Configuring OpenID Provider information
You must configure OpenID Provider (OP) settings and information when configuring service provider (SP) browser single sign-on (SSO).
Steps
On the OpenID Provider Info tab, provide the scopes, the endpoints, and the authentication scheme.
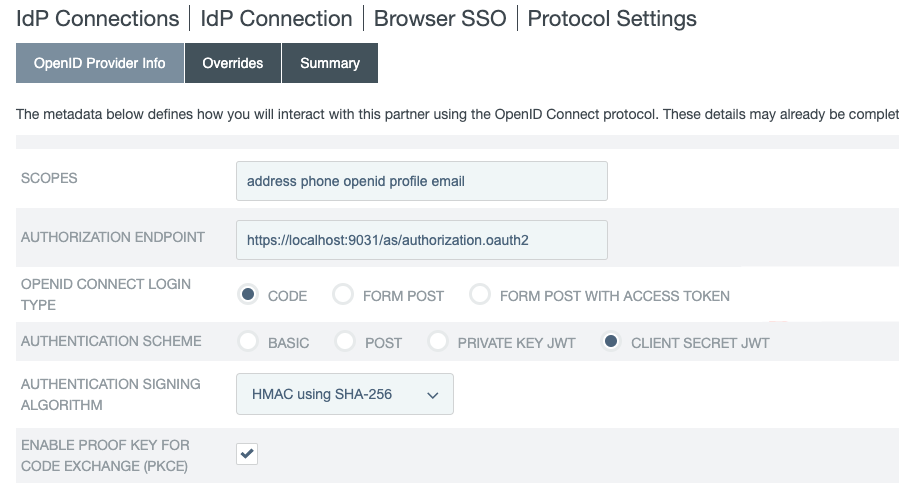
|
If you clicked Load Metadata from the OpenID Provider (OP) on the General Info tab, the Scopes field and all endpoints are pre-populated, provided that the metadata contains the information. |
| Field | Description | ||||||
|---|---|---|---|---|---|---|---|
Scopes |
The scopes to be included in the OpenID Connect (OIDC) authentication and OAuth token requests to the OP. Multiple space-separated values are allowed. The default value, without loading metadata from the OP, is
|
||||||
Authorization Endpoint |
The authorization endpoint at the OP. You can enter a relative path, starting with a forward slash, if you provide base URL on the General Info tab. There is no default value without loading metadata from the OP. |
||||||
OpenID Connect Login Type |
The OIDC client profile of the client. This client represents PingFederate and is created and managed at the OP.
The resulting value of the The resulting value of the The resulting values of the The default selection, without loading metadata from the OP, is Code. |
||||||
JWT Secured Authorization Response Mode (JARM) |
JARM is supported when sending authorization requests as a relying party to the OpenID Provider using IdP Connections. These values map to:
|
||||||
Authentication Scheme |
The client authentication method that PingFederate uses. Applicable and visible only to clients supporting the Basic Client profile.
The default selection, without loading metadata from the OP, is Basic. |
||||||
Authentication Signing Algorithm |
If Private Key JWT or Client Secret JWT is the chosen authentication scheme, select the algorithm that PingFederate uses to sign the JSON Web Token (JWT).
If Client Secret JWT is the chosen authentication scheme, the signing algorithms are |
||||||
Type |
If Private Key JWT or Client Secret JWT is the chosen authentication scheme, specify the JWT type. The default is none, but it’s recommended to use a preset value of |
||||||
Lifetime (Minutes) |
If Private Key JWT or Client Secret JWT is the chosen authentication scheme, define the lifetime of the JWT in minutes. The default is 5 minutes and is modifiable. |
||||||
Audience |
If Private Key JWT or Client Secret JWT is the chosen authentication scheme, determine the audience of the JWT. The default is the IdP’s token endpoint, but a suggested preset value is the issuer. Learn more in RFC 7523. |
||||||
Include Not Before (NBF) Claim |
If Private Key JWT or Client Secret JWT is the chosen authentication scheme, the produced assertion will include an |
||||||
Enable Proof Key for Code Exchange (PKCE) |
Select this checkbox to enable PingFederate to send a SHA256 code challenge and corresponding code verifier as a Proof Key for Code Exchange (PKCE) to the OP during the Code authentication flow. This checkbox is applicable and visible only when the OpenID Connect Login Type is Code.
|
||||||
Pushed Authorization Request Endpoint |
The Pushed Authorization Request (PAR) endpoint at the OP. When you configure a PAR endpoint, the IdP connection sends authorization requests directly to this endpoint. All parameters associated with an authorization request are transmitted to the PAR endpoint. You can find more information about the PAR protocol in OAuth 2.0 Pushed Authorization Requests on the IETF website. You can enter the relative path,
|
||||||
Token Endpoint, UserInfo Endpoint, and JWKS URL |
OAuth 2.0 and OIDC 1.0 endpoints at the OP. Learn more in OpenID Connect specifications.
There are no default values without loading metadata from the OP. |
||||||
Sign Request |
Select this checkbox to send request parameters as claims in a request object, a self-contained, signed JWT as one When this optional configuration is enabled, the OP can validate the integrity of the request parameters based on the digital signature found in the signed JWT. Learn more in Passing a Request Object by Value in the OpenID Connect specification. When this optional configuration is enabled, the JWT signed request object includes the This checkbox is not selected by default, in which case PingFederate sends request parameters with multiple query parameters, unsigned. |
||||||
Request Signing Algorithm |
Select the algorithm that PingFederate uses to sign the request object. Applicable and visible only when the Sign Request checkbox is selected. If the client signs its JWTs using an RSASSA-PSS signing algorithm, PingFederate must be deployed to run in a Java 8 or Java 11 runtime environment or integrated with a hardware security module (HSM) and a static-key configuration for OAuth and OIDC. You can find more information on HSM integration and static keys in Supported hardware security modules and Keys for OAuth and OpenID Connect, respectively.
|
||||||
Track User Sessions for Logout |
When selected, PingFederate tracks logout entries in the user session so that PingFederate can handle and initiate logout requests. Also, when selected, the Logout Endpoint field is displayed, and the IdP Connection page’s Activation & Summary tab displays the connection’s Front-Channel Logout URI and Back-Channel Logout URI. The checkbox is cleared by default. |
||||||
Logout Endpoint |
The endpoint to which PingFederate will redirect the user in order to terminate their session at the OP. This field is only displayed if Track User Sessions for Logout is selected. When this field is populated, theIdP Connection page’s Activation & Summary tab displays the connection’s Post-Logout Redirect URI. |
Remain on the OpenID Provider Info tab and specify the request parameters that are allowed to be included in the authentication requests to the OP under Request Parameters. Learn more in Configuring request parameters and SSO URLs.