Working with alternate authorization identities
The following sections cover the procedures to configure the alternate authorization identities for the PingDirectoryProxy server.
Access control rules in an entry-balanced deployment are configured in the PingDirectory backend servers and require access to the entry contents of the user issuing the request.
This can introduce a potential issue when clients to the PingDirectoryProxy server authenticate as users whose entries are among the entry-balanced sets. If the server processing a request doesn’t contain the issuing user’s entry, the access control can’t be evaluated. One solution to this problem is to make use of an alternate authorization identity for the user, which references an entry that exists in all PingDirectory server’s in all backend sets and has an equivalent set of access control rights as the authenticated user.
For the following example, assume a deployment has two entry-balancing sets: set-01 and set-02. Set-01 has entries in the uid=0-10000 range, while set-02 has entries for uid=10001-20000.
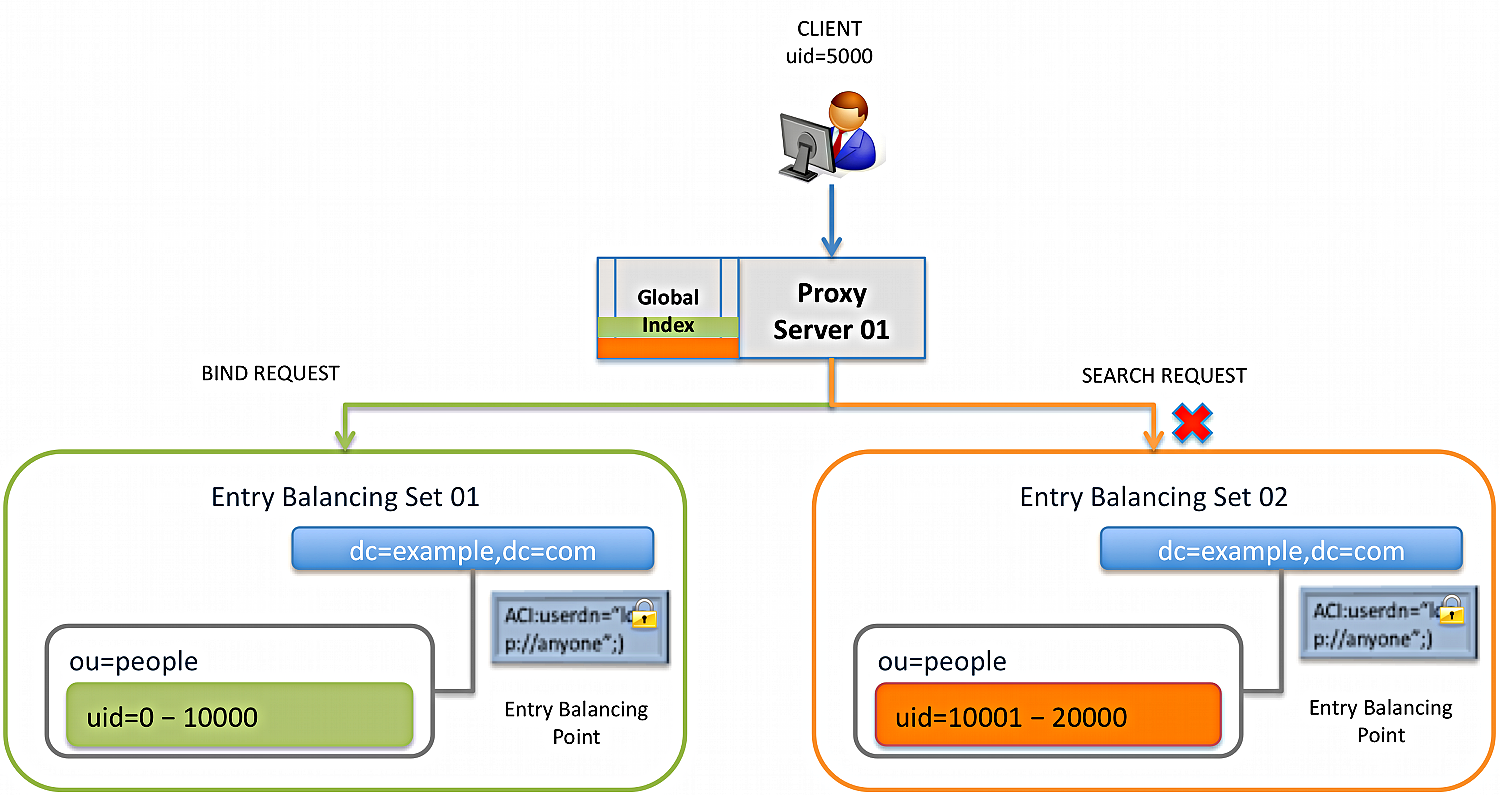
Processing steps
-
The client with
uid=5000binds to the PingDirectoryProxy server, which sends aBINDrequest to entry-balancing set-01. -
The client sends a
SEARCHrequest with filter(uid=15000). -
The PingDirectoryProxy server determines that
uid=15000lives on entry-balancing set-02. -
The PingDirectoryProxy server determines that the entry for the authenticated user with
uid=5000doesn’t exist in set-02 and that the access control handler has to reject theSEARCHrequest issued by an unknown user. -
The PingDirectoryProxy server observes that the PingDirectory server processing a request doesn’t contain the entry of the user issuing the request and decides to use an alternate authorization identity.