
-
Sign on to your PingOne account as an administrator.
-
Configure an external identity provider, such as PingFederate, with a
Tagsattribute. The value must be in JSON format as specified by the AWS session tag feature.
Steps
-
Go to Applications → OIDC.
-
Select the application you want to edit and click Edit.
-
In the Default User Profile Attribute Contract section, click Add Attribute.
-
Enter
http://aws.amazon.com/tagsas shown, then click Next.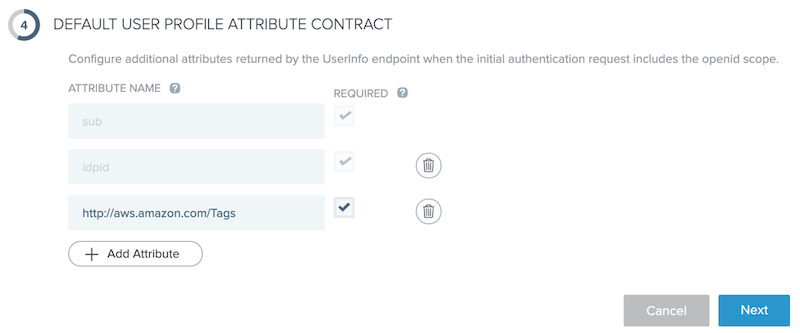
-
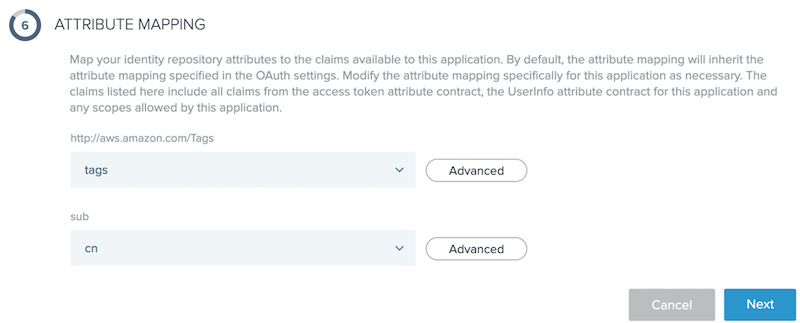
In the Attribute Mapping section, map the
http://aws.amazon.come/tagsattribute to the external identity provider attribute that contains the JSON formatted session tags data as shown.