Policy enforcement
The following procedure gives an example of how to request and enforce policy decisions from Identity Cloud.
Enforce a simple policy
Before you start, set up and test the example in Cross-domain single sign-on.
-
Set up Identity Cloud:
-
In the Identity Cloud admin UI, select Native Consoles > Access Management. The AM admin UI is displayed.
-
Select Authorization > Policy Sets > New Policy Set, and add a policy set with the following values:
-
Id :
PEP-CDSSO -
Resource Types :
URL
-
-
In the new policy set, add a policy with the following values:
-
Name :
CDSSO -
Resource Type :
URL -
Resource pattern :
*://*:*/* -
Resource value :
http://app.example.com:8081/home/cdssoThis policy protects the home page of the sample application.
-
-
On the Actions tab, add an action to allow HTTP
GET. -
On the Subjects tab, remove any default subject conditions, add a subject condition for all
Authenticated Users.
-
-
Set up IG:
-
Replace
cdsso-idc.jsonwith the following route, and correct the value for the property amInstanceUrl:-
Linux
-
Windows
$HOME/.openig/config/routes/pep-cdsso-idc.json
%appdata%\OpenIG\config\routes\pep-cdsso-idc.json
{ "name": "pep-cdsso-idc", "baseURI": "http://app.example.com:8081", "condition": "${find(request.uri.path, '^/home/cdsso')}", "properties": { "amInstanceUrl": "https://myTenant.forgeblocks.com/am" }, "heap": [ { "name": "SystemAndEnvSecretStore-1", "type": "SystemAndEnvSecretStore" }, { "name": "AmService-1", "type": "AmService", "config": { "url": "&{amInstanceUrl}", "realm": "/alpha", "agent": { "username": "ig_agent", "passwordSecretId": "agent.secret.id" }, "secretsProvider": "SystemAndEnvSecretStore-1", "sessionCache": { "enabled": false } } } ], "handler": { "type": "Chain", "config": { "filters": [ { "name": "CrossDomainSingleSignOnFilter-1", "type": "CrossDomainSingleSignOnFilter", "config": { "redirectEndpoint": "/home/cdsso/redirect", "authCookie": { "path": "/home", "name": "ig-token-cookie" }, "amService": "AmService-1" } }, { "name": "PolicyEnforcementFilter-1", "type": "PolicyEnforcementFilter", "config": { "application": "PEP-CDSSO", "ssoTokenSubject": "${contexts.cdsso.token}", "amService": "AmService-1" } } ], "handler": "ReverseProxyHandler" } } }Note the following feature of the route compared to
cdsso-idc.json:-
The CrossDomainSingleSignOnFilter is followed by a PolicyEnforcementFilter to enforce the policy
PEP-CDSSO.
-
-
When verificationSecretId is not configured, IG discovers
and uses the AM JWK set to verify the signature of AM session
tokens. If the JWK set isn’t available, IG does not verify the tokens.
|
-
Test the setup:
-
Go to https://ig.ext.com:8443/home/cdsso.
If you have warnings that the site is not secure respond to the warnings to access the site.
IG redirects you to Identity Cloud for authentication.
-
Log in to Identity Cloud as user
demo, passwordCh4ng3!t.Identity Cloud redirects you back to the request URL, and IG requests a policy decision. Identity Cloud returns a policy decision that grants access to the sample application.
-
Step up authorization for a transaction
Before you start, set up and test the example in Enforce a simple policy.
-
In the Identity Cloud admin UI, select Scripts > Auth Scripts > New Script > Journey Decision Node > Next, and add a default Journey Decision Node Script script called
TxTestPassword:/* - Data made available by nodes that have already executed are available in the sharedState variable. - The script should set outcome to either "true" or "false". */ var givenPassword = nodeState.get("password").asString() if (givenPassword.equals("7890")) { outcome = "true" } else { outcome = "false" } -
Configure a journey:
-
Click Journeys and add a journey with the following configuration:
-
Name:
Tx01_Tree -
Identity Object:
Alpha realm usersThe journey canvas is displayed.
-
-
In Nodes > Basic Authentication, drag a Password Collector node onto the canvas.
-
In Nodes > Utilities, drag a Scripted decision node onto the canvas.
-
Configure the scripted decision node as follows:
-
Script: select
TxTestPassword -
Outcomes: enter
trueandfalse
-
-
Connect the nodes as shown:
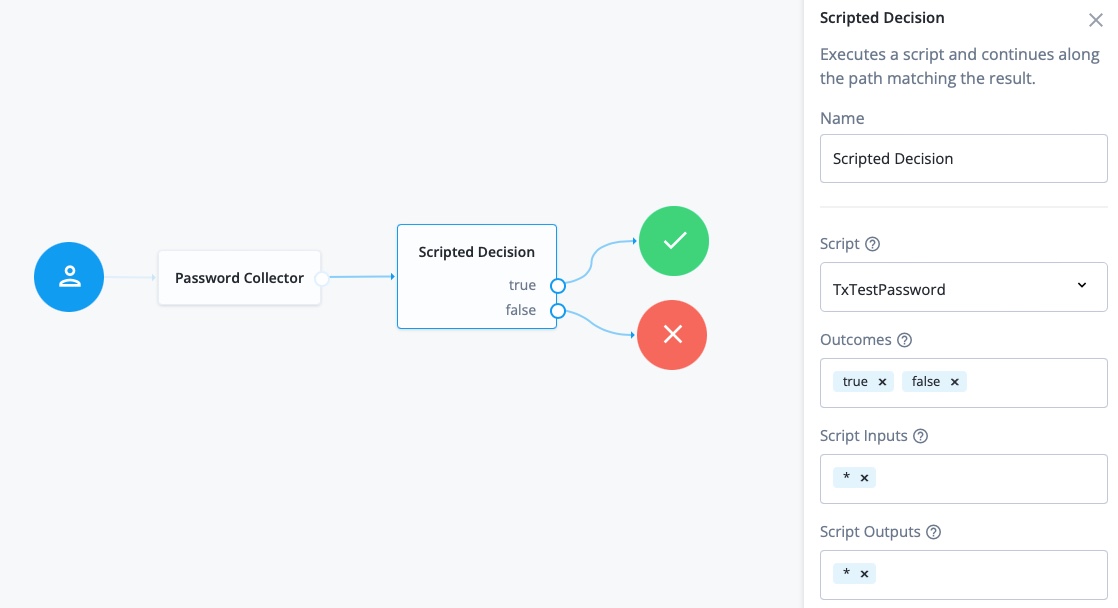
For information about configuring trees, refer to ForgeRock Identity Cloud Docs
-
-
Edit the authorization policy:
-
In the Identity Cloud admin UI, select Native Consoles > Access Management. The AM admin UI is displayed.
-
Select Authorization > Policy Sets > PEP-CDSSO, and add the following environment condition to the
CDSSOpolicy:-
All of -
Type:
Transaction -
Script name:
Authenticate to tree -
Strategy Specifier:
Tx01_Tree
-
-
-
Test the setup:
-
In a browser, go to https://ig.ext.com:8443/home/cdsso.
If you have not previously authenticated to Identity Cloud, the CrossDomainSingleSignOnFilter redirects the request to Identity Cloud for authentication.
-
Log in to Identity Cloud as user
demo, passwordCh4ng3!t. -
Enter the password
7890required by the scriptTxTestPassword.Identity Cloud redirects you back to the request URL, and IG requests a policy decision. Identity Cloud returns a policy decision based on the authentication journey.
-