Defining a provisioning target
You can define a provisioning target, including the provider’s web-service endpoint for provisioning users, and, if required, credentials that PingFederate uses for authentication to the provisioning API for the service provider (SP).
About this task
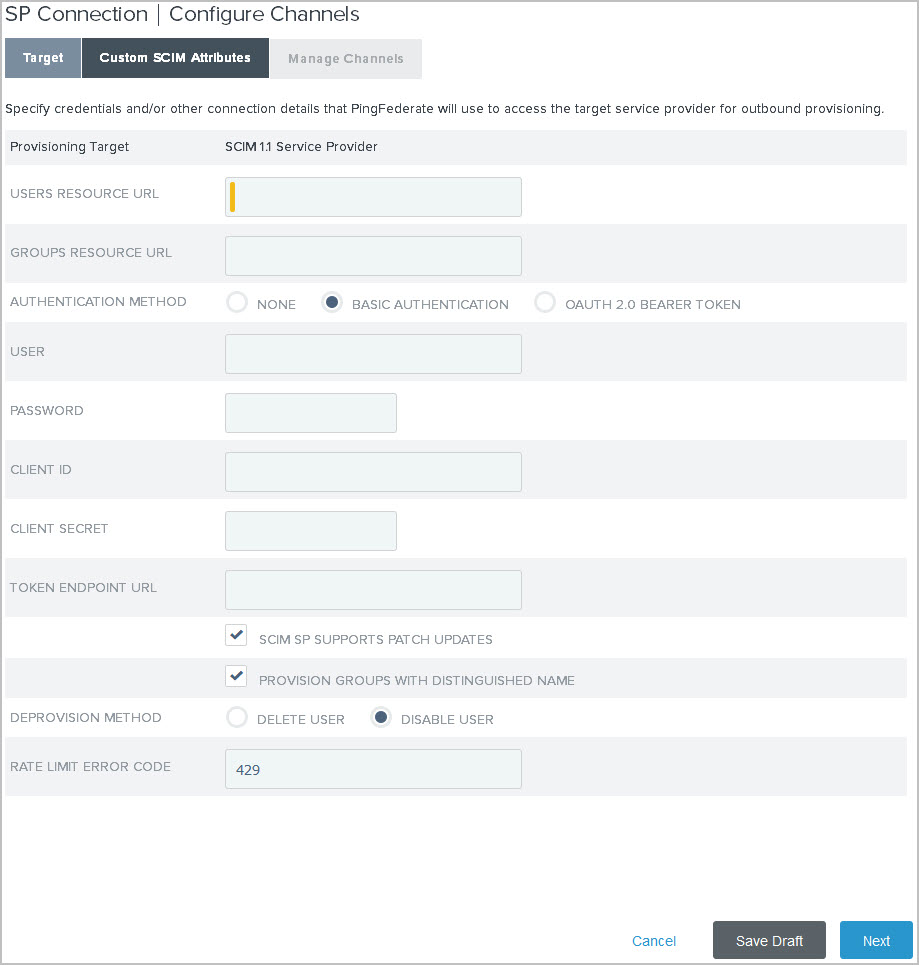
|
The target configuration settings vary among System for Cross-domain Identity Management (SCIM) outbound provisioning and various Software as a Service (SaaS) provisioning. For SCIM provisioning to PingOne for Enterprise, sign on to the PingOne admin portal and review the target information on the Setup > Identity Repository tab. For any SaaS Connector target, refer to the documentation in the add-on distribution package. |
The following steps describe the fields required for the bundled PingFederate provisioning plugin for SCIM partners.
Steps
-
Enter the endpoint for managing users in the Users Resource URL field. For example, https://example.com/v1/Users
This field is always required for SCIM outbound provisioning.
-
Go to Applications > Integration > SP Connections > SP Connection > Configure Channels>
-
On the Custom SCIM Attributes tab, configure the remaining outbound provisioning settings.
Refer to the following table for detailed information about each field:
Field Description Groups Resource URL
The partner’s group management endpoint. For example, https://example.com/v1/Groups
Required if the partner supports this notion and groups should be provisioned.
Authentication Method
The authentication scheme that the partner’s endpoints support.
Available options:
-
None
-
Basic Authentication (default)
-
OAuth 2.0 Bearer Token: Uses the resource owner grant type by submitting the client ID, client secret, username, and password to the configured token endpoint URL in exchange for an access token that will be sent in each SCIM request.
User
Password
Valid credentials to access the partner’s endpoint.
Required if Basic Authentication is the selected authentication method.
Client ID
Client Secret
Token Endpoint URL
Valid OAuth client credentials and token endpoint to access the partner’s endpoint.
Required if OAuth 2.0 Bearer Token is the selected authentication method.
SCIM SP Supports Patch Updates
Clear this checkbox if the partner does not support PATCH updates.
Learn more about PATCH in the www.simplecloud.info/specs/draft-scim-api-01.html#edit-resource-with-patch[SCIM specification].
This checkbox is selected by default.
Provision Groups with Distinguished Name
Select this checkbox to provision groups by supplying complete LDAP distinguished names (DNs), rather than only common names (CNs), to identify groups.
Some SCIM partners, including PingOne for Enterprise, allow administrators to parse full DNs when necessary, such as in the case of duplicate CNs, to determine group access mapping to specific applications based on other DN elements. Consult the partner for its requirement.
This checkbox is selected by default.
Deprovision Method
Deprovisioning is triggered when previously provisioned users no longer meet the condition set in Manage Channels > Channel > Source Location.
Available options:
-
Disable User (default)
This option deactivates the user accounts.
-
Delete User
This option removes the user accounts.
For SaaS provisioning, the provisioner does not necessarily remove deprovisioned users from target data stores in accordance with common practice. Instead, their status changes to indicate that the accounts are no longer active.
Rate Limit Error Code
The expected error code returned by the partner based on its rate-limiting threshold.
The default value is
429. -
-
Click Next.
For some provisioning plugins, including the built-in SCIM outbound provisioner, when you enter or change credentials and click Next, PingFederate immediately tests connectivity to the target.