Simple network
The Simple network option offers secure connectivity between your resources in on-premise, AWS, or third-party cloud environments.
This option is best if you:
-
Complete authentication from PingOne Advanced Services to a data source located either on-premise or in another cloud environment
-
Can have log streaming available on either a public or private network
There are two different types of Simple network options available:
These networks are not mutually exclusive, so both can be used at the same time, if appropriate.
Simple VPN network
The Simple VPN network option supports a wide range of protocols, such as LDAPS and HTTPS, to connect to your resources, including Oracle, Active Directory, and LDAP. The VPN connection also supports REST and some custom protocols in your network.
There are two different types of Simple VPN networks:
- Single VPN network
-
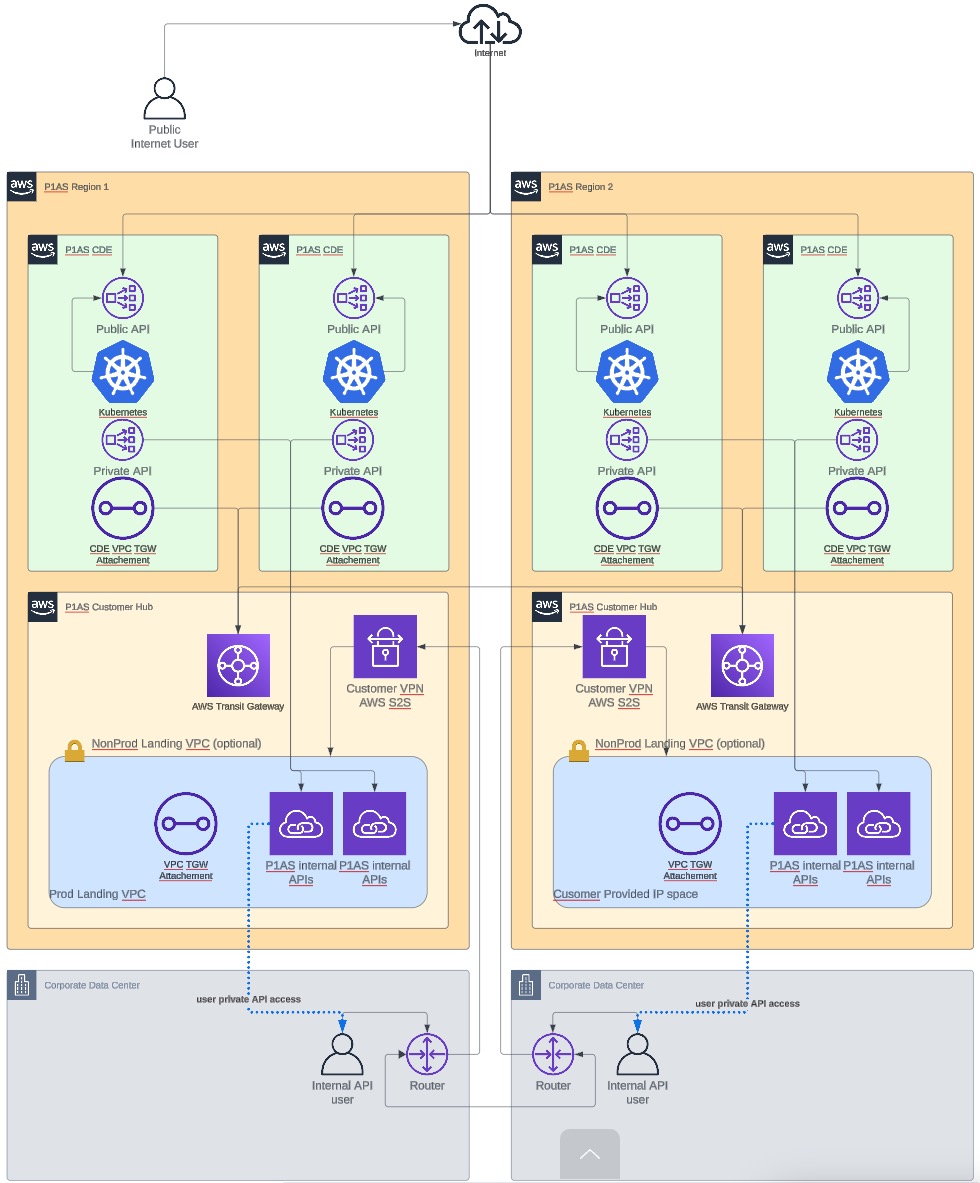
This model uses a single VPN connection for each region.
Single VPN network diagram
- Split VPN network
-
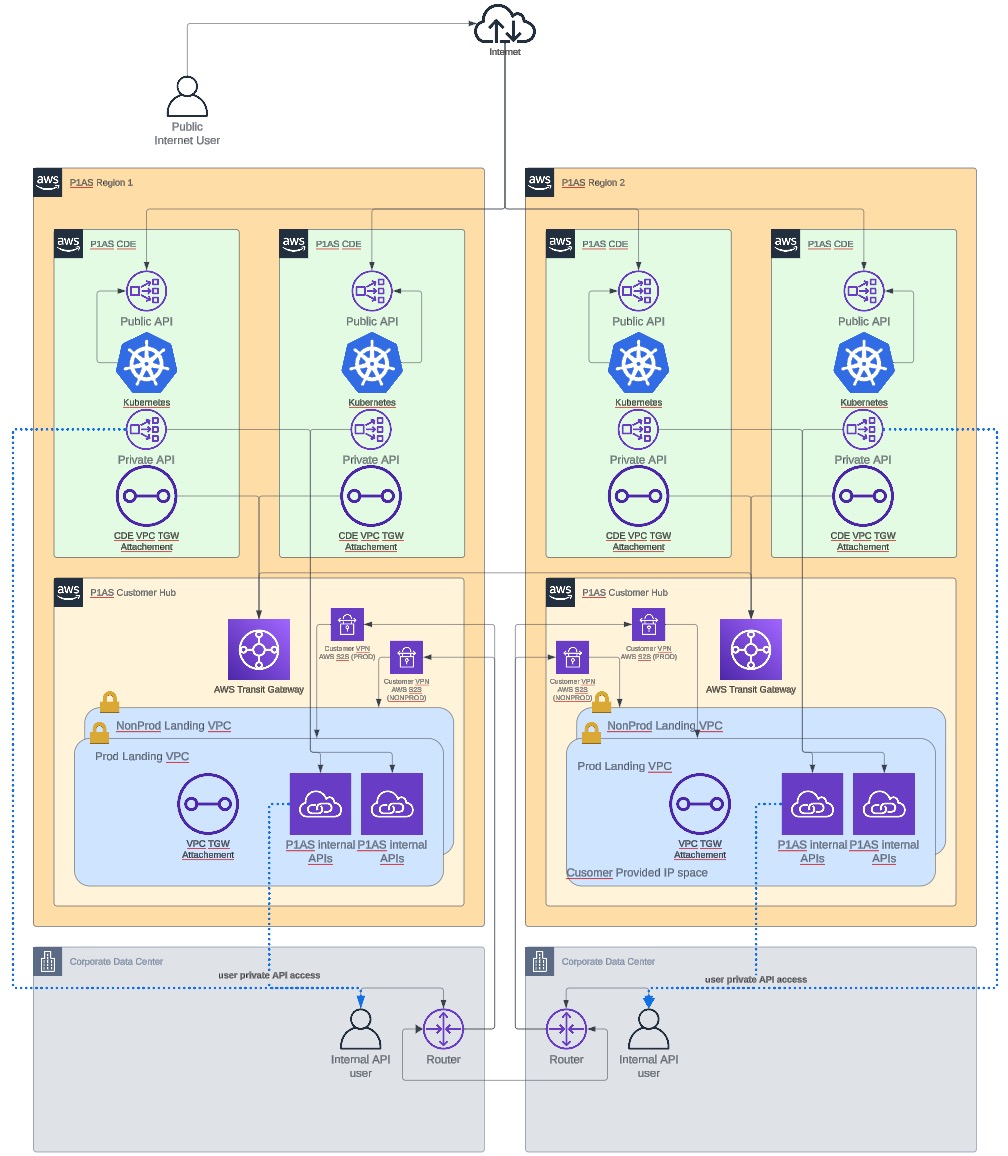
With this model, one connection is used for production environments (Prod and Stage), and the other connection is used for non-production environments (Dev and Test). If a split VPN connection is configured, the customer must supply a unique, customer-side router IP address for each connection. They are not redundant connections. Refer to the following diagram for details.
Split VPN network diagram
Additional items to consider include:
-
The type of VPN used must be on the list of VPNs supported by AWS.
-
A Site-to-Site VPN connection is used to connect your remote network to a VPC, which requires you to provide IP addresses. Each Site-to-Site VPN connection has two tunnels, with each tunnel using a unique public IP address. You should configure both tunnels for redundancy. Learn more in Tunnel options for your Site-to-Site VPN connection.
-
For this type of network, you will need to provide a /24 CIDR block from your RFC1918 IP space for the VPN landing zone. All the private PingOne Advanced Services private endpoints that you connect to will be within the specified IP range in your AWS account.
To learn more, see What is AWS Site-to-Site VPN? in the AWS Site-to-Site VPN User Guide.
To learn more about additional items that you might also need to consider, see Setup considerations.
AWS PrivateLink network
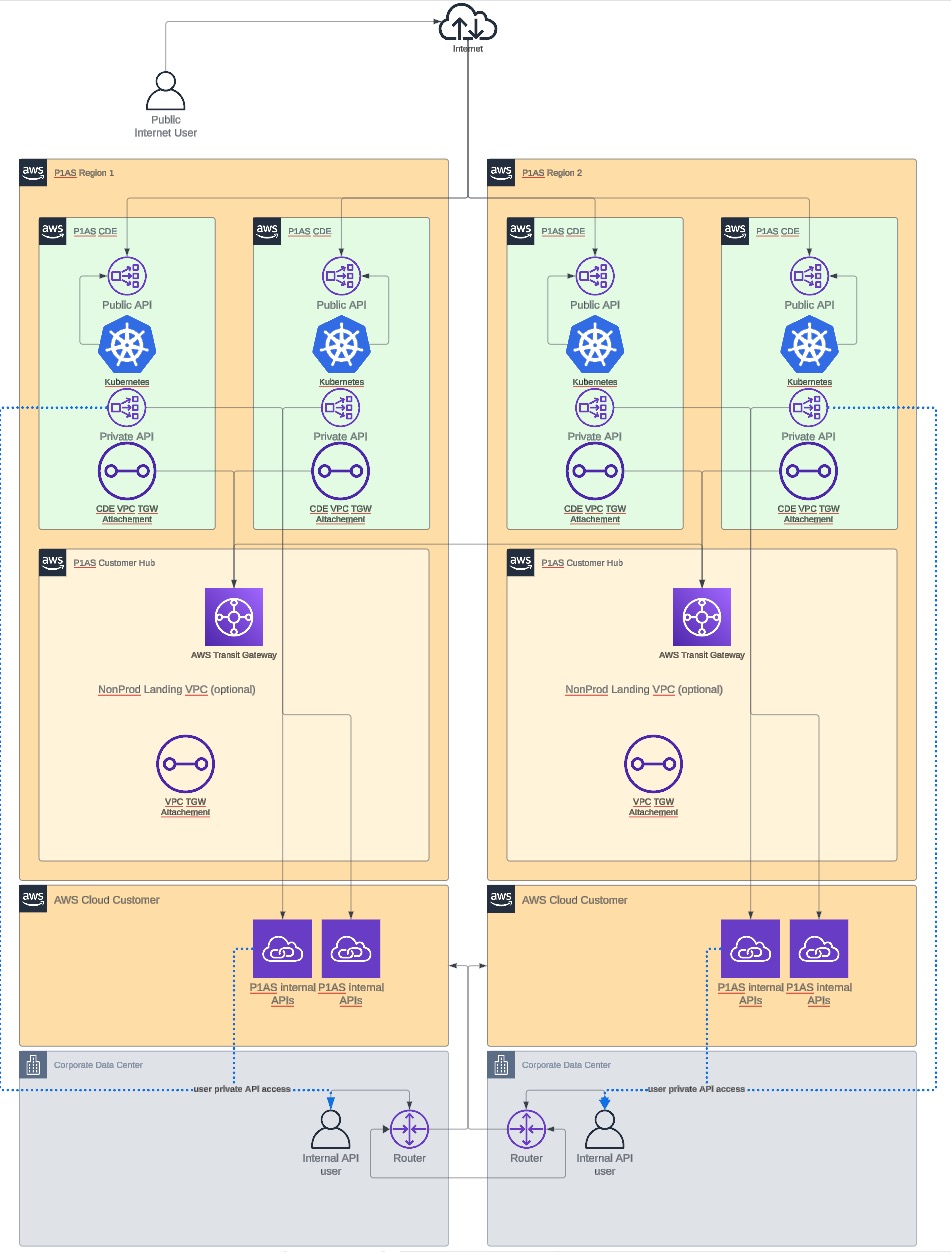
If you have your own AWS infrastructure and already established network connectivity and routing to and from it, the AWS PrivateLink network might be the right option for you. It does not require you to provide IP addresses for development or connectivity because IP space is hosted within your AWS Virtual Private Cloud (VPC).
This network option might also be appropriate if you need TCP connectivity and can be used in conjunction with a Simple VPN network.
Unlike the Simple VPN network, it is not a multipurpose connection. Instead, consider which services will be exposed for each environment and ensure they can be accessed using the appropriate protocol, such as HTTPS (API endpoints for PingAccess, PingFederate, and PingDirectory) and LDAPS.
-
Set up AWS PrivateLink for each of your PingOne Advanced Services environments.
-
Then, set up AWS PrivateLink endpoints in your AWS account that point to the exposed services.
-
Finally, set up a private hosted zone that contains the required hostnames in DNS records for the exposed services.
AWS PrivateLink network diagram
To learn more, see What is AWS PrivateLink? in the Amazon Virtual Private Cloud User Guide.
To learn more about additional items you might need to consider, see Setup considerations.
Simple network endpoints
Public and private endpoints for the Simple network model are listed here.
Default public endpoints
| Default public endpoints | URLs |
|---|---|
PingAccess |
https://pingaccess.{environment}-{customer}.{region}.ping.cloud/ |
PingFederate |
https://pingfederate.{environment}-{customer}.{region}.ping.cloud/ |
Environment logs |
https://logs.{environment}-{customer}.{region}.ping.cloud/ |
Environment monitoring |
https://monitoring.{environment}-{customer}.{region}.ping.cloud/ |
PingFederate admin console |
https://pingfederate-admin.{environment}-{customer}.{region}.ping.cloud/ |
PingAccess admin console |
https://pingaccess-admin.{environment}-{customer}.{region}.ping.cloud/ |
PingCentral |
https://pingcentral-admin.{customer}.{region}.ping.cloud/ |
Argo CD |
https://argocd.{customer}.{region}.ping.cloud/ |
Optional public endpoints
| Optional public endpoints | URLs | ||
|---|---|---|---|
PingFederate admin API |
https://ext-pingfederate-admin-api.{environment}-{customer}.{region}.ping.cloud |
||
PingAccess admin API |
https://ext-pingaccess-admin-api.{environment}-{customer}.{region}.ping.cloud |
||
PingDirectory
|
ldaps://ext-pingdirectory-admin.{environment}-{customer}.{region}.ping.cloud |
||
PingDirectory API |
https://ext-pingdirectory.{environment}-{customer}.{region}.ping.cloud |
||
PingDelegator |
https://ext-pingdelegator.{environment}-{customer}.{region}.ping.cloud |
||
PingFederate global (multi-region only) |
https://pf.{environment}.global.{customer}.ping.cloud |
||
PingAccess global (multi-region only) |
https://pa.{environment}.global.{customer}.ping.cloud |
Optional private endpoints
| Optional private endpoints | URLs | ||
|---|---|---|---|
PingFederate admin API |
https://int-pingfederate-admin-api.{environment}-{customer}.{region}.ping.cloud/ |
||
PingAccess admin API |
https://int-pingaccess-admin-api.{environment}-{customer}.{region}.ping.cloud/ |
||
PingDirectory
|
ldaps://int-pingdirectory-admin.{environment}-{customer}.{region}.ping.cloud/ |
||
PingDirectory API |
https://int-pingdirectory.{environment}-{customer}.{region}.ping.cloud |
||
PingDelegator |
https://int-pingdelegator.{environment}-{customer}.{region}.ping.cloud/ |
|
If the AWS PrivateLink network model is used,
an |