Configuring Policy Editor policy request header mappings
You can configure the Policy Editor to enforce request header mappings during policy development and testing.
About this task
By defining a policy request header mapping, you can map a decision request header to a Trust Framework attribute. The Policy Editor uses this mapping to dynamically populate the attribute’s value with the value of an incoming request header, enabling you to leverage header data as additional context in the request body.
You can configure policy request header mappings in embedded policy decision point (PDP) mode for production environments. Learn more in Configuring policy request header mappings.
Steps
-
Make a copy of the default options file:
$ cp config/options.yml my-options.yml -
In the
coresection of the new options file, uncomment thedecisionRequestHeaderMappingfield. -
In the
headerKeysfield, enter a list of mappings in the form of key-value pairs, where the key is the header name and the value is the attribute’s full name:decisionRequestHeaderMapping: enabled:true headerKeys: "x-correlation-id": "Request.Headers.x-correlation-id"The full name of an attribute represents that attribute’s full path in the Trust Framework hierarchy. For example, a Param1 attribute with parent attributes Request and Header would have a full name of Request.Header.Param1. To quickly obtain an attribute’s full name, in the attribute’s hamburger menu , select Copy full name to clipboard.
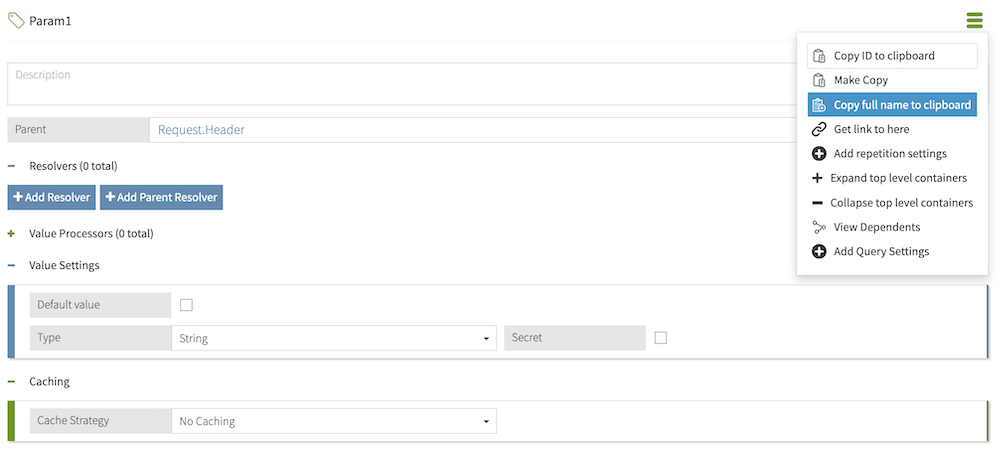
The header name is not case sensitive.
-
Stop the Policy Editor.
-
Run
setupusing the--optionsFileargument and customize all other options as appropriate:$ bin/setup demo \ --adminUsername admin \ --generateSelfSignedCertificate \ --decisionPointSharedSecret pingauthorize \ --hostname <pap-hostname> \ --port <pap-port> \ --adminPort <admin-port> \ --licenseKeyFile <path-to-license> \ --optionsFile my-options.yml -
Start the Policy Editor.
$ bin/start-server