Maintenance
This guide covers how to perform maintenance tasks in ForgeRock Access Management such as backing up and restoring, monitoring, and others.
This guide is written for anyone that sets up and maintains Access Management services for their organizations. This guide covers tasks and configurations you might repeat throughout the life cycle of a deployment in your organization.
ForgeRock® Identity Platform serves as the basis for our simple and comprehensive Identity and Access Management solution. We help our customers deepen their relationships with their customers, and improve the productivity and connectivity of their employees and partners. For more information about ForgeRock and about the platform, see https://www.forgerock.com.
Back up configurations
During normal production operations, you rely on directory replication to maintain multiple, current copies of AM’s configuration. To recover from the loss of a server or from a serious administrative error, back up directory data and configuration files.
To back up your external configuration directory server, refer to Backup and Restore in the DS documentation.
Back up instance configuration data
This procedure backs up the configuration files stored with the server. You can restore this backup when rebuilding a failed server.
Consider the following when using this procedure:
-
Refer to the documentation for your external directory server or work with your directory server administrator to back up and restore configuration data stored in the directory server.
For more information about Directory Services, refer to Backup and restore in the DS documentation.
-
Do not restore configuration data from a backup of a different major version of AM. The structure of the configuration data can change from release to release.
Follow these steps for each AM server that you want to back up:
-
Stop AM or the container in which it runs.
-
Back up AM server files.
This example uses the default configuration location, and excludes logs.
$HOMEis the home directory of the user who runs the web container where AM is deployed. AM is deployed in Apache Tomcat underopenam:$ cd $HOME $ zip -r AM-config-dir-backup-`date -u +%F-%H-%M`.zip openam .openamcfg/* \ -x openam/var/debug/* openam/var/audit/* openam/var/stats* openam/opends/* … $ ls AM-config-dir-backup-*.zip AM-config-dir-backup-2022-10-01-05-07-50.zipbash -
Start AM or the container in which it runs.
Monitor AM instances
AM provides a number of interfaces for you to check the status of AM instances and to gather monitoring data. This section describes the steps to enable monitoring and use the monitoring endpoints.
Check the status of an AM instance
In certain deployments, such as Kubernetes, it can be useful to poll endpoints to check if an instance is running, and ready to handle requests. You can determine the status of an AM instance by using the following endpoints:
/json/health/live-
Use the
liveendpoint to determine if AM instances are up and running.If the instance is running the endpoint returns an HTTP status code of
200. If not, it returns a503response.For example, use the following
curlcommand to determine when an AM instance is alive:$ curl --include --retry 10 --retry-connrefused 'http://am.example.com:8080/am/json/health/live' Warning: Transient problem: connection refused Will retry in 1 seconds. 10 Warning: retries left. Warning: Transient problem: connection refused Will retry in 2 seconds. 9 Warning: retries left. Warning: Transient problem: connection refused Will retry in 4 seconds. 8 Warning: retries left. HTTP/1.1 200 X-Frame-Options: SAMEORIGIN X-Content-Type-Options: nosniff Cache-Control: private Content-API-Version: resource=1.0 Content-Length: 0 Date: Mon, 09 Nov 2020 12:22:38 GMTbash /json/health/ready-
Use the
readyendpoint to determine if AM instances are ready to process requests.If the instance is ready to process requests, the endpoint returns an HTTP status code of
200. If not, it returns a503response.For example, use the following
curlcommand to determine when an AM instance is ready to process requests:$ curl --include --retry 10 --retry-connrefused 'http://am.example.com:8080/am/json/health/ready' Warning: Transient problem: connection refused Will retry in 1 seconds. 10 Warning: retries left. Warning: Transient problem: connection refused Will retry in 2 seconds. 9 Warning: retries left. Warning: Transient problem: connection refused Will retry in 4 seconds. 8 Warning: retries left. Warning: Transient problem: connection refused Will retry in 8 seconds. 7 Warning: retries left. HTTP/1.1 200 X-Frame-Options: SAMEORIGIN X-Content-Type-Options: nosniff Cache-Control: private Content-API-Version: resource=1.0 Content-Length: 0 Date: Mon, 09 Nov 2020 12:45:03 GMTbash
Deprecated isAlive.jsp page
AM provides a deprecated isAlive.jsp page, to check whether AM is up.
Point your application to the file under the deployment URL,
such as https://openam.example.com:8443/openam/isAlive.jsp.
If you get a success code (with Server is ALIVE: in the body of the page returned), then the instance is in operation.
The isAlive.jsp page is deprecated and will be removed in a future release.
Update your environment to use the live and ready endpoints instead.
|
The endpoints and |
JMX monitoring
You can configure AM to let you listen for Java Management eXtension (JMX) clients, by default on port 9999.
Either go to Configure > Global Services > Monitoring in the AM admin UI
and make sure both Monitoring Status and Monitoring RMI interface status are enabled,
or use the ssoadm command:
$ ssoadm \
set-attr-defs \
--servicename iPlanetAMMonitoringService \
--schematype Global \
--adminid uid=amAdmin,ou=People,dc=openam,dc=forgerock,dc=org \
--password-file /tmp/pwd.txt \
--attributevalues iplanet-am-monitoring-enabled=true \
iplanet-am-monitoring-rmi-enabled=trueA number of tools support JMX, including jvisualvm and jconsole.
When you use jconsole to browse AM MBeans for example,
the default URL for the AM running on the local system is service:jmx:rmi:///jndi/rmi://localhost:9999/server.
$ jconsole service:jmx:rmi:///jndi/rmi://localhost:9999/server &To browse MBeans, connect to your web application container, and go to the AM MBeans. By default, JMX monitoring for the container is likely to be accessible only locally, using the process ID.
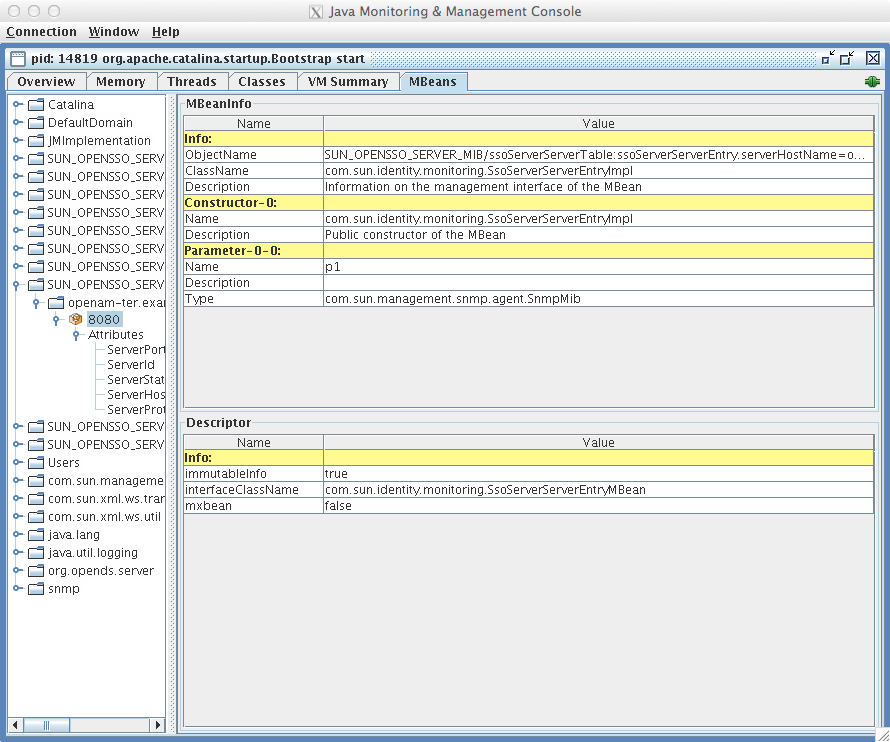
Also refer to Monitoring and Management Using JMX for instructions on how to connect remotely, how to use SSL, and so on.
|
JMX has a limitation in that some Operations and CTS tables cannot be properly serialized from AM to JMX. As a result, only a portion of AM’s monitoring information is available through JMX. ForgeRock recommends using Prometheus, Graphite, or Common REST monitoring. |
For monitoring metrics reference, refer to Monitoring metrics.
Monitor with Prometheus
Prometheus is third-party software used for gathering and processing monitoring data. AM exposes an endpoint which Prometheus uses to gather metrics from the AM instance. For more information about installing and running Prometheus, refer to the Prometheus documentation.
When enabled, AM makes the Prometheus-formatted metrics available at the /json/metrics/prometheus endpoint.
Configure Prometheus to monitor the AM endpoint, using the prometheus.yml configuration file.
For more information on configuring Prometheus, refer to the
Prometheus configuration documentation.
|
Prometheus provides monitoring and processing for the information provided by AM, but further analysis and visualization may be desired. In this case, you can use tools such as Grafana to create customized charts and graphs based on the information collected by Prometheus. For more information on installing and running Grafana, refer to the Grafana website. |
For monitoring metrics reference, refer to Monitoring metrics.
Enable Prometheus monitoring
-
Ensure you have enabled monitoring.
-
Go to Configure > Global Services > Monitoring.
-
On Secondary Configurations tab, click
prometheus, then select Enabled. -
In the Authentication Type drop-down menu, select one of the following options:
-
None. Prometheus does not need to authenticate when accessing the endpoint.
-
HTTP Basic. Prometheus must authenticate using a username and a password when accessing the endpoint.
-
-
If Prometheus must authenticate when accessing the endpoint, specify the Username and Password that it will use.
-
Save your work.
Common REST monitoring
Common REST is the ForgeRock® Common REST framework. AM exposes an endpoint that lets REST clients gather information about your AM installation in JSON format.
When enabled, AM makes the Common REST-formatted metrics
available at the /json/metrics/api endpoint.
For example, to query all monitoring metrics:
$ curl \
--request GET \
--header 'Content-Type: application/json' \
--header 'iPlanetDirectoryPro: P8Eri6d…xAAA.*' \
'https://openam.example.com:8443/openam/json/metrics/api?_queryFilter=true&_prettyPrint=true'
{
"result" : [ {
"_id" : "session.authentication-client-based.get-matching-sessions.failure",
"count" : 0,
"max" : 0.0,
"mean" : 0.0,
"min" : 0.0,
"p50" : 0.0,
"p75" : 0.0,
"p95" : 0.0,
"p98" : 0.0,
"p99" : 0.0,
"p999" : 0.0,
"stddev" : 0.0,
"m15_rate" : 0.0,
"m1_rate" : 0.0,
"m5_rate" : 0.0,
"mean_rate" : 0.0,
"duration_units" : "milliseconds",
"rate_units" : "calls/second",
"total" : 0.0,
"_type" : "timer"
},
…To output values for a specific metric, use the format /json/metric/api/metric name.
For example:
$ curl \
--request GET \
--header 'Content-Type: application/json' \
--header 'iPlanetDirectoryPro: P8Eri6d…xAAA.*' \
'https://openam.example.com:8443/openam/json/metrics/api/authentication.success'
{
"_id":"authentication.success",
"m15_rate":2.3882880682497324E-4,
"m1_rate":1.0818067450729532E-12,
"m5_rate":3.057223961594952E-5,
"mean_rate":1.072595825176473E-4,
"units":"events/second",
"total":9.0,
"count":9,
"_type":"summary"
}For monitoring metrics reference, refer to Monitoring metrics.
Enable the Common REST monitoring interface
-
Ensure you have enabled monitoring.
-
Go to Configure > Global Services > Monitoring.
-
On the Secondary Configurations tab, click
crest. -
Set CREST to Enabled.
-
Click Save Changes.
Graphite monitoring
Graphite is third-party software used for storing monitoring data, and rendering graphs of the data. For more information about installing and running Graphite, see the Graphite documentation.
For monitoring metrics reference, refer to Monitoring metrics.
Enable the Graphite monitoring interface
-
Ensure you have enabled monitoring.
-
Go to Configure > Global Services > Monitoring.
-
On the Secondary Configurations tab, click Add a Secondary Configuration.
-
Select Graphite Reporter.
-
Specify the Name and Hostname of the Graphite instance to push the metrics data to.
-
Click Create.
MBean monitoring (legacy)
|
This functionality is labelled as legacy. |
You can configure AM to let you access a web based view of AM MBeans on port 8082
where the core server runs, such as http://openam.example.com:8082/.
Either use the console (Configure > Global Services > Monitoring), or use the ssoadm command:
$ ssoadm \
set-attr-defs \
--servicename iPlanetAMMonitoringService \
--schematype Global \
--adminid uid=amAdmin,ou=People,dc=openam,dc=forgerock,dc=org \
--password-file /tmp/pwd.txt \
--attributevalues iplanet-am-monitoring-http-enabled=trueThe default authentication file lets you authenticate over HTTP as user demo, password Ch4ng31t.
The user name and password are kept in the file specified, with the password encrypted:
$ cat openam/security/openam_mon_auth
demo AQICMBCKlwx6G3vzK3TYYRbtTpNYAagVIPNPYou can encrypt a new password using the ampassword command.
After changing the authentication file, you must restart AM for the changes to take effect.
SNMP monitoring
|
The interface stability of this legacy feature is deprecated. |
SNMP depends on labels known as Object Identifiers (OIDs).
These are uniquely defined labels, organized in tree format.
For AM, they are configured in a .mib file named FORGEROCK-OPENAM-CTS.mib,
found inside the /path/to/tomcat/webapps/openam/WEB-INF/lib/openam-mib-schema-<version>.jar file
of the AM deployment.
For detailed information on configured OIDs, refer to SNMP CTS object identifiers.
With the OIDs in hand, you can set up an SNMP server to collect the data. You would also need SNMP utility commands with associated OIDs to measure the current state of a component.
Enable SNMP monitoring
-
Stop the AM instance or the container where it runs.
-
Download the AM ZIP file from the ForgeRock BackStage download site.
-
Extract the contents of the ZIP file.
-
Go to the
/snmpfolder, and run theopendmk.jarinstaller file. For example:$ java -jar opendmk.jarbash -
Accept the License Agreement.
-
Select the directory you want to install to.
For example:
/tmp/opendmk. -
Copy the
jdmkrt.jarfile from the/libfolder of the extracted archive to the AM/WEB-INF/libfolder.For example:
$ cp /tmp/opendmk/OpenDMK-bin/lib/jdmkrt.jar /path/to/openam.war/WEB-INF/libbash -
Restart the AM instance or the container in which it runs.
-
Go to Configure > Global Services > Monitoring.
-
Set Monitoring Status to
enabled. -
Set Monitoring SNMP interface status to
enabled.By default, AM listens on port 8085 for SNMP monitoring.
-
Save your work.
-
Restart the AM instance for the change to take effect.
Once enabled, SNMP monitoring works over UDP by default. You may want to install one of many available network monitoring tools. For the purpose of this section, basic SNMP service and monitoring tools have been installed on a Unix-like system.
First, to verify the operation of SNMP on a GNU/Linux system, run the following command over port 8085 using SNMP version 2c:
# snmpstatus -c public -v 2c localhostThe output should specify communications over UDP.
If you get a timeout message, the SNMP service may not be running.
You can get the value for a specific OID. For example, the following command retrieves the cumulative count for CTS create operations, over port 8085:
# snmpget -c public -v 2c :8085 enterprises.36733.1.2.3.3.1.1.1If your version of the tool does not support the enterprises OID string,
use 1.3.6.1.4.1 instead, as in 1.3.6.1.4.1.36733.1.2.3.3.1.1.1.
For one view of the tree of OIDs, you can use the snmpwalk command.
For example, the following command lists all OIDs related to CTS:
# snmpwalk -c public -v 2c :8085 enterprises.36733.1.2.3A number of CTS OIDs are listed with a Counter64 value.
As defined in RFC 2578,
an OID so configured has a maximum value of 264 - 1.
SNMP monitoring for sessions
You can monitor server-side session statistics over SNMP. AM records statistics for up to a configurable number of recent sessions. (You can configure the number in the AM admin UI under Configuration > System > Monitoring. For details, refer to the system configuration reference section, Monitoring.)
SNMP uses OIDs defined in a .mib file that specifies the statistics
AM keeps for policy evaluation operations, the FORGEROCK-OPENAM-SESSION.mib file.
This file is found inside the /path/to/tomcat/webapps/openam/WEB-INF/lib/openam-mib-schema-<version>.jar file
of the AM deployment.
When monitoring is active, AM records statistics about both the numbers of internal, remote, and CTS sessions, and also the times taken to process sessions.
The statistics are all read-only. The base OID for session statistics is enterprises.36733.1.2.1.
Times are expressed in nanoseconds rather than milliseconds, as many operations take less than one millisecond.
The following table describes the values that you can read:
| OID | Description | Syntax |
|---|---|---|
|
Total number of current internal sessions |
|
|
Average time it takes to refresh an internal session |
|
|
Average time it takes to logout an internal session |
|
|
Average time it takes to destroy an internal session |
|
|
Average time it takes to set a property on an internal session |
|
|
Total number of current remote sessions |
|
|
Average time it takes to refresh a remote session |
|
|
Average time it takes to logout a remote session |
|
|
Average time it takes to destroy a remote session |
|
|
Average time it takes to set a property on a remote session |
|
|
Total number of sessions currently in the Core Token Service (CTS) |
|
|
Average time it takes to refresh a CTS session |
|
|
Average time it takes to logout a CTS session |
|
|
Average time it takes to destroy a CTS session |
|
|
Average time it takes to set a property on a CTS session |
|
|
Total number of client-side sessions (always returns |
|
|
Average time it takes to refresh a client-side session |
|
|
Average time it takes to logout a client-side session |
|
|
Average time it takes to destroy a client-side session |
|
|
Average time it takes to set a property on a client-side session |
|
(1) Full SNMP monitoring functionality is not available for client-side sessions, because client-side sessions cannot monitor active sessions.
SNMP monitoring for policy evaluation
You can monitor policy evaluation performance over SNMP. AM records statistics for up to a number of recent policy evaluation requests. (You can configure the number in the AM admin UI under Configuration > System > Monitoring.) For details, refer to Monitoring.
SNMP uses OIDs defined in the .mib file, FORGEROCK-OPENAM-POLICY.mib,
found inside the /path/to/tomcat/webapps/openam/WEB-INF/lib/openam-mib-schema-<version>.jar file
of the AM deployment.
This file specifies the statistics AM keeps for policy evaluation operations.
When monitoring is active, AM records statistics about the numbers and rates of policy evaluations performed, and the time taken to process policy evaluations.
The statistics are all read-only.
The base OID for policy evaluation statistics is enterprises.36733.1.2.2.1.
The following table describes the values that you can read:
| OID | Description | Syntax |
|---|---|---|
|
Cumulative number of policy evaluations for specific resources (self) |
|
|
Average rate of policy evaluations for specific resources (self) |
|
|
Minimum rate of policy evaluations for specific resources (self) |
|
|
Maximum rate of policy evaluations for specific resources (self) |
|
|
Cumulative number of policy evaluations for a tree of resources (subtree) |
|
|
Average rate of policy evaluations for a tree of resources (subtree) |
|
|
Minimum rate of policy evaluations for a tree of resources (subtree) |
|
|
Maximum rate of policy evaluations for a tree of resources (subtree) |
|
|
Average length of time to evaluate a policy for a specific resource (self) |
|
|
Slowest evaluation time for a specific resource (self) |
|
|
Average length of time to evaluate a policy for a tree of resources (subtree) |
|
|
Slowest evaluation time for a tree of resources (subtree) |
|
|
Slowest individual policy evaluation time overall |
|
Change host names
Changing AM host names involves the following high-level steps:
-
Add the new host name to the Realm/DNS Aliases list.
-
Export, edit, then import the configuration.
This step relies on the
ssoadmcommand, which you install separately from AM as described in Set up administration tools. -
Stop AM and edit configuration files.
-
Remove the old host name from the Realm/DNS Aliases list.
Before you start, make sure you have an up to date backup of your installation. See Back up configurations for instructions.
Add the new host name as an alias
-
In the AM admin UI, go to Realms > Realm Name and click Properties.
-
Add the new host name to the Realm/DNS Aliases list, and save your work.
Export, edit, and import the service configuration
-
Export the service configuration:
$ ssoadm \ export-svc-cfg \ --adminid uid=amAdmin,ou=People,dc=openam,dc=forgerock,dc=org \ --encryptsecret myEncryptSecretString1234 \ --password-file /tmp/pwd.txt \ --outfile config.xml Service Configuration was exported.bashAM uses the value entered in
--encryptsecretto encrypt passwords stored in the backup file. It can be any value, and is required when restoring a configuration. -
Edit the service configuration file:
-
Change the fully qualified domain name, such as
openam.example.com, throughout the file. -
If you are changing the context path, such as
/openam, make the following changes:-
Change the value of
com.iplanet.am.services.deploymentDescriptor. -
Change contextPath in the value of the
propertiesViewBeanURL="contextPath/auth/ACServiceInstanceList". -
Change contextPath in the value of
propertiesViewBeanURL="contextPath/auth/ACModuleList". -
Change the context path in a
<Value>element that is a child of an<AttributeValuePair>element. -
Change the context path where it occurs throughout the file in the full URL to AM, such as
http://openam.example.com:8080/contextPath.
-
-
If you are changing the port number, change the value of
com.iplanet.am.server.port.Also change the port number in
host:portcombinations throughout the file. -
If you are changing the domain name, change the cookie domain, such as
<Value>.example.com</Value>, throughout the file.
-
-
Import the updated service configuration:
$ ssoadm \ import-svc-cfg \ --adminid uid=amAdmin,ou=People,dc=openam,dc=forgerock,dc=org \ --encryptsecret myEncryptSecretString1234 \ --password-file /tmp/pwd.txt \ --xmlfile config.xml Directory Service contains existing data. Do you want to delete it? [y\|N] y Please wait while we import the service configuration… Service Configuration was imported.bash
Edit configuration files for the new host name
-
Stop AM or the web container where it runs.
-
Edit the boot properties file, such as
/home/user/openam/boot.json, changing the fully qualified domain name (FQDN), port, and context path for AM as necessary. -
If you are changing the context path, move the folder containing AM configuration, such as
/home/user/openam/, to match the new context path, such as/home/user/openam2/. -
If you are changing the location or context path, change the name of the file in the
/home/user/.openamcfgfolder, such asAMConfig_path_to_tomcat_webapps_openam_, to match the new location and context path.Also edit the path name in the file to match the change you made when moving the folder.
-
Restart AM or the web container where it runs.
Tune AM
This page covers key AM tuning strategies to ensure performant access and federation management, and to maximize throughput while minimizing response times.
|
The recommendations provided here are guidelines for your testing rather than hard and fast rules for every situation. Said another way, the fact that a given setting is configurable implies that no one setting is right in all circumstances. The extent to which performance tuning advice applies depends to a large extent on your requirements, on your workload, and on what resources you have available. Test suggestions before rolling them out into production. |
The suggestions in this page apply to AM deployments with the following characteristics:
-
The deployment has a dedicated DS server for the Core Token Service. The host running this directory server is a high-end server with a large amount of memory and multiple CPUs.
-
The AM server is configured to use server-side sessions.
The following table summarizes the high-level tasks required to tune an AM instance:
| Task | Resources |
|---|---|
Tune general AM settings |
|
Tune connectivity to LDAP data stores |
|
Tune the JVM where AM runs |
|
Tune the configuration and user cache |
Tuning server settings
AM has a number of settings that can be tuned to increase performance.
Logging settings
The following general points apply:
-
Set debug logging level to
error. -
Set container-level logging to a low level, such as
errororsevere.
Notification settings
AM has two thread pools used to send notifications to clients. The Service Management Service (SMS) thread pool can be tuned in the AM admin UI, under Configure > Server Defaults > SDK > Data Store:
| Property | Default value | Suggestions |
|---|---|---|
Notification Pool Size |
1 |
Specifies the size of the thread pool used to send notifications.
A value of ( |
The session service has its own thread pool to send notifications to listeners about changes to server-side sessions. This is configured under Configure > Server Defaults > Session > Notification:
| Property | Default value | Suggestions |
|---|---|---|
Notification Pool Size |
10 |
This is the size of the thread pool used to send notifications. In production this should be around 25-30. ( |
Notification Thread Pool Threshold |
5000 |
This is the maximum number of notifications in the queue waiting to be sent. The default value should be fine in the majority of installations. ( |
Session settings
The Session service has additional properties to tune, which are configured under Configure > Server Defaults > Session > Session Limits. The following suggestion applies to deployments using server-side sessions:
| Property | Default Value | Suggestion |
|---|---|---|
Maximum Session Cache Size |
5000 |
Maximum number of AM sessions to cache on the server. In production, this value can safely be set into the 100,000s. The maximum session cache size is really controlled by the maximum size of the JVM heap which must be tuned appropriately to match the desired session cache size. ( |
Policy evaluation settings
The AM policy engine places policies for evaluation on a queue in batches.
Use ssoadm to optimize performance evaluation throughput by configuring the number
of threads available for this queue.
This example increases the number of threads from the default value of 10 to 20:
./ssoadm set-entitlement-conf -u <admin_id> -f <password_file> -a evalThreadSize=20
For more information about this command, refer to set-entitlement-conf.
Tune LDAP connectivity
AM instances use pools of connections when communicating to LDAP data stores. You can tune these connection pools to improve performance, and help with load balancing in the case of failover.
AM provides a global timeout setting for connections in a pool, and each store has properties for the maximum pool size, and in some cases, the minimum pool size.
AM will attempt to use as few connections to LDAP data stores as possible, down to the minimum pool value, if specified. Under heavy load, AM creates additional connections to the configured data stores, up to the maximum pool value. These connections are made to any of the available LDAP data stores that are configured for the relevant purpose.
When the load begins to drop, some of those connections become idle. If a connection is idle for longer than the configured connection idle time, AM closes the connection, until any specified minimum pool size is reached.
By closing idle connections and recreating them when needed, AM balances connections across all available LDAP servers, rather than keeping the entire pool connected to a single server.
Tuning the connection pool settings can increase performance, or make AM more responsive to LDAP data store outages.
Configure connection pool timeouts
-
To configure the timeout used for connections to LDAP stores:
-
Open the
bootstrapConfig.propertiesfile in the AM classpath; for example, in/path/to/tomcat/webapps/openam/WEB-INF/classes/. -
Add, or update the following property, and set the idle timeout, in seconds:
com.sun.am.ldap.connection.idle.seconds=300properties
-
-
You must also configure the setting in the Advanced section of the server defaults, as follows:
-
In the AM admin UI, go to Configure > Server Defaults > Advanced.
-
Add, or edit the following property, and set the idle timeout, in seconds:
com.sun.am.ldap.connection.idle.seconds=300properties
-
-
Restart AM or the container in which it runs for these changes to take effect.
After configuring the timeout for the stores, set the pool sizes assigned to the different stores in the AM admin UI:
Tune configuration store LDAP connections
To change LDAP configuration store settings, go to Deployment > Servers > Server Name > Directory Configuration.
| Setting | Default value | Details |
|---|---|---|
Minimum Connection Pool |
1 |
Property: |
Maximum Connection Pool |
10 |
The default value of Property: |
Tune CTS store LDAP connections
You can increase the number of connections used for connecting to the CTS to increase throughput.
The default maximum number of connections to the CTS is 100.
To change the default, go to Deployment > Servers > Server Name > CTS > CTS Token Store,
and set the Max Connections property.
You may need to click the Inherit value property to unlock the value for editing.
|
You can also edit the |
If you need to change the default CTS connection timeout, go to Deployment > Servers > Server Name > Advanced
and set the org.forgerock.services.datalayer.connection.timeout.cts.async property.
Most CTS requests to the directory server are handled quickly, so the default timeout of 10 seconds is suitable in most cases.
You must restart AM or the container in which it runs for these changes to take effect.
Tune external policy and applications store LDAP connections
To change external policy and application data store settings, go to Configure > Global Services > External Data Stores > Secondary Configurations > Store Name.
|
Policy and application data is stored in the configuration data store if not configured separately. To manage the configuration store connection pool, refer to Tune configuration store LDAP connections. |
| Setting | Default value | Information |
|---|---|---|
Minimum Connection Pool Size |
1 |
Must be less than the maximum size to allow reaping to function. Property: |
Maximum Connection Pool Size |
10 |
Property: |
Tune identity store LDAP connections
To change LDAP data store settings, go to Realms > Realm Name > Identity Stores > Identity Store Name. Each store has its own connection pool, so each store needs its own tuning:
| Setting | Default value | Details |
|---|---|---|
LDAP Connection Pool Minimum Size |
1 |
A good tuning value for this property is 10. Property: |
LDAP Connection Pool Maximum Size |
10 |
The maximum LDAP connection pool size; a high tuning value for this property is 65, though you might well be able to reduce this for your deployment. Ensure your LDAP server can cope with the maximum number of clients across all the AM servers. Property: |
Tune UMA store LDAP connections
To increase the number of connections used for UMA-related data stores,
go to Deployment > Servers > Server Name > UMA > UMA Store Type, and edit the Max Connections property.
You may need to click the Inherit value property to unlock the value for editing.
|
You can also edit the |
| Setting | Default value | Details |
|---|---|---|
UMA Resource Store > Max Connections |
10 |
Property: |
UMA Audit Store > Max Connections |
10 |
Property: |
Pending Requests Store > Max Connections |
10 |
Property: |
UMA Resource Labels Store > Max Connections |
2 |
Property: |
Tune authentication node/module LDAP connections
To change connection pool settings for the LDAP Decision node and LDAP Authentication Module, go to Configure > Authentication > Core Attributes > Global Attributes.
| Setting | Default value | Details |
|---|---|---|
Default LDAP Connection Pool Size |
1:10 |
The minimum and maximum LDAP connection pool used by the LDAP authentication node/module, separated by a colon (:) character. Use Property: |
Tune JVM settings
This section gives some initial guidance on configuring the JVM for running AM when the deployment has a dedicated CTS token store, and AM is configured to use server-side sessions.
These settings provide a strong foundation to the JVM before a more detailed garbage collection tuning exercise, or as best practice configuration for production:
| JVM parameters | Suggested value | Description |
|---|---|---|
|
At least 1 GB (2 GB with embedded DS), in production environments at least 2 GB to 3 GB. This setting depends on the available physical memory, and on whether a 32- or 64-bit JVM is used. |
|
|
Set both to 256 MB |
Controls the size of the metaspace in the JVM |
|
60000 |
Controls the read timeout in the Java HTTP client implementation. This applies only to the Sun/Oracle HotSpot JVM. |
|
High setting: 30000 (30 seconds) |
Controls the connect timeout in the Java HTTP client implementation When you have hundreds of incoming requests per second, reduce this value to avoid a huge connection queue. This applies only to the Sun/Oracle HotSpot JVM. |
| JVM parameters | Suggested value | Description |
|---|---|---|
|
|
Controls the protocols used for outbound HTTPS connections from AM. Specify one or more of the following values, separated by commas:
This setting applies only to Sun/Oracle Java environments. |
|
|
Controls the protocol AM uses to connect to affected external resources. Specify one or more of the following values, separated by commas:
This setting overrides the default server value. For details, refer to advanced properties. |
| JVM parameters | Suggested value | Description |
|---|---|---|
|
Verbose garbage collection reporting. |
|
|
|
Logs detailed information about garbage collection.
When using the |
|
Out of Memory errors generate a heap dump automatically. |
|
|
|
Location of the heap dump. |
|
Prints a heap histogram when the JVM receives a SIGTERM signal. |
| Module flag | Suggested value | Description |
|---|---|---|
|
|
When running AM with JRE 17, SAML Artifact flows (or any flows that use Xerces SOAP libraries) can fail with the following error:
Set this module flag to avoid this error. |
Tune caching
AM caches data to avoid having to query user and configuration data stores each time it needs the information. By default, AM makes use of LDAP persistent search to receive notification of changes to cached data. For this reason, caching works best when data are stored in a directory server that supports LDAP persistent search.
AM has two kinds of configurable cache on the server side; one for configuration data and one for user data. You can generally use the default settings for configuration data cache. This section covers the configuration choices available for caching user data.
AM implements the global user data cache for its user data stores.
The user data store also supports a DN cache, used to cache DN lookups that tend to occur in bursts during authentication.
The DN cache can become out of date when a user is moved or renamed in the underlying LDAP store, events that are not
always reflected in a persistent search result. You can enable the DN cache when the underlying LDAP store supports
persistent search and mod DN operations (that is, move or rename DN).
The following diagram depicts the two kinds of cache, and also the two types of caching available for user data:
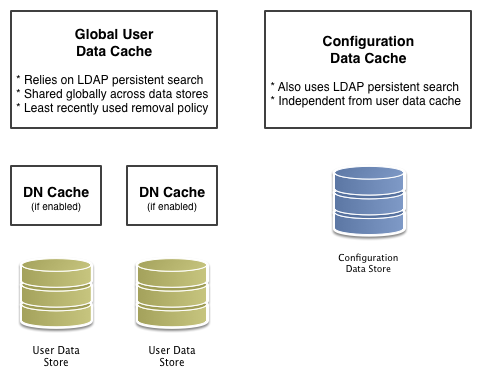
The rest of this page concerns mainly settings for global user data cache and for SDK clients. For a look at data store cache settings, refer to Tune LDAP connectivity.
Overall server cache settings
By default, AM has caching enabled for both configuration data and user data.
This setting is governed by the server property com.iplanet.am.sdk.caching.enabled, which is true by default. If you
set this advanced property to false, you can enable caching independently for configuration data and for user data.
Turn off global user data caching
| Disabling caching can have a severe negative impact on performance. This is because when caching is disabled, AM must query a data store each time it needs data. |
If, however, you have at least one identity store that does not support LDAP persistent search, then you must disable the global cache for user data. Otherwise, user data caches cannot stay in sync with changes to user data entries:
-
In the AM admin UI, go to Deployment > Servers > Server Name > Advanced.
-
Set the value of the
com.iplanet.am.sdk.caching.enabledproperty tofalseto disable caching overall. -
Set the value of the
com.sun.identity.sm.cache.enabledproperty totrueto enable configuration data caching.All supported configuration data stores support LDAP persistent search, so it is safe to enable configuration data caching.
You must explicitly set this property to true, because setting the value of the propertycom.iplanet.am.sdk.caching.enabledtofalsein the previous step disables both user and configuration data caching. -
Save your work.
-
AM starts persistent searches on user data stores when possible(1) in order to monitor changes.
With user data store caching disabled, AM still starts the persistent searches, even though it no longer uses the results.
Therefore, if you disable user data store caching, you should also disable persistent searches on identity stores in your deployment to improve performance.
To disable persistent search on an identity store, go to Realms > Realm Name > Identity Stores > Identity Store Name > Persistent Search Controls and remove the value of the Persistent Search Base DN configuration property (leave it blank).
(1) AM starts persistent searches on user data stores on directory servers that support the psearch control.
Change the maximum size of the global user data cache
With a large user data store and active user base, the number of user entries in cache can grow large.
-
In the AM admin UI, go to Configure > Server Defaults > SDK.
-
Change the value of SDK Caching Maximum Size.
There is no corresponding setting for configuration data, because the number of configuration entries in a large deployment is not likely to grow nearly as large as the number of user entries.
Clear the configuration cache
When you change configuration property values, the old value remains in effect until the affected service is restarted. To avoid having to restart AM when you change a property value, you can clear the configuration cache and force the new property value to take effect.
To clear the configuration cache, send an empty POST request to the /json/cache endpoint with the clear action, for
example:
$ curl \
--request POST \
--header "Content-Type: application/json" \
--header "iplanetDirectoryPro: kYQVVJ2YFCuAe-b1xjm7evGBDkw.AAJTSQACMDEAAlNLABxQS0ZIYzBPeFVWUzBQOTNLaHV0elVQemdqVU09AAR0eXBlAANDVFMAAlMxAAA. " \
--header "Accept-API-Version: resource=1.0" \
--data '{}' \
https://openam.example.com:8443/openam/json/cache?_action=clear
{}Only members of a group with the Realm Admin or Cache Admin privilege can run this operation to clear the cache.
All attempts to access the endpoint are audited, including information about the user that attempted to clear the cache.
Cache settings
The table below provides a quick reference, primarily for user data cache settings.
Notice that many properties for configuration data cache have sm (for Service Management) in their names,
whereas those for user data have idm (for Identity Management) in their names:
| Property | Description | Default | Applies to |
|---|---|---|---|
|
Maximum number of user entries cached. |
10000 |
Server and SDK |
|
Whether to enable caching for both configuration data and also for user data. If If |
|
Server and SDK |
|
How often in minutes the SDK client, such as a web or a Java agent, should poll AM for modified user data entries. The SDK also uses this value to determine the age of the oldest changes requested. The oldest changes requested are 2 minutes older than this setting. In other words, by default the SDK polls for entries changed in the last 3 minutes. Set this to 0 or a negative integer to disable polling. |
1 (minute) |
SDK |
|
How long AM stores a given change to a cached entry, so that clients polling for changes do not miss the change. |
30 (minutes) |
Server only |
|
If Otherwise, set this to |
|
Server and SDK |
|
How many minutes to store a user data entry in the global user data cache. |
30 (minutes) |
Server and SDK |
|
Whether user data entries in the global user data cache should expire over time. |
|
Server and SDK |
|
Whether the SDK client, such as a web or a Java agent, should register a notification listener for user data changes with the AM server. The SDK client uses the URL specified by If notifications cannot be enabled for some reason, then the SDK client falls back to polling for changes. |
|
SDK |
|
If Otherwise, set this to |
|
Server and SDK |
|
Set this to |
|
Server and SDK |
|
Sets the cache size. |
|
Server and SDK |
Debug logging
AM services capture a variety of information in debug logs. Unlike audit log records, debug log records are unstructured. Debug logs contain different types of information that is useful when troubleshooting AM, including stack traces.
AM uses Logback as the handler for debug logging, making it easily customizable. For example, the level of debug log record output is configurable, as is the storage location and format.
AM lets you enable the debug log level for specific classes in the AM code base. This can be useful when you must turn on debug logging in a production system where you want to avoid excessive logging, but must gather messages when you reproduce a problem.
You can choose the level of logging from the following options:
Off-
No debug messages are logged.
Error-
Debug messages signifying that an error has occurred are logged.
This is the default level.
Warning-
Debug messages signifying potentially harmful situations are logged.
Information-
Debug messages that contain coarse-grained information about the status of AM are logged.
Debug-
Debug messages that contain fine-grained information useful for troubleshooting AM are logged.
Trace-
All debug messages are logged.
Create loggers to specify the debug level for a class, and choose where the output is recorded. The logger used by a feature in AM is hierarchical, based on the class that is creating the debug messages. The most specific logger is used, which is the logger whose path most closely matches the class that is creating the log messages.
For example, if you knew there was an issue in an authentication module,
you might enable trace-level debug logging in org.forgerock.openam.authentication.modules.
If you are not sure where the problem lies, you may choose a broader option,
for example org.forgerock.openam.authentication.
The least-specific, catch-all logger is named ROOT.
AM also logs information related to client interactions
using the org.apache.http.wire and org.apache.http.headers appenders.
The information they collect is useful, for example, when you are developing authentication scripts
or when your environment requires STS transformations.
By default, these appenders are always set to the Warning level unless logging is disabled.
For more information,
see the org.forgerock.allow.http.client.debug
advanced server property.
You can configure debug logging temporarily by using the AM admin UI, or you can create a file in the AM classpath with persistent debug configuration.
Temporarily enable debug logging with Logback.jsp
These steps let you temporarily capture debug messages, until the next time AM or the container in which it runs is restarted.
-
In the AM admin UI, go to
Logback.jspin the root context of the AM installation, for examplehttps://openam.example.com:8443/openam/Logback.jsp.No links to this page are provided in the AM admin UI.
Only the
amAdminadministrator account can access theLogback.jsppage and alter the debug settings; delegated administrators do not have access.The page displays all the appenders and their associated debug loggers, for example:
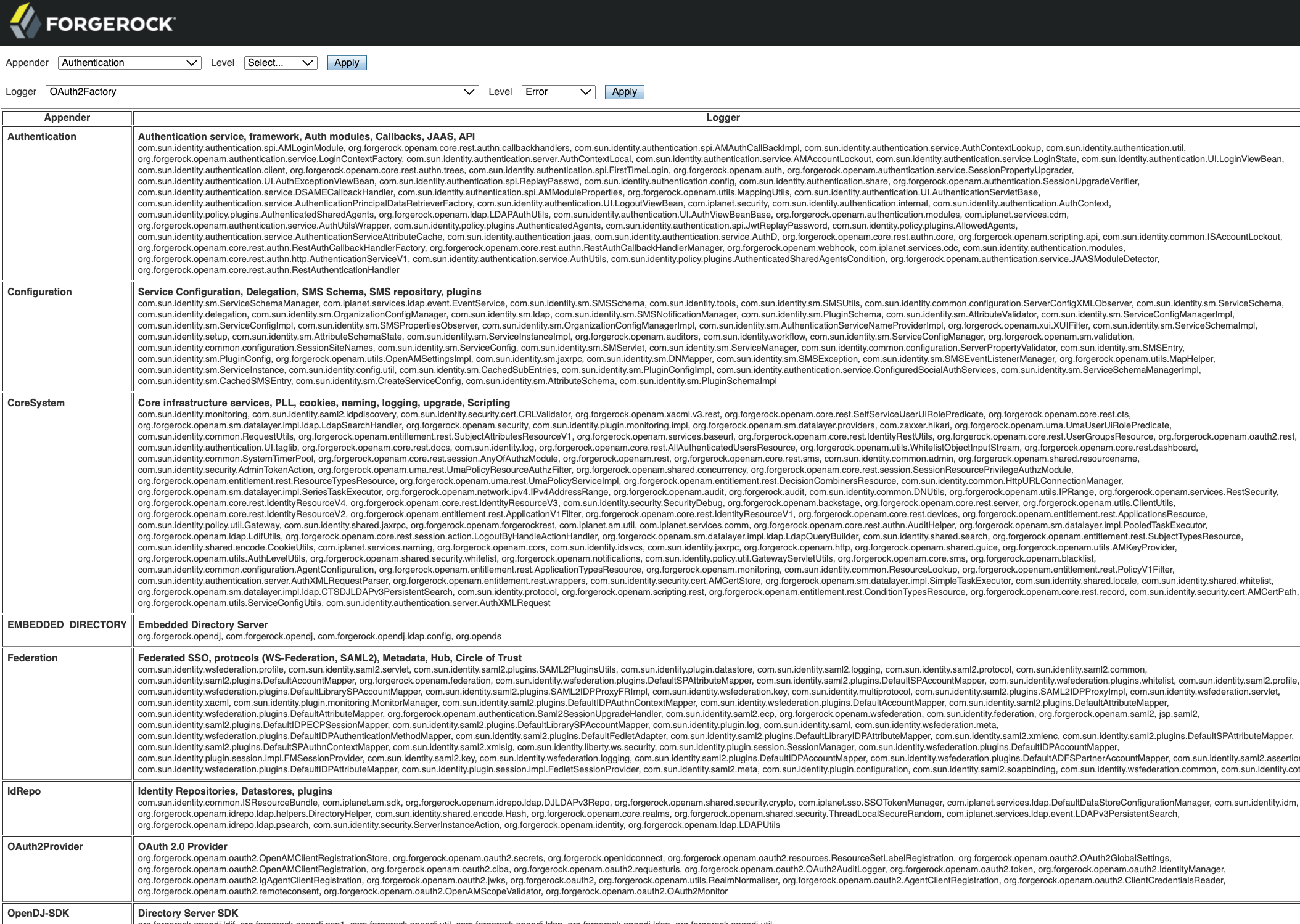
For configuration that defines similar appenders and loggers, refer to the example logback.xml.
Logback.jsp logger names
The following lists contain the available logger names ordered by their associated appender:
Authentication
Authentication service, framework, Auth modules, Callbacks, JAAS, API com.sun.identity.authentication.spi.AMLoginModule, org.forgerock.openam.core.rest.authn.callbackhandlers, com.sun.identity.authentication.spi.AMAuthCallBackImpl, com.sun.identity.authentication.service.AuthContextLookup, com.sun.identity.authentication.util, org.forgerock.openam.authentication.service.LoginContextFactory, com.sun.identity.authentication.server.AuthContextLocal, com.sun.identity.authentication.service.AMAccountLockout, com.sun.identity.authentication.service.LoginState, com.sun.identity.authentication.UI.LoginViewBean, com.sun.identity.authentication.client, org.forgerock.openam.core.rest.authn.trees, com.sun.identity.authentication.spi.FirstTimeLogin, org.forgerock.openam.auth, org.forgerock.openam.authentication.service.SessionPropertyUpgrader, com.sun.identity.authentication.UI.AuthExceptionViewBean, com.sun.identity.authentication.spi.ReplayPasswd, com.sun.identity.authentication.config, com.sun.identity.authentication.share, org.forgerock.openam.authentication.SessionUpgradeVerifier, com.sun.identity.authentication.service.DSAMECallbackHandler, com.sun.identity.authentication.spi.AMModuleProperties, org.forgerock.openam.utils.MappingUtils, com.sun.identity.authentication.UI.AuthenticationServletBase, com.sun.identity.authentication.service.AuthenticationPrincipalDataRetrieverFactory, com.sun.identity.authentication.UI.LogoutViewBean, com.iplanet.security, com.sun.identity.authentication.internal, com.sun.identity.authentication.AuthContext, com.sun.identity.policy.plugins.AuthenticatedSharedAgents, org.forgerock.openam.ldap.LDAPAuthUtils, com.sun.identity.authentication.UI.AuthViewBeanBase, org.forgerock.openam.authentication.modules, com.iplanet.services.cdm, org.forgerock.openam.authentication.service.AuthUtilsWrapper, com.sun.identity.policy.plugins.AuthenticatedAgents, com.sun.identity.authentication.spi.JwtReplayPassword, com.sun.identity.policy.plugins.AllowedAgents, com.sun.identity.authentication.service.AuthenticationServiceAttributeCache, com.sun.identity.authentication.jaas, com.sun.identity.authentication.service.AuthD, org.forgerock.openam.core.rest.authn.core, org.forgerock.openam.scripting.api, com.sun.identity.common.ISAccountLockout, org.forgerock.openam.core.rest.authn.RestAuthCallbackHandlerFactory, org.forgerock.openam.core.rest.authn.RestAuthCallbackHandlerManager, org.forgerock.openam.webhook, com.iplanet.services.cdc, com.sun.identity.authentication.modules, org.forgerock.openam.core.rest.authn.http.AuthenticationServiceV1, com.sun.identity.authentication.service.AuthUtils, com.sun.identity.policy.plugins.AuthenticatedSharedAgentsCondition, org.forgerock.openam.authentication.service.JAASModuleDetector, org.forgerock.openam.core.rest.authn.RestAuthenticationHandler
Configuration
Service Configuration, Delegation, SMS Schema, SMS repository, plugins com.sun.identity.sm.ServiceSchemaManager, com.iplanet.services.ldap.event.EventService, com.sun.identity.sm.SMSSchema, com.sun.identity.tools, com.sun.identity.sm.SMSUtils, com.sun.identity.common.configuration.ServerConfigXMLObserver, com.sun.identity.sm.ServiceSchema, com.sun.identity.delegation, com.sun.identity.sm.OrganizationConfigManager, com.sun.identity.sm.ldap, com.sun.identity.sm.SMSNotificationManager, com.sun.identity.sm.PluginSchema, com.sun.identity.sm.AttributeValidator, com.sun.identity.sm.ServiceConfigManagerImpl, com.sun.identity.sm.ServiceConfigImpl, com.sun.identity.sm.SMSPropertiesObserver, com.sun.identity.sm.OrganizationConfigManagerImpl, com.sun.identity.sm.AuthenticationServiceNameProviderImpl, org.forgerock.openam.xui.XUIFilter, com.sun.identity.sm.ServiceSchemaImpl, com.sun.identity.setup, com.sun.identity.sm.AttributeSchemaState, com.sun.identity.sm.ServiceInstanceImpl, org.forgerock.openam.auditors, com.sun.identity.workflow, com.sun.identity.sm.ServiceConfigManager, org.forgerock.openam.sm.validation, com.sun.identity.common.configuration.SessionSiteNames, com.sun.identity.sm.ServiceConfig, com.sun.identity.sm.SMServlet, com.sun.identity.sm.ServiceManager, com.sun.identity.common.configuration.ServerPropertyValidator, com.sun.identity.sm.SMSEntry, com.sun.identity.sm.PluginConfig, org.forgerock.openam.utils.OpenAMSettingsImpl, com.sun.identity.sm.jaxrpc, com.sun.identity.sm.DNMapper, com.sun.identity.sm.SMSException, com.sun.identity.sm.SMSEventListenerManager, org.forgerock.openam.utils.MapHelper, com.sun.identity.sm.ServiceInstance, com.sun.identity.config.util, com.sun.identity.sm.CachedSubEntries, com.sun.identity.sm.PluginConfigImpl, com.sun.identity.authentication.service.ConfiguredSocialAuthServices, com.sun.identity.sm.ServiceSchemaManagerImpl, com.sun.identity.sm.CachedSMSEntry, com.sun.identity.sm.CreateServiceConfig, com.sun.identity.sm.AttributeSchema, com.sun.identity.sm.PluginSchemaImpl
CoreSystem
Core infrastructure services, PLL, cookies, naming, logging, upgrade, Scripting com.sun.identity.monitoring, com.sun.identity.saml2.idpdiscovery, com.sun.identity.security.cert.CRLValidator, org.forgerock.openam.xacml.v3.rest, org.forgerock.openam.core.rest.SelfServiceUserUiRolePredicate, org.forgerock.openam.core.rest.cts, org.forgerock.openam.sm.datalayer.impl.ldap.LdapSearchHandler, org.forgerock.openam.security, com.sun.identity.plugin.monitoring.impl, org.forgerock.openam.sm.datalayer.providers, com.zaxxer.hikari, org.forgerock.openam.uma.UmaUserUiRolePredicate, com.sun.identity.common.RequestUtils, org.forgerock.openam.entitlement.rest.SubjectAttributesResourceV1, org.forgerock.openam.services.baseurl, org.forgerock.openam.core.rest.IdentityRestUtils, org.forgerock.openam.core.rest.UserGroupsResource, org.forgerock.openam.oauth2.rest, com.sun.identity.authentication.UI.taglib, org.forgerock.openam.core.rest.docs, com.sun.identity.log, org.forgerock.openam.core.rest.AllAuthenticatedUsersResource, org.forgerock.openam.utils.WhitelistObjectInputStream, org.forgerock.openam.core.rest.dashboard, com.sun.identity.common.SystemTimerPool, org.forgerock.openam.core.rest.session.AnyOfAuthzModule, org.forgerock.openam.rest, org.forgerock.openam.core.rest.sms, com.sun.identity.common.admin, org.forgerock.openam.shared.resourcename, com.sun.identity.security.AdminTokenAction, org.forgerock.openam.uma.rest.UmaPolicyResourceAuthzFilter, org.forgerock.openam.shared.concurrency, org.forgerock.openam.core.rest.session.SessionResourcePrivilegeAuthzModule, org.forgerock.openam.entitlement.rest.ResourceTypesResource, org.forgerock.openam.uma.rest.UmaPolicyServiceImpl, org.forgerock.openam.entitlement.rest.DecisionCombinersResource, com.sun.identity.common.HttpURLConnectionManager, org.forgerock.openam.sm.datalayer.impl.SeriesTaskExecutor, org.forgerock.openam.network.ipv4.IPv4AddressRange, org.forgerock.openam.audit, org.forgerock.audit, com.sun.identity.common.DNUtils, org.forgerock.openam.utils.IPRange, org.forgerock.openam.services.RestSecurity, org.forgerock.openam.core.rest.IdentityResourceV4, org.forgerock.openam.core.rest.IdentityResourceV3, com.sun.identity.security.SecurityDebug, org.forgerock.openam.backstage, org.forgerock.openam.core.rest.server, org.forgerock.openam.utils.ClientUtils, org.forgerock.openam.core.rest.IdentityResourceV2, org.forgerock.openam.entitlement.rest.ApplicationV1Filter, org.forgerock.openam.core.rest.IdentityResourceV1, org.forgerock.openam.core.rest.devices, org.forgerock.openam.entitlement.rest.ApplicationsResource, com.sun.identity.policy.util.Gateway, com.sun.identity.shared.jaxrpc, org.forgerock.openam.forgerockrest, com.iplanet.am.util, com.iplanet.services.comm, org.forgerock.openam.core.rest.authn.AuditHelper, org.forgerock.openam.sm.datalayer.impl.PooledTaskExecutor, org.forgerock.openam.ldap.LdifUtils, org.forgerock.openam.core.rest.session.action.LogoutByHandleActionHandler, org.forgerock.openam.sm.datalayer.impl.ldap.LdapQueryBuilder, com.sun.identity.shared.search, org.forgerock.openam.entitlement.rest.SubjectTypesResource, com.sun.identity.shared.encode.CookieUtils, com.iplanet.services.naming, org.forgerock.openam.cors, com.sun.identity.idsvcs, com.sun.identity.jaxrpc, org.forgerock.openam.http, org.forgerock.openam.shared.guice, org.forgerock.openam.utils.AMKeyProvider, org.forgerock.openam.utils.AuthLevelUtils, org.forgerock.openam.shared.security.whitelist, org.forgerock.openam.notifications, com.sun.identity.policy.util.GatewayServletUtils, org.forgerock.openam.core.sms, org.forgerock.openam.blacklist, com.sun.identity.common.configuration.AgentConfiguration, org.forgerock.openam.entitlement.rest.ApplicationTypesResource, org.forgerock.openam.monitoring, com.sun.identity.common.ResourceLookup, org.forgerock.openam.entitlement.rest.PolicyV1Filter, com.sun.identity.authentication.server.AuthXMLRequestParser, org.forgerock.openam.entitlement.rest.wrappers, com.sun.identity.security.cert.AMCertStore, org.forgerock.openam.sm.datalayer.impl.SimpleTaskExecutor, com.sun.identity.shared.locale, com.sun.identity.shared.whitelist, org.forgerock.openam.sm.datalayer.impl.ldap.CTSDJLDAPv3PersistentSearch, com.sun.identity.protocol, org.forgerock.openam.scripting.rest, org.forgerock.openam.entitlement.rest.ConditionTypesResource, org.forgerock.openam.core.rest.record, com.sun.identity.security.cert.AMCertPath, org.forgerock.openam.utils.ServiceConfigUtils, com.sun.identity.authentication.server.AuthXMLRequest
EMBEDDED_DIRECTORY
Embedded Directory Server org.forgerock.opendj, com.forgerock.opendj, com.forgerock.opendj.ldap.config, org.opends
Federation
Federated SSO, protocols (WS-Federation, SAML2), Metadata, Hub, Circle of Trust com.sun.identity.wsfederation.profile, com.sun.identity.saml2.servlet, com.sun.identity.saml2.plugins.SAML2PluginsUtils, com.sun.identity.plugin.datastore, com.sun.identity.saml2.logging, com.sun.identity.saml2.protocol, com.sun.identity.saml2.common, com.sun.identity.saml2.plugins.DefaultAccountMapper, org.forgerock.openam.federation, com.sun.identity.wsfederation.plugins.DefaultSPAttributeMapper, com.sun.identity.saml2.plugins.DefaultSPAccountMapper, com.sun.identity.wsfederation.plugins.whitelist, com.sun.identity.saml2.profile, com.sun.identity.wsfederation.plugins.DefaultLibrarySPAccountMapper, com.sun.identity.saml2.plugins.SAML2IDPProxyFRImpl, com.sun.identity.wsfederation.key, com.sun.identity.multiprotocol, com.sun.identity.saml2.plugins.SAML2IDPProxyImpl, com.sun.identity.wsfederation.servlet, com.sun.identity.xacml, com.sun.identity.plugin.monitoring.MonitorManager, com.sun.identity.saml2.plugins.DefaultIDPAuthnContextMapper, com.sun.identity.wsfederation.plugins.DefaultAccountMapper, com.sun.identity.saml2.plugins.DefaultAttributeMapper, com.sun.identity.wsfederation.plugins.DefaultAttributeMapper, org.forgerock.openam.authentication.Saml2SessionUpgradeHandler, com.sun.identity.saml2.ecp, org.forgerock.openam.wsfederation, com.sun.identity.federation, org.forgerock.openam.saml2, jsp.saml2, com.sun.identity.saml2.plugins.DefaultIDPECPSessionMapper, com.sun.identity.saml2.plugins.DefaultLibrarySPAccountMapper, com.sun.identity.plugin.log, com.sun.identity.saml, com.sun.identity.wsfederation.meta, com.sun.identity.wsfederation.plugins.DefaultIDPAuthenticationMethodMapper, com.sun.identity.saml2.plugins.DefaultFedletAdapter, com.sun.identity.saml2.plugins.DefaultLibraryIDPAttributeMapper, com.sun.identity.saml2.xmlenc, com.sun.identity.saml2.plugins.DefaultSPAttributeMapper, com.sun.identity.saml2.plugins.DefaultSPAuthnContextMapper, com.sun.identity.saml2.xmlsig, com.sun.identity.liberty.ws.security, com.sun.identity.plugin.session.SessionManager, com.sun.identity.wsfederation.plugins.DefaultIDPAccountMapper, com.sun.identity.plugin.session.impl.FMSessionProvider, com.sun.identity.saml2.key, com.sun.identity.wsfederation.logging, com.sun.identity.saml2.plugins.DefaultIDPAccountMapper, com.sun.identity.wsfederation.plugins.DefaultADFSPartnerAccountMapper, com.sun.identity.saml2.assertion, com.sun.identity.wsfederation.plugins.DefaultIDPAttributeMapper, com.sun.identity.plugin.session.impl.FedletSessionProvider, com.sun.identity.saml2.meta, com.sun.identity.plugin.configuration, com.sun.identity.saml2.soapbinding, com.sun.identity.wsfederation.common, com.sun.identity.cot
IdRepo
Identity Repositories, Datastores, plugins com.sun.identity.common.ISResourceBundle, com.iplanet.am.sdk, org.forgerock.openam.idrepo.ldap.DJLDAPv3Repo, org.forgerock.openam.shared.security.crypto, com.iplanet.sso.SSOTokenManager, com.iplanet.services.ldap.DefaultDataStoreConfigurationManager, com.sun.identity.idm, org.forgerock.openam.idrepo.ldap.helpers.DirectoryHelper, com.sun.identity.shared.encode.Hash, org.forgerock.openam.core.realms, org.forgerock.openam.shared.security.ThreadLocalSecureRandom, com.iplanet.services.ldap.event.LDAPv3PersistentSearch, org.forgerock.openam.idrepo.ldap.psearch, com.sun.identity.security.ServerInstanceAction, org.forgerock.openam.identity, org.forgerock.openam.ldap.LDAPUtils
OAuth2Provider
OAuth 2.0 Provider org.forgerock.openam.oauth2.OpenAMClientRegistrationStore, org.forgerock.openam.oauth2.secrets, org.forgerock.openidconnect, org.forgerock.openam.oauth2.resources.ResourceSetLabelRegistration, org.forgerock.openam.oauth2.OAuth2GlobalSettings, org.forgerock.openam.oauth2.OpenAMClientRegistration, org.forgerock.openam.oauth2.ciba, org.forgerock.openam.oauth2.requesturis, org.forgerock.openam.oauth2.OAuth2AuditLogger, org.forgerock.openam.oauth2.token, org.forgerock.openam.oauth2.IdentityManager, org.forgerock.openam.oauth2.IgAgentClientRegistration, org.forgerock.openam.oauth2.jwks, org.forgerock.oauth2, org.forgerock.openam.utils.RealmNormaliser, org.forgerock.openam.oauth2.AgentClientRegistration, org.forgerock.openam.oauth2.ClientCredentialsReader, org.forgerock.openam.oauth2.remoteconsent, org.forgerock.openam.oauth2.OpenAMScopeValidator, org.forgerock.openam.oauth2.OAuth2Monitor
OpenDJ-SDK
Directory Server SDK org.forgerock.opendj.ldif, org.forgerock.opendj.asn1, com.forgerock.opendj.util, com.forgerock.opendj.ldap, org.forgerock.opendj.ldap, org.forgerock.opendj.util
OtherLogging
Miscellaneous logs org.forgerock.openam.secrets.SecretIdChoiceValues, org.forgerock.am.iot.IntrospectTokenActionHandler, com.sun.identity.sm.SmsObjectResolver, org.forgerock.config.resolvers, org.forgerock.openam.services.datastore, org.forgerock.openam.utils.JCECipherProvider, org.forgerock.config.resolvers.SystemPropertyResolver, com.sun.identity.policy.plugins, org.forgerock.openam.entitlement.rest, org.forgerock.openam.services.datastore.DataStoreConsistencyFilter, org.forgerock.openam.oauth2.saml2, org.forgerock.secrets.propertyresolver.PropertyResolverSecretStore, org.forgerock.openam.headers.DisableSameSiteCookiesFilter, org.forgerock.openam.oauth2.resources, org.forgerock.openam.uma.rest, org.forgerock.openam.integration.idm.IdmClientIdRepo, org.forgerock.am.health.HealthCheckService, com.sun.identity.shared, org.forgerock.openam.network.ipv4, com.forgerock, org.forgerock.openam.core.rest.session, org.forgerock.util.encode.Base64url, org.forgerock.openam.core.rest, com.iplanet.services.ldap.ServerGroup, org.forgerock.am.iot.ThingsResource, org.forgerock.openam.uma, org.forgerock.openam.secrets.config.GoogleKeyManagementServiceSecretStore, org.forgerock.api.models.Resource, org.forgerock.openam.oauth2.saml2.core.Saml2GrantTypeHandler, com.sun.identity.configuration.ConfigFedMonitoring, org.forgerock.openam.setup.BootstrapSubstitutionService, org.forgerock.util.promise, org.forgerock.config.resolvers.EnvironmentVariableResolver, org.forgerock.config.util, org.forgerock.openam.scripting.ScriptEngineConfigurator, org.forgerock.openam.oauth2.guice, org.forgerock.openam.scripting.persistence, org.forgerock.api.models.Items, org.forgerock.openam.homedirectory.HomeDirectoryUtils, org.forgerock.openam.selfservice, com.iplanet.services, org.forgerock.openam.scripting.ThreadPoolScriptEvaluator, jsp, org.forgerock.am.health.ReadinessCheckEndpoint, io.swagger.models.parameters.AbstractSerializableParameter, org.forgerock.openam.social, com.sun.identity.plugin.monitoring, org.forgerock.openam.services.MailService, OAuth2Factory, org.apache.http.headers, org.forgerock.json, org.forgerock.openam.oauth2.OAuth2UrisFactory, com.sun.identity.shared.encode, org.forgerock.http.swagger, com.iplanet, com.sun.identity.common.configuration, org.forgerock.json.resource.InterfaceCollectionInstance, org.forgerock.json.resource.http.HttpUtils, org.forgerock.openam.uma.UmaProviderSettingsFactory, org.forgerock.openam.utils, org.forgerock.openam.scripting, org.forgerock.openam.uma.rest.UmaEnabledFilter, org.forgerock.openam.sts.publish.rest.RestSTSSetupListener, org.forgerock.util.encode.Base64, com.zaxxer, org.forgerock.openam.oauth2.guice.OAuth2GuiceModule, org.forgerock.openam.social.idp.SocialIdpJwksSecretsProvider, org.forgerock.secrets, org.forgerock.util.promise.Promises, org.forgerock.secrets.SecretReference, org.forgerock.openam.sts.publish.common.STSInstanceConfigStoreBase, io.swagger.models.parameters, org.forgerock.openam.sts.publish.common, io.swagger, org.forgerock.openam.oauth2.pop, org.forgerock.openam.sm.datalayer, org.forgerock.openam.social.idp.choiceValues.AllowedJweAlgorithms, org.forgerock.http, oauth2, org.forgerock.openam.service.datastore.LdapDataStoreService, org.forgerock.http.filter, org.apache.http.wire, org.forgerock.http.swagger.OpenApiRequestFilter, org.forgerock.openam.xui, org.forgerock.api.models, com.iplanet.services.ldap.event, org.forgerock.json.jose.jws.SigningManager, com.sun.identity.shared.xml.XMLUtils, org.forgerock.http.oauth2, org.forgerock.util.promise.PromiseImpl, org.forgerock.openam.secrets, org.forgerock.openam.sts.publish.service, org.forgerock.openam.sm.config.ConsoleConfigHandlerImpl, org.forgerock.openam.integration.idm, com.sun.identity.authentication, io.swagger.models, org.forgerock.openam.selfservice.SelfServiceRequestHandler, org.forgerock.am.health.LivenessCheckEndpoint, com.sun.identity.sm.RootSuffixProvider, org.forgerock.am.iot, idRepoAuditor, org.forgerock.openam.sm.datalayer.impl, org.forgerock.http.util, com.sun.identity.plugin.session.impl, com.sun.identity.common, org.forgerock.openam.utils.PerThreadCache, com.sun.identity.shared.xml, org.forgerock.openam.service.datastore, com.sun.identity.shared.datastruct, org.forgerock.json.jose.jws, com.sun.identity.common.configuration.ConfigurationObserver, com.sun.identity.configuration, org.forgerock.http.filter.TransactionIdInboundFilter, frRest, org.forgerock.secrets.propertyresolver, org.apache, org.forgerock.openam.service, org.forgerock.openam.secrets.SecretsUtils, org.forgerock.openam.utils.LogUtils, ROOT, com.sun.identity.common.ShutdownManager, org.forgerock.am.iot.GetAccessTokenActionHandler, org.forgerock.openam.core.rest.authn, org.forgerock.openam.scripting.persistence.config.consumer.ScriptTypeAdapter, com.sun, org.forgerock.util.i18n, org.forgerock.openam.entitlement.service.ApplicationServiceImpl, com.sun.identity.policy.plugins.PrefixResourceName, com.sun.identity.wsfederation.plugins, org.forgerock.openam.secrets.config.GoogleSecretManagerSecretStoreProvider, org.forgerock.api.transform, org, org.forgerock.util.encode, com.sun.identity.sm.SmsWrapperObject, org.forgerock.openam.sm.config, org.forgerock.openam.scripting.sandbox, org.forgerock.openam.shared.security, org.forgerock.api.transform.OpenApiTransformer, org.forgerock.http.oauth2.ResourceServerFilter, org.forgerock.openam.headers, com.sun.identity, org.forgerock.openam.core.rest.authn.http, org.forgerock.openam.errors, org.forgerock.openam.idrepo.ldap.helpers, org.forgerock.openam.secrets.config.SecretsPlugin, org.forgerock.http.protocol.Form, org.forgerock.json.resource, org.forgerock.util.i18n.PreferredLocales, com.iplanet.services.ldap, com.sun.identity.sm.schema.ParsedSchema, org.forgerock.openam.scripting.service.ScriptChoiceValues, org.forgerock.openam.sts.publish.rest.RestSTSInstancePublisherImpl, org.forgerock.openam.errors.AgentResourceExceptionMappingHandler, org.forgerock.config.resolvers.FlatFileResolver, org.forgerock.http.routing, org.forgerock.openam.oauth2.pop.MutualTlsConfirmationMethod, org.forgerock.openam.scripting.StandardScriptEvaluator, org.forgerock.am.iot.IotClientRegistrationStore, org.forgerock.http.servlet.Servlet3Adapter, org.forgerock.openam.idrepo, org.forgerock.config, ldapUrl, org.forgerock.json.resource.InterfaceSingletonHandler, org.forgerock.openam.secrets.config, org.forgerock.openam.sm.DefaultAnnotatedServiceRegistry, org.forgerock.am.health, org.forgerock.caf.authentication.framework, org.forgerock.am.iot.GetUserTokenActionHandler, com.sun.identity.authentication.UI.LoginLogoutMapping, org.forgerock.openam.config, io, org.forgerock.caf.authentication, org.forgerock.openam.sm, org.forgerock.openam.sm.ServiceSchemaRegistrar, org.forgerock.api.models.Operation, org.forgerock.http.protocol, org.forgerock.util.DirectoryWatcher, com.sun.identity.security, org.forgerock.openam.entitlement, org.forgerock.openam.oauth2.ClientCertificateHeaderFormat, org.forgerock.am.iot.GetUserCodeActionHandler, org.forgerock.openam.shared, org.forgerock.http.servlet, org.forgerock.api.CrestApiProducer, org.forgerock.openam.sm.annotations.SchemaBuilder, org.forgerock.openam.scripting.sandbox.RhinoSandboxClassShutter, org.forgerock.util.xml, com.sun.identity.authentication.service.ConfiguredIdentityTypes, org.forgerock.openam.xacml, org.forgerock.openam.scripting.service.GlobalScriptChoiceValues, com.iplanet.services.ldap.Server, com.sun.identity.sm, org.forgerock.openam.sts.publish.rest.RestSTSPublishServiceListener, org.forgerock.secrets.AllowedKeyUsageConstraint, org.forgerock.openam.oauth2.jar, org.forgerock.openam.oauth2.OAuth2Utils, org.forgerock.openam.sm.health.FbcLivenessCheck, org.forgerock.json.resource.http, org.forgerock.openam.idrepo.ldap, com.sun.identity.authentication.UI, com.iplanet.services.util, com.sun.identity.liberty.ws, com.sun.identity.authentication.server, org.forgerock.openam.sts.publish.service.SoapSTSPublishServiceRequestHandler, org.forgerock.util, com.iplanet.sso, org.forgerock.openam.sm.health.PluginStartupCheck, org.forgerock.guice.core.InjectorFactory, org.forgerock.openam.sm.datalayer.impl.ldap, org.forgerock.openam.sts.publish, org.forgerock.macaroons, org.forgerock.openam.selfservice.SelfServiceTreesResource, com, org.forgerock.openam.scripting.service.StandardScriptStoreFactory, org.forgerock.openam.scripting.persistence.config, org.forgerock.openam.validation, com.sun.identity.authentication.service, com.sun.identity.sm.SMSThreadPool, org.forgerock.openam.validation.RequestEntitySizeVerificationFilter, org.forgerock.util.promise.Promises$CompletedPromise, com.sun.identity.authentication.service.AuthConfigMonitor, org.forgerock.am, org.forgerock.openam.scripting.service, org.forgerock.api, org.forgerock.http.header.SetCookieHeader, org.forgerock.macaroons.SerializationFormatV2, org.forgerock.am.iot.IotService, org.forgerock.openam.ldap, com.iplanet.am, com.sun.identity.plugin, org.forgerock.macaroons.SerializationFormatV1, com.sun.identity.plugin.session, org.forgerock.openam.services, org.forgerock.util.xml.XMLUtils, org.forgerock.openam.oauth2.saml2.core, org.forgerock.openam.social.idp, org.forgerock.openam.config.ServiceComponentConfigBuilder, org.forgerock.openam.core.rest.session.action, com.sun.identity.liberty, org.forgerock.openam.homedirectory, org.forgerock.openam.scripting.StandardScriptEngineManager, org.forgerock.openam.secrets.Secrets, org.forgerock.caf.authentication.framework.AuthenticationFramework, org.forgerock.json.jose.utils.Utils, org.forgerock.openam.social.idp.SocialIdentityProviders, org.forgerock.openam.core.rest.authn.AuthIdHelper, org.forgerock.openam.oauth2, org.forgerock.openam.core.CoreWrapper, org.forgerock.guice, org.forgerock.http.protocol.Entity, org.forgerock.openam.sts.publish.service.RestSTSPublishServiceRequestHandler, org.forgerock.openam.scripting.persistence.config.consumer, org.forgerock.openam.network, org.forgerock.http.header, org.forgerock.openam.entitlement.service, org.forgerock.openam.integration, com.sun.identity.common.SystemTimer, org.forgerock.openam.core, com.sun.identity.sm.SmsChangesLogger, org.forgerock.openam.sm.datalayer.impl.CtsConnectionCheck, org.forgerock.openam.sts, com.sun.identity.authentication.server.AuthXMLHandler, org.forgerock.openam.sm.annotations, org.forgerock.config.resolvers.PropertyResolvers, org.forgerock.secrets.SecretsProvider, com.sun.identity.policy, com.sun.identity.wsfederation, org.forgerock.json.resource.http.HttpAdapter, org.forgerock.http.util.Uris, com.sun.identity.shared.datastruct.CollectionHelper, org.forgerock.guice.core, org.forgerock, org.forgerock.openam.sts.publish.rest, org.forgerock.openam.social.idp.choiceValues, com.iplanet.services.util.Crypt, com.sun.identity.config, org.forgerock.json.resource.InterfaceCollectionHandler, org.forgerock.openam, jsp.realmSelection, org.forgerock.openam.service.datastore.SmsDataStoreLookup, com.sun.identity.authentication.service.AMLoginContext, com.sun.identity.authentication.spi, org.forgerock.config.util.JsonValuePropertyEvaluator, org.forgerock.openam.xacml.v3, org.forgerock.http.routing.Router, com.iplanet.services.ldap.LDAPUser, com.sun.identity.policy.util, org.apache.http, com.sun.identity.sm.schema, org.forgerock.http.servlet.HttpFrameworkServlet, org.forgerock.openam.setup, org.forgerock.openam.social.idp.DefaultOpenIdConnectRelyingPartySettings, org.forgerock.openam.headers.SecureCookieFilter, com.iplanet.services.util.JCEEncryption, org.forgerock.json.jose, org.forgerock.openam.oauth2.OAuth2NotificationPublisher, com.sun.identity.security.cert, org.forgerock.json.jose.utils, org.forgerock.caf, org.forgerock.openam.oauth2.jar.JarAuthorizeRequestValidator, org.forgerock.openam.sm.health, org.forgerock.config.resolvers.ChainedPropertyResolver
Plugins
Plugin Framework org.forgerock.openam.plugins
Policy
Policy Framework,Subject, Condition, Resource Attributes, XACML, Plugins, API com.sun.identity.policy.PolicyManager, com.sun.identity.policy.plugins.Organization, com.sun.identity.policy.SharedSubject, com.sun.identity.policy.ActionDecision, com.sun.identity.policy.ResourceManager, com.sun.identity.policy.plugins.IDRepoResponseProvider, com.sun.identity.policy.plugins.AuthSchemeCondition, com.sun.identity.policy.plugins.LEAuthLevelCondition, com.sun.identity.policy.PolicyCache, com.sun.identity.policy.PolicyDecision, org.forgerock.openam.entitlement.monitoring, com.sun.identity.policy.ProxyPolicyEvaluatorFactory, com.sun.identity.policy.Rule, com.sun.identity.policy.ResourceComparatorValidator, com.sun.identity.policy.plugins.IPCondition, com.sun.identity.policy.ProxyPolicyEvaluator, com.sun.identity.policy.remote, com.sun.identity.policy.ValidationErrorHandler, org.forgerock.openam.entitlement.rest.EntitlementsExceptionMappingHandler, org.forgerock.openam.network.ipv6, com.sun.identity.policy.Subjects, com.sun.identity.policy.plugins.PeerOrgReferral, com.sun.identity.policy.Policy, com.sun.identity.policy.ActionSchema, org.forgerock.openam.idrepo.ldap.helpers.ADHelper, org.forgerock.openam.entitlement.configuration, com.sun.identity.policy.plugins.SubOrgReferral, com.sun.identity.policy.plugins.AuthenticateToRealmCondition, org.forgerock.openam.entitlement.indextree, com.sun.identity.policy.SubjectEvaluationCache, org.forgerock.openam.uma.rest.UserPolicyResource, com.sun.identity.policy.plugins.OrgReferral, com.sun.identity.policy.plugins.LDAPUsers, com.sun.identity.policy.plugins.UserSelfCheckCondition, com.sun.identity.policy.ResponseProviderTypeManager, com.sun.identity.policy.plugins.LDAPFilterCondition, com.sun.identity.policy.plugins.SimpleTimeCondition, com.sun.identity.policy.ResponseProviders, org.forgerock.openam.xacml.v3.resources, com.sun.identity.policy.PolicyUtils, com.sun.identity.policy.plugins.SessionCondition, org.forgerock.openam.entitlement.CachingEntitlementCondition, com.sun.identity.policy.plugins.AMIdentitySubject, com.sun.identity.policy.Referrals, com.sun.identity.policy.ResourceIndexManager, com.sun.identity.policy.plugins.AuthLevelCondition, com.sun.identity.policy.plugins.LDAPConnectionPools, com.sun.identity.policy.plugins.AuthenticateToServiceCondition, com.sun.identity.policy.plugins.AuthRoleCondition, com.sun.identity.policy.plugins.AMIdentityMembershipCondition, com.sun.identity.entitlement, com.sun.identity.policy.PolicyEvaluatorFactory, com.sun.identity.policy.plugins.SessionPropertyCondition, org.forgerock.openam.entitlement.PolicyConstants, com.sun.identity.policy.PolicyEvaluator, com.sun.identity.policy.ServiceTypeManager, com.sun.identity.policy.ServiceType, com.sun.identity.policy.ResourceResult, com.sun.identity.policy.plugins.ResourceEnvIPCondition, org.forgerock.openam.entitlement.conditions, com.sun.identity.policy.ConditionTypeManager, com.sun.identity.policy.PolicyConfig, com.sun.identity.policy.plugins.LDAPGroups, org.forgerock.openam.network.ipv4.IPv4Condition, com.sun.identity.policy.SubjectTypeManager, org.forgerock.openam.entitlement.utils, com.sun.identity.policy.util.PolicyDecisionUtils, org.forgerock.openam.entitlement.PolicySetNotificationConsumer, com.sun.identity.policy.Conditions, org.forgerock.openam.core.rest.authn.http.AuthenticationServiceV2, com.sun.identity.policy.ReferralTypeManager, org.forgerock.openam.entitlement.rest.PolicyResource, org.forgerock.openam.entitlement.rest.JsonPolicyParser
Push
Push Notification org.forgerock.openam.services.push
Radius
RADIUS server org.forgerock.openam.radius
Session
Session framework, session management, SSOToken, session failover, API org.forgerock.openam.core.rest.session.action.SetPropertyActionHandler, org.forgerock.openam.core.rest.session.action.GetPropertyActionHandler, org.forgerock.openam.core.rest.session.SessionResource, com.sun.identity.sm.ServerIDValidator, org.forgerock.openam.cts, org.forgerock.openam.core.rest.session.action.LogoutActionHandler, org.forgerock.openam.dpro, com.iplanet.sso.providers, org.forgerock.openam.core.rest.session.action.ValidateActionHandler, org.forgerock.openam.core.rest.session.action.GetSessionPropertiesActionHandler, org.forgerock.openam.session, org.forgerock.openam.sm.datalayer.impl.ldap.ExternalLdapConfig, org.forgerock.openam.core.rest.session.action.UpdateSessionPropertiesActionHandler, org.forgerock.openam.core.rest.session.SSOTokenPartialSessionFactory, org.forgerock.openam.sm.SMSConfigurationFactory, org.forgerock.openam.sm.datalayer.impl.SeriesTaskExecutorThread, com.iplanet.dpro, com.sun.identity.plugin.session.impl.FMSessionNotification, org.forgerock.openam.core.rest.session.action.GetPropertyNamesActionHandler, org.forgerock.openam.core.rest.session.SessionResourceUtil, org.forgerock.openam.core.rest.session.SessionResourceV2, com.sun.identity.sm.SiteIDValidator, org.forgerock.openam.core.rest.session.action.DeletePropertyActionHandler
UmaProvider
UMA provider org.forgerock.openam.oauth2.AccessTokenProtectionFilter, org.forgerock.openam.uma.UmaSettingsImpl, org.forgerock.openam.uma.icg, org.forgerock.openam.uma.PendingRequestEmailTemplate, org.forgerock.openam.uma.rest.UmaPolicyApplicationListener, org.forgerock.openam.uma.rest.UmaResourceSetRegistrationHook, org.forgerock.openam.oauth2.resources.labels, org.forgerock.openam.uma.UmaProviderSettingsImpl, org.forgerock.openam.uma.UmaGrantTypeHandler, org.forgerock.openam.uma.rest.UmaLabelResource, org.forgerock.openam.uma.PendingRequestsService, org.forgerock.openam.uma.audit
WebServices
Web services security (WSS), STS, Identity Services com.sun.identity.liberty.ws.paos, com.sun.identity.liberty.ws.common, com.sun.identity.policy.plugins.WebServicesClients, com.sun.identity.liberty.ws.soapbinding, com.sun.identity.authentication.spi.WSSReplayPasswd
amUpgrade
Upgrade framework com.sun.identity.sm.ServiceSchemaModifications, org.forgerock.openam.upgrade, com.sun.identity.common.configuration.ServerConfiguration, com.sun.identity.config.upgrade, com.sun.identity.security.cert.AMCRLStore
-
To set the logging level for all loggers that output to a particular appender:
-
Select the name of the appender from the Appender drop-down list.
-
Select the debug level from the Level drop-down list.
-
Click Apply.
-
-
To set the logging level for a class or package:
-
Select the name of the individual logger from the Logger drop-down list, or select the global
ROOTlogger to set the level for all loggers.The current debug level is shown in the Level field.
Scripts that create debug messages have their own logger that’s created after the script has executed at least once.
The name of the logger has the format:
scripts.<context>.<uuid>.(<name>).For example,
scripts.OIDC_CLAIMS.36863ffb-40ec-48b9-94b1-9a99f71cc3b5.(OIDC Claims Script). -
Select a new debug level from the Level drop-down list.
-
Click Apply.
When you apply any changes to the logger settings , a
Logger settings updatedmessage is shown at the top of theLogback.jsppage.Changes made in
Logback.jspapply immediately, but are not permanently stored. Restarting AM or the container in which it runs will reset the levels to defaults.You can configure the default settings that will be applied when AM starts up. Refer to Change the startup debug settings.
-
-
As soon as you have reproduced the problem you are investigating, return to the
Logback.jsppage and revert the logger levels to the previous settings, to avoid filling up disk space.
Persistent debug logging with logback.xml
Debug logging can be enabled and persisted in AM by configuring a logback.xml file.
This file describes
the classes for which to capture debug messages, and the destination, or appender, where the output is stored.
For more information about configuring Logback, refer to Logback configuration in the Logback Documentation.
Configure basic debug logging
Follow these steps to configure basic persistent debug logging in AM, using a logback.xml file:
-
Create a
logback.xmlfile in the AM classpath, for example in/path/to/tomcat/webapps/openam/WEB-INF/classes/.To view or use an existing file with example loggers and appenders, place the following
logback.xmlin your classpath and set the paths for your environment.Example
logback.xml<configuration> <!-- amUpgrade --> <appender name="amUpgrade" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/amUpgrade</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="com.sun.identity.sm.ServiceSchemaModifications" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="com.sun.identity.common.configuration.ServerConfiguration" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="com.sun.identity.wsfederation.plugins.DefaultIDPAccountMapper" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="com.sun.identity.saml2.plugins.DefaultIDPAccountMapper" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="com.sun.identity.config.upgrade" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="com.sun.identity.saml2.plugins.DefaultLibrarySPAccountMapper" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="com.sun.identity.wsfederation.plugins.DefaultADFSPartnerAccountMapper" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="com.sun.identity.wsfederation.plugins.DefaultIDPAttributeMapper" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="org.forgerock.openam.upgrade" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="com.sun.identity.wsfederation.plugins.DefaultSPAttributeMapper" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="com.sun.identity.saml2.plugins.DefaultSPAccountMapper" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="com.sun.identity.saml2.plugins.DefaultLibraryIDPAttributeMapper" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="com.sun.identity.security.cert.AMCRLStore" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="com.sun.identity.saml2.plugins.DefaultSPAttributeMapper" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <logger name="com.sun.identity.wsfederation.plugins.DefaultLibrarySPAccountMapper" level="Error" > <appender-ref ref="amUpgrade"/> </logger> <!-- Authentication --> <appender name="Authentication" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/Authentication</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="com.sun.identity.authentication.spi.AMLoginModule" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.core.rest.authn.callbackhandlers" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.spi.AMAuthCallBackImpl" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.service.AuthContextLookup" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.util" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.authentication.service.LoginContextFactory" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.server.AuthContextLocal" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.service.AMAccountLockout" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.service.LoginState" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.UI.LoginViewBean" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.client" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.core.rest.authn.trees" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.spi.FirstTimeLogin" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.auth" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.authentication.service.SessionPropertyUpgrader" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.UI.AuthExceptionViewBean" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.spi.ReplayPasswd" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.config" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.share" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.authentication.SessionUpgradeVerifier" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.service.DSAMECallbackHandler" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.spi.AMModuleProperties" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.utils.MappingUtils" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.UI.AuthenticationServletBase" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.service.AuthenticationPrincipalDataRetrieverFactory" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.UI.LogoutViewBean" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.iplanet.security" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.internal" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.AuthContext" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.policy.plugins.AuthenticatedSharedAgents" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.ldap.LDAPAuthUtils" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.UI.AuthViewBeanBase" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.authentication.modules" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.iplanet.services.cdm" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.authentication.service.AuthUtilsWrapper" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.policy.plugins.AuthenticatedAgents" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.spi.JwtReplayPassword" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.policy.plugins.AllowedAgents" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.service.AuthenticationServiceAttributeCache" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.jaas" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.service.AuthD" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.core.rest.authn.core" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.scripting.api" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.common.ISAccountLockout" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.core.rest.authn.RestAuthCallbackHandlerFactory" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.core.rest.authn.RestAuthCallbackHandlerManager" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.webhook" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.iplanet.services.cdc" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.modules" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.core.rest.authn.http.AuthenticationServiceV1" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.authentication.service.AuthUtils" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="com.sun.identity.policy.plugins.AuthenticatedSharedAgentsCondition" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.authentication.service.JAASModuleDetector" level="Error" > <appender-ref ref="Authentication"/> </logger> <logger name="org.forgerock.openam.core.rest.authn.RestAuthenticationHandler" level="Error" > <appender-ref ref="Authentication"/> </logger> <!-- Configuration --> <appender name="Configuration" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/Configuration</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="com.sun.identity.sm.ServiceSchemaManager" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.iplanet.services.ldap.event.EventService" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.SMSSchema" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.tools" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.SMSUtils" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.common.configuration.ServerConfigXMLObserver" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.ServiceSchema" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.delegation" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.OrganizationConfigManager" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.ldap" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.SMSNotificationManager" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.PluginSchema" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.AttributeValidator" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.ServiceConfigManagerImpl" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.ServiceConfigImpl" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.SMSPropertiesObserver" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.OrganizationConfigManagerImpl" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.AuthenticationServiceNameProviderImpl" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="org.forgerock.openam.xui.XUIFilter" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.ServiceSchemaImpl" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.setup" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.AttributeSchemaState" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.ServiceInstanceImpl" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="org.forgerock.openam.auditors" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.workflow" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.ServiceConfigManager" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="org.forgerock.openam.sm.validation" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.common.configuration.SessionSiteNames" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.ServiceConfig" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.SMServlet" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.ServiceManager" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.common.configuration.ServerPropertyValidator" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.SMSEntry" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.PluginConfig" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="org.forgerock.openam.utils.OpenAMSettingsImpl" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.jaxrpc" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.DNMapper" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.SMSException" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.SMSEventListenerManager" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="org.forgerock.openam.utils.MapHelper" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.ServiceInstance" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.config.util" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.CachedSubEntries" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.PluginConfigImpl" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.authentication.service.ConfiguredSocialAuthServices" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.ServiceSchemaManagerImpl" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.CachedSMSEntry" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.CreateServiceConfig" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.AttributeSchema" level="Error" > <appender-ref ref="Configuration"/> </logger> <logger name="com.sun.identity.sm.PluginSchemaImpl" level="Error" > <appender-ref ref="Configuration"/> </logger> <!-- CoreSystem --> <appender name="CoreSystem" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/CoreSystem</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="com.sun.identity.monitoring" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.saml2.idpdiscovery" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.security.cert.CRLValidator" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.xacml.v3.rest" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.SelfServiceUserUiRolePredicate" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.cts" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.sm.datalayer.impl.ldap.LdapSearchHandler" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.security" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.plugin.monitoring.impl" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.sm.datalayer.providers" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.zaxxer.hikari" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.uma.UmaUserUiRolePredicate" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.common.RequestUtils" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.entitlement.rest.SubjectAttributesResourceV1" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.services.baseurl" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.IdentityRestUtils" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.UserGroupsResource" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.oauth2.rest" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.authentication.UI.taglib" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.docs" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.log" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.AllAuthenticatedUsersResource" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.utils.WhitelistObjectInputStream" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.dashboard" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.common.SystemTimerPool" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.session.AnyOfAuthzModule" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.rest" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.sms" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.common.admin" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.shared.resourcename" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.security.AdminTokenAction" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.uma.rest.UmaPolicyResourceAuthzFilter" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.shared.concurrency" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.session.SessionResourcePrivilegeAuthzModule" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.entitlement.rest.ResourceTypesResource" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.uma.rest.UmaPolicyServiceImpl" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.entitlement.rest.DecisionCombinersResource" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.common.HttpURLConnectionManager" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.sm.datalayer.impl.SeriesTaskExecutor" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.network.ipv4.IPv4AddressRange" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.audit" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.audit" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.common.DNUtils" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.utils.IPRange" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.services.RestSecurity" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.IdentityResourceV4" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.IdentityResourceV3" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.security.SecurityDebug" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.backstage" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.server" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.utils.ClientUtils" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.IdentityResourceV2" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.entitlement.rest.ApplicationV1Filter" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.IdentityResourceV1" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.devices" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.entitlement.rest.ApplicationsResource" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.policy.util.Gateway" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.shared.jaxrpc" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.forgerockrest" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.iplanet.am.util" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.iplanet.services.comm" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.authn.AuditHelper" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.sm.datalayer.impl.PooledTaskExecutor" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.ldap.LdifUtils" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.session.action.LogoutByHandleActionHandler" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.sm.datalayer.impl.ldap.LdapQueryBuilder" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.shared.search" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.entitlement.rest.SubjectTypesResource" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.shared.encode.CookieUtils" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.iplanet.services.naming" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.cors" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.idsvcs" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.jaxrpc" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.http" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.shared.guice" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.utils.AMKeyProvider" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.utils.AuthLevelUtils" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.shared.security.whitelist" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.notifications" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.policy.util.GatewayServletUtils" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.sms" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.blacklist" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.common.configuration.AgentConfiguration" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.entitlement.rest.ApplicationTypesResource" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.monitoring" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.common.ResourceLookup" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.entitlement.rest.PolicyV1Filter" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.authentication.server.AuthXMLRequestParser" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.entitlement.rest.wrappers" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.security.cert.AMCertStore" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.sm.datalayer.impl.SimpleTaskExecutor" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.shared.locale" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.shared.whitelist" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.sm.datalayer.impl.ldap.CTSDJLDAPv3PersistentSearch" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.protocol" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.scripting.rest" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.entitlement.rest.ConditionTypesResource" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.core.rest.record" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.security.cert.AMCertPath" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="org.forgerock.openam.utils.ServiceConfigUtils" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <logger name="com.sun.identity.authentication.server.AuthXMLRequest" level="Error" > <appender-ref ref="CoreSystem"/> </logger> <!-- Embedded --> <appender name="Embedded" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/Embedded</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="org.forgerock.opendj" level="Error" > <appender-ref ref="Embedded"/> </logger> <logger name="com.forgerock.opendj" level="Error" > <appender-ref ref="Embedded"/> </logger> <logger name="com.forgerock.opendj.ldap.config" level="Error" > <appender-ref ref="Embedded"/> </logger> <logger name="org.opends" level="Error" > <appender-ref ref="Embedded"/> </logger> <!-- Federation --> <appender name="Federation" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/Federation</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="com.sun.identity.wsfederation.profile" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.servlet" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.plugins.SAML2PluginsUtils" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.plugin.datastore" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.logging" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.protocol" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.common" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.plugins.DefaultAccountMapper" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="org.forgerock.openam.federation" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.wsfederation.plugins.whitelist" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.profile" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.plugins.SAML2IDPProxyFRImpl" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.wsfederation.key" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.multiprotocol" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.plugins.SAML2IDPProxyImpl" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.wsfederation.servlet" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.xacml" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.plugin.monitoring.MonitorManager" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.plugins.DefaultIDPAuthnContextMapper" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.wsfederation.plugins.DefaultAccountMapper" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.plugins.DefaultAttributeMapper" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.wsfederation.plugins.DefaultAttributeMapper" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="org.forgerock.openam.authentication.Saml2SessionUpgradeHandler" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.ecp" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="org.forgerock.openam.wsfederation" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.federation" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="org.forgerock.openam.saml2" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="jsp.saml2" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.plugins.DefaultIDPECPSessionMapper" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.plugin.log" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.wsfederation.meta" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.wsfederation.plugins.DefaultIDPAuthenticationMethodMapper" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.plugins.DefaultFedletAdapter" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.xmlenc" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.plugins.DefaultSPAuthnContextMapper" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.xmlsig" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.liberty.ws.security" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.plugin.session.SessionManager" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.plugin.session.impl.FMSessionProvider" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.key" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.wsfederation.logging" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.assertion" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.plugin.session.impl.FedletSessionProvider" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.meta" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.plugin.configuration" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.saml2.soapbinding" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.wsfederation.common" level="Error" > <appender-ref ref="Federation"/> </logger> <logger name="com.sun.identity.cot" level="Error" > <appender-ref ref="Federation"/> </logger> <!-- IdRepo --> <appender name="IdRepo" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/IdRepo</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="com.sun.identity.common.ISResourceBundle" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="com.iplanet.am.sdk" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="org.forgerock.openam.idrepo.ldap.DJLDAPv3Repo" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="org.forgerock.openam.shared.security.crypto" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="com.iplanet.sso.SSOTokenManager" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="com.iplanet.services.ldap.DefaultDataStoreConfigurationManager" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="com.sun.identity.idm" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="org.forgerock.openam.idrepo.ldap.helpers.DirectoryHelper" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="com.sun.identity.shared.encode.Hash" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="org.forgerock.openam.core.realms" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="org.forgerock.openam.shared.security.ThreadLocalSecureRandom" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="com.iplanet.services.ldap.event.LDAPv3PersistentSearch" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="org.forgerock.openam.idrepo.ldap.psearch" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="com.sun.identity.security.ServerInstanceAction" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="org.forgerock.openam.identity" level="Error" > <appender-ref ref="IdRepo"/> </logger> <logger name="org.forgerock.openam.ldap.LDAPUtils" level="Error" > <appender-ref ref="IdRepo"/> </logger> <!-- OAuth2Provider --> <appender name="OAuth2Provider" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/OAuth2Provider</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="org.forgerock.openam.oauth2.OpenAMClientRegistrationStore" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.secrets" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openidconnect" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.resources.ResourceSetLabelRegistration" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.OAuth2GlobalSettings" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.OpenAMClientRegistration" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.ciba" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.requesturis" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.OAuth2AuditLogger" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.token" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.IdentityManager" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.IgAgentClientRegistration" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.jwks" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.oauth2" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.utils.RealmNormaliser" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.AgentClientRegistration" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.ClientCredentialsReader" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.remoteconsent" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.OpenAMScopeValidator" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <logger name="org.forgerock.openam.oauth2.OAuth2Monitor" level="Error" > <appender-ref ref="OAuth2Provider"/> </logger> <!-- OpenDJ-SDK --> <appender name="OpenDJ-SDK" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/OpenDJ-SDK</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="org.forgerock.opendj.ldif" level="Error" > <appender-ref ref="OpenDJ-SDK"/> </logger> <logger name="org.forgerock.opendj.asn1" level="Error" > <appender-ref ref="OpenDJ-SDK"/> </logger> <logger name="com.forgerock.opendj.util" level="Error" > <appender-ref ref="OpenDJ-SDK"/> </logger> <logger name="com.forgerock.opendj.ldap" level="Error" > <appender-ref ref="OpenDJ-SDK"/> </logger> <logger name="org.forgerock.opendj.ldap" level="Error" > <appender-ref ref="OpenDJ-SDK"/> </logger> <logger name="org.forgerock.opendj.util" level="Error" > <appender-ref ref="OpenDJ-SDK"/> </logger> <!-- Plugins --> <appender name="Plugins" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/Plugins</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="org.forgerock.openam.plugins" level="Error" > <appender-ref ref="Plugins"/> </logger> <!-- Policy --> <appender name="Policy" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/Policy</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="com.sun.identity.policy.PolicyManager" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.Organization" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.SharedSubject" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ActionDecision" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ResourceManager" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.IDRepoResponseProvider" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.AuthSchemeCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.LEAuthLevelCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.PolicyCache" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.PolicyDecision" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.entitlement.monitoring" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ProxyPolicyEvaluatorFactory" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.Rule" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ResourceComparatorValidator" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.IPCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.PolicyContinuousListener" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ProxyPolicyEvaluator" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.remote" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ValidationErrorHandler" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.entitlement.rest.EntitlementsExceptionMappingHandler" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.network.ipv6" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.Subjects" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.PeerOrgReferral" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.Policy" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ActionSchema" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.idrepo.ldap.helpers.ADHelper" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.entitlement.configuration" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.SubOrgReferral" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.AuthenticateToRealmCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.entitlement.indextree" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.LDAPRoles" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.SubjectEvaluationCache" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.uma.rest.UserPolicyResource" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.OrgReferral" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.LDAPUsers" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.UserSelfCheckCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ResponseProviderTypeManager" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.LDAPFilterCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.SimpleTimeCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ResponseProviders" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.xacml.v3.resources" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.PolicyUtils" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.SessionCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.entitlement.CachingEntitlementCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.AMIdentitySubject" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.Referrals" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ResourceIndexManager" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.AuthLevelCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.LDAPConnectionPools" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.AuthenticateToServiceCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.AuthRoleCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.AMIdentityMembershipCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.entitlement" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.PolicyEvaluatorFactory" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.SessionPropertyCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.entitlement.PolicyConstants" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.PolicyEvaluator" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ServiceTypeManager" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ServiceType" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ResourceResult" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.ResourceEnvIPCondition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.entitlement.conditions" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ConditionTypeManager" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.PolicyConfig" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.plugins.LDAPGroups" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.network.ipv4.IPv4Condition" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.SubjectTypeManager" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.entitlement.utils" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.util.PolicyDecisionUtils" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.entitlement.PolicySetNotificationConsumer" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.Conditions" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.core.rest.authn.http.AuthenticationServiceV2" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="com.sun.identity.policy.ReferralTypeManager" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.entitlement.rest.PolicyResource" level="Error" > <appender-ref ref="Policy"/> </logger> <logger name="org.forgerock.openam.entitlement.rest.JsonPolicyParser" level="Error" > <appender-ref ref="Policy"/> </logger> <!-- Push --> <appender name="Push" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/Push</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="org.forgerock.openam.services.push" level="Error" > <appender-ref ref="Push"/> </logger> <!-- Radius --> <appender name="Radius" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/Radius</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="org.forgerock.openam.radius" level="Error" > <appender-ref ref="Radius"/> </logger> <!-- Session --> <appender name="Session" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/Session</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="org.forgerock.openam.core.rest.session.action.SetPropertyActionHandler" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.core.rest.session.action.GetPropertyActionHandler" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.core.rest.session.SessionResource" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="com.sun.identity.sm.ServerIDValidator" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.cts" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.core.rest.session.action.LogoutActionHandler" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.dpro" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="com.iplanet.sso.providers" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.core.rest.session.action.ValidateActionHandler" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.core.rest.session.action.GetSessionPropertiesActionHandler" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.session" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.sm.datalayer.impl.ldap.ExternalLdapConfig" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.core.rest.session.action.UpdateSessionPropertiesActionHandler" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.core.rest.session.SSOTokenPartialSessionFactory" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.sm.SMSConfigurationFactory" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.sm.datalayer.impl.SeriesTaskExecutorThread" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="com.iplanet.dpro" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="com.sun.identity.plugin.session.impl.FMSessionNotification" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.core.rest.session.action.GetPropertyNamesActionHandler" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.core.rest.session.SessionResourceUtil" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.core.rest.session.SessionResourceV2" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="com.sun.identity.sm.SiteIDValidator" level="Error" > <appender-ref ref="Session"/> </logger> <logger name="org.forgerock.openam.core.rest.session.action.DeletePropertyActionHandler" level="Error" > <appender-ref ref="Session"/> </logger> <!-- UmaProvider --> <appender name="UmaProvider" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/UmaProvider</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="org.forgerock.openam.oauth2.AccessTokenProtectionFilter" level="Error" > <appender-ref ref="UmaProvider"/> </logger> <logger name="org.forgerock.openam.uma.UmaSettingsImpl" level="Error" > <appender-ref ref="UmaProvider"/> </logger> <logger name="org.forgerock.openam.uma.PendingRequestEmailTemplate" level="Error" > <appender-ref ref="UmaProvider"/> </logger> <logger name="org.forgerock.openam.uma.rest.UmaPolicyApplicationListener" level="Error" > <appender-ref ref="UmaProvider"/> </logger> <logger name="org.forgerock.openam.uma.rest.UmaResourceSetRegistrationHook" level="Error" > <appender-ref ref="UmaProvider"/> </logger> <logger name="org.forgerock.openam.oauth2.resources.labels" level="Error" > <appender-ref ref="UmaProvider"/> </logger> <logger name="org.forgerock.openam.uma.UmaProviderSettingsImpl" level="Error" > <appender-ref ref="UmaProvider"/> </logger> <logger name="org.forgerock.openam.uma.UmaGrantTypeHandler" level="Error" > <appender-ref ref="UmaProvider"/> </logger> <logger name="org.forgerock.openam.uma.rest.UmaLabelResource" level="Error" > <appender-ref ref="UmaProvider"/> </logger> <logger name="org.forgerock.openam.uma.PendingRequestsService" level="Error" > <appender-ref ref="UmaProvider"/> </logger> <logger name="org.forgerock.openam.uma.audit" level="Error" > <appender-ref ref="UmaProvider"/> </logger> <!-- WebServices --> <appender name="WebServices" class="ch.qos.logback.core.FileAppender"> <file>/path/to/debug/WebServices</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="com.sun.identity.liberty.ws.paos" level="Error" > <appender-ref ref="WebServices"/> </logger> <logger name="com.sun.identity.liberty.ws.common" level="Error" > <appender-ref ref="WebServices"/> </logger> <logger name="com.sun.identity.policy.plugins.WebServicesClients" level="Error" > <appender-ref ref="WebServices"/> </logger> <logger name="com.sun.identity.liberty.ws.soapbinding" level="Error" > <appender-ref ref="WebServices"/> </logger> <logger name="com.sun.identity.authentication.spi.WSSReplayPasswd" level="Error" > <appender-ref ref="WebServices"/> </logger> <!-- OtherLogging rotation created so that ROOT could be set without outputting same debug to all files --> <appender name="OtherLogging" class="ch.qos.logback.core.rolling.RollingFileAppender"> <rollingPolicy class="ch.qos.logback.core.rolling.SizeAndTimeBasedRollingPolicy"> <file>/path/to/debug/OtherLogging</file> <fileNamePattern>/path/to/debug/OtherLogging.%d{yyyy-MM-dd}-%i</fileNamePattern> <maxFileSize>1GB</maxFileSize> </rollingPolicy> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <root level="Error"> <appender-ref ref="OtherLogging" /> </root> </configuration>xmlDownload
logback.xml. -
In your empty
logback.xmlfile, add a top-level element calledconfiguration.For example:
<configuration> </configuration>xmlThis element will contain the configuration of the loggers and appenders, added in later steps.
-
To instruct AM to periodically check the
logback.xmlfile for changes, and apply them to the running instance, add both ascanand ascanPeriodattribute to the<configuration>element. For example:<configuration scan="true" scanPeriod="30 seconds"> </configuration>xmlIf AM is not configured to scan the
logback.xmlfile for changes, you’ll need to restart the instance in order to pick up any changes.You can set the
scanPeriodattribute to a longer time period, for example one hour, so that you don’t have to restart a running system when you need to alter the debugging level.For more information, refer to Automatically reloading configuration file upon modification in the Logback Documentation.
-
To troubleshoot issues when configuring debug logging using the
logback.xmlfile, add adebugattribute, set totrue, to the<configuration>element. For example:<configuration debug="true"> </configuration>xmlAM records debug logging status information to the default log file for the container in which it’s running. For example, in Tomcat, status messages about the configuration of logback are recorded in the
Catalina.outfile.For more information, refer to Status data in the Logback Documentation.
-
-
Define one or more appenders in the
<configuration>element.The following example appender logs messages to a file named
debug.outin the default AM debug directory:<configuration> <appender name="DEBUG.OUT" class="ch.qos.logback.core.FileAppender"> <file>openam/var/debug/debug.out</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> </configuration>xmlThe pattern in the above example creates debug log entries that are identical to the output produced by previous versions of AM, including the transaction ID to aid with tracking events as they occur throughout the system.
You can also define an appender that uses the JsonLayout class to include the transaction ID automatically. Refer to Format log files for details.
-
Define one or more loggers in the
<configuration>element.Loggers specify which classes to capture debug messages from, including any sub-classes. They also specify the level of debug information to capture, and which appender is used to store the output.
This example logger applies the
Debuglevel to thescripts.OIDC_CLAIMS.36863ffb-40ec-48b9-94b1-9a99f71cc3b5.(OIDC Claims Script). Note that script loggers are only created after the script has executed at least once. The output is recorded in the file specified in thedebug.outappender, created in an earlier step:<configuration> <appender name="DEBUG.OUT" class="ch.qos.logback.core.FileAppender"> <file>openam/var/debug/debug.out</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="scripts.OIDC_CLAIMS.36863ffb-40ec-48b9-94b1-9a99f71cc3b5.(OIDC Claims Script)" level="Debug" > <appender-ref ref="DEBUG.OUT" /> </logger> </configuration>xml -
Define a single
<root>catch-all element in the<configuration>element, to specify the global logging level for all classes that don’t match any of the loggers defined in thelogback.xmlfile.<configuration> <appender name="DEBUG.OUT" class="ch.qos.logback.core.FileAppender"> <file>openam/var/debug/debug.out</file> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender> <logger name="scripts.OIDC_CLAIMS.36863ffb-40ec-48b9-94b1-9a99f71cc3b5.(OIDC Claims Script)" level="Debug" > <appender-ref ref="DEBUG.OUT" /> </logger> <root level="Error"> <appender-ref ref="DEBUG.OUT" /> </root> </configuration>xml -
Save your changes.
The changes are applied the next time you restart AM, or the container in which it runs.
If you are editing an existing
logback.xmlthat AM has already loaded, and contains thescan="true"attribute, you do not need to reboot.Instead, wait for the amount of time specified in the
scanPeriodattribute, and the new configuration will be loaded into AM. -
To verify that the configuration from the
logback.xmlfile has loaded, go to theLogback.jspfile, for example athttps://openam.example.com:8443/openam/Logback.jsp, which reflects the configuration found: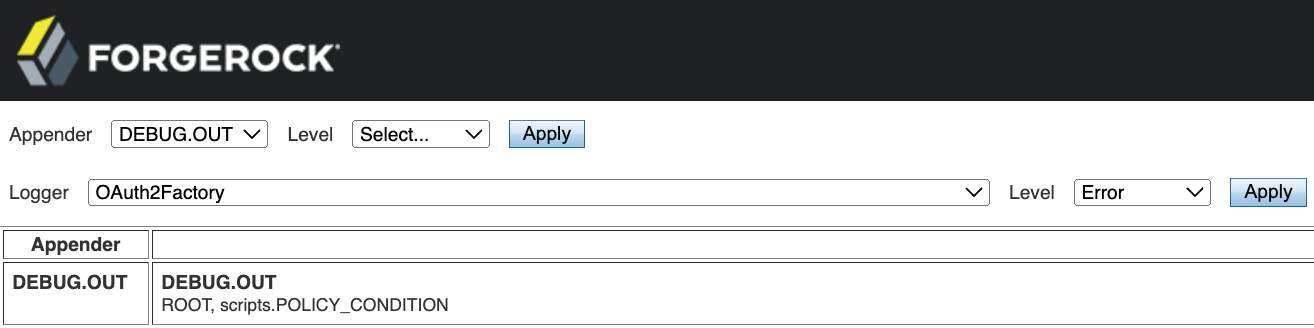
Note that any changes made in the
Logback.jspare temporary, and are not persisted to thelogback.xmlfile.
Output to stdout
Configure logback.xml to send logging to standard output.
For example, for Apache Tomcat deployments, console output is typically redirected to the Tomcat logging file, catalina.out.
This example configuration captures all debug-level logging using the default <root> element,
and redirects it to the STDOUT appender:
<configuration>
<appender name="STDOUT" class="ch.qos.logback.core.ConsoleAppender"> (1)
<encoder>
<pattern>%d{HH:mm:ss.SSS} [%thread] %-5level %logger{36} - %msg%n</pattern>
</encoder>
</appender>
<root level="Debug"> (2)
<appender-ref ref="STDOUT" />
</root>
</configuration>-
To configure this example, create the following elements:
1 An <appender>that uses thech.qos.logback.core.ConsoleAppenderclass.2 A <logger>, or a<root>element as shown here, referencing the STDOUT appender. -
Save your changes as described in Configure basic debug logging.
-
Check that debug logging is now output to stdout. For example:
tail -f $TOMCAT_HOME/logs/catalina.out
Output to multiple locations
You can direct debug logging to more than one output location by defining multiple appenders and loggers. Note that you can only define at most one root element.
This example defines loggers for the com.sun.identity.sm.ServiceInstance and org.forgerock.openam.utils.MapHelper classes that output debug logging to file using the DEBUG.OUT appender.
All warning-level logging is also directed to standard output using the STDOUT appender.
<configuration>
<appender name="DEBUG.OUT" class="ch.qos.logback.core.FileAppender"> (1)
<file>openam/var/debug/debug.out</file>
<encoder>
<pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern>
</encoder>
</appender>
<appender name="STDOUT" class="ch.qos.logback.core.ConsoleAppender"> (2)
<encoder>
<pattern>%d{HH:mm:ss.SSS} [%thread] %-5level %logger{36} - %msg%n</pattern>
</encoder>
</appender>
<logger name="com.sun.identity.sm.ServiceInstance" level="Debug"> (3)
<appender-ref ref="DEBUG.OUT" />
</logger>
<logger name="org.forgerock.openam.utils.MapHelper" level="Debug"> (3)
<appender-ref ref="DEBUG.OUT" />
</logger>
<root level="Warning"> (4)
<appender-ref ref="STDOUT" />
</root>
</configuration>-
To configure this example, create the following elements:
1 An <appender>that uses thech.qos.logback.core.FileAppenderclass.2 An <appender>that uses thech.qos.logback.core.ConsoleAppenderclass.3 A <logger>for each script, referencing the DEBUG.OUT appender.4 A <logger>, or a<root>element as shown here, referencing the STDOUT appender. -
Save and verify your changes as described in Configure basic debug logging.
Format log files
The org.forgerock.openam.logback.JsonLayout class extends Logback JSON layout
functionality by adding the transaction ID to the JSON output.
This example shows how you can include the JsonLayout class to format your log files:
<appender name="JSON" class="ch.qos.logback.core.rolling.RollingFileAppender"> (1)
<rollingPolicy class="ch.qos.logback.core.rolling.TimeBasedRollingPolicy">
<fileNamePattern>openam/var/debug/debugLog.%d{yyyy_MM_dd}.json</fileNamePattern>
<maxHistory>7</maxHistory>
</rollingPolicy>
<encoder class="ch.qos.logback.core.encoder.LayoutWrappingEncoder"> (2)
<layout class="org.forgerock.openam.logback.JsonLayout"> (3)
<jsonFormatter class="ch.qos.logback.contrib.jackson.JacksonJsonFormatter"> (4)
<prettyPrint>true</prettyPrint>
</jsonFormatter>
<timestampFormat>yyyy-MM-dd' 'HH:mm:ss.SSS</timestampFormat>
<appendLineSeparator>true</appendLineSeparator>
</layout>
</encoder>
</appender>-
To configure this example, create the following elements:
1 An <appender>that uses thech.qos.logback.core.rolling.RollingFileAppenderclass.2 An <encoder>that uses thech.qos.logback.core.encoder.LayoutWrappingEncoderclass.3 A <layout>element that uses theorg.forgerock.openam.logback.JsonLayoutclass.4 A <jsonFormatter>element that uses thech.qos.logback.contrib.jackson.JacksonJsonFormatterclass. -
Save and verify your changes as described in Configure basic debug logging.
The use of the JsonLayout class results in the addition of a
transactionIdat the top level of the log entry.For example:
{ "timestamp" : "2022-07-28 15:39:44.562", "level" : "DEBUG", "thread" : "http-nio-8080-exec-6", "mdc" : { "transactionId" : "eb0664cc-4615-461e-973a-64a1fc4f659a-34695" }, "logger" : "org.forgerock.openam.rest.restAuthenticationFilter", "message" : "OpenAM SSO Token Session Module has successfully authenticated the client", "context" : "default", "transactionId" : "eb0664cc-4615-461e-973a-64a1fc4f659a-34695" }json
Rotate debug logs
Logback provides built-in support for a number of log file rotation schemes, including time- and-size based rotation.
If you have configured AM with a logback.xml file, you can configure log file rotation in the appenders,
as follows:
-
In the
<configuration>element, create an appender that uses thech.qos.logback.core.rolling.RollingFileAppenderclass, for example:<appender name="DAILYLOG" class="ch.qos.logback.core.rolling.RollingFileAppender"> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender>xmlWithin the appender, specify whether to rotate based on time, and optionally also size, as follows:
-
To rotate the log files based only on time, add a
<rollingPolicy>element to the appender, which uses thech.qos.logback.core.rolling.TimeBasedRollingPolicyclass.Include a
<fileNamePattern>element that defines when the log files should roll over, and the naming convention.For example, the following appender rolls the log file over at midnight each day, and includes the date in the filename:
<appender name="DAILYLOG" class="ch.qos.logback.core.rolling.RollingFileAppender"> <rollingPolicy class="ch.qos.logback.core.rolling.TimeBasedRollingPolicy"> <fileNamePattern>openam/var/debug/dailyLog.%d{yyyy-MM-dd}.log</fileNamePattern> </rollingPolicy> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender>xml -
To rotate the log files based on both time and size, add a
<rollingPolicy>element to the appender, which uses thech.qos.logback.core.rolling.SizeAndTimeBasedRollingPolicyclass.Include a
<fileNamePattern>element that defines when the log files should roll over, and where the counter for rolling over based on size occurs, specified by including%i. You must also include a<maxFileSize>element to define the maximum size of the log files.For example, the following appender rolls the log file over at midnight each day, but earlier if the file reaches 2 gigabytes in size, and includes the date in the filename:
<appender name="DAILYLOG2GB" class="ch.qos.logback.core.rolling.RollingFileAppender"> <rollingPolicy class="ch.qos.logback.core.rolling.SizeAndTimeBasedRollingPolicy"> <fileNamePattern>openam/var/debug/dailyLog2GB.%d{yyyy-MM-dd}-%i.log</fileNamePattern> <maxFileSize>2GB</maxFileSize> </rollingPolicy> <encoder> <pattern>%lo{5}: %d{ISO8601}: Thread[%t]: TransactionId[%X{transactionId}]%n%level: %m%n%ex</pattern> </encoder> </appender>xml
-
-
Save and verify your changes as described in Configure basic debug logging.
Debug log files will roll over each night, and also if they reach the 2GB size limit. The file names will contain the date, and a counter to signify the order in which they were written.
Change the startup debug settings
You can configure the settings that are applied when AM starts up
and there is no logback.xml file present.
The settings specified as defaults will be reflected in the Logback.jsp file,
for example at https://openam.example.com:8443/openam/Logback.jsp.
However, they will not override the configuration contained with a custom logback.xml file.
Set the default debug level
These steps set the default debug level used by all loggers, when AM starts up:
-
In the AM admin UI, go to Deployment > Servers > Server Name > General > Debugging.
-
Select an option from the Debug Level field.
The default level for debug logging is
Error. This level is appropriate for normal production operations, in which case no debug log messages are expected.Setting the debug log level to
Warningincreases the volume of messages. Setting the debug log level toMessagedumps detailed trace messages.Unless told to do so by qualified support personnel, do not use
WarningorMessagelevels as a default in production. Instead, set the levels on a per-class basis. -
Save your changes.
Changes are applied immediately.
Set the default debug directory
These steps set the default directory used to store debug log files:
-
In the AM admin UI, go to Deployment > Servers > Server Name > General > Debugging.
-
Enter a directory in which to store log files in the Debug Directory field.
The default value is as follows:
-
Unix/Linux
-
Windows
%BASE_DIR%/var/debugBASE_DIRis the local Access Management configuration directory; for example/path/to/openam.%BASE_DIR%\var\debugBASE_DIRis the local Access Management configuration directory; for example\path\to\openam.Make sure that the specified folder can be written to by the account that is running AM or the container in which it runs.
-
-
Save your changes.
The changes are applied the next time you restart AM, or the container in which it runs.
Combine log messages in a single file
These steps log all debug messages to a single debug.out file:
-
In the AM admin UI, go to Deployment > Servers > Server Name > General > Debugging.
-
Set the Merge Debug Files property to
On. -
Save your changes.
Changes are applied immediately.
All debug log messages will be written to a single debug file named
debug.out. The file will be located in the directory specified in the Debug Directory property. Refer to Set the default debug directory.
Capture troubleshooting information
The AM recording facility lets you initiate events to monitor AM while saving output that is useful when performing troubleshooting.
AM recording events save four types of information:
-
AM debug logs
-
Thread dumps, which show you the status of every active thread, with output similar to a JStack stack trace
-
Important runtime properties
-
The AM configuration
You initiate a recording event by invoking the ssoadm start-recording command with a JSON file,
or through a REST call with a JSON payload.
The file or payload controls the amount of information AM records,
the duration of the recording, and the location of recording output files.
Recording control file/payload reference
issueID-
Type: Number
Required. The issue identifier—a positive integer stored internally as a Java
longdata type. A case number is a good choice for theissueIDvalue.The
issueIDis a component of the path at which recorded information is stored.See Retrieving Recording Information for more information.
referenceID-
Type: String
Required. A second identifier for the recording event. Use this property to segregate multiple recording events for the same issue.
The
referenceIDis a component of the path at which recorded information is stored.Spaces are not allowed in the
referenceIDvalue.See Retrieving Recording Information for more information.
Description-
Type: String
Required. A textual description of the recording event.
zipEnable-
Type: Boolean
Required. Whether to compress the output directory into a zip file when recording has stopped.
configExport-
Type: Object
Required. An object containing the following properties:
enable-
Type: Boolean
Required. Whether to export the AM configuration upon completion of the recording event. Exporting the AM configuration is a best practice, because it is extremely useful to have access to the configuration when troubleshooting.
password-
Type: String
Required if
enableistrue. A key required to import the exported configuration. The key is used the same way that thessoadm export-svc-cfgcommand uses the-eargument. sharePassword-
Type: Boolean
Required if
enableistrue. Whether to show thepasswordvalue in thessoadm start-recording,ssoadm get-recording-status, andssoadm stop-recordingoutput, and in theinfo.jsonfile, which is output during recording events, and which contains runtime properties.
debugLogs-
Type: Object
Required. An object containing the following properties:
debugLevel-
Type: String
Required. The debug level to set for the recording event. Set the value of
debugLeveltoMESSAGEto get the most troubleshooting information from your recording period. Other acceptable but less commonly used values areERRORandWARNING. autoStop-
Type: Object
Optional. Contains another object used to specify an event that automatically ends a recording period. For time-based termination, specify a
timeobject; for termination based on uncompressed file size, specify afileSizeobject. If you specify bothtimeandfileSizeobjects, the event that occurs first causes recording to stop.Specifying
fileSizeandtimeobjects is a best practice, because it ensures that the recorded output does not occupy a larger than expected amount of space on your file system, and that recording events end in a timely fashion.time-
Type: Object
Optional; must be specified in the
autoStopobject iffileSizeis not specified. Configures a recording period to terminate recording after this amount of time.timeUnit:-
Type: String
Required. Acceptable values are
MILLISECONDS,SECONDS,MINUTES,HOURS, andDAYS.value:-
Type: Numeric
Required. Values in
MILLISECONDSare rounded down to the second. The minimum acceptable value forautoStopis one second.
fileSize-
Type: Object
Optional; must be specified in the
autoStopobject iftimeis not specified. Configures a recording period to terminate after the aggregate size of uncompressed debug logs has reached this size.sizeUnit:-
Type: String
Required. Acceptable values are
B,KB,MB, andGB.value:-
Type: Numeric
Required.
threadDump-
Type: Object
Required. An object containing the following properties:
enable-
Type: Boolean
Required. Whether to dump threads during the recording event. Thread dumps are especially useful when troubleshooting performance issues and issues with unresponsive servers.
delay-
Type: Object
Required if
enableistrue. Contains another object used to specify an interval at which thread dumps are taken. The initial thread dump is taken at the start of the recording event; subsequent thread dumps are taken at multiples of thedelayinterval.timeUnit-
Type: String
Required. Acceptable values are
MILLISECONDS,SECONDS,MINUTES,HOURS, andDAYS. value-
Type: Numeric
Required. The minimum acceptable value is one second. Time units that are smaller than seconds, such as
MILLISECONDS, are rounded to the closest second.
Recording control file/payload example
{
"issueID": 103572,
"referenceID": "policyEvalFails",
"description": "Troubleshooting artifacts in support of case 103572",
"zipEnable": true,
"configExport": {
"enable": true,
"password": "5x2RR70",
"sharePassword": false
},
"debugLogs": {
"debugLevel": "MESSAGE",
"autoStop": {
"time": {
"timeUnit": "SECONDS",
"value": 15
},
"fileSize": {
"sizeUnit": "GB",
"value": 1
}
}
},
"threadDump": {
"enable": true,
"delay": {
"timeUnit": "SECONDS",
"value": 5
}
}
}The recording control file properties in the preceding example affect the recording output as follows:
| Recording Control File Property | Value | Effect |
|---|---|---|
|
|
Recording output is stored at the path |
|
|
No effect. |
|
|
Recording output is compressed into a ZIP file. |
|
|
The AM configuration is exported at the start of the recording event. |
|
|
Knowledge of this password will be required to access the AM configuration that was saved during recording. |
|
|
The password is not displayed in output messages displayed during the recording event
or in the |
|
|
Recording enables message-level debug logs during the recording event. |
|
|
Because both the |
|
|
Because both the |
|
|
Thread dumps are taken throughout the recording event. |
|
|
The first thread dump is taken when the recording event starts. Additional thread dumps are taken every five seconds hence. |
The following table shows different tasks related to recording troubleshooting information:
| Task or Requirement | Resources |
|---|---|
Start and stop recording information Use the |
|
Retrieve information AM stores the troubleshooting information you gathered, so it is ready to be sent to ForgeRock Support representatives. |
Start and stop recording (ssoadm)
Start AM recording with the ssoadm start-recording command.
For example:
$ ssoadm \
start-recording \
--servername https://openam.example.com:8443/openam \
--adminid uid=amAdmin,ou=People,dc=openam,dc=forgerock,dc=org \
--password-file /tmp/pwd.txt \
--jsonfile recording.json
{
"recording": true,
"record": {
"issueID": 103572,
"referenceID": "policyEvalFails",
"description": "Record everything",
"zipEnable": false,
"threadDump": {
"enable": true,
"delay": {
"timeUnit": "SECONDS",
"value": 5
}
},
"configExport": {
"enable": true,
"password": "admin password",
"sharePassword": true
},
"debugLogs": {
"debugLevel": "message",
"autoStop": {
"time": {
"timeUnit": "MILLISECONDS",
"value": 15000
},
"fileSize": {
"sizeUnit": "KB",
"value": 1048576
}
}
},
"status": "RUNNING",
"folder": "/home/openam/debug/record/103572/policyEvalFails/"
}
}|
The |
In the preceding ssoadm start-recording command example,
the recording.json file specifies the information to be recorded
and under what conditions recording automatically terminates.
An active recording event stops when:
-
To explicitly tell AM to stop recording, use the
ssoadm stop-recordingcommand.See the ssoadm for details about this command.
-
Another
ssoadm start-recordingcommand is sent to AM that specifies an issue ID that differs from the active recording event’s issue ID. In this case, the initial recording session terminates and the new recording event starts. Note that you can determine whether an AM recording event is active by using thessoadm get-recording-statuscommand. -
A timer configured in the recording control file determines that the maximum amount of time for the recording event has been reached.
-
A file size monitor configured in the recording control file determines that the maximum amount of information in debug logs has been reached.
Start and stop recording (REST)
To start a recording event, send an HTTP POST request to the /json/records endpoint,
specifying the _action=start parameter in the URL.
Specify a JSON payload identical in format to the input file for the ssoadm start-recording command.
You must authenticate to AM as an administrative user to obtain an SSO token
prior to calling the /json/records REST endpoint.
You then pass the SSO token in the iPlanetDirectoryPro header as proof of authentication.
$ curl \
--request POST \
--header "Content-Type: application/json" \
--header "iPlanetDirectoryPro: AQIC5…" \
--header "Accept-API-Version: resource=1.0" \
--data ' {
"issueID": 103572,
"referenceID": "policyEvalFails",
"description": "Troubleshooting artifacts in support of case 103572",
"zipEnable": true,
"configExport": {
"enable": true,
"password": "5x2RR70",
"sharePassword": false
},
"debugLogs": {
"debugLevel": "MESSAGE",
"autoStop": {
"time": {
"timeUnit": "SECONDS",
"value": 15
},
"fileSize": {
"sizeUnit": "GB",
"value": 1
}
}
},
"threadDump" : {
"enable": true,
"delay" : {
"timeUnit": "SECONDS",
"value": 5
}
}
}' \
https://openam.example.com:8443/openam/json/records?_action=start
{
"recording":true,
"record":{
"issueID":103572,
"referenceID":"policyEvalFails",
"description":"Troubleshooting artifacts in support of case 103572",
"zipEnable":true,
"threadDump":{
"enable":true,
"delay":{
"timeUnit":"SECONDS",
"value":5
}
},
"configExport":{
"enable":true,
"password":"xxxxxx",
"sharePassword":false
},
"debugLogs":{
"debugLevel":"message",
"autoStop":{
"time":{
"timeUnit":"MILLISECONDS",
"value":15000
},
"fileSize":{
"sizeUnit":"KB",
"value":1048576
}
}
},
"status":"RUNNING",
"folder":"/opt/demo/openam/config/openam/debug/record/103572/policyEvalFails/"
}
}The curl command output is indented for ease of reading.
The actual output is not indented,
and the actions available from the /json/records endpoint do not support the _prettyPrint parameter.
To stop a recording event, send an HTTP POST request to the /json/records endpoint,
specifying the _action=stop parameter in the URL:
$ curl \
--request POST \
--header "iPlanetDirectoryPro: AQIC5…" \
--header "Accept-API-Version: resource=1.0" \
https://openam.example.com:8443/openam/json/records?_action=stopIf there is no active recording event, AM returns a 400 error code.
If there is an active recording event, output similar to the following appears:
{
"recording": false,
"record": {
"issueID": 103572,
"referenceID": "policyEvalFails",
"description": "Troubleshooting artifacts in support of case 103572",
"zipEnable": true,
"threadDump": {
"enable": true,
"delay": {
"timeUnit": "SECONDS",
"value": 5
}
},
"configExport": {
"enable": true,
"password": "xxxxxx",
"sharePassword": false
},
"debugLogs": {
"debugLevel": "message",
"autoStop": {
"time": {
"timeUnit": "MILLISECONDS",
"value": 15000
},
"fileSize": {
"sizeUnit": "KB",
"value": 1048576
}
}
},
"status": "STOPPED",
"folder": "/opt/demo/openam/config/openam/debug/record/103572/policyEvalFails/"
}
}Get recording status (REST)
To get the status of a recording event, perform an HTTP POST using the /json/records endpoint,
specifying the _action=status parameter in the URL:
$ curl \
--request POST \
--header "iPlanetDirectoryPro: AQIC5…" \
--header "Accept-API-Version: resource=1.0" \
https://openam.example.com:8443/openam/json/records?_action=statusIf there is no active recording event, the following output appears:
{
"recording":false
}If there is an active recording event, output similar to the following appears:
{
"recording":true,
"record":{
"issueID":103572,
"referenceID":"policyEvalFails",
"description":"Troubleshooting artifacts in support of case 103572",
"zipEnable":true,
"threadDump":{
"enable":true,
"delay":{
"timeUnit":"SECONDS",
"value":5
}
},
"configExport":{
"enable":true,
"password":"xxxxxx",
"sharePassword":false
},
"debugLogs":{
"debugLevel":"message",
"autoStop":{
"time":{
"timeUnit":"MILLISECONDS",
"value":15000
},
"fileSize":{
"sizeUnit":"KB",
"value":1048576
}
}
},
"status":"RUNNING",
"folder":"/opt/demo/openam/config/openam/debug/record/103572/policyEvalFails/"
}
}Retrieve recording information
Information recorded by AM is stored at the path debugFileLocation/record/issueID/referenceID.
For example, if the debug file location is /home/openam/debug, the issue ID 103572,
and the reference ID policyEvalFails, the path containing recorded information is
/home/openam/debug/record/103572/policyEvalFails.
When there are multiple recording events with the same issueID and referenceID,
AM appends a timestamp to the referenceID of the earliest paths.
For example, multiple recording events for issue ID 103572
and reference ID policyEvalFails might be stored at the following paths:
-
Most recent recording:
debugFileLocation/record/103572/policyEvalFails -
Next most recent recording:
debugFileLocation/record/103572/policyEvalFails_2015-10-24-11-48-51-902-PDT -
Earliest recording:
debugFileLocation/record/103572/policyEvalFails_2015-08-10-15-15-10-140-PDT
AM compresses the output from recording events when you set the zipEnable property to true.
The output file can be found at the path debugFileLocation/record/issueID/referenceID_timestamp.zip.
For example, compressed output for a recording event for issue ID 103572 and reference ID policyEvalFails
might be stored at the following path:
debugFileLocation/record/103572/policyEvalFails_2015-08-12-12-19-02-683-PDT.zip.
Use the referenceID property value to segregate output when reproducing the same problem multiple times.
For example, while troubleshooting case 103572,
you notice that you only have a problem when evaluating policy for members of the Finance realm.
You could trigger two recording events as follows:
| AM behavior | referenceIDValue | Recording output path |
|---|---|---|
Policy evaluation behaves as expected for members of the Engineering realm. |
|
|
Policy evaluation unexpectedly fails for members of the Finance realm. |
|
|
Reference
This reference provides information related to maintaining an AM instance, and covers the following topics:
For the global services reference, refer to Global services configuration.
Monitoring
amster service name: Monitoring
Configuration
The following settings appear on the Configuration tab:
- Monitoring Status
-
Enable / Disable the monitoring system
Default value:
falseamsterattribute:enabled - Monitoring HTTP Port
-
Port number for the HTTP monitoring interface
Default value:
8082amsterattribute:httpPort - Monitoring HTTP interface status
-
Enable / Disable the HTTP access to the monitoring system
Default value:
falseamsterattribute:httpEnabled - Monitoring HTTP interface authentication file path
-
Path to the monitoring system authentication file
The
openam_mon_authfile contains the username and password of the account used to protect the monitoring interfaces. The default username isdemowith a password ofchangeit. Use theampasswordcommand to encrypt a new password.Default value:
%BASE_DIR%/security/openam_mon_authamsterattribute:authfilePath - Monitoring RMI Port
-
Port number for the JMX monitoring interface
Default value:
9999amsterattribute:rmiPort - Monitoring RMI interface status
-
Enable / Disable the JMX access to the monitoring system
Default value:
falseamsterattribute:rmiEnabled - Monitoring SNMP Port
-
Port number for the SNMP monitoring interface
Default value:
8085amsterattribute:snmpPort - Monitoring SNMP interface status
-
Enable / Disable the SNMP access to the monitoring system
Default value:
falseamsterattribute:snmpEnabled - Policy evaluation monitoring history size
-
Size of the window of most recent policy evaluations to record to expose via monitoring system. Valid range is 100 - 1000000.
Default value:
10000amsterattribute:policyHistoryWindowSize - Session monitoring history size
-
Size of the window of most recent session operations to record to expose via monitoring system. Valid range is 100 - 1000000.
Default value:
10000amsterattribute:sessionHistoryWindowSize
Secondary configurations
This service has the following secondary configurations.
graphite
- Hostname
-
The hostname of the Graphite server to which metrics should be published.
amsterattribute:host - Port
-
The port of the Graphite server to which metrics should be published.
Default value:
2004amsterattribute:port - Frequency
-
The frequency (in seconds) at which metrics should be published.
Default value:
30amsterattribute:frequency
Monitoring metric types
This page describes the monitoring metric types that are available in AM.
Summary
Metric that samples observations, providing a count of observations, sum total of observed amounts, average rate of events, and moving average rates across sliding time windows.
Fields
When using the Common REST, JMX, or Graphite interfaces, the Summary metric type has the following fields:
| Field | Description | ||
|---|---|---|---|
|
The metric ID. |
||
|
The metric type. |
||
|
The number of events recorded for this metric. |
||
|
The sum of the values of events recorded for this metric.
|
||
|
The one-minute average rate. |
||
|
The five-minute average rate. |
||
|
The fifteen-minute average rate. |
||
|
The average rate. |
||
|
A description of the units the metric is presented in. |
The following is an example of the authentication.success metric from the Common REST endpoint:
{
"_id" : "authentication.success",
"_type" : "summary",
"count" : 2,
"total" : 2.0,
"m1_rate" : 3.2668341885586836E-14,
"m5_rate" : 7.794695663154025E-5,
"m15_rate" : 0.01377545747021923,
"mean_rate" : 8.238608027596704E-4,
"units" : "events/second"
}Prometheus fields
The Prometheus endpoint does not provide rate-based statistics, as rates can be calculated from the time-series data.
When using the Prometheus interface, the Summary metric type has the following fields:
| Field | Description |
|---|---|
|
The metric ID, and type. Formatted as a comment. |
|
The number of events recorded. |
|
The sum of the amounts of events recorded |
The following is an example of the am_authentication{outcome="success"} metric from the Prometheus endpoint:
# TYPE am_authentication summary
am_authentication_count{outcome="success"} 2.0
am_authentication_total{outcome="success"} 2.0Timer
Metric that combines both rate and duration information.
Fields
When using the Common REST, JMX, or Graphite interfaces, the Timer metric type has the following fields:
| Field | Description |
|---|---|
|
The metric ID. |
|
The metric type. |
|
The number of events recorded for this metric. |
|
The sum of the durations recorded for this metric. |
|
The minimum duration recorded for this metric. |
|
The maximum duration recorded for this metric. |
|
The mean average duration recorded for this metric. |
|
The standard deviation of durations recorded for this metric. |
|
The units used for measuring the durations in the metric. |
|
50% of the durations recorded are at or below this value. |
|
75% of the durations recorded are at or below this value. |
|
95% of the durations recorded are at or below this value. |
|
98% of the durations recorded are at or below this value. |
|
99% of the durations recorded are at or below this value. |
|
99.9% of the durations recorded are at or below this value. |
|
The one-minute average rate. |
|
The five-minute average rate. |
|
The fifteen-minute average rate. |
|
The average rate. |
|
The units used for measuring the rate of the metric. |
|
Duration-based values, such as |
The following is an example of the cts.connection.success metric from the Common REST endpoint:
{
"_id" : "cts.connection.success",
"_type" : "timer",
"count" : 486,
"total" : 80.0,
"min" : 0.0,
"max" : 1.0,
"mean" : 0.1905615495053855,
"stddev" : 0.39274399467782056,
"duration_units" : "milliseconds",
"p50" : 0.0,
"p75" : 0.0,
"p95" : 1.0,
"p98" : 1.0,
"p99" : 1.0,
"p999" : 1.0,
"m1_rate" : 0.1819109974890356,
"m5_rate" : 0.05433445522996721,
"m15_rate" : 0.03155662103953588,
"mean_rate" : 0.020858521722211427,
"rate_units" : "calls/second"
}Prometheus fields
The Prometheus endpoint does not provide rate-based statistics, as rates can be calculated from the time-series data.
When using the Prometheus interface, the Timer metric type has the following fields:
| Field | Description |
|---|---|
|
The metric ID, and type.
Note that the |
|
The number of events recorded. |
|
The sum of the durations recorded. |
|
50% of the durations are at or below this value. |
|
75% of the durations are at or below this value. |
|
95% of the durations are at or below this value. |
|
98% of the durations are at or below this value. |
|
99% of the durations are at or below this value. |
|
99.9% of the durations are at or below this value. |
|
Duration-based quantile values are weighted towards newer data. By representing approximately the last five minutes of data, the timers make it easier to see recent changes in behavior, rather than a uniform average of recordings since the server was started. |
The following is an example of the am_cts_connection_seconds{outcome="success"} metric from the Prometheus endpoint:
# TYPE am_cts_connection_seconds summary
am_cts_connection_seconds{outcome="success",quantile="0.5",} 0.0
am_cts_connection_seconds{outcome="success",quantile="0.75",} 0.0
am_cts_connection_seconds{outcome="success",quantile="0.95",} 0.001
am_cts_connection_seconds{outcome="success",quantile="0.98",} 0.001
am_cts_connection_seconds{outcome="success",quantile="0.99",} 0.001
am_cts_connection_seconds{outcome="success",quantile="0.999",} 0.001
am_cts_connection_count{outcome="success",} 492.0
am_cts_connection_seconds_total{outcome="success",} 0.081Gauge
Metric for a numerical value that can increase or decrease. The value for a gauge is calculated when requested, and represents the state of the metric at that specific time.
Fields
When using the Common REST, JMX, or Graphite interfaces, the Gauge metric type has the following fields:
| Field | Description |
|---|---|
|
The metric ID. |
|
The metric type. |
|
The current value of the metric. |
The following is an example of the jvm.used-memory metric from the Common REST endpoint:
{
"_id" : "jvm.used-memory",
"_type" : "gauge",
"value" : 2.13385216E9
}Prometheus fields
When using the Prometheus interface, the Timer metric type has the following fields:
| Field | Description |
|---|---|
|
The metric ID, and type. Formatted as a comment. |
|
The current value. Large values may be represented in scientific E-notation. |
The following is an example of the am_jvm_used_memory_bytes metric from the Prometheus endpoint:
# TYPE am_jvm_used_memory_bytes gauge
am_jvm_used_memory_bytes 2.13385216E9Distinct counter
Metric providing an estimate of the number of unique values recorded.
For example, this could be used to estimate the number of unique users who have authenticated, or unique client IP addresses.
|
The |
Fields
When using the Common REST, JMX, or Graphite interfaces, the DistinctCounter metric type has the following fields:
| Field | Description |
|---|---|
|
The metric ID. |
|
The metric type.
Note that the |
|
The calculated estimate of the number of unique values recorded in the metric. |
The following is an example of the authentication.unique-uuid.success metric from the Common REST endpoint:
{
"_id" : "authentication.unique-uuid.success",
"_type" : "gauge",
"value" : 3.0
}Prometheus fields
When using the Prometheus interface, the distinctCounter metric type has the following fields:
| Field | Description |
|---|---|
|
The metric ID, and type.
Note that the |
|
The calculated estimate of the number of unique values recorded in the metric. |
The following is an example of the am_authentication_unique_uuid{outcome="success"} metric
from the Prometheus endpoint:
# TYPE am_authentication_unique_uuid gauge
am_authentication_unique_uuid{outcome="success"} 3.0Monitoring metrics
AM exposes the monitoring metrics described in this page.
Authentication metrics
AM exposes the following authentication-related monitoring metrics:
authentication.module.<auth-module-name>.<outcome>-
Rate of successful/unsuccessful authentication module outcomes. (Summary)
Prometheus syntax:
am_authentication_module{module=<auth-module-name>,outcome=<outcome>}Labels:
<auth-module-name>-
Classname of the authentication module, for example:
ApplicationDataStore <outcome>-
successfailuretimeout
authentication.unique-uuid.success-
Count of unique identities which have successfully logged in. (DistinctCounter)
Prometheus syntax:
am_authentication_unique_uuid{outcome=success} authentication.<outcome>-
Rate of successful/unsuccessful/timed-out authentication flows. (Summary)
Prometheus syntax:
am_authentication{outcome=<outcome>}Labels:
<outcome>-
successfailuretimeout
Authorization Metrics
AM exposes the following authorization-related monitoring metrics:
authorization.policy-set.<policy-set-name>.evaluate.action.<policy-action-name>.<outcome>-
Rate of policy evaluation allowed/denied actions being returned under a given policy set. (Summary)
Prometheus syntax:
am_authorization_policy_set_evaluate_action{policy_set=<policy-set-name>, action-type=<policy-action-name>,outcome=<outcome>}Labels:
<policy-set-name>-
Name of the policy set, for example:
iPlanetAMWebAgentServiceoauth2Scopes <policy-action-name>-
Name of the action as specified in the policy, for example:
GETPOSTGRANT <outcome>-
allowdeny
authorization.policy-set.<policy-set-name>.evaluate.advice.<policy-advice-type-name>-
Rate of policy evaluation advice types being returned under a given policy set. (Summary)
Prometheus syntax:
am_authorization_policy_set_evaluate_advice{policy_set=<policy-set-name>,advice-type=<policy-advice-type-name>}Labels:
<policy-set-name>-
Name of the policy set, for example:
iPlanetAMWebAgentServiceoauth2Scopes <policy-advice-type-name>-
Name of the policy condition advice, for example:
AuthSchemeConditionAdviceAuthenticateToServiceConditionAdviceAuthLevelConditionAdviceAuthenticateToTreeConditionAdviceAuthenticateToRealmConditionAdviceTransactionConditionAdvice
authorization.policy-set.evaluate.subject-cache.size-
Number of cached subject membership relationships. (Gauge)
Prometheus syntax:
am_authorization_policy_set_evaluate_subject_cache_size authorization.policy-set.<policy-set-name>.evaluate.<outcome>-
Rate of successful/unsuccessful policy evaluation calls under a given policy set and time taken to perform this operation. (Timer)
Prometheus syntax:
am_authorization_policy_set_evaluate{policy_set=<policy-set-name>,outcome=<outcome>}Labels:
<policy-set-name>-
Name of the policy set, for example:
iPlanetAMWebAgentServiceoauth2Scopes <outcome>-
successfailuretimeout
authorization.policy-set.<policy-set-name>.policy.<operation>-
Number of policies created/updated/deleted under a given policy set since this AM instance was started. (Summary)
Prometheus syntax:
am_authorization_policy_set_policy{policy_set=<policy-set-name>,operation=<operation>}Labels:
<policy-set-name>-
Name of the policy set, for example:
iPlanetAMWebAgentServiceoauth2Scopes <operation>-
createupdatedelete
Denylisting metrics
AM exposes the following denylisting monitoring metrics:
<blacklist-type>.blacklist.bloomfilter.check.<outcome>-
Rate of bloom filter denylist checks. (Summary)
Prometheus syntax:
am_blacklist_bloomfilter_check{blacklist_type=<blacklist-type>,outcome=<outcome>}Labels:
<blacklist-type>-
session.client-based(Prometheus:session_client_based)oauth2 <outcome>-
negative. The bloom filter reports that the checked token is not blacklisted.false-positive. The bloom filter reports that the checked token may be blacklisted, but the token was not blacklisted.positive. The bloom filter reports that the checked token may be blacklisted, and this was found to be true.
<blacklist-type>.blacklist.cache.hit-
Rate of cache hits of the denylist cache layer. (Summary)
Prometheus syntax:
am_blacklist_cache{blacklist_type=<blacklist-type>,outcome=hit}Labels:
<blacklist-type>-
session.client-based(Prometheus:session_client_based)oauth2
<blacklist-type>.blacklist.cache.miss-
Rate of cache misses of the denylist cache layer. (Summary)
Prometheus syntax:
am_blacklist_cache{blacklist_type=<blacklist-type>,outcome=miss}Labels:
<blacklist-type>-
session.client-based(Prometheus:session_client_based)oauth2
<blacklist-type>.blacklist.check.<outcome>-
Rate of denylist checks. (Summary)
Prometheus syntax:
am_blacklist_check{blacklist_type=<blacklist-type>,outcome=<outcome>}Labels:
<blacklist-type>-
session.client-based(Prometheus:session_client_based)oauth2 <outcome>-
true. The token is blacklisted.false. The token is not blacklisted.
<blacklist-type>.blacklist.cts.search.result-
Rate of denylist entries returned by searches. (Summary)
Prometheus syntax:
am_blacklist_cts_search_result{blacklist_type=<blacklist-type>}Labels:
<blacklist-type>-
session.client-based(Prometheus:session_client_based)oauth2
<blacklist-type>.blacklist.cts.search.<outcome>-
Tracks time to search CTS for denylist entries. (Timer)
Prometheus syntax:
am_blacklist_cts_search{blacklist_type=<blacklist-type>,outcome=<outcome>}Labels:
<blacklist-type>-
session.client-based(Prometheus:session_client_based)oauth2 <outcome>-
successfailure
CTS metrics
AM exposes the following CTS-related monitoring metrics:
cts.connection.<outcome>-
Rate of successful/unsuccessful CTS connections to DS and time taken to obtain the connection. (Timer)
Prometheus syntax:
am_cts_connection{outcome=<outcome>}Labels:
<outcome>-
successfailure
cts.connection.state.<status>-
The number of connections in each state. (Counter)
Prometheus syntax:
am_cts_connection_state{status=<status>}Labels:
<status>-
outpending
cts.reaper.cache.size-
Number of entries in the token reaper cache. (Gauge)
Prometheus syntax:
am_cts_reaper_cache_size cts.reaper.cache.<token-type>.deletion.<outcome>-
Rate of successful/unsuccessful token deletions from cache by token type. (Summary)
Prometheus syntax:
am_cts_reaper_deletion{reaper_type=cache,token_type=<token-type>,outcome=<outcome>}Labels:
<token-type>-
sessionsaml2oauth2restoauth2-csrf-protection(Prometheus:oauth2_csrf_protection)resource-set(Prometheus:resource_set)uma-permission-ticket(Prometheus:uma_permission_ticket)uma-requesting-party(Prometheus:uma_requesting_party)uma-audit-entry(Prometheus:uma_audit_entry)session-blacklist(Prometheus:session_blacklist)uma-pending-request(Prometheus:uma_pending_request)stsoauth2-blacklist(Prometheus:oauth2_blacklist)oauth2-stateless(Prometheus:oauth2_stateless)push-notification(Prometheus:push_notification)cluster-notification(Prometheus:cluster_notification)oauth2-stateless-grant(Prometheus:oauth2_stateless_grant)transactionauthentication-whitelist(Prometheus:authentication_whitelist)oauth2-grant-set(Prometheus:oauth2_grant_set) <outcome>-
successfailure
cts.reaper.search.<token-type>.deletion.<outcome>-
Rate of successful/unsuccessful token deletions from search by token type. (Summary)
Prometheus syntax:
am_cts_reaper_deletion{reaper_type=search,token_type=<token-type>,outcome=<outcome>}Labels:
<token-type>-
sessionsaml2oauth2restoauth2-csrf-protection(Prometheus:oauth2_csrf_protection)resource-set(Prometheus:resource_set)uma-permission-ticket(Prometheus:uma_permission_ticket)uma-requesting-party(Prometheus:uma_requesting_party)uma-audit-entry(Prometheus:uma_audit_entry)session-blacklist(Prometheus:session_blacklist)uma-pending-request(Prometheus:uma_pending_request)stsoauth2-blacklist(Prometheus:oauth2_blacklist)oauth2-stateless(Prometheus:oauth2_stateless)push-notification(Prometheus:push_notification)cluster-notification(Prometheus:cluster_notification)oauth2-stateless-grant(Prometheus:oauth2_stateless_grant)transactionauthentication-whitelist(Prometheus:authentication_whitelist)oauth2-grant-set(Prometheus:oauth2_grant_set) <outcome>-
successfailure
cts.reaper.search.<outcome>-
Rate of successful/unsuccessful search and time taken to perform this operation. (Timer)
Prometheus syntax:
am_cts_reaper_search{outcome=<outcome>}Labels:
<outcome>-
successfailure
cts_task.<token-type>.<operation-type>.<outcome>-
Rate of successful/unsuccessful CTS operation types, by token type and time taken to perform them. (Timer)
Prometheus syntax:
am_cts_task{operation=<operation-type>,token-type=<token-type>,outcome=<outcome>}Labels:
<token-type>-
sessionsaml2oauth2restoauth2-csrf-protection(Prometheus:oauth2_csrf_protection)resource-set(Prometheus:resource_set)uma-permission-ticket(Prometheus:uma_permission_ticket)uma-requesting-party(Prometheus:uma_requesting_party)uma-audit-entry(Prometheus:uma_audit_entry)session-blacklist(Prometheus:session_blacklist)uma-pending-request(Prometheus:uma_pending_request)stsoauth2-blacklist(Prometheus:oauth2_blacklist)oauth2-stateless(Prometheus:oauth2_stateless)push-notification(Prometheus:push_notification)cluster-notification(Prometheus:cluster_notification)oauth2-stateless-grant(Prometheus:oauth2_stateless_grant)transactionauthentication-whitelist(Prometheus:authentication_whitelist)oauth2-grant-set(Prometheus:oauth2_grant_set) <operation-type>-
createreadupdatedeletepatchquerypartial-query(Prometheus:partial_query) <outcome>-
successfailure
JVM metrics
AM exposes the JVM-related monitoring metrics covered in this section.
To get the metric name used by Prometheus, prepend am_ to the names below,
and replace period (.)) and hyphen (-) characters with underscore (_) characters.
For example, the jvm.available-cpus metric is named am_jvm_available_cpus in Prometheus.
|
These metrics may depend on the JVM version and configuration. In particular, garbage-collector-related metrics depend on the garbage collector that the server uses. The garbage-collector metric names are unstable, and can change even in a minor JVM release. |
| Name | Description |
|---|---|
|
Number of processors available to the Java virtual machine. (Gauge) |
|
Number of classes loaded since the Java virtual machine started. (Gauge) |
|
Number of classes unloaded since the Java virtual machine started. (Gauge) |
|
Amount of free memory. |
|
Amount of used memory. |
|
Maximum amount of memory. |
|
Number of collections performed by the "copy" garbage collection algorithm. (Gauge) |
|
Approximate accumulated time taken by the "copy" garbage collection algorithm. (Gauge) |
|
Number of collections performed by the "mark sweep" garbage collection algorithm. (Gauge) |
|
Approximate accumulated time taken by the "mark sweep" garbage collection algorithm. (Gauge) |
|
Amount of heap memory the Java virtual machine initially requested from the operating system. (Gauge) |
|
Maximum amount of heap memory the Java virtual machine attempts to use. (Gauge) |
|
Amount of heap memory committed for the Java virtual machine to use. (Gauge) |
|
Amount of heap memory used by the Java virtual machine. (Gauge) |
|
Percentage of heap memory used out of the maximum available. (Gauge). |
|
Amount of non-heap memory the Java virtual machine initially requested from the operating system. (Gauge) |
|
Maximum amount of non-heap memory the Java virtual machine attempts to use. (Gauge) |
|
Amount of non-heap memory that is committed for the Java virtual machine to use. (Gauge) |
|
Amount of non-heap memory used by the Java virtual machine. (Gauge) |
|
Percentage of non-heap memory used out of the maximum available. (Gauge) |
|
Amount of "compressed class space" memory the Java virtual machine initially requested from the operating system. (Gauge) |
|
Maximum amount of "compressed class space" memory the Java virtual machine attempts to use. (Gauge) |
|
Amount of "compressed class space" memory committed for the Java virtual machine to use. (Gauge) |
|
Amount of "compressed class space" memory used by the Java virtual machine. (Gauge) |
|
Percentage of "compressed class space" memory used out of the maximum available. (Gauge) |
|
Amount of CodeHeap "non-nmethods" memory the Java virtual machine initially requested from the operating system. (Gauge) |
|
Maximum amount of CodeHeap "non-nmethods" memory the Java virtual machine attempts to use. (Gauge) |
|
Amount of CodeHeap "non-nmethods" memory committed for the Java virtual machine to use. (Gauge) |
|
Amount of CodeHeap "non-nmethods" memory used by the Java virtual machine. (Gauge) |
|
Percentage of CodeHeap "non-nmethods" memory used out of the maximum available. (Gauge) |
|
Amount of CodeHeap "non-profiled-nmethods" memory the Java virtual machine initially requested from the operating system. (Gauge) |
|
Maximum amount of CodeHeap "non-profiled-nmethods" memory the Java virtual machine attempts to use. (Gauge) |
|
Amount of CodeHeap "non-profiled-nmethods" memory committed for the Java virtual machine to use. (Gauge) |
|
Amount of CodeHeap "non-profiled-nmethods" memory used by the Java virtual machine. (Gauge) |
|
Percentage of CodeHeap "non-profiled-nmethods" memory used out of the maximum available. (Gauge) |
|
Amount of CodeHeap "profiled-nmethods" memory the Java virtual machine initially requested from the operating system. (Gauge) |
|
Maximum amount of CodeHeap "profiled-nmethods" memory the Java virtual machine attempts to use. (Gauge) |
|
Amount of CodeHeap "profiled-nmethods" memory committed for the Java virtual machine to use. (Gauge) |
|
Amount of CodeHeap "profiled-nmethods" memory used by the Java virtual machine. (Gauge) |
|
Percentage of CodeHeap "profiled-nmethods" memory used out of the maximum available. (Gauge) |
|
Amount of "metaspace" memory the Java virtual machine initially requested from the operating system. (Gauge) |
|
Maximum amount of "metaspace" memory the Java virtual machine attempts to use. (Gauge) |
|
Amount of "metaspace" memory committed for the Java virtual machine to use. (Gauge) |
|
Amount of "metaspace" memory used by the Java virtual machine. (Gauge) |
|
Percentage of "metaspace" memory used out of the maximum available. (Gauge) |
|
Amount of "eden space" memory the Java virtual machine initially requested from the operating system. (Gauge) |
|
Maximum amount of "eden space" memory (young generation) the Java virtual machine attempts to use. (Gauge) |
|
Amount of "eden space" memory (young generation) committed for the Java virtual machine to use. (Gauge) |
|
Amount of "eden space" memory (young generation) after the last time garbage collection recycled unused objects in this memory pool. (Gauge) |
|
Amount of "eden space" memory (young generation) used by the Java virtual machine. (Gauge) |
|
Percentage of "eden space" memory (young generation) used out of the maximum available. (Gauge) |
|
Amount of "tenured generation" (old generation) memory the Java virtual machine initially requested from the operating system. (Gauge) |
|
Maximum amount of "tenured generation" (old generation) memory the Java virtual machine attempts to use. (Gauge) |
|
Amount of "tenured generation" memory (old generation) committed for the Java virtual machine to use. (Gauge) |
|
Amount of "tenured generation" memory (old generation) after the last time garbage collection recycled unused objects in this memory pool. (Gauge) |
|
Amount of "tenured generation" memory (old generation) used by the Java virtual machine. (Gauge) |
|
Percentage of "tenured generation" memory (old generation) used out of the maximum available. (Gauge) |
|
Amount of "survivor space" memory (young generation) the Java virtual machine initially requested from the operating system. (Gauge) |
|
Maximum amount of "survivor space" memory (young generation) the Java virtual machine attempts to use. (Gauge) |
|
Amount of "survivor space" memory (young generation) committed for the Java virtual machine to use. (Gauge) |
|
Amount of "survivor space" memory (young generation) after the last time garbage collection recycled unused objects in this memory pool. (Gauge) |
|
Amount of "survivor space" memory (young generation) used by the Java virtual machine. (Gauge) |
|
Percentage of "survivor space" memory (young generation) used out of the maximum available. (Gauge) |
|
Amount of memory committed for the Java virtual machine to use. (Gauge) |
|
Amount of memory the Java virtual machine initially requested from the operating system. (Gauge) |
|
Maximum amount of memory the Java virtual machine attempts to use. (Gauge) |
|
Amount of memory used by the Java virtual machine. (Gauge) |
|
Number of threads in the BLOCKED state. (Gauge) |
|
Number of live threads including both daemon and non-daemon threads. (Gauge) |
|
Number of live daemon threads. (Gauge) |
|
Number of threads in the NEW state. (Gauge) |
|
Number of threads in the RUNNABLE state. (Gauge) |
|
Number of threads in the TERMINATED state. (Gauge) |
|
Number of threads in the TIMED_WAITING state. (Gauge) |
|
Number of threads in the WAITING state. (Gauge) |
OAuth 2.0 metrics
AM exposes the following OAuth 2.0 monitoring metrics:
oauth2.grant.<grant-type>-
Rate of OAuth 2.0 grant completion by grant type. (Summary)
Prometheus syntax:
am_oauth2_grant{grant_type=<grant-type>}Labels:
<grant-type>-
authorization-code(Prometheus:authorization_code)client-credentials(Prometheus:client_credentials)device-code(Prometheus:device_code)implicitrefreshresource-owner-password(Prometheus:resource_owner_password)
oauth2.grant.revoke-
Rate of OAuth 2.0 grant revocation. (Summary)
Prometheus syntax: `am_oauth2_grant_revoke
oauth2.token.<token-type>.issue-
Rate of OAuth 2.0 token issuance by token type. (Summary)
Prometheus syntax:
am_oauth2_token_issue{token_type=<token-type>}Labels:
<token-type>-
access-token(Prometheus:access_token)authorization-code(Prometheus:authorization_code)device-code(Prometheus:device_code)id-token. OpenID Connect ID token. (Prometheus:id_token)ops. OpenID Connect Ops token for session management.permission-ticket. User-Managed Access permission ticket. (Prometheus:permission_ticket)refresh-token(Prometheus:refresh_token)
oauth2.token.access-token.revoke-
Rate of OAuth 2.0 access token revocation. (Summary)
Prometheus syntax:
am_oauth2_token_revoke{token_type=access_token} oauth2.token.read-as-jwt.<outcome>-
Rate of successfully/unsuccessfully reading OAuth 2.0 JSON Web Tokens (JWT). (Timer)
Prometheus syntax:
am_oauth2_token_read_as_jwt{outcome=<outcome>}Labels:
<outcome>-
successfailure
Session metrics
AM exposes the following session-related monitoring metrics:
session.authentication-in-memory.store.size-
Number of authentication sessions stored in the in-memory authentication session store. (Gauge)
Prometheus syntax:
am_session_authentication_in_memory_store_size session.cts-based.cache.eviction-
Rate of evictions from the session cache. (Summary)
Prometheus syntax:
am_session_cts_based_cache_eviction session.cts-based.cache.size-
Number of sessions in the session cache. (Gauge)
Prometheus syntax:
am_session_cts_based_cache_size session.cts-based.cache.hit-
Rate of cache hits for the session cache. (Summary)
Prometheus syntax:
am_session_cts_based_cache{outcome=hit} session.cts-based.cache.miss-
Rate of cache misses for the session cache. (Summary)
Prometheus syntax:
am_session_cts_based_cache{outcome=miss} session.<session-type>.lifetime-
Rate of session lifetimes. (Timer)
Prometheus syntax:
am_session_lifetime{session_type=<session-type>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based)
session.<session-type>.add-listener.<outcome>-
Rate of successful/unsuccessful p-search listener adds and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=add-listener, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.add-pll-listener.<outcome>-
Rate of successful/unsuccessful PLL listener adds and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=add-pll-listener, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.check-exists.<outcome>-
Rate of successful/unsuccessful calls to check if a session exists and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=check-exists, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.create.<outcome>-
Rate of successful/unsuccessful session creation and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=create, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.destroy.<outcome>-
Rate of successful/unsuccessful session destroy and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=destroy, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.get-restricted-token-id.<outcome>-
Rate of successful/unsuccessful restricted token ID dereferencing and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=get-restricted-token-id, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.idle-timeout.<outcome>-
Rate of successful/unsuccessful session idle time out and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=idle-timeout, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.logout.<outcome>-
Rate of successful/unsuccessful session logout and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=logout, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.max-timeout.<outcome>-
Rate of successful/unsuccessful session end of life and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=max-timeout, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.read-all.<outcome>-
Rate of successful/unsuccessful requests to read all sessions and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=read-all, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.read.<outcome>-
Rate of successful/unsuccessful session reads and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=read, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.refresh.<outcome>-
Rate of successful/unsuccessful session refresh and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=refresh, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.search.<outcome>-
Rate of successful/unsuccessful session searches and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=search, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.set-external-property.<outcome>-
Rate of successful/unsuccessful setting a property on a session and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=set-external-property, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.set-property.<outcome>-
Rate of successful/unsuccessful session property setting and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=set-property, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
session.<session-type>.validate.<outcome>-
Rate of successful/unsuccessful session validation and time taken to perform this operation. (Timer)
Prometheus syntax:
am_session{session_type=<session-type>,operation=validate, outcome=<outcome>}Labels:
<session-type>-
authentication-in-memory. In-memory authentication sessions used to track authentication progress. (Prometheus:authentication_in_memory)authentication-cts-based. Server-side authentication sessions used to track authentication progress. (Prometheus:authentication_cts_based)authentication-client-based. Client-side authentication sessions used to track authentication progress. (Prometheus:authentication_client_based)cts-based. Server-side sessions issued after successful authentication. (Prometheus:cts_based)client-based. Client-side sessions; for example in a browser cookie, issued after successful authentication. (Prometheus:client_based) <outcome>-
successfailure
SNMP CTS object identifiers
The OIDs related to SNMP monitoring of CTS follow guidance described in RFC 1271.
|
The interface stability of the legacy SNMP monitoring feature is deprecated. |
The OIDs listed in this section include the prefix assigned to ForgeRock, enterprises.36733.
They also include the entries associated with AM (1), SNMP (2), and CTS monitoring (3): 1.2.3.
Therefore, the root OID for all CTS monitored components is enterprises.36733.1.2.3.
All individual monitored CTS components are suffixes that are consistent with the image shown here.
CTS token type OIDs
This table shows how OIDs are split into different token types. Do not forget the prefix.
For example, the complete OID for monitoring SAML v2.0 tokens is enterprises.36733.1.2.3.1.1.2.
The options for the token table are also shown.
For example, the token table OID for SAML v2.0 is based on the entries associated with ForgeRock, enterprises.36733,
AM 1, SNMP 2, CTS Monitoring 3, token table 1, entry 1, and SAML v2.0 2,
which is enterprises.36733.1.2.3.1.1.2.
| OID by token type | Description |
|---|---|
|
Session |
|
SAML v2.0 |
|
OAuth 2.0 |
|
REST |
|
OAuth 2.0 CSRF Protection |
|
UMA Resource |
|
UMA Permission Ticket |
|
UMA Requesting Party |
|
UMA Audit Entry |
|
Session Blacklist |
|
UMA Pending Request |
|
Security Token Service |
|
OAuth 2.0 Blacklist |
|
OAuth 2.0 Client-Based |
|
Push Notification |
|
Cluster-wide Notification |
CTS monitoring operation types
OIDs related to CTS monitoring operations are based on basic CRUD operations (plus list).
This table shows the options for the operation table.
| OID by operation | Description |
|---|---|
|
Create |
|
Read |
|
Update |
|
Delete |
|
List |
CTS monitoring entry data types
CTS monitoring entries use the following data types:
Counter64-
A 64-bit, unsigned integer type.
Counter64is a standard data type returned by SNMP OIDs. For more information, refer to Structure of Management Information Version 2. Float2dp-
A floating point number with the value d-2 in the
DISPLAY-HINTclause. SNMP clients that handle theDISPLAY-HINTclause will correctly display the value as a floating point number with two decimal places. Other types of clients that do not handle theDISPLAY-HINTclause will incorrectly display the value as an integer that is one hundred times larger than the correct value.Float2dpis a custom data type returned by some ForgeRock CTS OIDs.
CTS CRUD operation entries
The OIDs in this table relate to all CRUD (and list) operations.
The options for the CRUD operations table are shown in the following tables. Each value is associated with CRUD and list operations.
| OID by operation entry | Data type | Description |
|---|---|---|
|
|
Cumulative count |
|
|
Average (in period) |
|
|
Minimum (in period) |
|
|
Maximum (in period) |
|
|
Cumulative failure count |
|
|
Average failures (in period) |
|
|
Minimum failures (in period) |
|
|
Maximum failures (in period) |
Each of the options in this table can be divided into CRUD and list related operations. The suffix OID for such operations is as follows:
-
1: Create
-
2: Read
-
3: Update
-
4: Delete
-
5: List
For example, since the OID for cumulative count is enterprises.36733.1.2.3.3.1.1,
the OID for the cumulative count of delete operations is enterprises.36733.1.2.3.3.1.1.4
| Cumulative count operations OID | Data type | Description |
|---|---|---|
|
|
Cumulative count of CREATE operations |
|
|
Cumulative count of READ operations |
|
|
Cumulative count of UPDATE operations |
|
|
Cumulative count of DELETE operations |
|
|
Cumulative count of LIST operations |
| Average number operations OID | Data type | Description |
|---|---|---|
|
|
Average number of CREATE operations (in period) |
|
|
Average number of READ operations (in period) |
|
|
Average number of UPDATE operations (in period) |
|
|
Average number of DELETE operations (in period) |
|
|
Average number of LIST operations (in period) |
| Minimum number operations OID | Data type | Description |
|---|---|---|
|
|
Minimum number of CREATE operations (in period) |
|
|
Minimum number of READ operations (in period) |
|
|
Minimum number of UPDATE operations (in period) |
|
|
Minimum number of DELETE operations (in period) |
|
|
Minimum number of LIST operations (in period) |
| Maximum Number Operations OID | Data Type | Description |
|---|---|---|
|
|
Maximum number of CREATE operations (in period) |
|
|
Maximum number of READ operations (in period) |
|
|
Maximum number of UPDATE operations (in period) |
|
|
Maximum number of DELETE operations (in period) |
|
|
Maximum number of LIST operations (in period) |
| Cumulative failure operations OID | Data type | Description |
|---|---|---|
|
|
Cumulative Failure of CREATE operations (in period) |
|
|
Cumulative Failure of READ operations (in period) |
|
|
Cumulative Failure of UPDATE operations (in period) |
|
|
Cumulative Failure of DELETE operations (in period) |
|
|
Cumulative Failure of LIST operations (in period) |
| Average number, failure operations OID | Data type | Description |
|---|---|---|
|
|
Average number of CREATE operations failures (in period) |
|
|
Average number of READ operations failures (in period) |
|
|
Average number of UPDATE operations failures (in period) |
|
|
Average number of DELETE operations failures (in period) |
|
|
Average number of LIST operations failures (in period) |
| Minimum number, operations failures OID | Data type | Description |
|---|---|---|
|
|
Minimum number of CREATE operations failures (in period) |
|
|
Minimum number of READ operations failures (in period) |
|
|
Minimum number of UPDATE operations failures (in period) |
|
|
Minimum number of DELETE operations failures (in period) |
|
|
Minimum number of LIST operations failures (in period) |
| Maximum number, operations failures OID | Data type | Description |
|---|---|---|
|
|
Maximum number of CREATE operations failures (in period) |
|
|
Maximum number of READ operations failures (in period) |
|
|
Maximum number of UPDATE operations failures (in period) |
|
|
Maximum number of DELETE operations failures (in period) |
|
|
Maximum number of LIST operations failures (in period) |
CTS CRUD operations per token type
OIDs that start with enterprises.36733.1.2.3.4.1 are labels for CTS CRUD operations per token type.
Tokens of each type can be created, read, updated, deleted, and listed. Each of these types can be measured cumulatively. They can also be measured over a period of time (default=10 seconds), as an average, minimum, and maximum.
OID suffixes for CRUD operations are defined according to the following rules.
The first part of the OID is enterprises.36733.1.2.3.4.1.
The next OID suffix specifies a metric:
| OID suffix | Data type | Metric |
|---|---|---|
1 |
|
Cumulative count |
2 |
|
Average (in period) |
3 |
|
Minimum (in period) |
4 |
|
Maximum (in period) |
The next OID suffix specifies a token type:
| OID suffix | Token type |
|---|---|
1 |
Session |
2 |
SAML v2.0 |
3 |
OAuth 2 |
4 |
REST |
5 |
OAuth 2.0 CSRF Protection |
6 |
UMA Resource |
7 |
UMA Permission Ticket |
8 |
UMA Requesting Party |
9 |
UMA Audit Entry |
10 |
Session Blacklist |
11 |
UMA Pending Request |
12 |
Security Token Service |
13 |
OAuth 2.0 Blacklist |
14 |
OAuth 2.0 Client-Based |
15 |
Push Notification |
16 |
Cluster-wide Notification |
The final OID suffix specifies an operation:
| OID suffix | Operation |
|---|---|
1 |
Create |
2 |
Read |
3 |
Update |
4 |
Delete |
5 |
List |
The following examples illustrate OID construction for CTS CRUD operations per token type.
| OID | Data type | Description |
|---|---|---|
|
|
Cumulative count of updated Session tokens |
|
|
Maximum deleted OAuth 2.0 tokens (in period) |
|
|
Average listed Session Blacklist tokens (in period) |
CTS token operation status
The CTS token OIDs defined in this section specify the total number of tokens of each type and their average current lifetimes.
The options for token operations are shown in the following tables. Total and average current lifetimes are associated with each CTS token type.
| Total tokens, by type | Data type | Description |
|---|---|---|
|
|
Total number of Session tokens |
|
|
Total number of SAML v2.0 tokens |
|
|
Total number of OAuth 2.0 tokens |
|
|
Total number of REST tokens |
|
|
Total number of OAuth 2.0 CSRF Protection tokens |
|
|
Total number of UMA Resource tokens |
|
|
Total number of UMA Permission Ticket tokens |
|
|
Total number of UMA Requesting Party tokens |
|
|
Total number of UMA Audit Entry tokens |
|
|
Total number of Session Blacklist tokens |
|
|
Total number of UMA Pending Request tokens |
|
|
Total number of Security Token Service tokens |
|
|
Total number of OAuth 2.0 Blacklist tokens |
|
|
Total number of OAuth 2.0 client-side tokens |
|
|
Total number of Push Notification tokens |
|
|
Total number of Cluster-wide Notification tokens |
| Average token lifetime, by type | Data type | Description |
|---|---|---|
|
|
Average lifetime of Session tokens in seconds |
|
|
Average lifetime of SAML v2.0 tokens in seconds |
|
|
Average lifetime of OAuth 2.0 tokens in seconds |
|
|
Average lifetime of REST tokens in seconds |
|
|
Average lifetime of OAuth 2.0 CSRF Protection tokens in seconds |
|
|
Average lifetime of UMA Resource tokens in seconds |
|
|
Average lifetime of UMA Permission Ticket tokens in seconds |
|
|
Average lifetime of UMA Requesting Party tokens in seconds |
|
|
Average lifetime of UMA Audit Entry tokens in seconds |
|
|
Average lifetime of Session Blacklist tokens in seconds |
|
|
Average lifetime of UMA Pending Request tokens in seconds |
|
|
Average lifetime of Security Token Service tokens in seconds |
|
|
Average lifetime of OAuth 2.0 denylist tokens in seconds |
|
|
Average lifetime of OAuth 2.0 client-side tokens in seconds |
|
|
Average lifetime of Push Notification tokens in seconds |
|
|
Average lifetime of Cluster-wide Notification tokens in seconds |
CTS reaper run information
The CTS reaper deletes unused or expired tokens. Unless AM is in a shutdown cycle, the CTS reaper is designed to run continuously. By default, the CTS reaper runs in fixed intervals, unless AM is in the process of shutting down.
A single OID, enterprises.36733.1.2.3.6.0, relates to the CTS reaper.
This OID:
-
Specifies the average rate of deleted tokens per CTS reaper run
-
Has the
Float2dpdata type.
CTS connection factory OIDs
Every request for a CTS token is a request to the CTSConnectionFactory.
Such requests can either succeed or fail.
The following OIDs provide measures for both such connections.
The CTSConnectionFactory OIDs are also measured using a rate window system, similar to all the other CTS OIDs,
except the CTS Reaper.
As there are no indexes required to look up the value of CTSConnectionFactory OIDs, they end in 0. Success or failure of these OIDs are not specific to any operation or token type.
The following tables list the OIDs related to the CTSConnectionFactory.
| Successes, CTSConnectionFactory | Data type | Description |
|---|---|---|
|
|
Cumulative number of successful connections |
|
|
Average number of successful connections (in period) |
|
|
Minimum number of successful connections (in period) |
|
|
Maximum number of successful connections (in period) |
| Failures, CTSConnectionFactory | Data type | Description |
|---|---|---|
|
|
Cumulative number of failed connections |
|
|
Average number of failed connections (in period) |
|
|
Minimum number of failed connections (in period) |
|
|
Maximum number of failed connections (in period) |