Web Access Management Agent proof of concept deployment architecture
This proof of concept deployment environment emulates a Web Access Management (WAM) agent production environment for testing purposes.
In the test environment, PingAccess can be set up with the minimum hardware requirements. This environment example does not provide high availability and is not recommended in production.
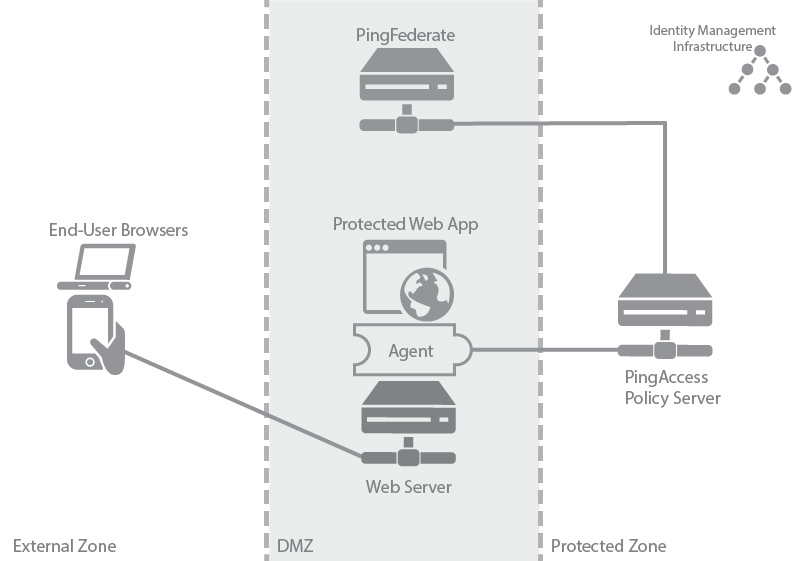
The following table describes the three zones within this proposed architecture.
| Zone | Description |
|---|---|
External Zone |
External network where incoming requests for web applications originate. |
DMZ |
Externally exposed segment where application web server is accessible to web clients. PingAccess agent is deployed as a plugin on this web server. The agent interacts with PingAccess policy server in the protected zone. PingFederate is deployed as a standalone instance in this environment because during user authentication clients interact with PingFederate. PingFederate requires access to identity management infrastructure to authenticate users. |
Protected Zone |
Backend controlled zone with no direct access by web clients. PingAccess policy server is deployed in this zone. PingAccess interacts with PingFederate in the DMZ zone. Identity management infrastructure is deployed in this zone. |