Configuring AWS session tags for PingFederate SAML connections
You can configure AWS Identity and Access Management (IAM) and AWS IAM Identity Center session tag support for SAML connections in PingFederate.
Before you begin
-
If you want to use OGNL expressions to populate the values of the AWS session tags, see Enabling and disabling expressions in the PingFederate documentation.
-
Create an Amazon Web Services (AWS) console account and policy that uses session tags. For help, see AWS prerequisites (page 241) in the PingAccess documentation.
Steps
-
Open your service provider (SP) connection. Go to SP Connection > Browser SSO > Assertion Creation > Attribute Contract.
-
Extend the contract of the AWS SP connection.
Choose from:
-
If you are using AWS SSO, include the access control tags based on the following format:
-
https://aws.amazon.com/SAML/Attributes/AccessControl:{attribute}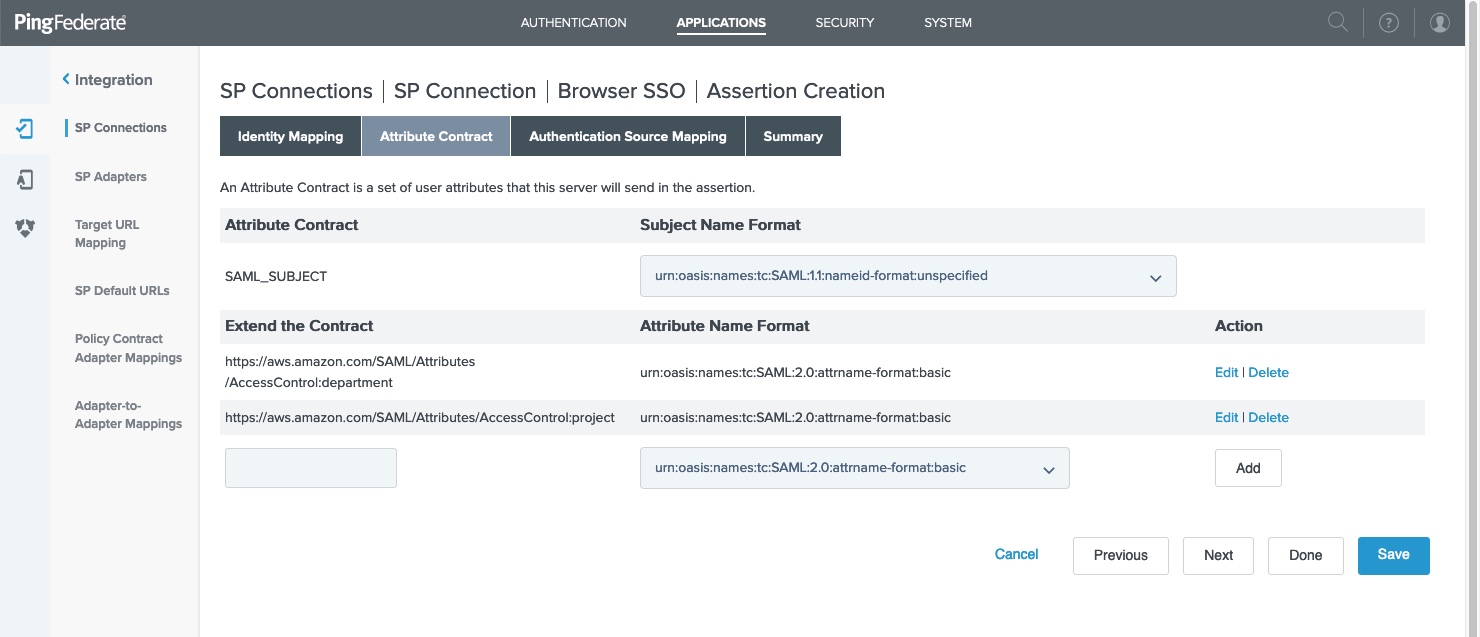
-
-
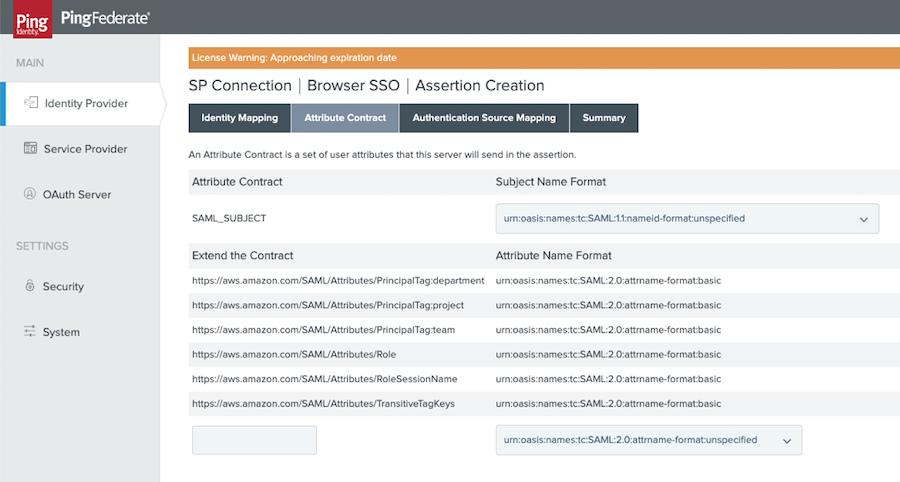
If you are using AWS IAM, include the AWS Principal Tags and TransitiveTagKeys, based on the following examples:
-
https://aws.amazon.com/SAML/Attributes/AccessControl:{attribute} -
https://aws.amazon.com/SAML/Attributes/PrincipalTag:project -
https://aws.amazon.com/SAML/Attributes/Role -
https://aws.amazon.com/SAML/Attributes/RoleSessioName -
https://aws.amazon.com/SAML/Attributes/TransitiveTagKeys
-
-
-
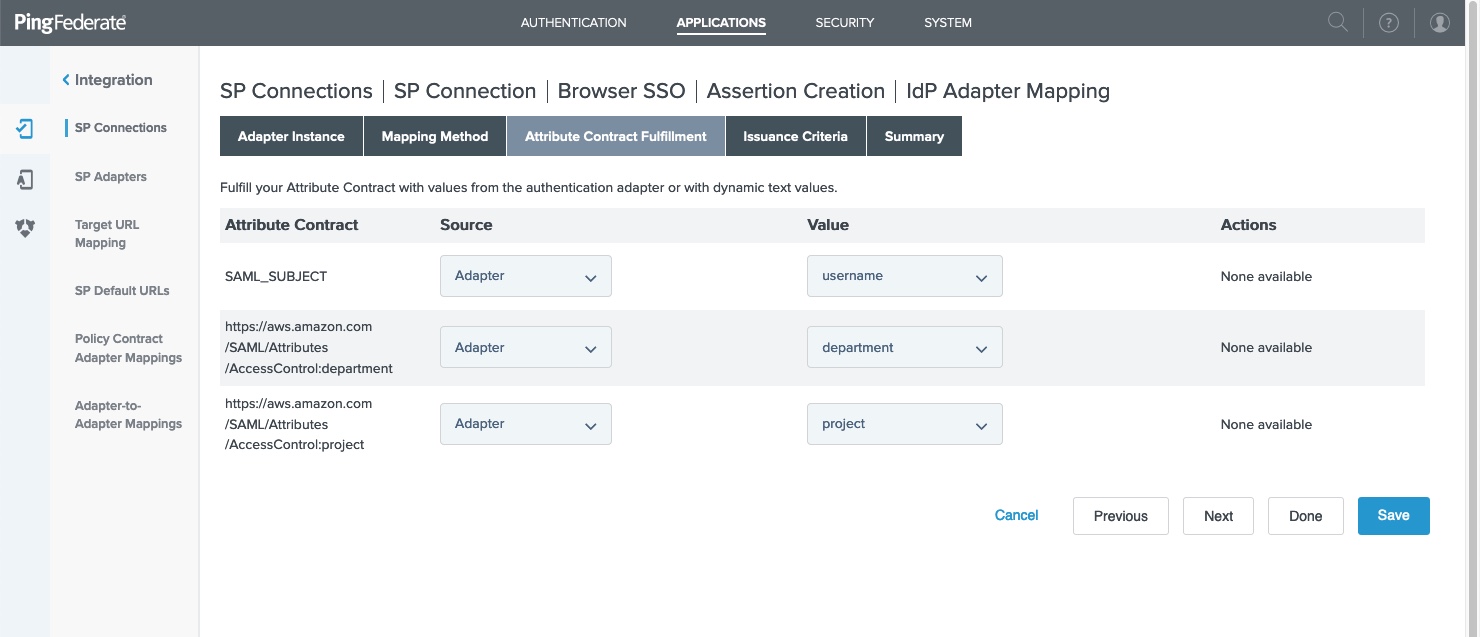
Go to SP Connection > Browser SSO > Assertion Creation > IdP Adapter Mapping > Attribute Sources & User Lookup > Attribute Contract Fulfillment.
-
Configure the attribute contract fulfillment for the AWS attributes.
Example 1: This example shows AWS IAM Identity Center attributes mapped directly from an HTML Form Adapter instance.
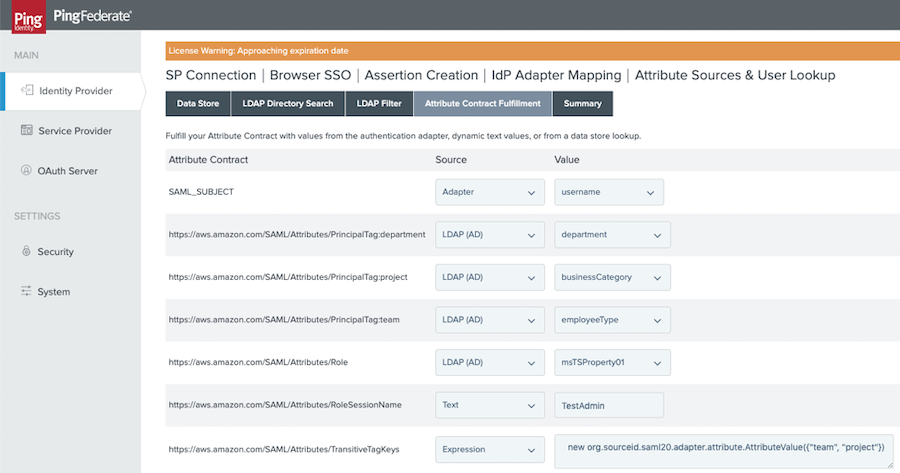
Example 2: This example shows AWS IAM attributes mapped from a data source and manipulated by the OGNL expression language available in PingFederate.
-
Click Save.