OpenToken Adapter
To transfer identity and other user information between the PingFederate server and an end application, the PingFederate architecture allows for custom adapters to be deployed with the server.
PingFederate ships with a deployed OpenToken Adapter, which uses a secure token format OpenToken to transfer user attributes between an application and the PingFederate server.
On the identity provider (IdP) side, the OpenToken Adapter allows the PingFederate server to receive a user’s identity from the IdP application.
For SAML connections, the IdP application can provide an authentication context to the service provider (SP) by including the authnContext attribute with the desired value in the secure token. Standard URIs are defined in the SAML specifications. For more information on assertions and protocol for SAML, see and saml-authn-context-2.0-os.pdf in the OASIS documentation.
If the secure token does not contain the authnContext attribute, PingFederate sets the authentication context as follows:
-
urn:oasis:names:tc:SAML:1.0:am:unspecifiedfor SAML 1.x -
urn:oasis:names:tc:SAML:2.0:ac:classes:unspecifiedfor SAML 2.0
As needed, the authentication context can be overridden by either an instance of the Requested AuthN Context Authentication Selector or the SAML_AUTHN_CTX attribute in the SAML attribute contract. The latter takes precedence.
On the SP side, the OpenToken Adapter can be used to transfer user-identity information to the target SP application.
Specialized application integration kits are available from the Ping Identity Downloads website. Many kits leverage the OpenToken Adapter to integrate applications with the PingFederate server. The agent portions of the integration kits reside with the application and use the OpenToken to communicate with the OpenToken Adapter.
|
To integrate applications for use with the OpenToken Adapter, download an integration kit for PingFederate from the Ping Identity Downloads website and follow instructions for installing and using Agent Toolkits in the accompanying documentation. Follow the configuration instructions in Configuring an OpenToken IdP Adapter instance to setup and to use with your applications. |
The following figure shows a basic IdP-initiated single sign-on (SSO) scenario using PingFederate with the Java Integration Kit on both sides of an identity federation.
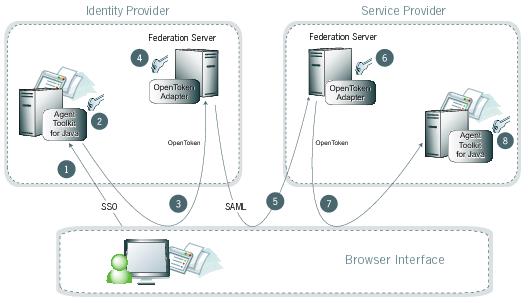
Processing steps
-
A user initiates an SSO transaction.
-
The IdP application inserts attributes into the Agent Toolkit for Java, which encrypts the data internally and generates an
OpenToken. -
A request containing the
OpenTokenis redirected to the PingFederate IdP server. -
The server invokes the OpenToken IdP Adapter, which retrieves the
OpenToken, decrypts, parses, and passes it to the PingFederate IdP server. The PingFederate IdP server then generates a SAML assertion. -
The SAML assertion is sent to the SP site.
-
The PingFederate SP server parses the SAML assertion and passes the user attributes to the OpenToken SP Adapter. The Adapter encrypts the data internally and generates an
OpenToken. -
A request containing the
OpenTokenis redirected to the SP application. -
The Agent Toolkit for Java decrypts and parses the
OpenTokenand makes the attributes available to the SP Application.