Creating advanced registration mapping
PingFederate leverages the HTML Form Adapter to deliver include PingFederate empowers administrators to deliver a secure and easy-to-use customer authentication, registration, and profile management solution. The HTML Form Adapter contract includes two core attributes.
About this task
Using the administrative console, create advanced registration mapping by defining authentication policies in your adapter instances.
To illustrate the configuration steps, consider the following setup that you have already made with the parameters username and policy.action.
Whether or not the local identity profile is configured with any authentication sources, if the user chooses to register directly by clicking on the Register now link, PingFederate sets the value to identity.registration. This fulfillment allows you to create rules to differentiate authentication requirements from the registration flow.
-
A PingDirectory installation with a set of users.
-
An LDAP datastore, an LDAP Username Password Credential Validator instance, and an HTML Form Adapter instance on PingFederate to validate credentials stored in PingDirectory.
-
An IdP authentication policy that chains the HTML Form Adapter instance, an PingID Adapter instance, and an authentication policy contract for the purpose of enforcing PingID multi-factor authentication in multiple browser-based single sign-on (SSO) use cases through service provider (SP) connections, OAuth authorization code flow, and OAuth implicit flow. The following window capture illustrates your existing policy.
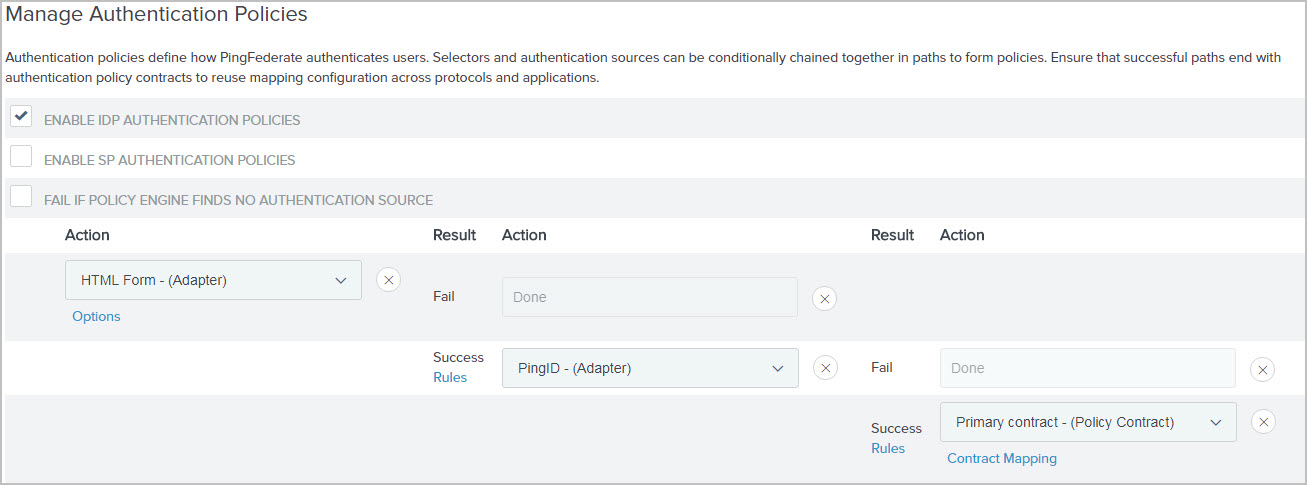
To illustrate the configuration steps, consider the following setup that you have. You need to add support for a consumer registration use case similar to the one in Setting up self-service registration, and, at the same time, keep the policy that enforces the multi-factor authentication requirement.
Steps
-
Set up PingDirectory for customer identities.
-
Make a note of which authentication policy contract is currently being used in your policy.
-
Create a local identity profile.
-
G to Authentication → Policies → Local Identity Profiles configuration wizard.
-
On the Profile Info tab, in the Local Identity Profile Name field, enter a name of the local identity profile, and from the Authentication Policy Contract list, select the authentication policy from step step 2. Select the Enable Registration check box.
If you want to enable profile management as well, select the relevant check box.
-
-
Configure the HTML Form Adapter instance for customer identities.
-
Go to Authentication → Integration → IdP Adapters.
-
From the Instance Name section, select the HTMLFormAdapter.
-
On the IdP Adapter tab, from the Local Identity Profile list, select a local identity profile.
-
Complete the rest of the configuration and save all changes.
-
-
Modify your existing IdP authentication policy.
-
Go to Authentication → Policies → Policies.
-
On the Policies tab, under the Policy section, click the relevant policy to open the Policy window.
-
Under the Success path of the HTML Form Adapter instance, click Rules.
-
In the Rules dialog, create a policy path for users who choose to register. For this sample use case, configure as follows.
Defining authentication policy rules attributes field and values Attribute Name Condition Value Result policy.action
equal to
identity.registration
Registration
Complete the rest of the configuration to create the local identity. The Result field controls the label shown for the policy path of this rule.
In addition, ensure the Default to Success check box is selected. When selected, the Success path remains, which is important for this sample use case where users are redirected to the PingID Adapter instance to fulfill the multi-factor authentication requirement after authenticating successfully against the HTML Form Adapter.
When finished, click Done, which brings you back to the Manage Authentication Policies window.
-
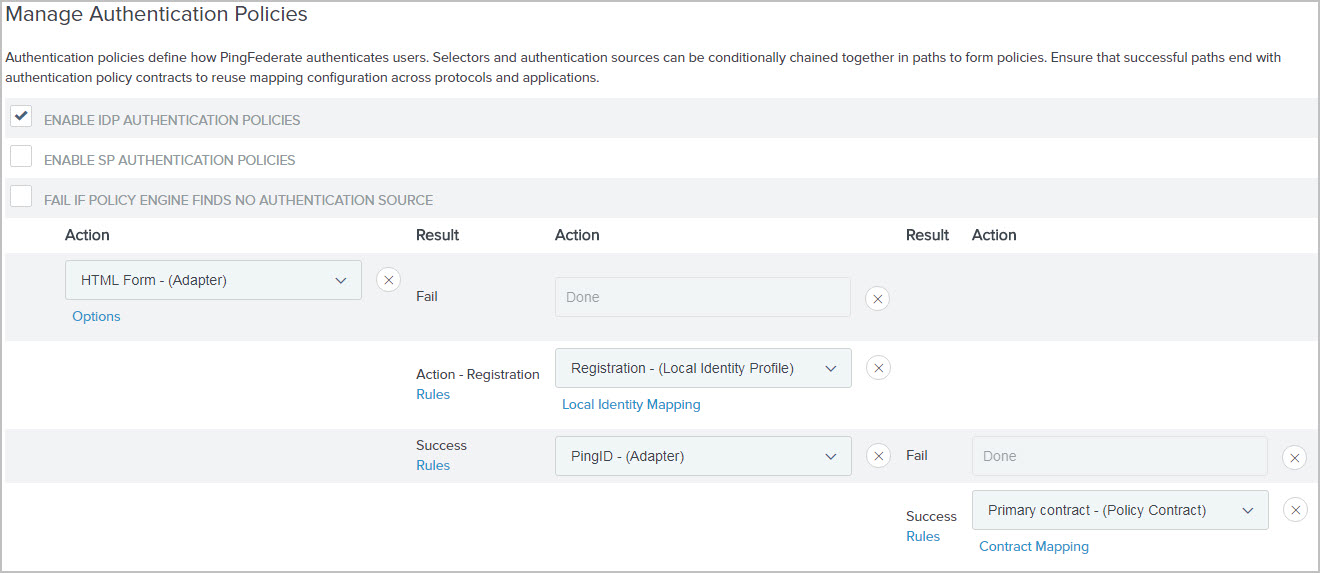
For the Registration path, select the local identity profile from step step 3 under Action and then complete its Local Identity Mappingconfiguration.
The following screen capture illustrates your new policy.
-
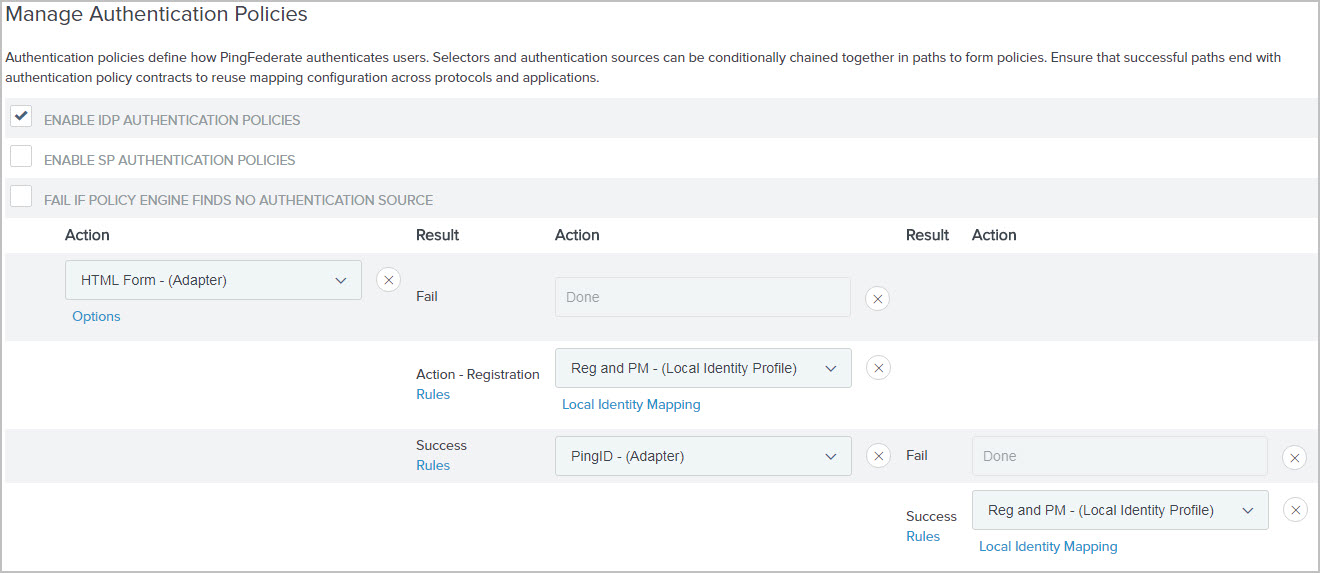
If you have enabled profile management in step step 3, you must also replace the policy contract with the local identity profile and then complete its Local Identity Mapping configuration.
This step is required so that PingFederate can route users through the HTML Form → PingID policy path when they try to access the profile management page.
The following screen capture illustrates this change.
No reconfiguration is required in your Browser SSO connections and OAuth grant-mapping configuration for your new policy to take effect.
-
Click Save to keep your changes.
-