Configuring Apigee for PingAccess integration
Install the PingAuth shared flow bundle in Apigee and configure it to integrate with PingAccess.
Steps
-
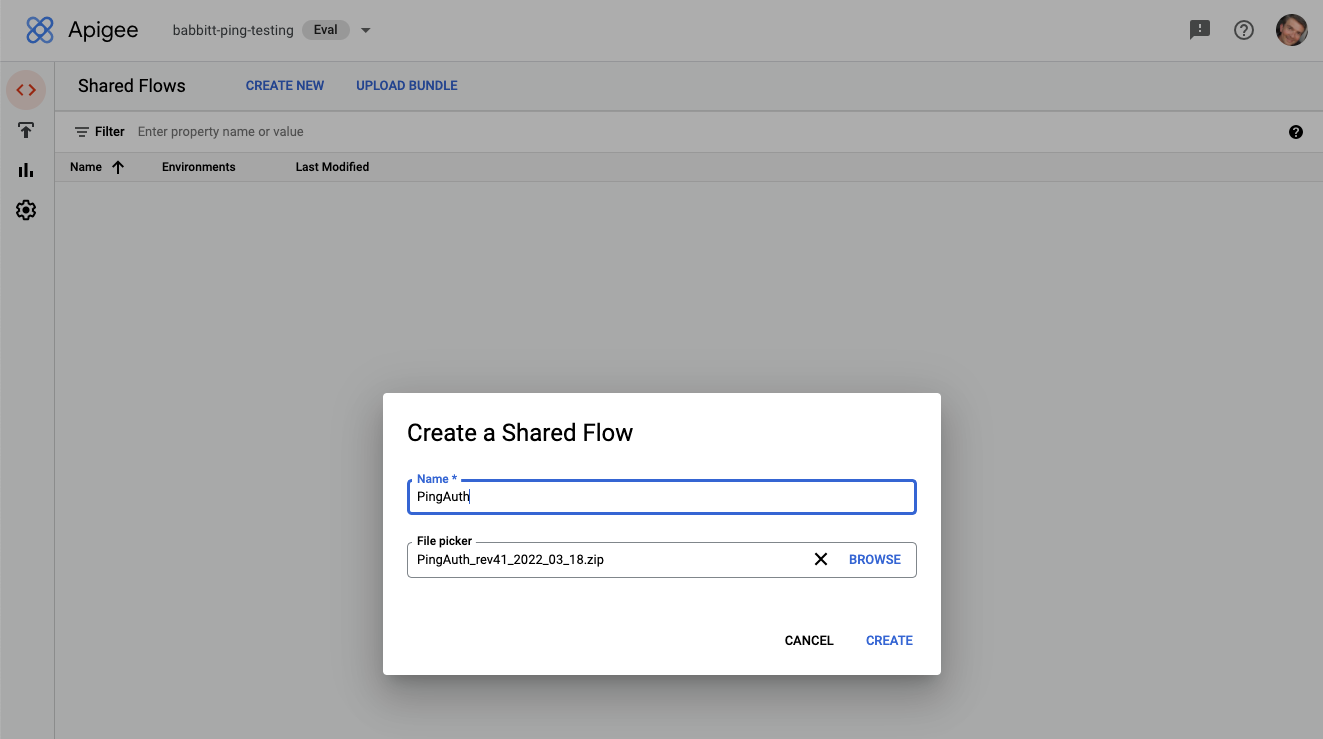
Upload the shared flow bundle.
Choose from:
-
If you’re using Apigee X, go to Develop > Shared Flows and click Upload Bundle. Upload the PingAuth shared flow
.zipfile, and name the shared flowPingAuth. -
If you’re using Apigee Edge or Apigee Private Cloud, click Shared Flow, then click Upload Bundle. Upload the PingAuth shared flow bundle
.zipfile, and name the shared flowPingAuth.
-
-
If you’re using Apigee X, configure the connection to PingAccess.
Unlike Apigee Edge, Apigee X doesn’t currently support managing the configuration values stored in key value maps in the Apigee interface. You must add these configuration values to the key value map policy. The key value map is created and the configuration values are added the first time the PingAuth shared flow is executed at runtime.
-
Go to the PingAuth shared flow at Develop > Shared Flows > PingAuth.
-
Click the Develop tab and examine Revisions to make sure you are on the latest revision.
-
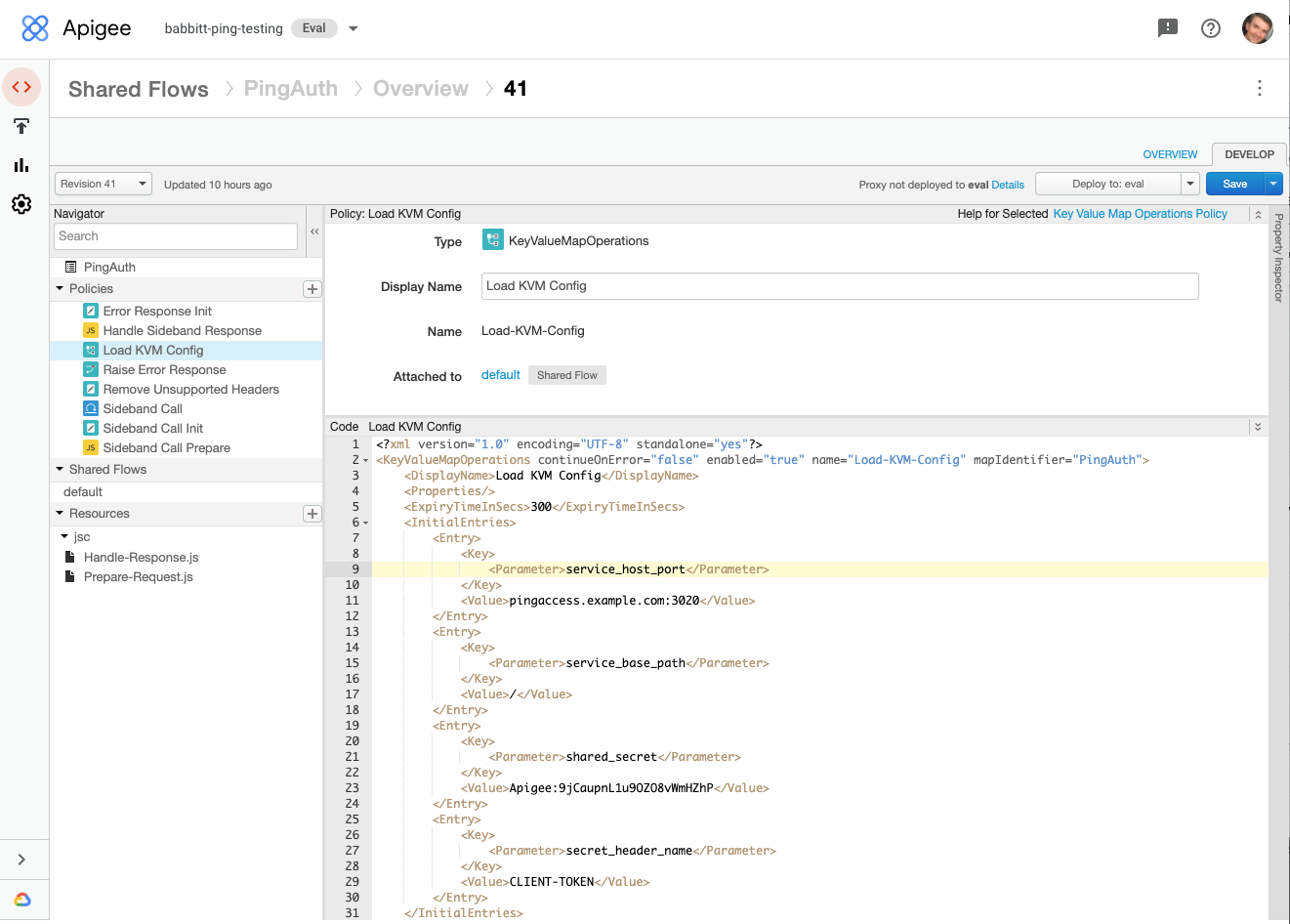
In the Policies panel on the left, click the Load KVM Config policy.
-
In the policy editor panel, remove the comment lines above and below the
InitialEntrieselement. -
Edit the values for
service_host_portandshared_secretto match the values that you obtained in the previous procedure, Configuring PingAccess for Apigee integration. -
Click Save.
-
-
If you’re using Apigee Edge or Apigee Private Cloud, configure the connection to PingAccess.
Apigee Edge stores environment-specific configuration values in key value maps so that the same policies can be used across multiple deployment environments without any changes to the policies.
-
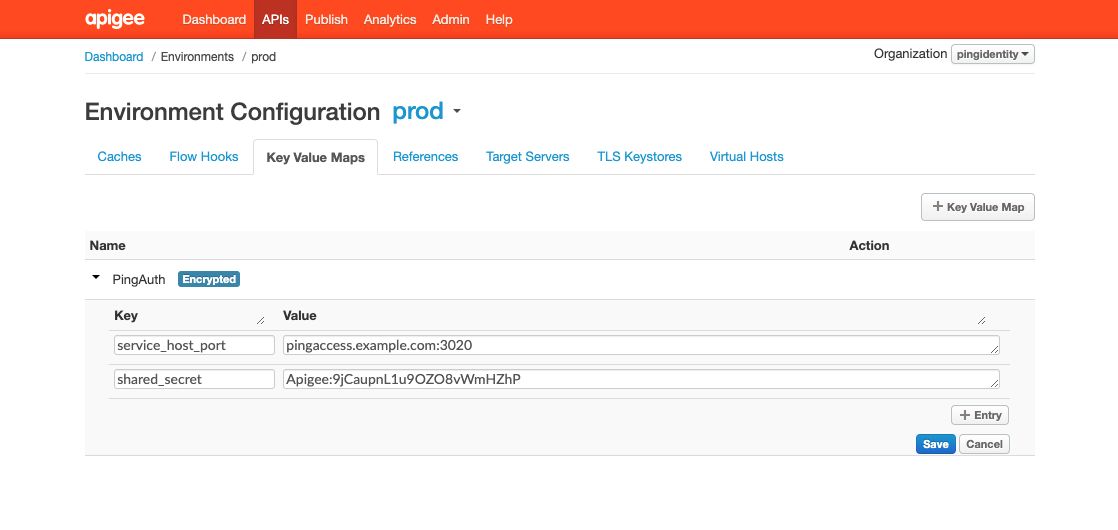
Go to Environment > Key Value Maps and click Key Value Map.
-
Edit the key value map and click Add Entry. Use the key names
service_host_portandshared_secret, and set the values to match the ones that you obtained in the previous procedure, Configuring PingAccess for Apigee integration. -
Click Save.
-
-
(Optional) Configure HTTPS trust for PingAccess.
By default, the PingAuth shared flow is configured to trust the PingAccess Sideband Listener HTTPS certificates only if they’re issued from a well-known CA. To trust specific HTTPS certificates for PingAccess servers:
-
Go to the PingAuth shared flow at Develop > Shared Flows > PingAuth.
-
Click the Develop tab and examine Revisions to make sure you are on the latest revision.
-
In the Policies section of the Navigator, click the Sideband Call policy.
-
In the policy editor panel, remove the comment characters surrounding the
TrustStoreelement.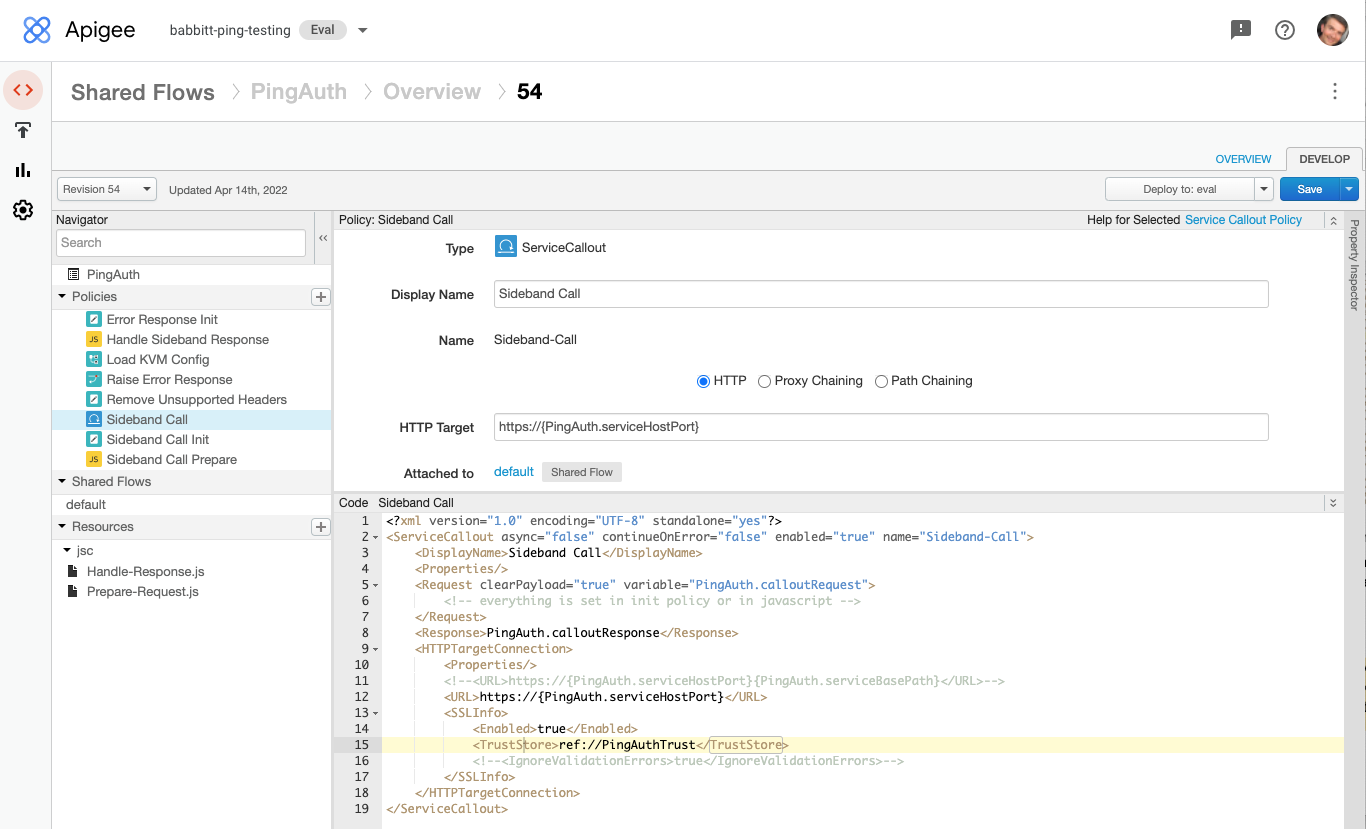
-
Click Save.
-
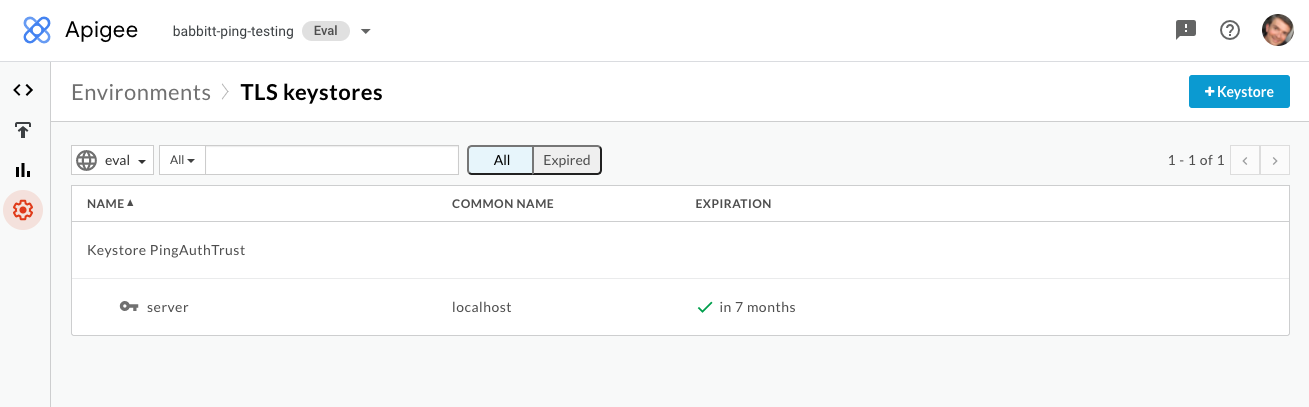
Go to Environment > TLS Keystores and click Keystore.
-
Give the key store a name that helps you identify your PingAccess environment, such as
PingAccess-dev-truststore. -
Click to add a certificate, give the certificate an alias, and upload the certificate that you obtained earlier. Click Save.
-
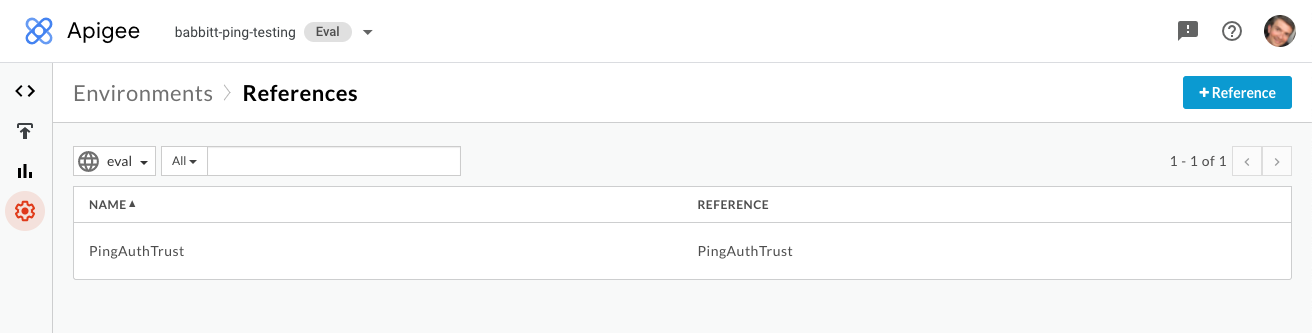
Go to Environment > References and click +Reference.
-
In the Name field, enter
PingAuthTrust. -
Select the key store you created earlier, then click Save.
-
-
Deploy the shared flow:
-
Go to Develop > Shared Flows > PingAuth.
-
Deploy the most recent revision of the shared flow to your environment.
-