WS-Federation
PingFederate supports the WS-Federation Passive Requestor Profile for service provider (SP)-initiated single sign-on (SSO), enabling interoperability with Microsoft’s Active Directory Federation Service (ADFS).
This profile allows for straightforward redirects and HTTP GET and POST methods to transport SAML assertions or JSON web tokens (JWTs) as security tokens for SSO and logout request and response messages for single logout (SLO).
|
Unlike SAML, WS-Federation consolidates the endpoints for SLO and SSO. When you set up a WS-Federation connection in PingFederate, both types of transactions are available to an SP web application that supports them both. |
For more information about WS-Federation and the Passive Requestor Profile, see web services Federation Languages.
Passive Requestor profile
This profile permits a user’s browser, the passive requestor, to request a security token from an identity provider (IdP) when the user requests access to a protected web service or other resource at an SP.
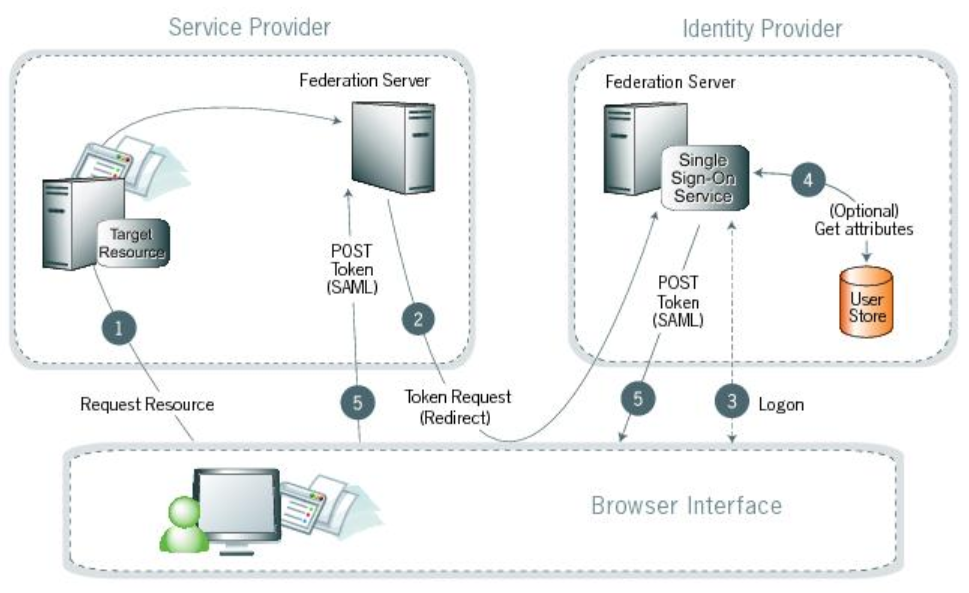
Processing steps
-
A user requests access to a protected SP resource. The user is not logged on to the site. The request is redirected to the federation server to handle authentication.
-
The SP generates a security token request and redirects the browser to the identity provider’s WS-Federation implementation.
-
If the user is not already logged on to the IdP site or if re-authentication is required, the IdP asks for credentials, such as ID and password, and the user logs on.
-
Additional information about the user can be retrieved from the user datastore for inclusion in the SAML response. These attributes are predetermined as part of the federation agreement between the IdP and the SP. For more information, see User attributes.
-
The federation server creates a response containing a signed SAML assertion, or a JSON Web Token, and returns it to the SP through POST.
-
(Not shown) If the signature and the assertion, or the JWT, are valid, the SP establishes a session for the user and redirects the browser to the target resource.
Single logout using WS-Federation is handled in much the same way as with SAML. For more information, see Single logout. However, HTTP GET/POST is always used as the transport mechanism.