SP-initiated SSO—POST-POST
In this scenario, a user attempts to access a protected resource directly on a service provider (SP) website without logging on. The user does not have an account on the SP site but does have a third-party identity provider (IdP)-federated account. The SP sends an authentication request to the IdP. The user’s browser sends both the request and the returned SAML assertion through HTTP POST.
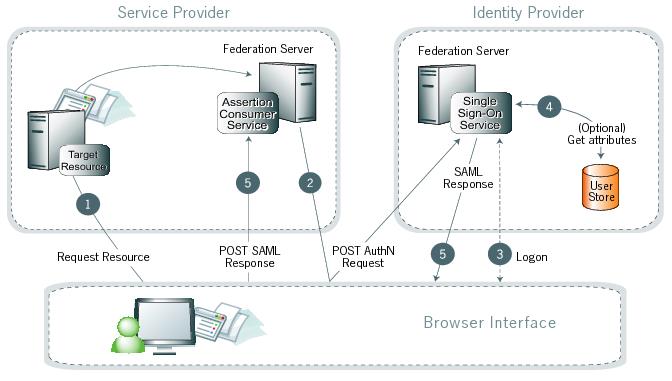
Processing steps
-
The user requests access to a protected SP resource. The request redirects to the federation server to handle authentication.
-
The federation server sends an HTML form back to the browser with a SAML request for authentication from the IdP. The HTML form automatically posts to the IdP’s SSO service.
-
If the user is not already logged on to the IdP site or needs to re-authenticate, The IdP asks for credentials, such as ID and password, and the user logs on.
-
The user data store can provide additional information about the user for inclusion in the SAML response. The federation agreement between the IdP and the SP predetermines these attributes. See User attributes.
-
The IdP’s SSO service returns an HTML form to the browser with a SAML response containing the authentication assertion and any additional attributes. The browser automatically posts the HTML form back to the SP.
SAML specifications require digitally-signed POST responses.
-
(Not shown) If the signature and the assertion, or the JSON Web Token, are valid, the SP establishes a session for the user and redirects the browser to the target resource.