Testing policies
Test PingAuthorize policies from end-to-end with visualization tools that show the complete decision flow.
Steps
-
Go to Policies.
-
Select the policy you want to test and then click the Test tab.
-
Define the test scenario:
-
In the Domain list, select any domains you want to include as request parameters.
-
In the Service list, select any services you want to include as request parameters.
-
In the Identity Provider list, select any identity providers you want to include as request parameters.
-
In the Action list, select any actions you want to include as request parameters.
-
In the Attributes list, select any attributes you want to include as request parameters and provide sample values.
-
In the Overrides section, configure attribute and service values to override those elements' default behavior.
For example, if an attribute is defined with a request parameter resolver and no value is specified in the test request, the decision service resolves that attribute from the Overrides configuration.
You can override any attribute’s value, regardless of its resolution or processing details.
-
-
Click Execute.
If the test scenario exceeds 50 kB in size, sample values will not be stored in the local cache after executing the test request. Result:
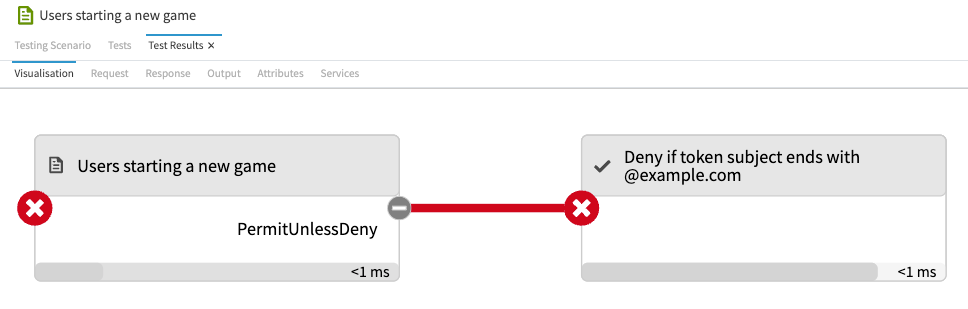
The Visualization tab shows test results.
-
Examine the decision flow to make sure decisions are evaluated according to your expectations.
You can click any box in the flow to show more details.
-
Click the other tabs for additional details.
-
Request tab: Shows the JSON request sent to the decision engine, allowing you to confirm that the expected information was sent.
-
Response tab: Shows the complete, high-verbosity response for the decision.
If the same comparison condition is attached to more than one rule in the policy subtree, the decision response only includes the evaluation of the first occurrence of this condition. Although the condition is only included once in the response, the decision engine evaluates this condition wherever it is needed to make a decision.
If the parent policy of the first instance of this condition is not applicable to the request, the decision response does not include evaluation of any rule containing this condition. This behavior is the same regardless of the rule’s outcome (
Permit,Deny,Not Applicable). -
Output tab: Shows details about the decision, including the time it took to evaluate policies and rules.
-
Attributes tab: Shows details about the attributes used in the decision.
-
Services tab: Shows details about the services used in the decision.
-
-
To repeat the test using a different scenario, click the Testing Scenario tab, change the parameters and then click Execute.