Authenticating users
Your users are initially authenticated through the identity bridge, and for most purposes this single, secure authentication is sufficient. However, you can choose a secondary level of authentication as well. Together, the primary and secondary levels of authentication are known as multi-factor authentication.
|
Creating a PingOne for Enterprise account also automatically creates a PingID account. If your organization doesn’t use PingID, go to Setup > PingID > Configuration and clear the Allow users to manage their devices on the web box. This will prevent users from accessing the PingID Devices page from the web or PingOne Dock. |
You can apply the authentication policy to all users, or a subset of your users based on group membership or IP address. The policy applies to:
-
SSO to PingOne.
-
All SAML-enabled applications.
-
Selected SAML-enabled applications.
You can also apply secondary authentication to the PingOne admin portal.
How It Works
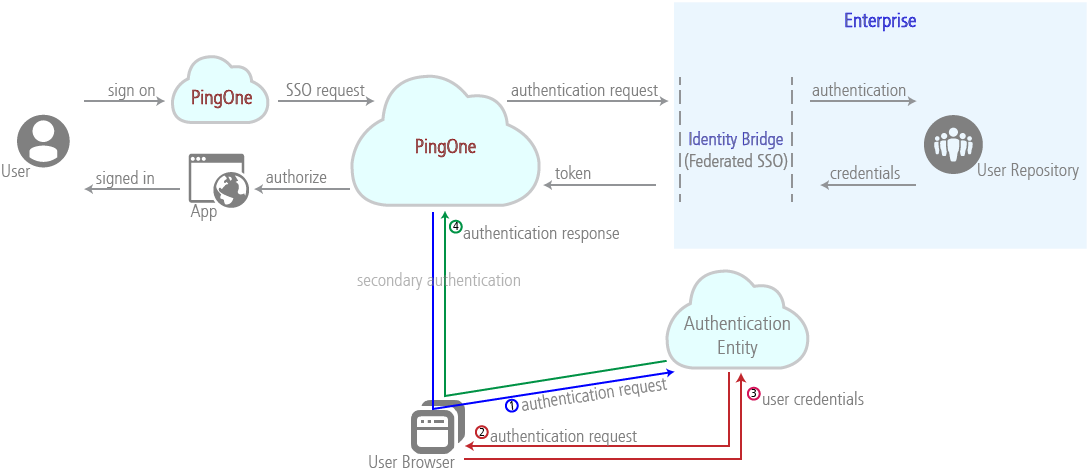
|
For Basic SSO applications, an identity bridge isn’t used and user credentials are sent to PingOne Directory. See Basic SSO (password vaulting) and Federated SSO with PingOne for Enterprise for descriptions. |