General format of the access control rules
Access control instructions (ACIs) are represented as strings that are applied to one or more entries within the directory information tree (DIT).
Typically, an ACI is placed on a subtree, such as dc=example,dc=com, and applies to that base entry and all entries below it in the tree. The directory server iterates through the DIT to compile the access control rules into an internally-used list of denied and allowed targets and their permissible operations. When a client application, such as ldapsearch, enters a request, the server checks that the user who binds with the server has the necessary access rights to the requested search targets. ACIs are cumulatively applied so that a user who has an ACI at an entry can also have other access rights available if ACIs are defined higher in the DIT and are applicable to the user. In most environments, ACIs are defined at the root of a main branch or a subtree, and not on individual entries unless absolutely required.
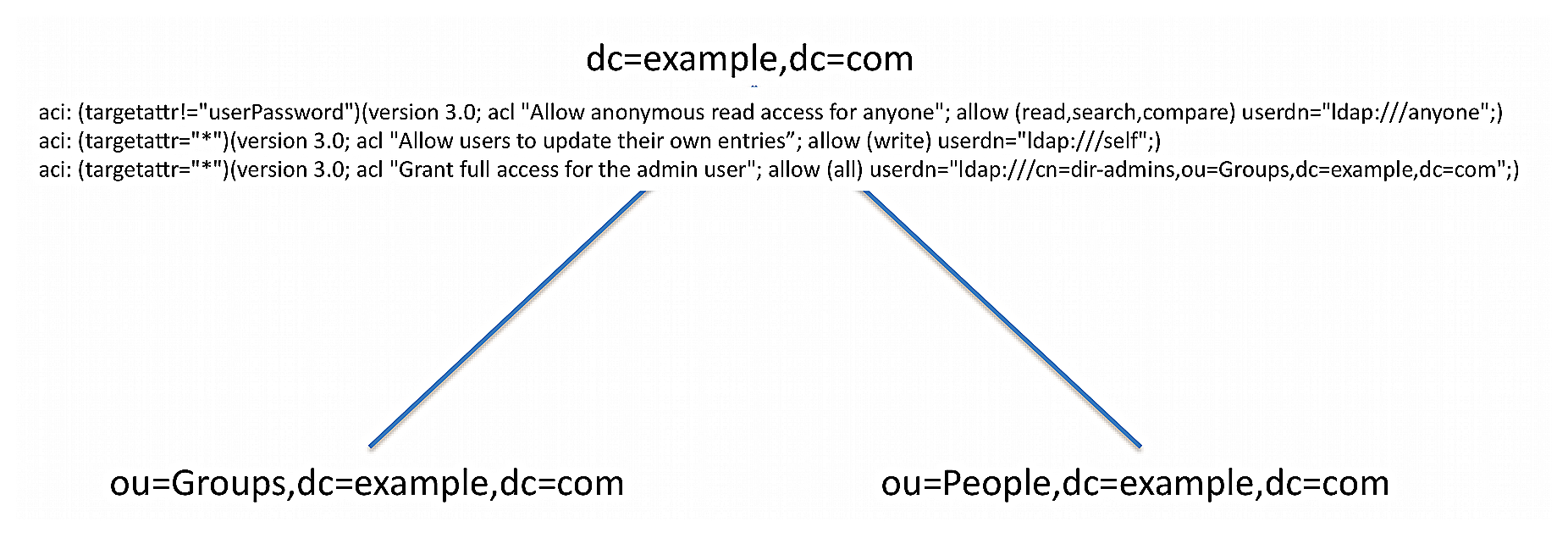
An access control rule has the following basic syntax:
aci : (targets) (version 3.0; acl "name";
permissions
bind rules
;)
| Access Control Component | Description | ||
|---|---|---|---|
targets |
Specifies the set of entries and attributes to which an access control rule applies. Use the following syntax: |
||
name |
Specifies the name of the ACI |
||
permissions |
Specifies the type of operations to which an access control rule might apply. Use the following syntax: |
||
bind rules |
Specifies the criteria that indicate whether an access control rule should apply to a given requester. Use the following syntax:
|